The Challenge
Modern Applications Present Challenges to Traditional CWPP Approaches
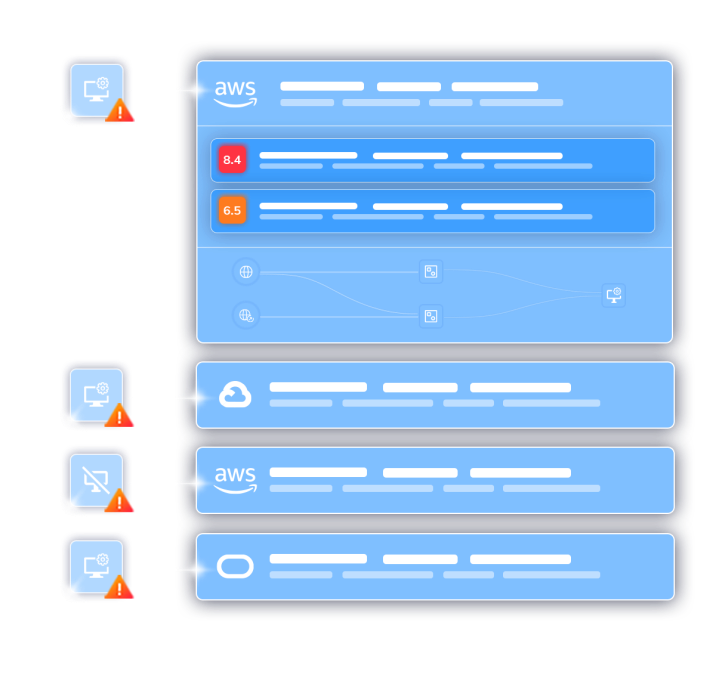
Agent-based and EDR-based CWPPs require tedious deployments and management for each workload, leading to limited visibility for security teams and high operational overhead. Vendors have tried to offer a “choice” between agents and agentless approaches, but only add to the complexity and often have hidden limits on their ‘agentless’ capabilities. In addition, CWPPs only cover cloud workloads and miss risks in the cloud control plane, such as misconfigurations and overly permissive identities.
Partial deployment of agents causes serious blind spots.
IT teams need to spend countless hours installing, configuring, and maintaining agents.
Agents and network scanners have a significant performance impact and can be a security risk.
Security teams often need to burden development and DevOps teams to install agents, creating organizational friction.
CWPPs don’t have insight into cloud configurations and identities, leaving important security gaps.
Our Approach
Complete Cloud Security for Full Stack Protection
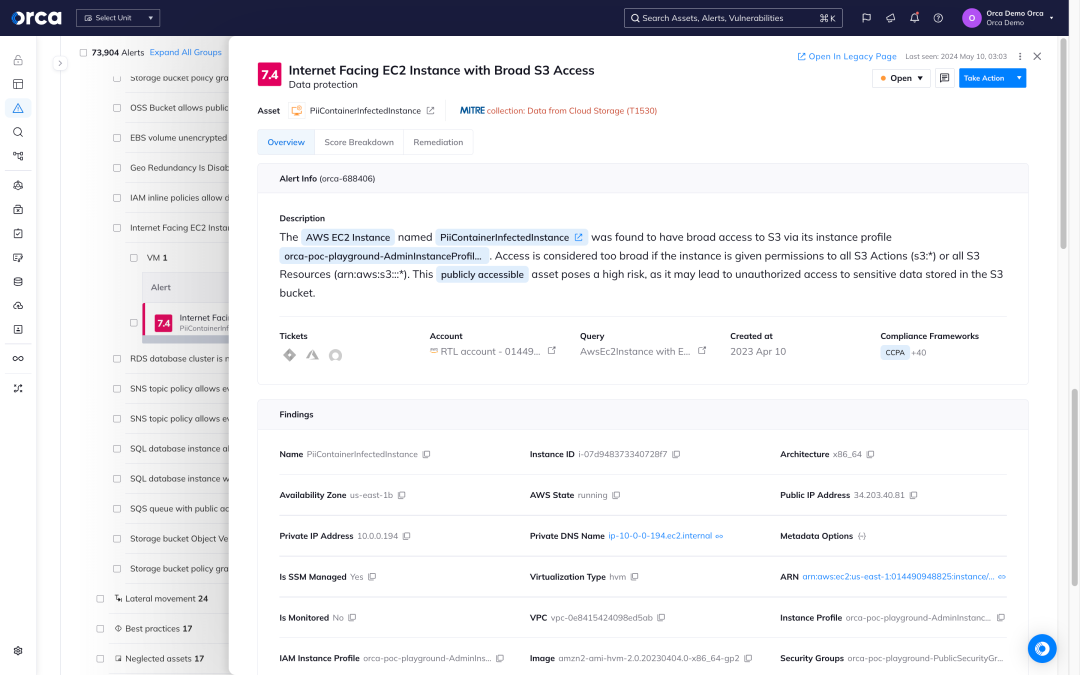
Unlike other CWPPs, Orca delivers an agentless-first approach to fully deploy in minutes with 100% coverage, and includes wide and deep visibility into risks across every layer of your cloud estate, including cloud configurations as well as workloads. Orca unifies all of your cloud security telemetry–ensuring you have the context you need to prioritize risks to your workloads and cloud native applications.
Orca collects data directly from your cloud configuration and the workload’s runtime block storage out-of-band.
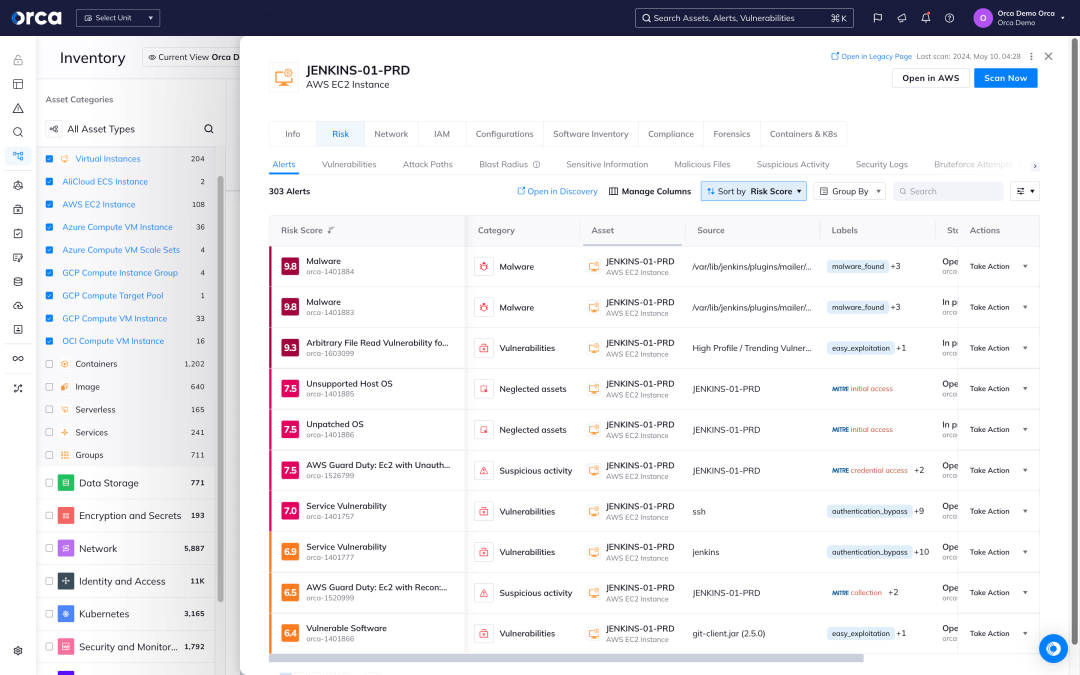
Orca quickly finds and prioritizes your most critical cloud risks, including vulnerabilities, malware, misconfigurations, lateral movement risks, IAM risks, and sensitive data at risk.
Unlike other approaches, Orca combines telemetry about your workloads with cloud configuration metadata all in one platform.
Orca’s patented SideScanning™ technology is a radical new approach that addresses the shortcomings of traditional agent-first cloud security solutions.
Cloud workload protection starts with risk prioritization
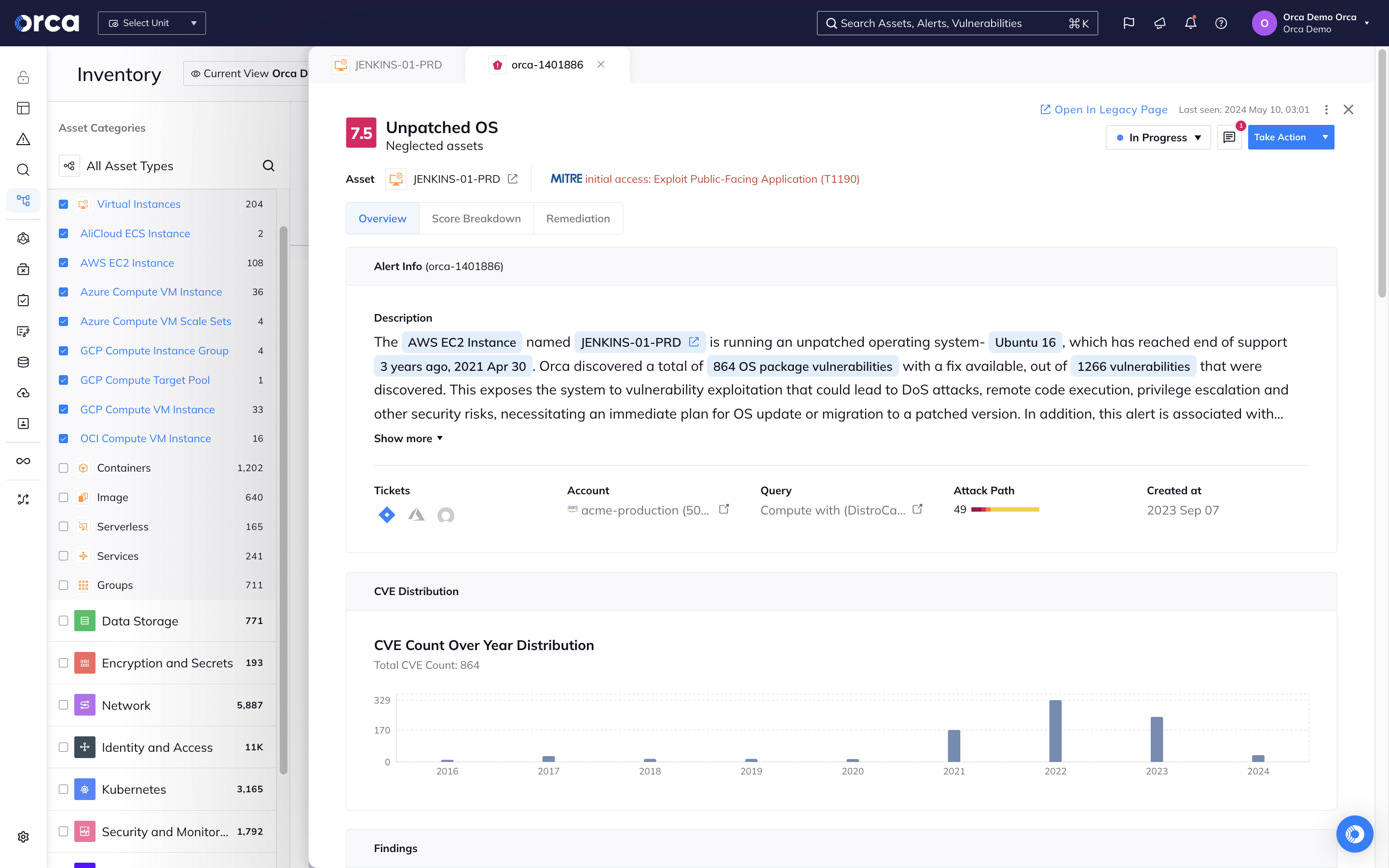
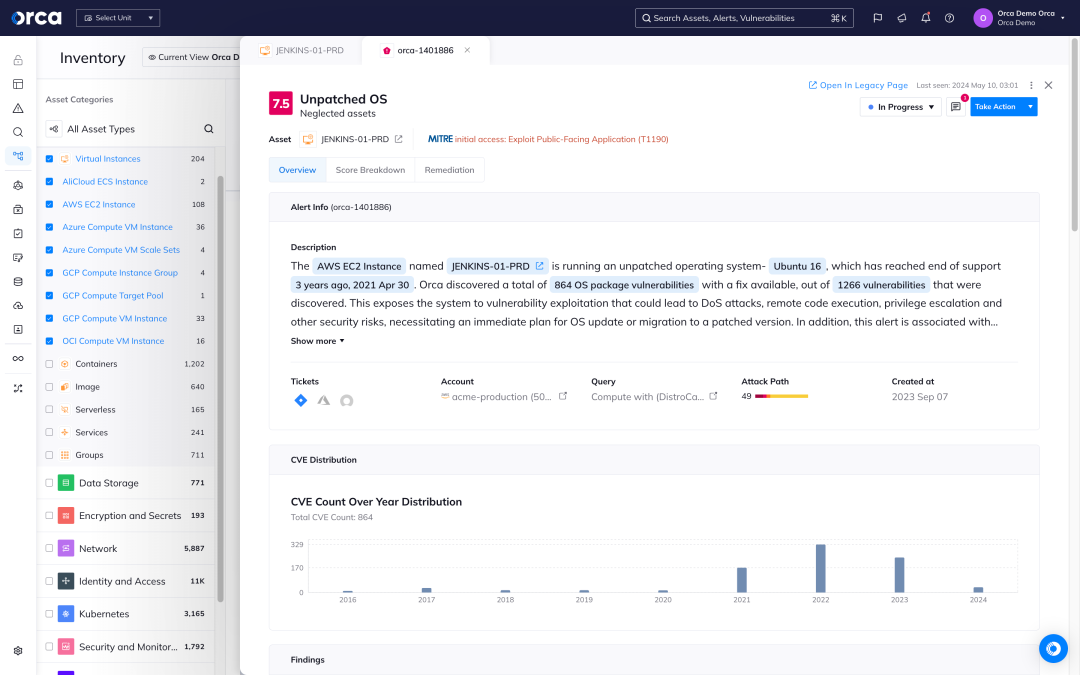
Orca identifies all your VMs, containers, Kubernetes clusters, and serverless functions and leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate.
- Orca’s workload inventory includes information on OS packages, applications, libraries, as well as versions and other identifying characteristics.
- Orca goes beyond just a mere CVSS score to consider the context of cloud assets, their connections and risks, to understand which vulnerabilities need to be addressed first.
- In rapid response situations such as Log4Shell, Orca allows you to quickly identify vulnerable cloud assets and prioritize patching the ones that pose the greatest risk to the business.
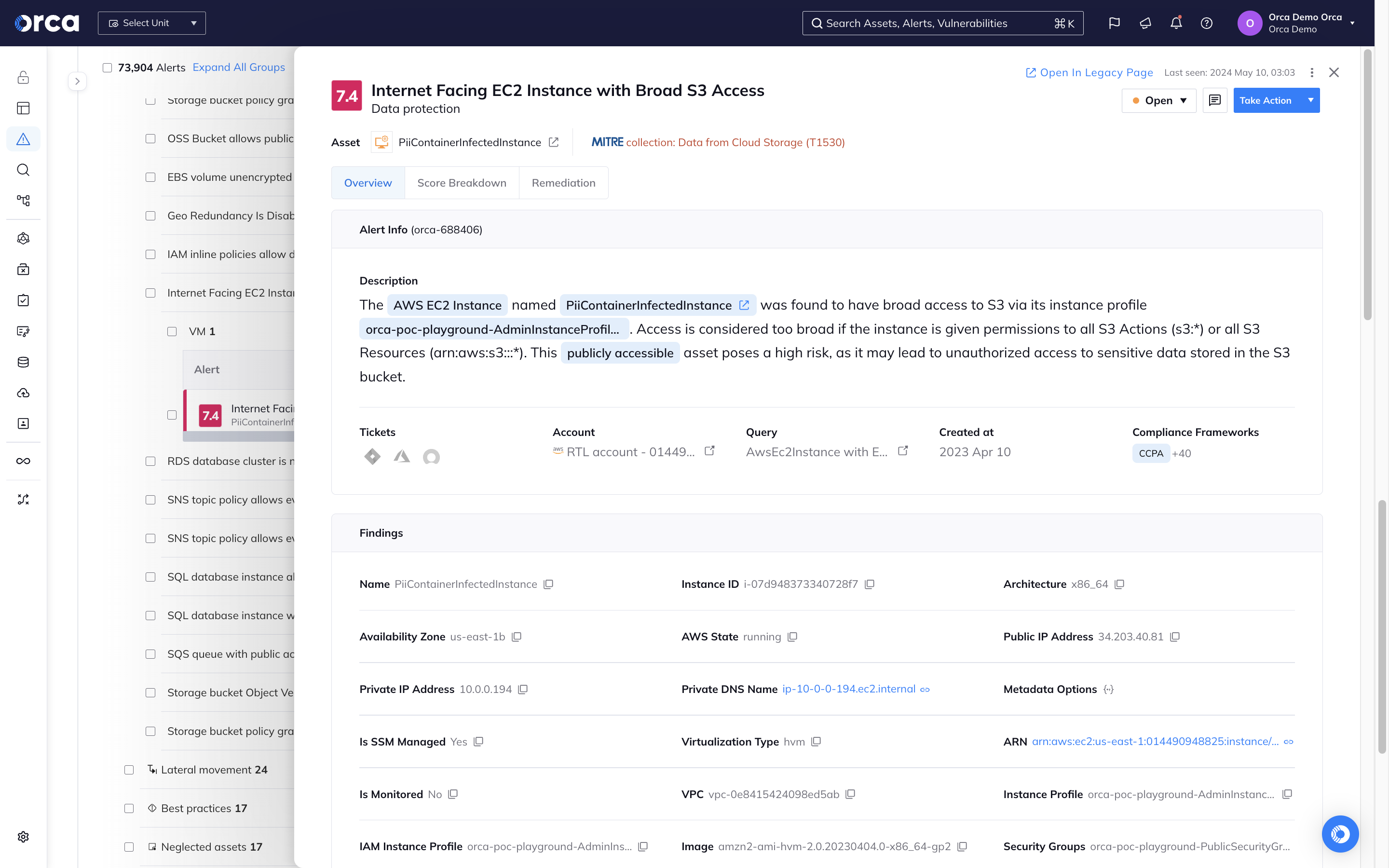
Protect your sensitive data with CWPP coverage
Orca scans the hidden corners of your cloud estate, searching for at-risk sensitive data, from personally identifiable information (PII) to protected healthcare information, and more.
- Detect at-risk sensitive data on every workload across your cloud estate regardless of whether the assets are running, idle, paused, or stopped.
- Sensitive data detection includes PII, including physical addresses, email addresses, credit card numbers, and Social Security identifiers.
- Understand which risk combinations are a straight attack path to your crown jewels.
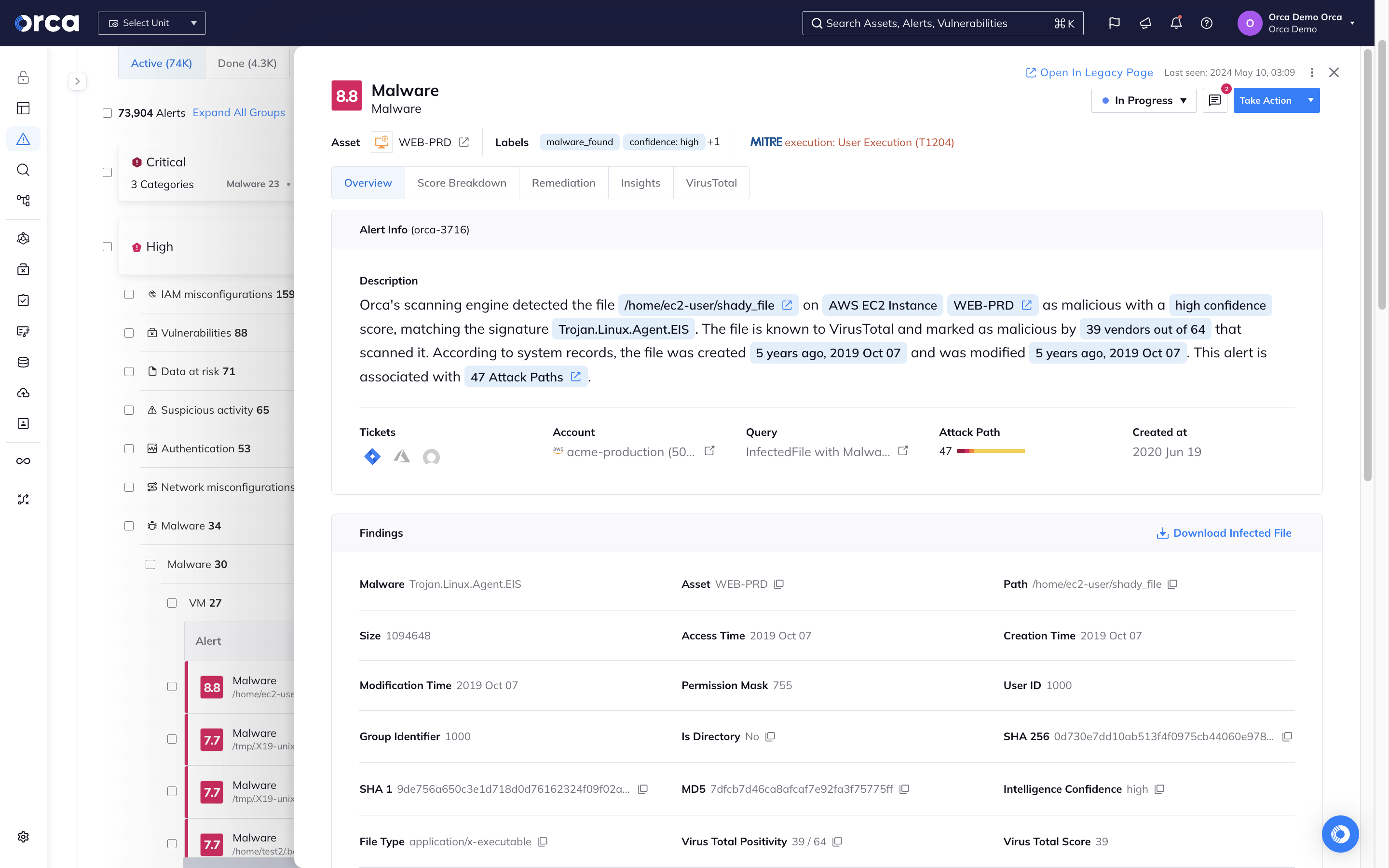
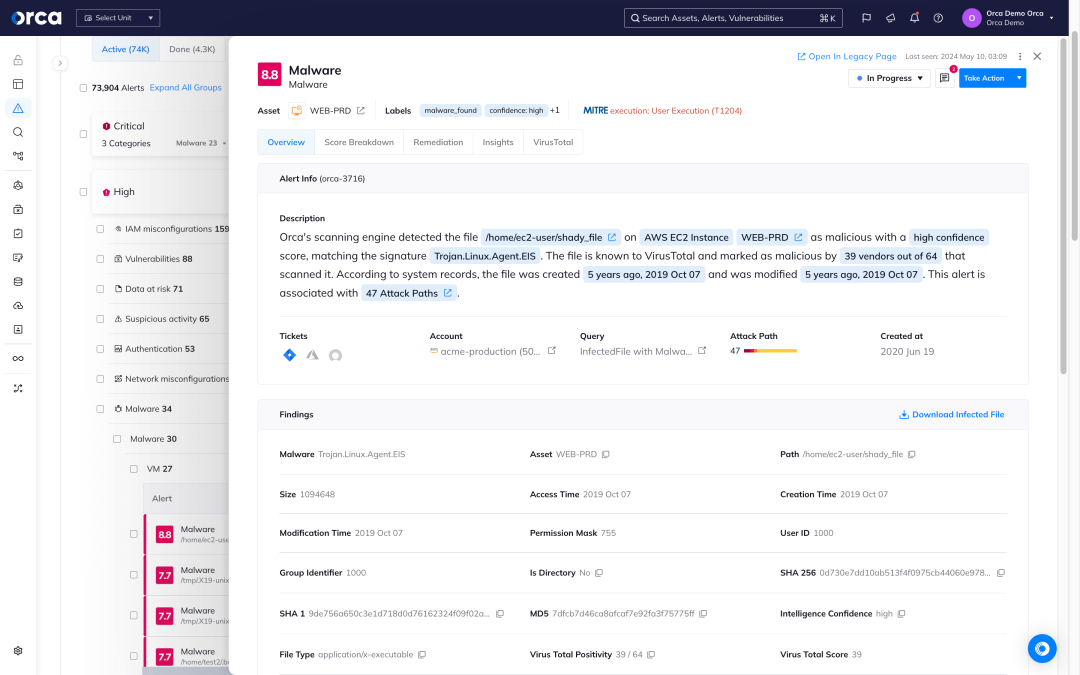
Detect known and unknown malware
Orca uses extensive malware detection techniques to locate known and potentially malicious code in your cloud workloads and resources.
- Signature-based scanning checks for file hashes of known malware.
- Heuristic file analysis closely inspects files to determine their purpose, destination, and intent.
- Dynamic scanning executes a file in a controlled virtual environment to observe its actions.
- Genetic signature detection uses previous malware definitions to discover malware within the same family.
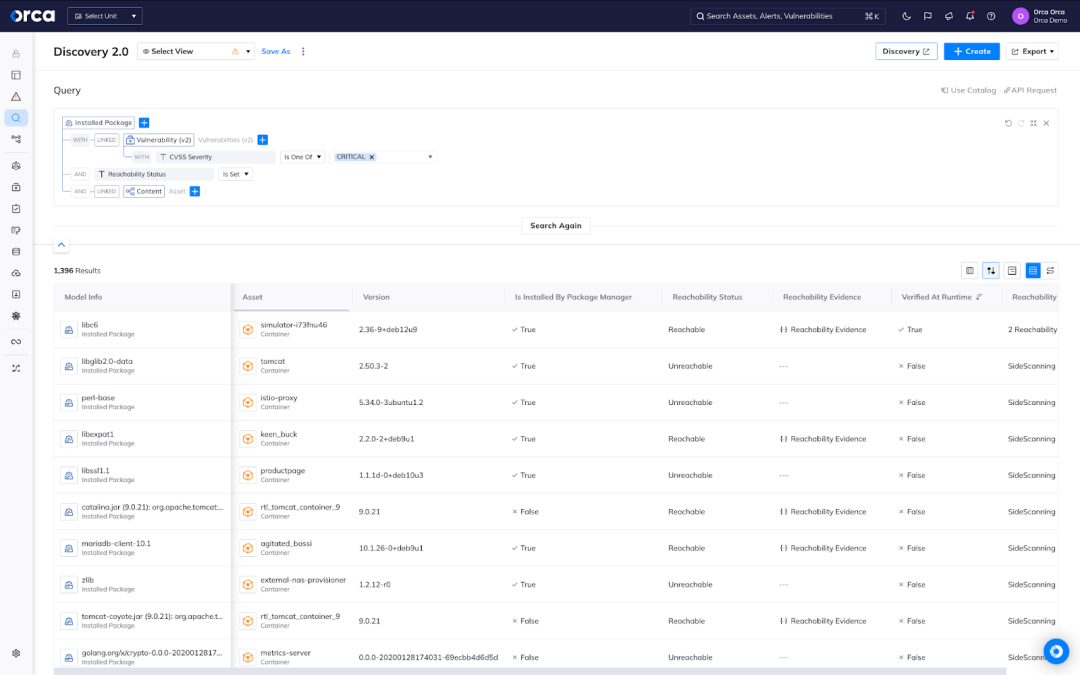
Know which vulnerable packages to fix first
Reachability analysis is the new frontier to reduce container vulnerabilities by 90%.
- Agentless Reachability Analysis out of the box – Detect which vulnerable software packages are reachable by attackers in containers detected by Orca’s SideScanning™ technology.
- Dynamic Runtime Reachability Analysis – Verify findings from our Agentless Reachability Analysis using Orca Sensor to discover which vulnerable packages are actually executed at runtime.
New
Leverage lightweight runtime protection for VMs and containers
Orca Sensor enables you to gain powerful runtime protection for your critical workloads—all from a lightweight, eBPF-based technology deeply integrated with the Orca Platform.
- Gain advanced, reliable protection with fast and simple deployments, automatic updates, and minimal maintenance for runtime security that doesn’t burden your teams.
- Get a real-time view of activity, threats, and malicious behavior flows directly from the Orca Platform.
- Leverage an extensive range of runtime detections that reinforce Orca’s comprehensive risk discovery, with the ability to build custom detections as needed.
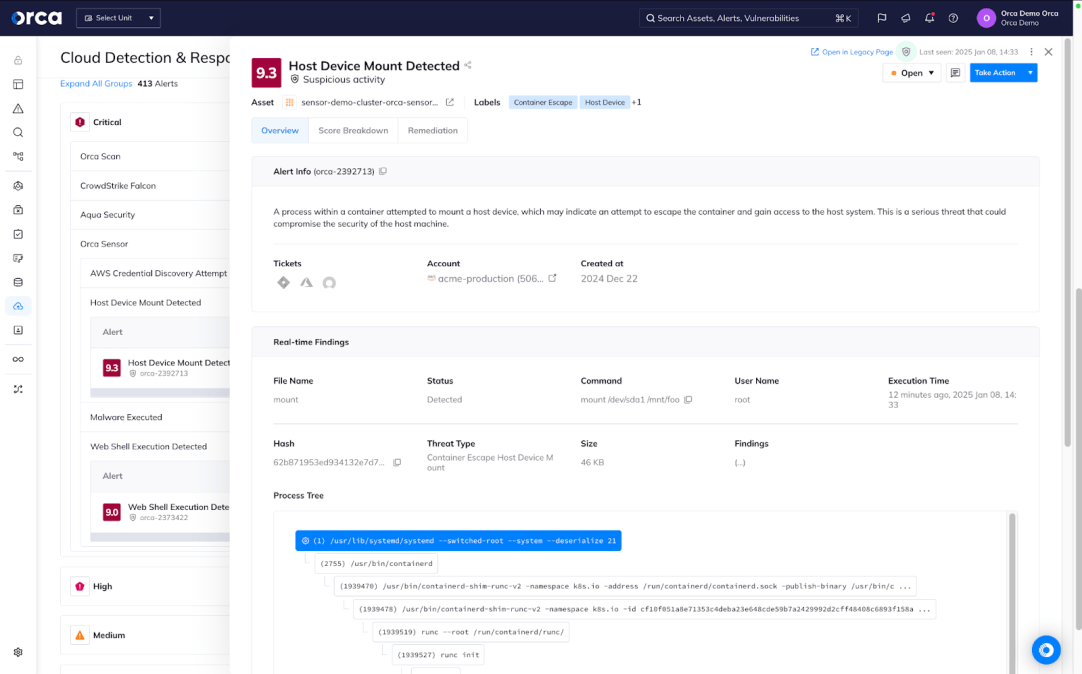
Full-Stack Cloud Visibility in Minutes
Frequently Asked Questions
A Cloud Workload Protection Platform (CWPP) is a cloud security solution dedicated to securing server workloads in the public cloud. CWPP solutions discover and detect risks in cloud workloads, including vulnerabilities, malware, and sensitive data at risk. CWPP capabilities are offered through standalone solutions or as part of cloud-native application protection platforms (CNAPP).
Public cloud services operate according to what’s called the shared responsibility model, an agreement between cloud service providers and their customers. The model makes each party responsible for certain aspects of cloud security:
- Cloud service providers are responsible for the physical access and infrastructure of their services.
- Organizations are responsible for securing the applications, services, and data they run and store on their cloud instances.
CWPP tools (either as standalone solutions or as part of a more comprehensive CNAPP) are necessary to provide visibility into and security for workloads, which are essential to meet the obligations of the shared responsibility model.
CWPPs are vital to securing cloud-native workloads. Traditional CWPPs require an agent to be installed on every asset to be monitored, which leads to incomplete coverage, high TCO, and performance degradation. However, modern CWPP solutions such as the Orca Platform provide 100% coverage of workloads without requiring a single agent.
Despite being a crucial cloud security solution, CWPP tools present important limitations, including:
- No visibility into the control plane: CWPPs only provide visibility into and security for workloads, not the cloud control plane, including misconfigurations such as publicly exposed storage buckets.
- Inability to contextualize risks: Because CWPP solutions can’t see into the cloud control plane, they also can’t account for contextual factors that may make a risk more or less severe. As a result, they can’t effectively alert teams and prioritize their efforts to focus on the most critical risks.
- Limited coverage: Traditional CWPPs are agent-based and therefore require individual agents to be installed and maintained for every cloud asset. This creates blind spots in cloud security. However modern CWPPs, such as the Orca Platform, provide instant 100% workload coverage and combine CWPP with other cloud security capabilities such as CSPM, CIEM, DSPM, and more.
- No detection for lateral movement: Without an additional solution, CWPP tools can’t identify keys that hackers could exploit to move laterally and access other assets.
Agent-based CWPPs require tedious deployments and management for each workload, leading to high TCO. Vendors offering a choice between agents and agentless approaches only add to the complexity and often have hidden limits on their ‘agentless’ capabilities. In addition, CWPPs only cover cloud workloads and miss risks in the cloud control plane, such as misconfigurations and overly permissive identities.
This limited visibility impacts the tool’s ability to provide full security coverage and effective alert prioritization. Any risks due to cloud misconfiguration (such as MFA not being enabled for the ‘root’ user account or KMS encryption keys not being rotated) cannot be detected by a CWPP. This lack of visibility also means CWPPs lack the context necessary to understand the full implications of a security issue and are therefore unable to prioritize alerts based on environmental context. This causes “swivel chair” alert triage, which leads to alert fatigue.
The Orca Platform provides full-stack visibility of your cloud estate, spanning the cloud infrastructure, OS, application, and data layers, without requiring a single agent and providing instant and continuous 100% coverage of your cloud assets.