AI-Driven Cloud Security
Simplify investigations and accelerate remediation with built-in generative AI
The Challenge
Overwhelmed Cloud Security Teams
Cloud security teams are receiving hundreds of alerts each day that require investigation, remediation and response. As cloud environments increase in complexity, more advanced technical skills are needed, further adding to the cloud security skills gap. Many cloud security tools are difficult to operationalize and use, resulting in limited value to the organization and leaving teams struggling to understand their cloud environments.
Short-staffed cloud security teams struggle to keep up, resulting in burnout and turnover.
Cloud security tools that require specialized skills and training bring limited value.
Cloud environments are becoming more complex, requiring more advanced technical knowledge.
Cloud security falls behind, with critical alerts being missed.
Our Approach
Supercharge Your Cloud Security Operations with AI
Orca is at the forefront of leveraging AI to augment cloud security, lowering required skill thresholds, simplifying tasks, and using AI to calculate optimal cloud configurations. Orca’s AI-driven capabilities significantly improve cloud security postures and alleviate daily workloads and stress while allowing developers to focus on higher-value tasks.
Help your security team be 2-3 times more productive with Orca as their ‘security co-pilot’, reducing burnout and attrition.
Allow teams across the organization, regardless of their skill level, to benefit from Orca’s cloud insights and improve decision making.
Simplify and accelerate responding to zero day risks, performing audits, optimizing cloud assets, and understanding exposure to threats.
“Organizations with extensive use of security AI and automation demonstrated the highest cost savings comparatively, with an average cost of a data breach at USD 3.60 million, which was USD 1.76 million less and a 39.3% difference compared to no use.”
2023 IBM Cost of a Data Breach Report
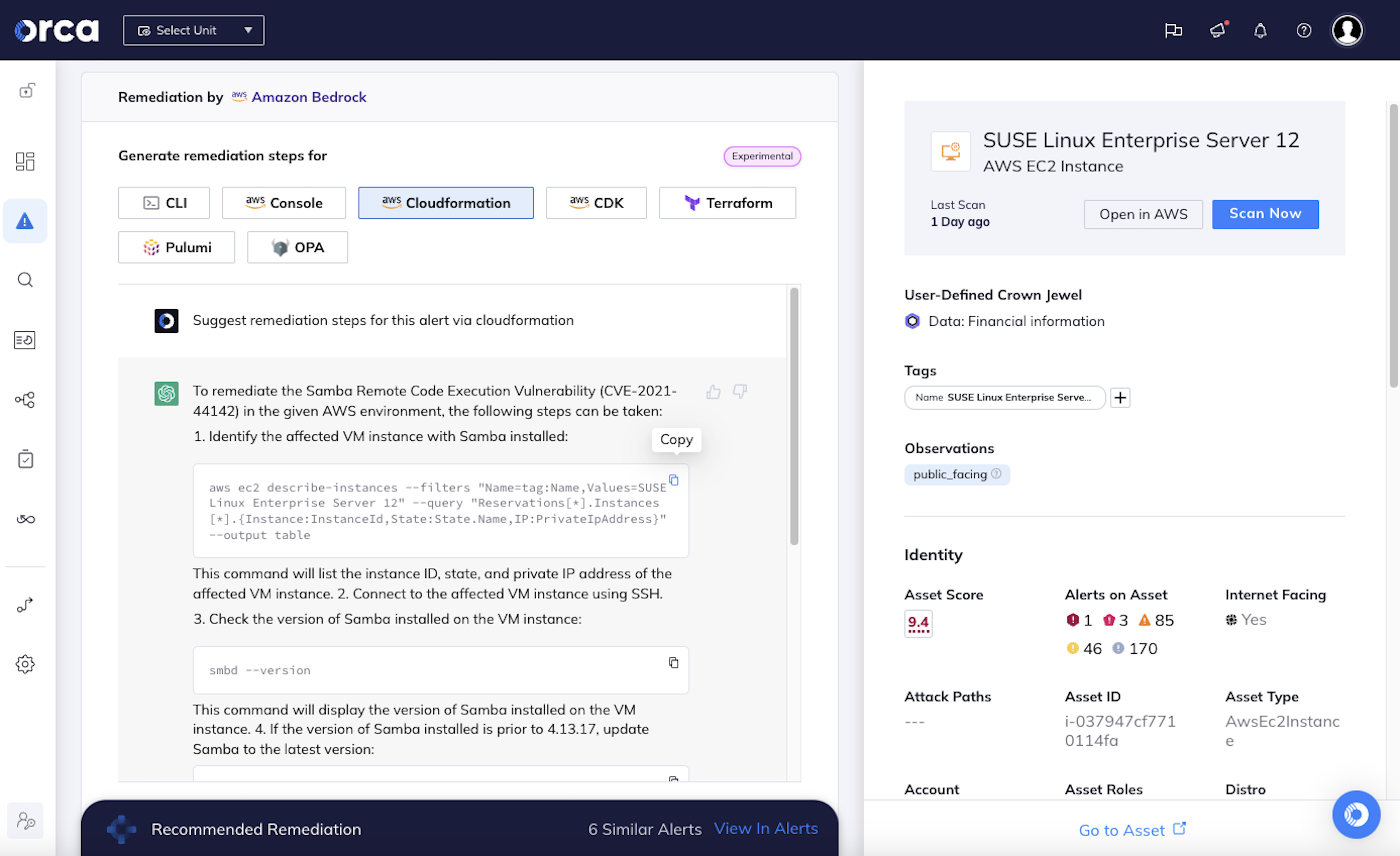
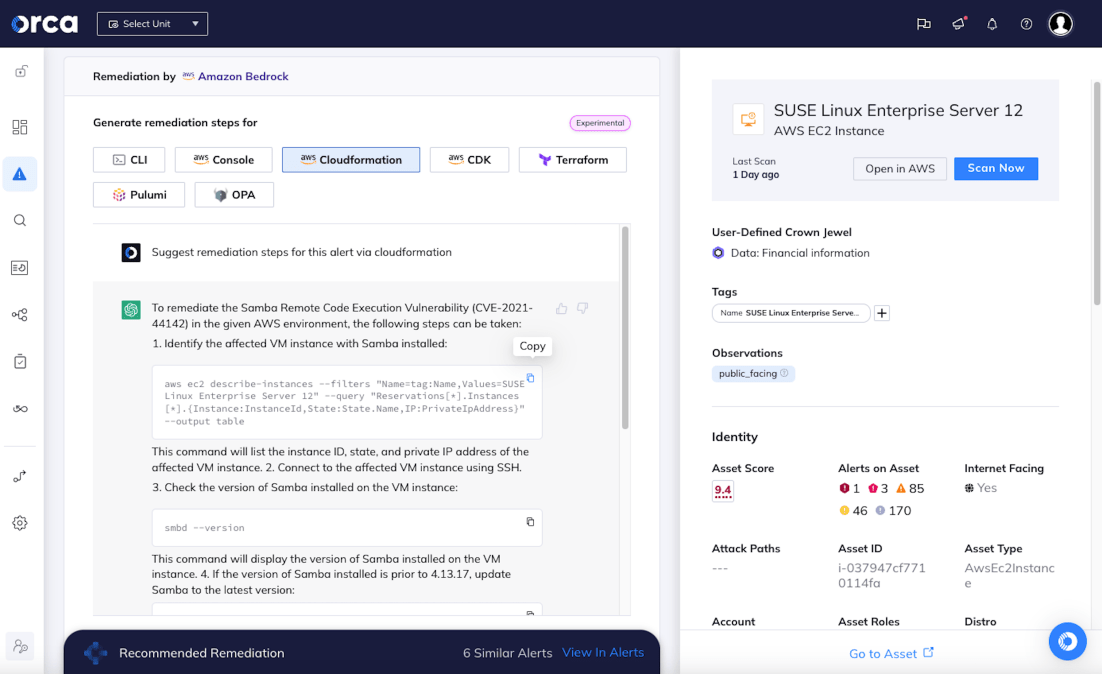
AI-generated, ready-to-use remediation steps
Instantly generate high-quality remediation instructions for each alert straight from the Orca Platform, enabling your team to address cloud vulnerabilities and risks 2-3 times faster. Data privacy is ensured by anonymizing requests and masking any sensitive data.
- Copy and paste remediation code into a command line interface or Infrastructure as Code (IaC) provisioning tools, or follow steps in the console.
- Ask follow-up questions to fine-tune remediation steps if needed.
- Leverage Azure OpenAI, Google Vertex AI, or Amazon Bedrock as your AI engine.
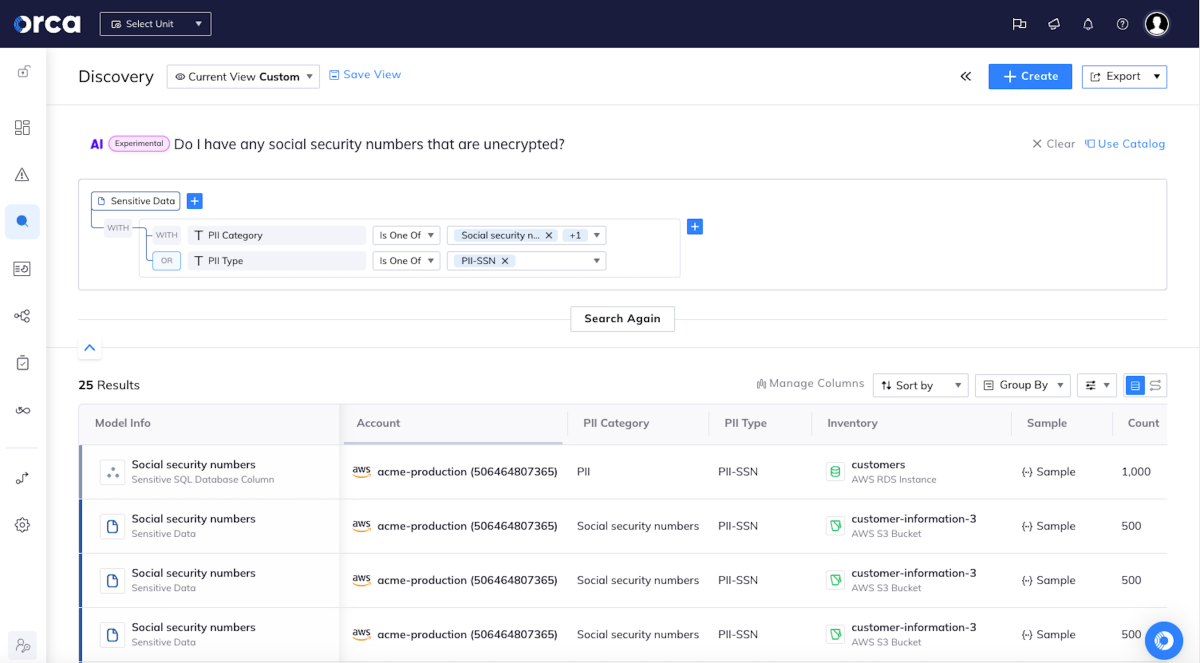
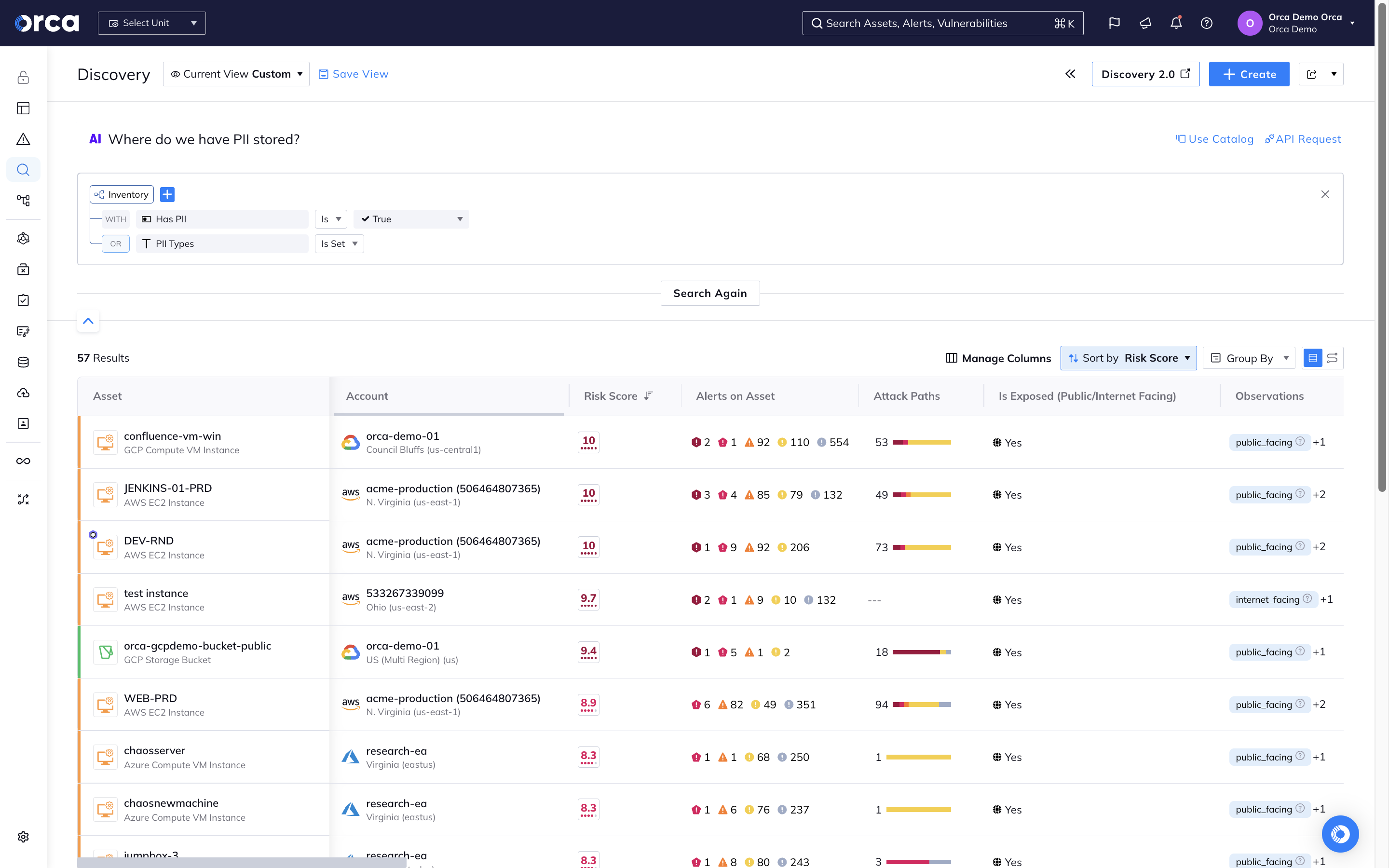
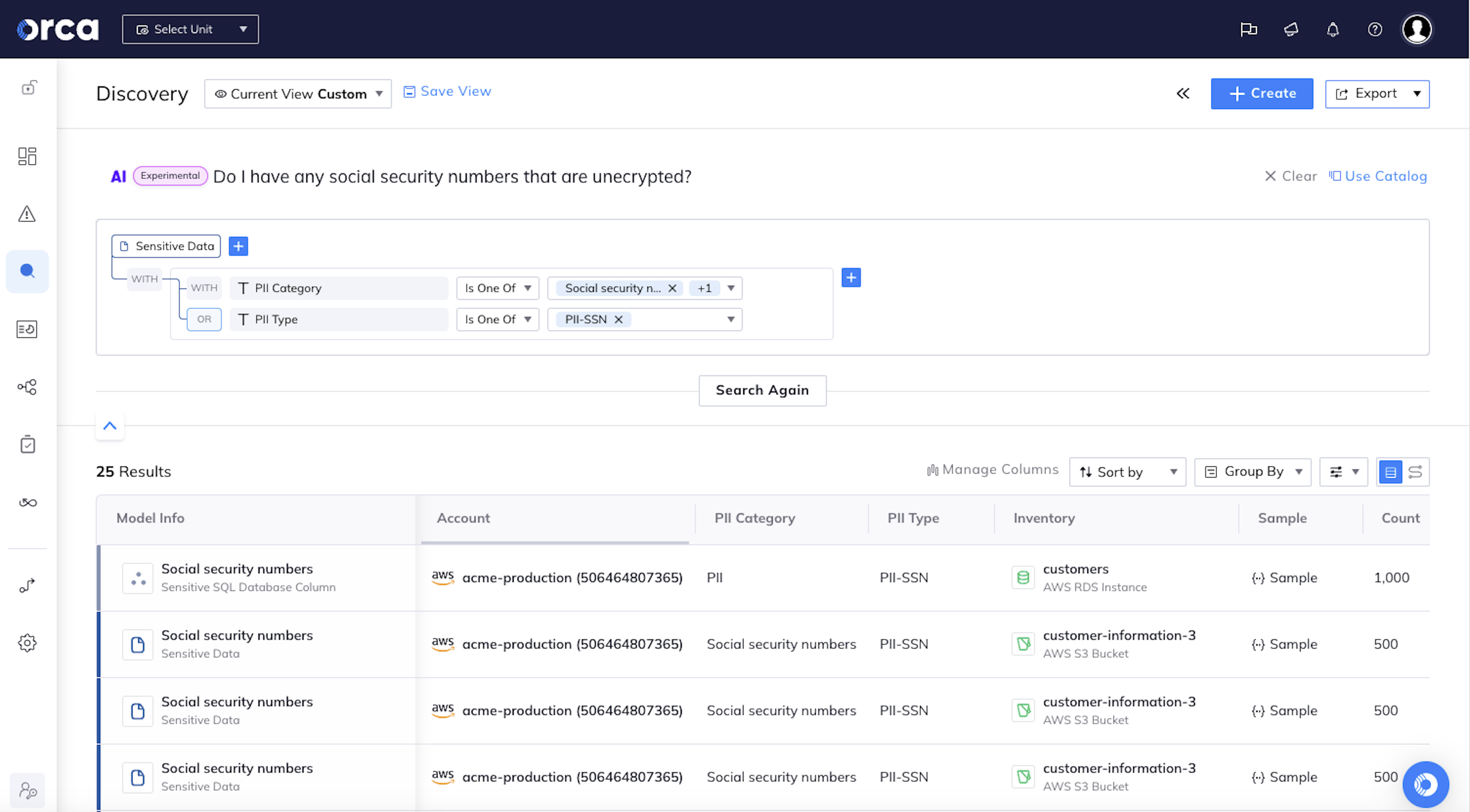
AI-powered search as intuitive as asking a question
Orca greatly simplifies searches by enabling users to ask natural language questions such as ‘Do I have any log4j vulnerabilities that are public facing?’ or “Do I have any unencrypted databases with sensitive data exposed to the Internet?”. This intuitive approach significantly reduces time-to-discovery, reducing risk and improving compliance.
- Users across the organization, regardless of their skill level, can easily understand exactly what’s in their cloud environment.
- Advanced users can craft complex and granular queries much faster than any human can.
- If applicable, Orca suggests related query options that could be used to refine results further.
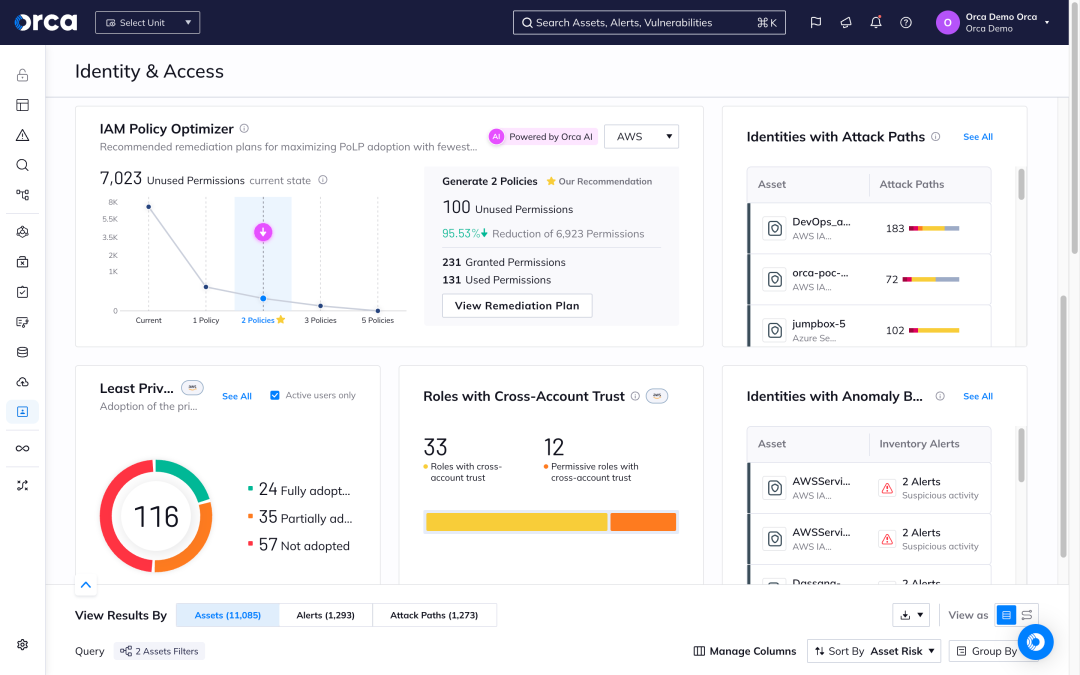
IAM policy management powered by AI
Orca leverages AI to simplify the complex task of securing identities and permissions and almost instantly helps organizations optimize their IAM policies to comply with the principle of least privilege and other best practices.
- Orca compares existing IAM policies to actual policy usage to recommend the optimal policy configurations that provide the largest security improvements with the least amount of changes.
- Get detailed information on suggested policy changes so you can select the best policy configuration for your needs.
- The selected configuration can be downloaded and effortlessly applied to your cloud account.
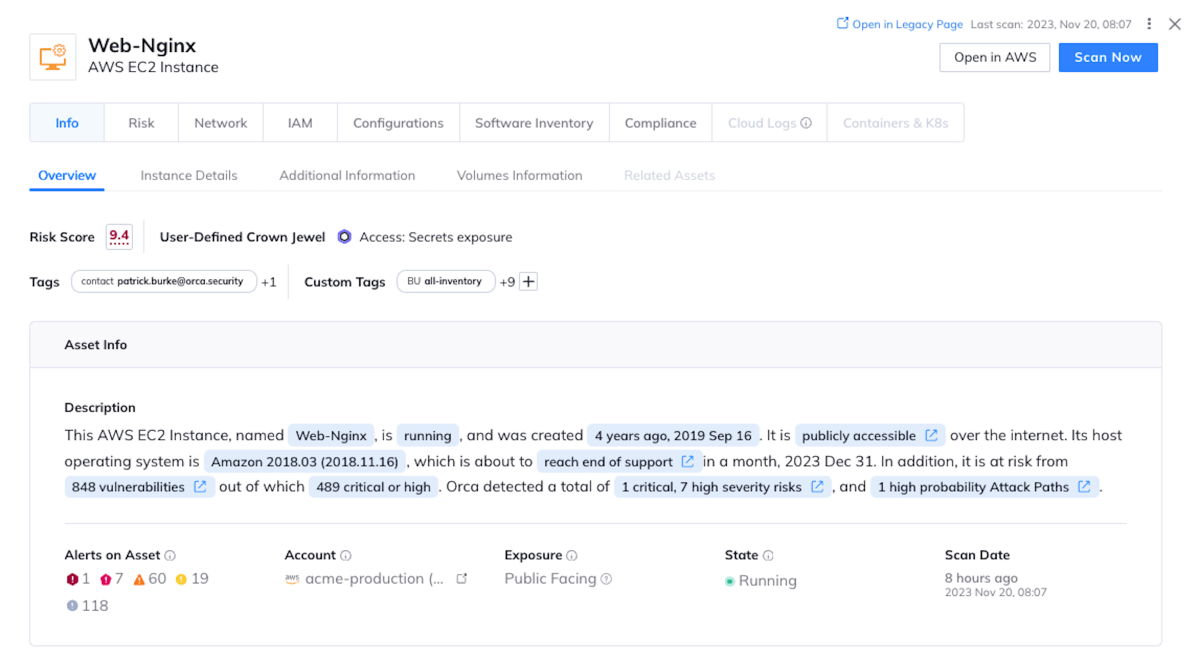
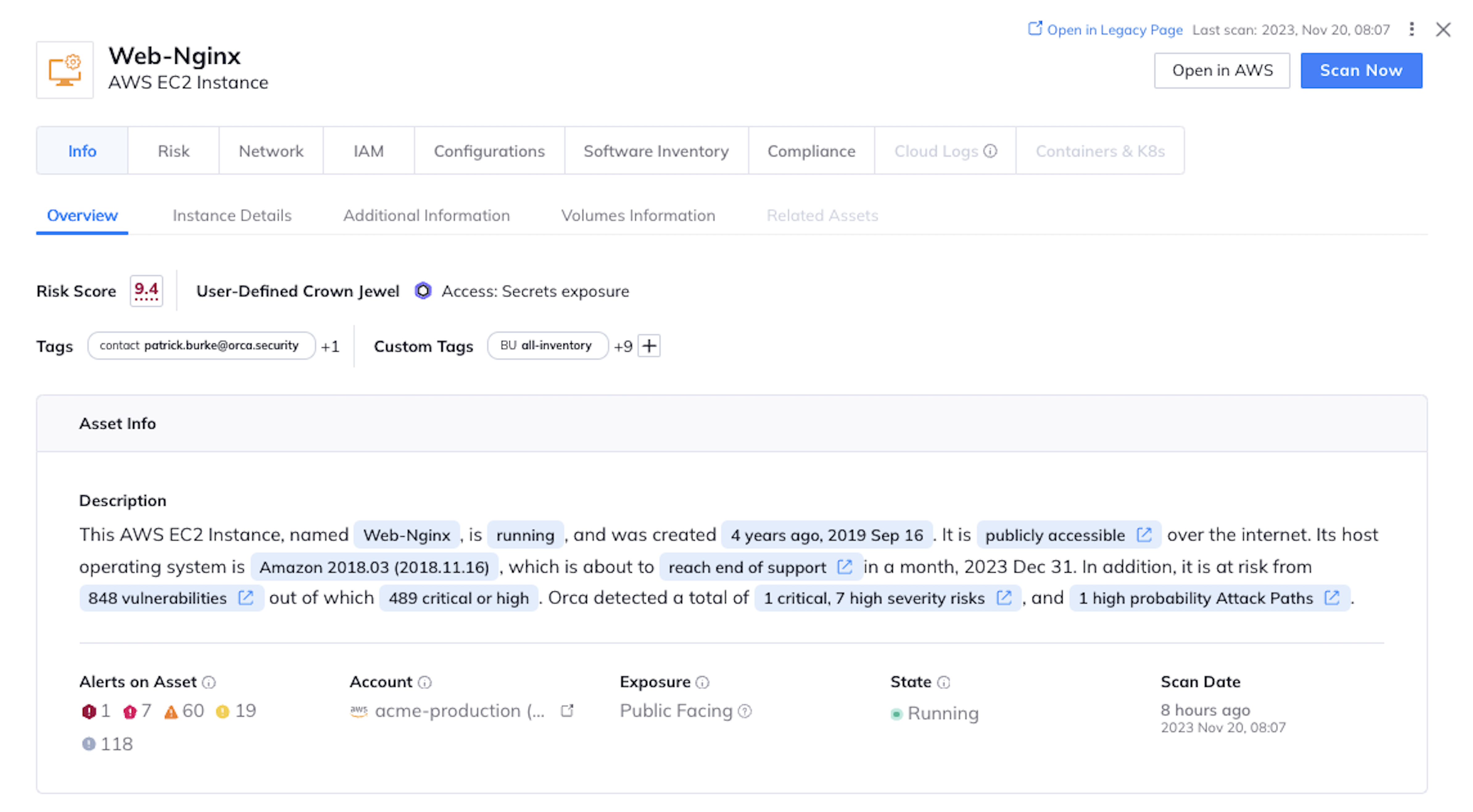
AI-generated alert and asset descriptions
Orca’s dynamic alert and asset descriptions greatly simplify investigations, summarizing all the important information that teams need to know in an easily consumable manner, reducing investigation time and improving Mean Time To Remediation (MTTR).
- For assets, Orca summarizes which risks are found and of what severity, how many attack paths they are part of, whether the asset is Internet-facing, running or paused, and more.
- For alerts, Orca explains what the risk is, when it was first found, if it is exploitable, whether there’s a fix, how an attacker could abuse it, and more.
- Where applicable, descriptions contain links to other resources with more information
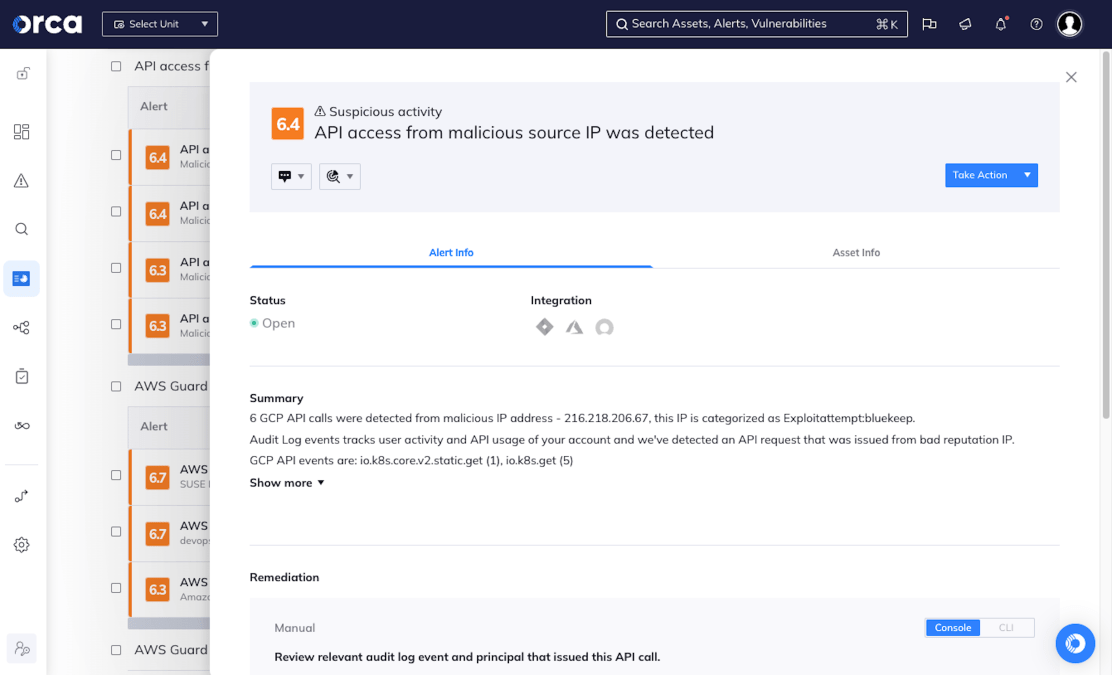
Intelligent anomaly detection using AI
Orca uses advanced analytics and machine learning algorithms to rapidly analyze and detect anomalies in cloud feeds, workloads, and configurations that might indicate malicious activity. By empowering teams to act swiftly on accurate and actionable alerts, the potential damage of a breach is greatly reduced.
- Orca performs continuous behavioral analysis to detect differences from baseline behavior.
- Leveraging full contextual insights into the cloud environment, Orca minimizes false positives and avoids alert fatigue.
- Orca enables teams to respond quickly and effectively by simplifying investigations and visually displaying potential attack paths.
Elevate Cloud Security with Orca AI
“During incident response, seconds matter. Security operators at most firms struggle to build, let alone maintain runbooks that can keep up with the speed of business. Generative AI and LLMs offer proven relief for these teams, so they can remain focused on what matters while continuing to raise the bar on security. Orca’s continued use of AI to power remediation shows how it can benefit security teams.”

Kathy Wang
CISO and Advisor