How Orca Security Compares to Lacework
Simple deployment, comprehensive visibility
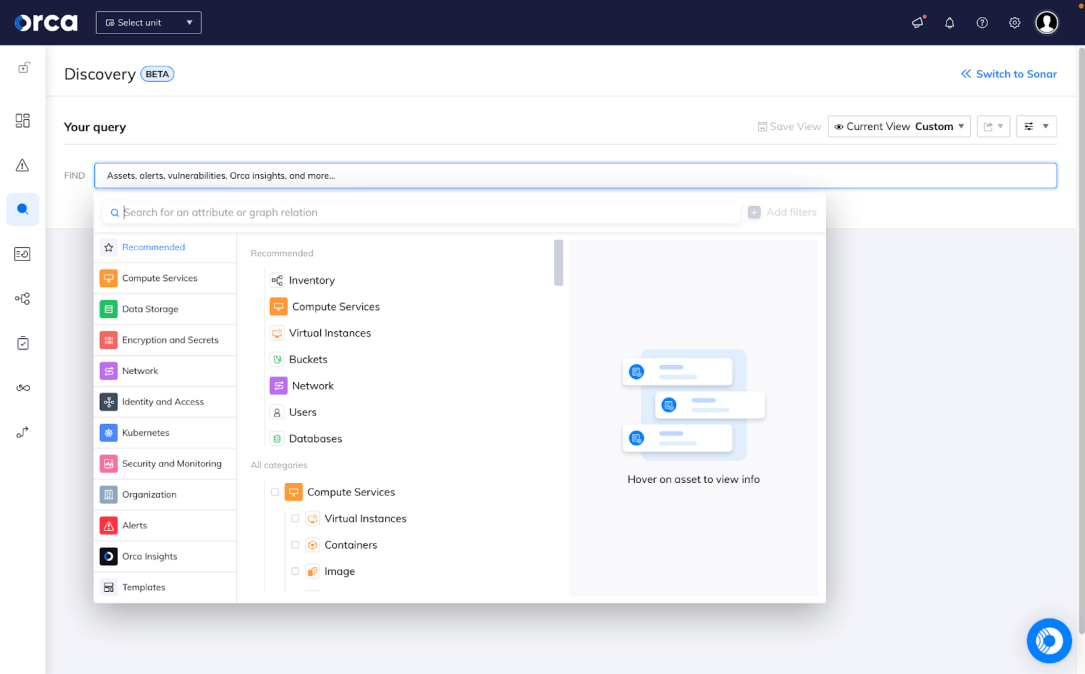
With Orca Security, a simple, 3-step configuration enables you to get up & running quickly. Our agentless approach ensures that all the workloads in the cloud account are discovered and assessed without having to deploy additional agents or configure additional scanners. Within hours, you have visibility that goes broad & deep while providing context that shows how an attacker might connect the disparate pieces from an exposed endpoint to critical data.
Lacework requires a complex array of configurations and agent deployments to get full functionality, making it more difficult and expensive to fully deploy.
The agentless security pioneer
Orca’s patent-pending SideScanning technology quickly and easily scans all of your Linux and Windows workloads, including cloud VMs, containers and Kubernetes applications, and serverless functions. Lacework provides an agentless approach to vulnerability scanning but requires several agents to be deployed to get full functionality, complicating deployment and maintenance. Orca provides you with instant-on security and complete coverage for all your workloads and applications that Lacework can’t match. Within the Orca UI, you can view detailed risk prioritization information about all of your assets with context to understand your greatest risks and the impact to your business.
Advanced functionality from the innovation leader
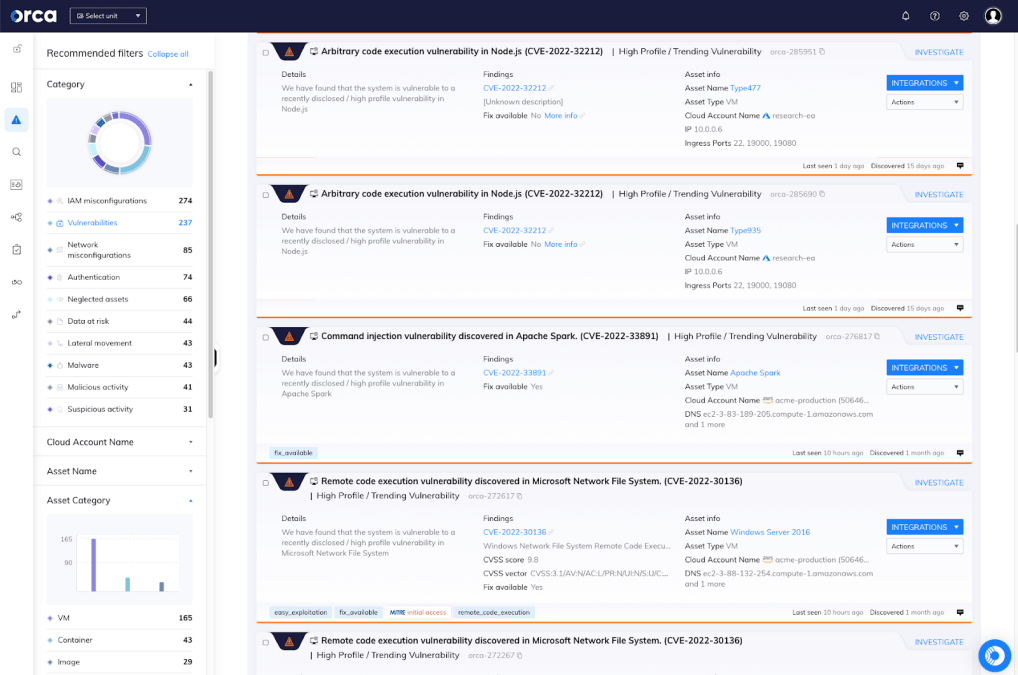
Orca Security goes beyond basics with advanced capabilities such as Cloud Infrastructure Entitlement Management, enabling you to find identity misconfigurations, and API Security, adding visibility into all your deployed API endpoints. You get more context and better intelligence about your cloud environments without having to buy & deploy additional products.
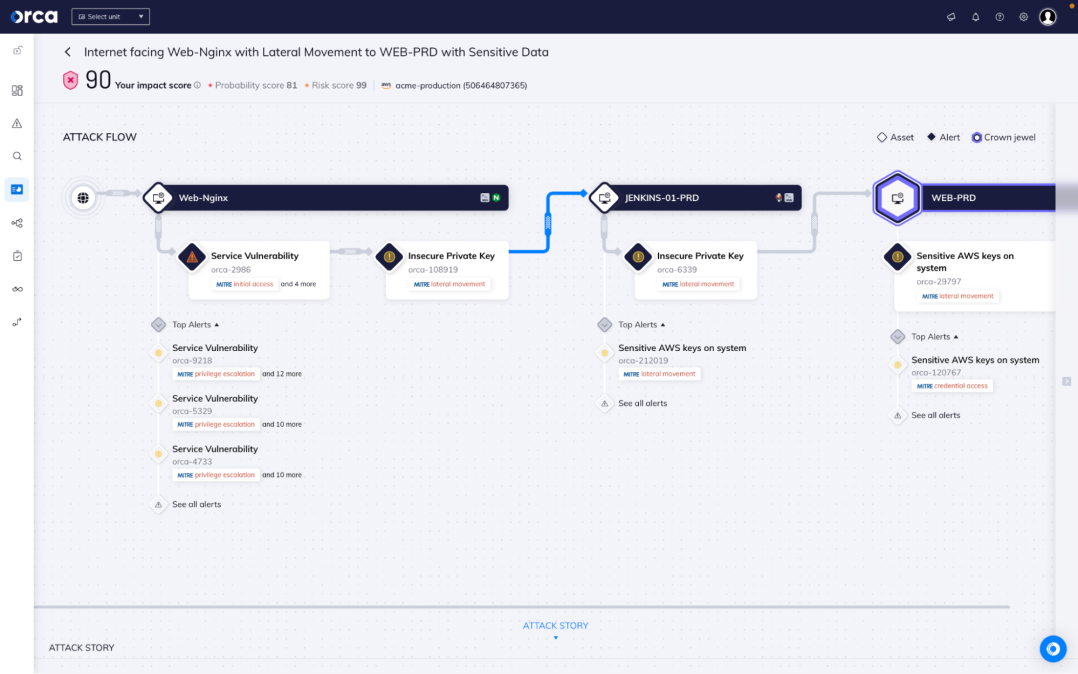
Target critical risk with attack paths
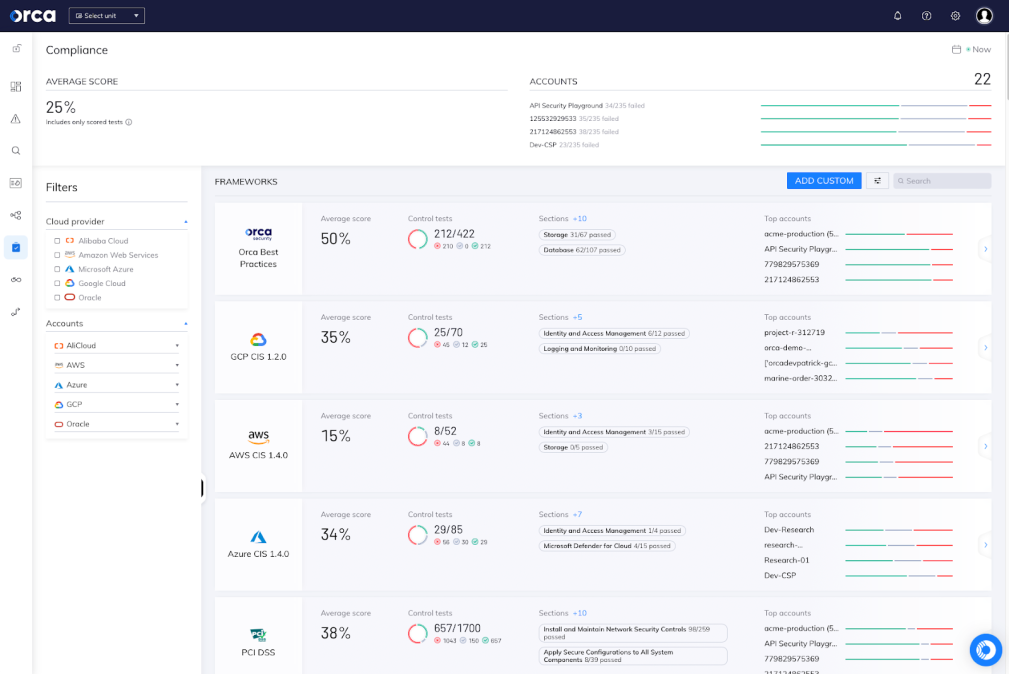
Orca supports over 100 compliance frameworks, as well as our own Orca Best Practices and custom frameworks. This ensures that you can view compliance in a single dashboard and report covering your cloud infrastructure, data, identities, workloads, and more.
Features

Deployment
Simple Onboarding
Simple 3-step activation model scans your cloud accounts, assets, workloads, data, and identities across multiple clouds without having to deploy agents
More Friction
Requires configuration of a mix of cloud service configuration, agentless configuration (for AWS EC2 only), and multi-step agent configuration for different platforms, requiring far more planning & investment to deploy
Compliance
Comprehensive
100+ compliance frameworks covering CIS, NIST, and industry-specific standards with all data and policies shown in a single dashboard for seamless reporting
Limited
Far fewer compliance reports available means compliance teams will spend more time answering questions & completing audits.
Attack Path Analysis
Automated and Interactive
Interactive dashboard, with automated impact score, surfaces toxic combinations of risks so teams can prioritize and fix the top 1% of issues. All risks mapped to the MITRE ATT&CK framework
Limited and Fragmented
Supports generating attack paths only for AWS EC2 instances, no centralized dashboard to investigate attack paths
PII detection
Seamless and Comprehensive
Automatic detection of PII across all cloud resources
None
No classification of data, making it far more difficult to find critical risks
Malware scanning
Robust
Signature and heuristic-based detection efficiently identifies malicious files present even when not executed
No Malware Detection
No scanning for known malware