Web-service unpatched
Hazardous (3)
Non-platform specific
About Web Service Vulnerabilities
Software systems require updates to adapt to the changing technological dynamics, accommodate consumer needs, and most importantly, fix vulnerabilities and bugs. A vulnerability is an exploitable flaw or weakness in a service, whereas a bug is when a service isn’t functioning as it’s designed to function. Both vulnerabilities and bugs can be exploited by cybercriminals to execute various kinds of cyberattacks.
A web service is an application that’s accessible from outside the network. Web services provide a way to communicate, connect, and use an application over the internet. For example, a web service may allow an external partner to access some data stored in your internal database.
All software has the potential to have vulnerabilities and bugs, including web services. Software vendors are responsible for discovering and fixing them before they are found and exploited by malicious actors. Software consumers are in turn responsible for immediately applying these fixes, released via updates or patches.
Regardless of how rigorous your security controls are, if you don’t regularly patch your software, you are at serious risk of compromise. This is because cyber criminals like to scan and target networks with known, unpatched vulnerabilities.
Cloud Risk Description
Unpatched services, with known vulnerabilities and bugs, can be one of the main attack vectors into your system. In fact, the majority of attack paths that Orca detects and analyzes begin with an exploitation of a known vulnerability. The stakes are considerably higher if the service is web-facing, that is, accessible from outside the network. Malicious actors can exploit an unpatched vulnerability or bug to cause service downtime, cause a denial of service, or more In some cases, unauthorized remote access may also be a possibility.
How Orca Can Help
Orca creates a full inventory of your cloud environment and leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate. Orca’s workload inventory includes information on OS packages, applications, libraries, web services, as well as versions and other identifying characteristics. Unlike other solutions that simply report on the CVSS score, Orca considers the context of cloud assets, their connections and risks, to understand which vulnerabilities need to be addressed first.
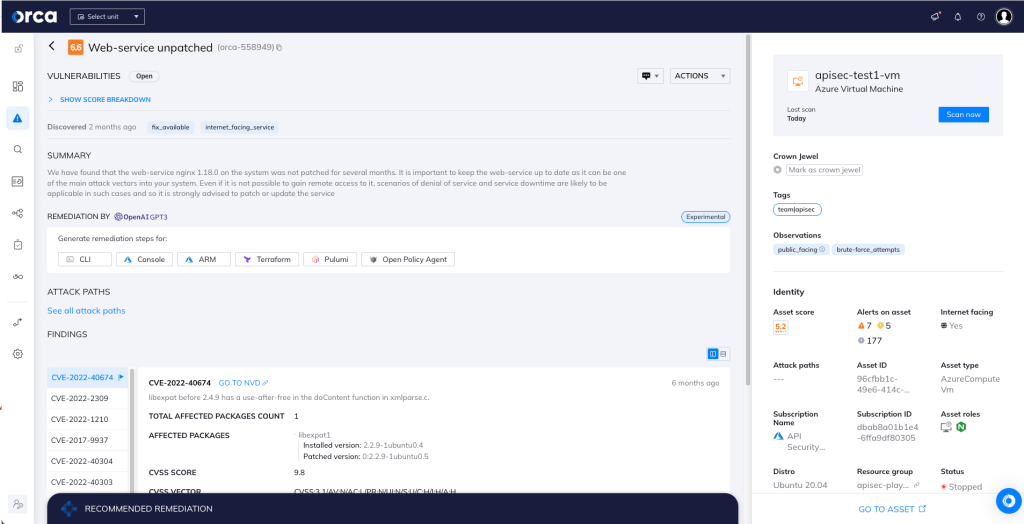
In this specific case, Orca detects an unpatched web service, and will alert on this type of issue as shown in the screenshot above.
Recommended Mitigation Strategies
-
Regularly apply software patches released by the official maintainers/vendors.
-
Ensure that all components of your web service, including the web server and third-party libraries are up-to-date.
-
Scan across your system for any applications/packages with known vulnerabilities.
-
Use a patch management system or policy to streamline the updating process.
Useful Links
- 2022 State of Public Cloud Security Report: https://orca.security/lp/2022-state-public-cloud-security-report/
- OWASP Top 10 vulnerabilities: https://owasp.org/www-project-top-ten/
- Common vulnerabilities and exposure (CVE) index: https://cve.mitre.org/
- Software security best practices: https://www.synopsys.com/blogs/software-security/top-10-software-security-best-practices/
- Risks of using unpatched software: https://www.1e.com/news-insights/blogs/5-biggest-dangers-of-unpatched-and-unused-software/
- Reasons why unpatched software is still a problem: https://searchsecurity.techtarget.com/feature/6-reasons-unpatched-software-persists-in-the-enterprise
- Patch management policy: https://heimdalsecurity.com/blog/patch-management-policy/
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
