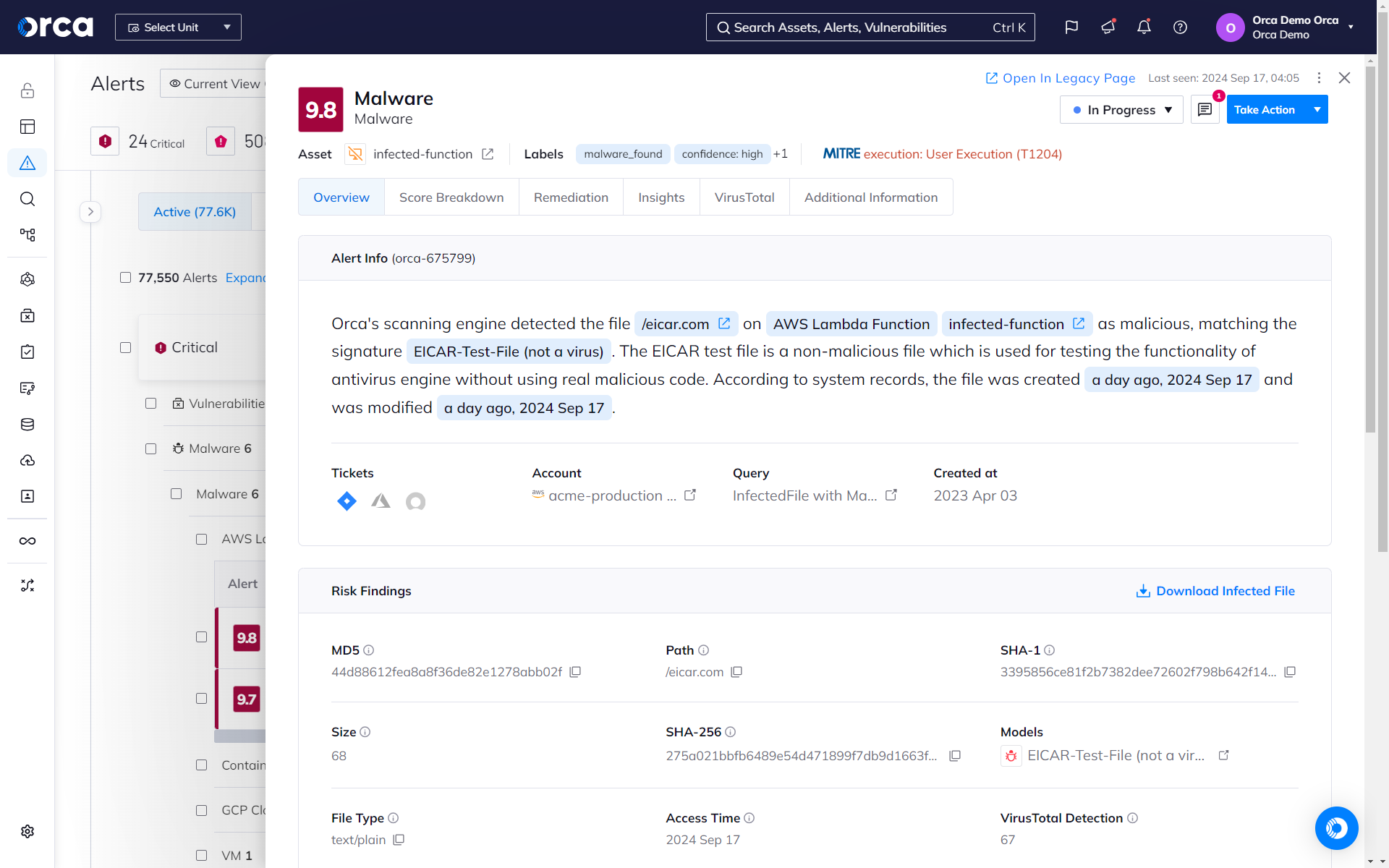
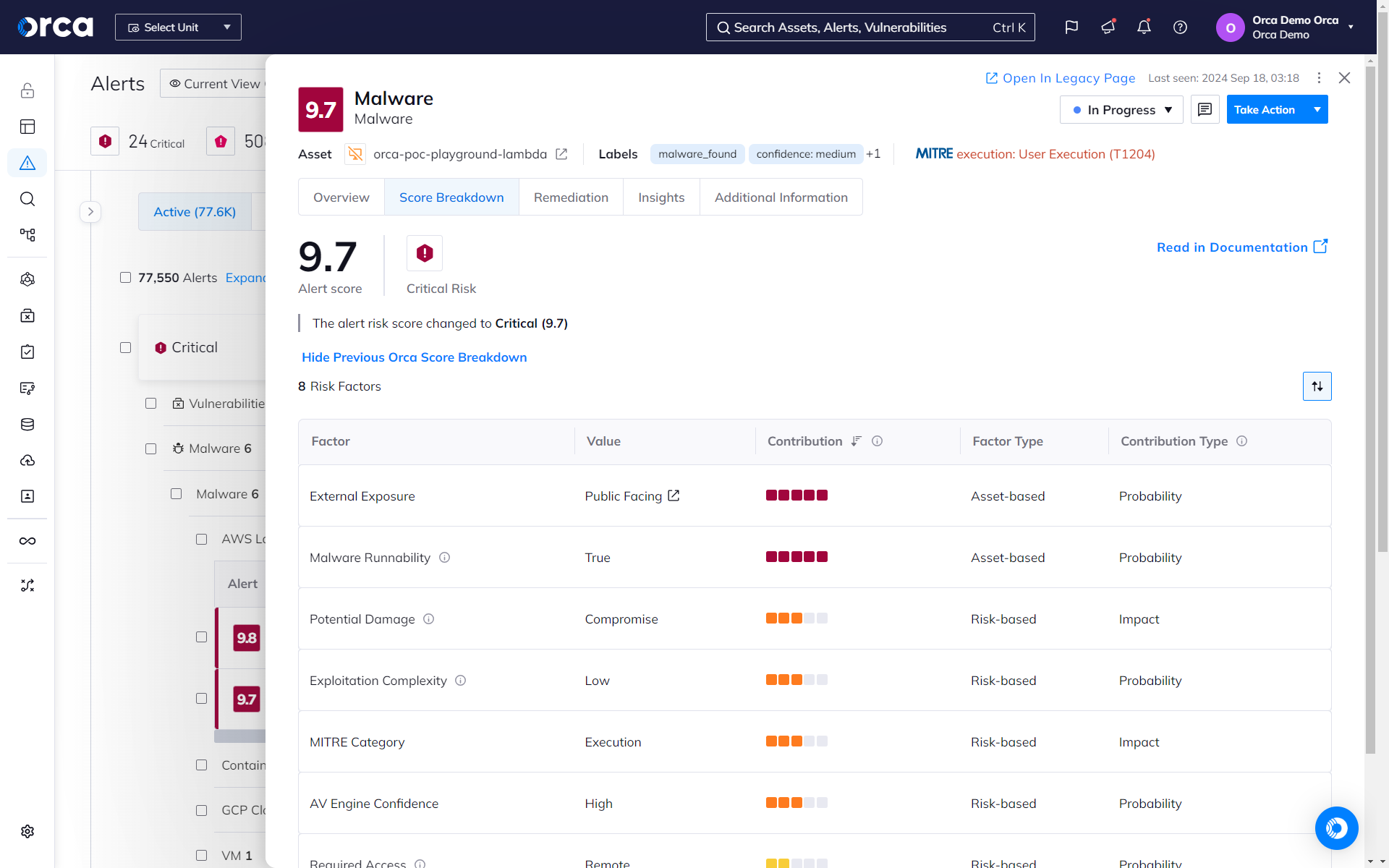
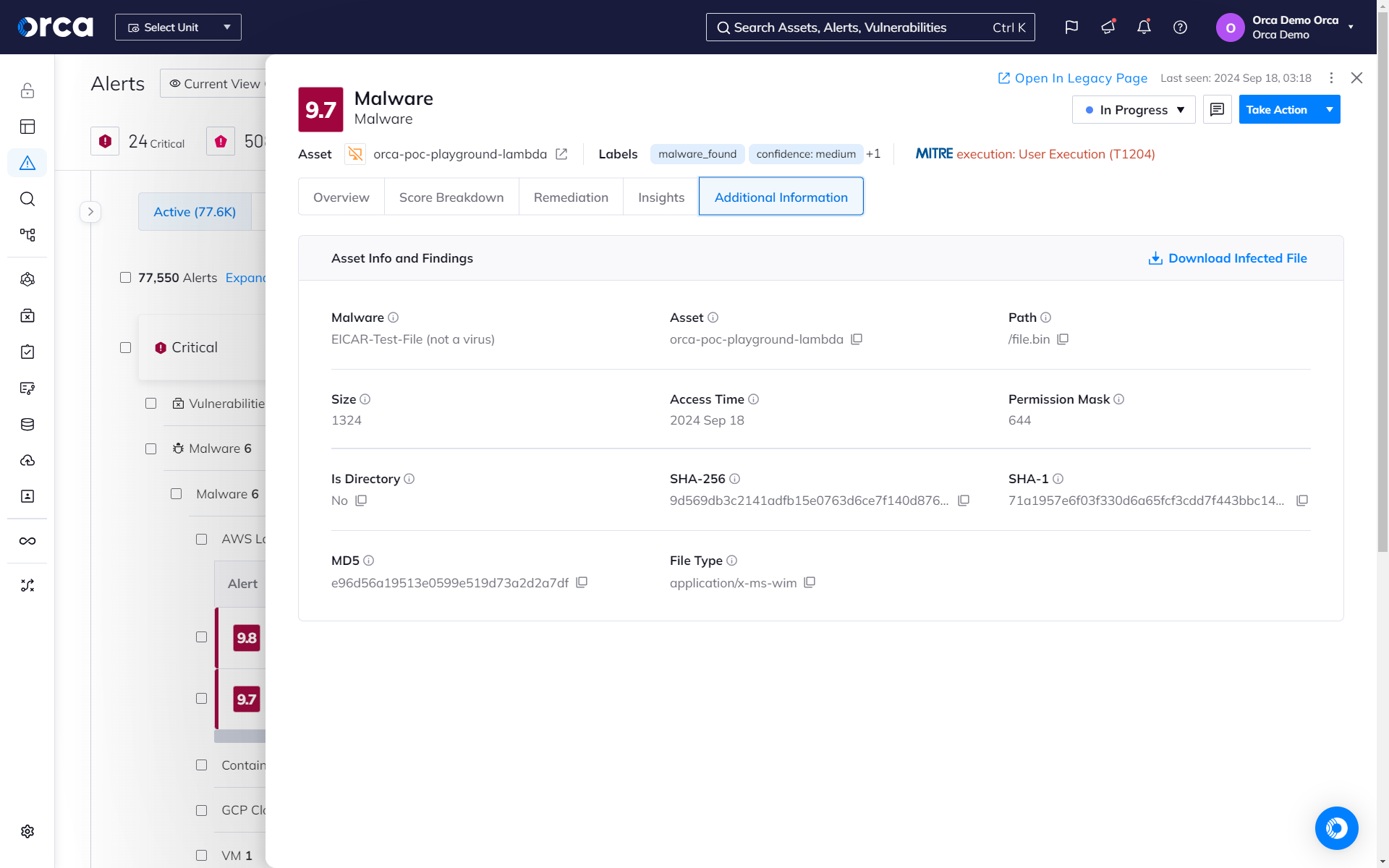
Agentless Malware Detection
Orca’s agentless SideScanning™ Technology performs signature-based and heuristic malware scanning with no impact on cloud workloads to effectively detect and prioritize malware on AWS, Azure, and GCP.
The Challenge
Cloud malware detection with agents doesn’t work
For malware detection to be effective, cloud assets must be completely and regularly scanned without impacting performance. Agent-based solutions are resource intensive and don’t scale well in the cloud, allowing threats to go undetected.
- Agent-based malware scanning impacts cloud workload performance.
- Less than 50% of cloud assets are covered by legacy security solutions.
- Relying on agent-based tools to detect malware requires ongoing maintenance for every asset deployed in your cloud.
Our Approach
Orca solves malware detection in the cloud
Orca’s agentless approach to cloud malware detection ensures complete and continuous coverage of 100% of your cloud estate with no performance impact.
Deploy once—
secure forever
Orca provides comprehensive and continuous malware coverage for your cloud assets with no impact on performance—covering even your idle, paused, and orphaned systems.
- Orca’s agentless SideScanning technology examines cloud workloads for malware out-of-band, eliminating the performance impact and operational overhead of agents.
- Orca takes snapshots from outside of your running environment and scans cloud assets for malware so there’s no need to schedule downtime, no risk to operations, and no impact to data.
- Ensure continuous compliance with regulations and standards that require malware detection.
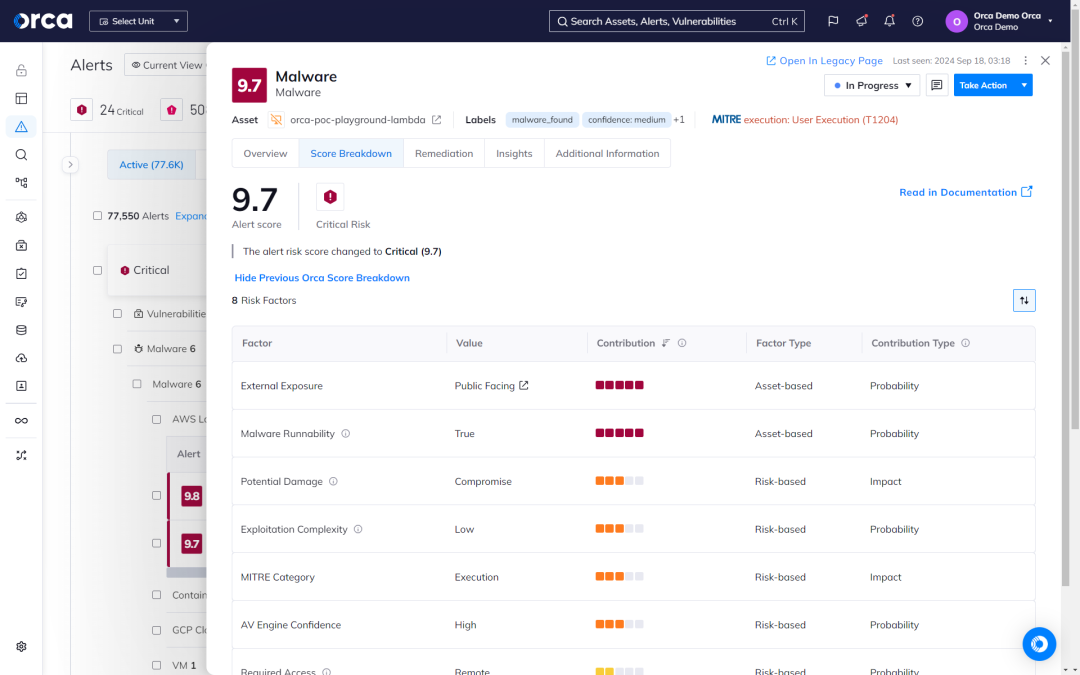
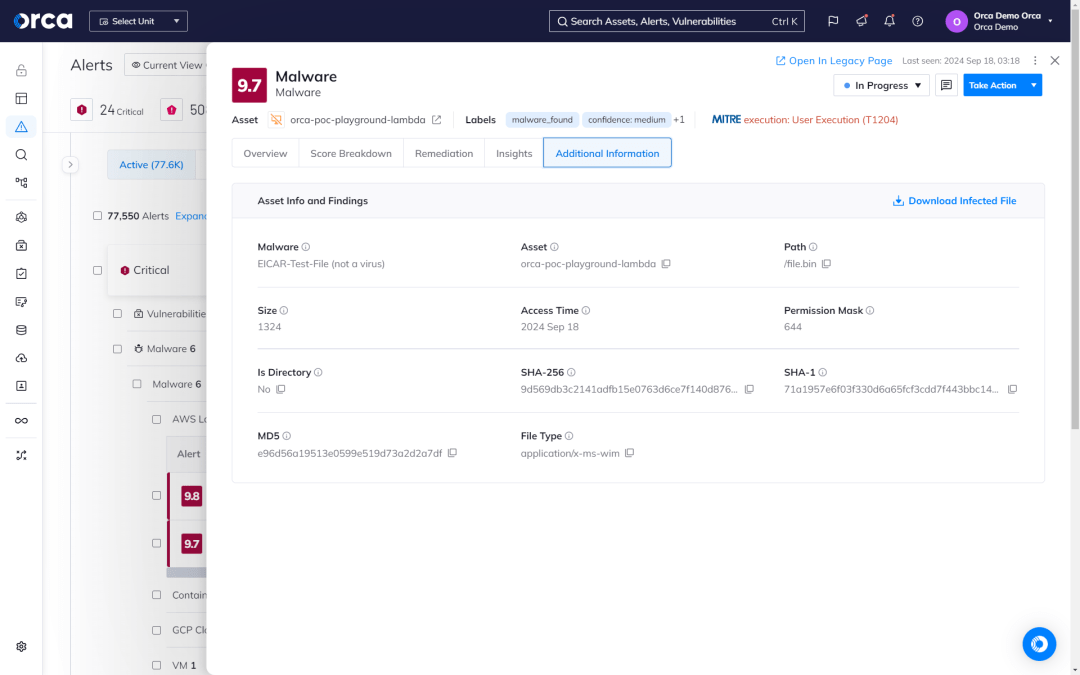
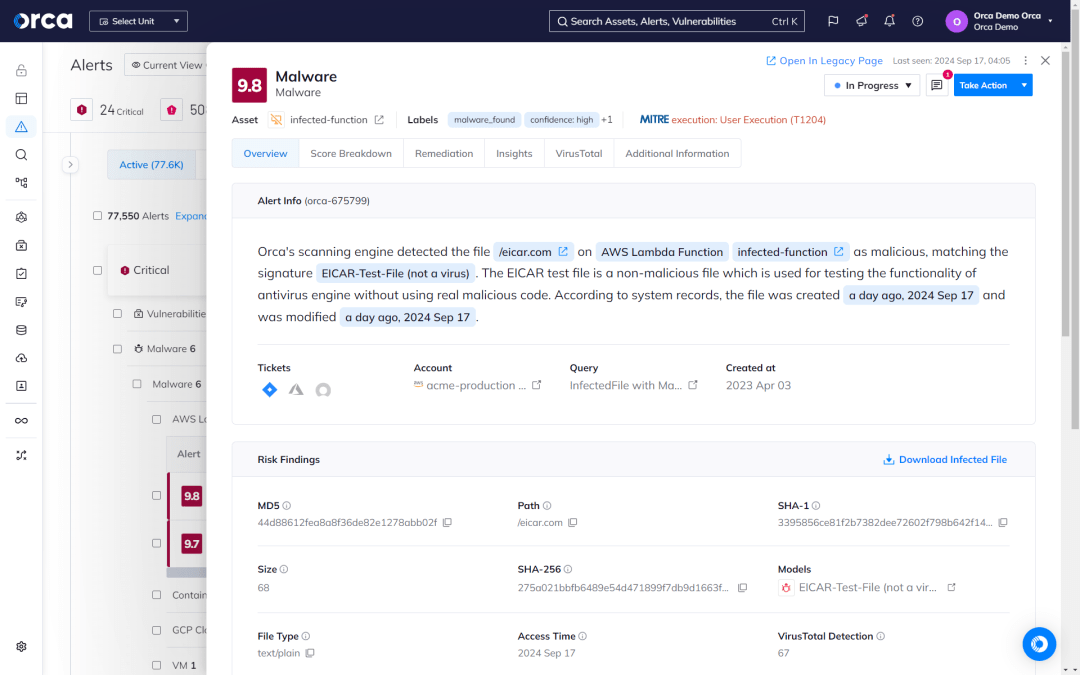
A multi-pronged approach to malware detection
Orca uses SideScanning in conjunction with a variety of malware detection techniques to locate known, unknown, and potentially malicious code in your cloud workloads and resources, such as storage buckets.
- Signature-based scanning looks for file hashes (signatures) of known malware.
- Heuristic file analysis closely inspects files for suspicious properties and behaviors, detecting known and unknown malware including polymorphic and metamorphic variants
- Dynamic scanning executes a file in a controlled virtual environment to observe its behavior.
- Genetic signature detection and YARA rules use previous malware definitions and patterns to discover malware within the same family.