Table of contents
Gartner estimates spending on cloud security solutions will increase 24% in 2024, more than any other segment in the global security and risk management market. Spurring this growth is the rise in demand for cloud computing. By 2027, the company predicts that more than 70% enterprises will depend on public cloud platforms to support their innovation, up from just 15% in 2023.
The growing marketplace for cloud security solutions is vast and complex. Organizations looking to secure their cloud estates must navigate an abundance of solutions, acronyms, and vendors. This can make finding the right solution challenging, requiring a nuanced understanding of each technology, including its key features, capabilities, and limitations.
In this post, we guide you through today’s cloud security solutions, including what they do, why they matter, and how to choose the right one for your organization.
Understanding cloud security solutions
Before we examine the different types of cloud security solutions, let’s get a foundational understanding of cloud security and why it remains essential for organizations investing in cloud computing.
What is cloud security?
Cloud security is a collection of strategies, technologies, and practices designed to protect the integrity, confidentiality, and availability of cloud data, resources, and services. Generally, it involves inventory and asset management, continuous monitoring, comprehensive risk detection, risk prioritization, risk remediation, and compliance.
Cloud security solutions play an essential role in helping organizations fully secure and protect their cloud environments. Unlike traditional on-premise environments, cloud environments are highly dynamic and distributed, making visibility, continuous monitoring, and risk detection challenging and essential. The self-service nature of these environments mean users can easily spin up and turn down resources, expanding the attack surface and easily creating risks such as misconfigurations.
Cloud security solutions help organizations understand the resources and risk in their environment, detect and prioritize their risks, and remediate issues before they can become security incidents.
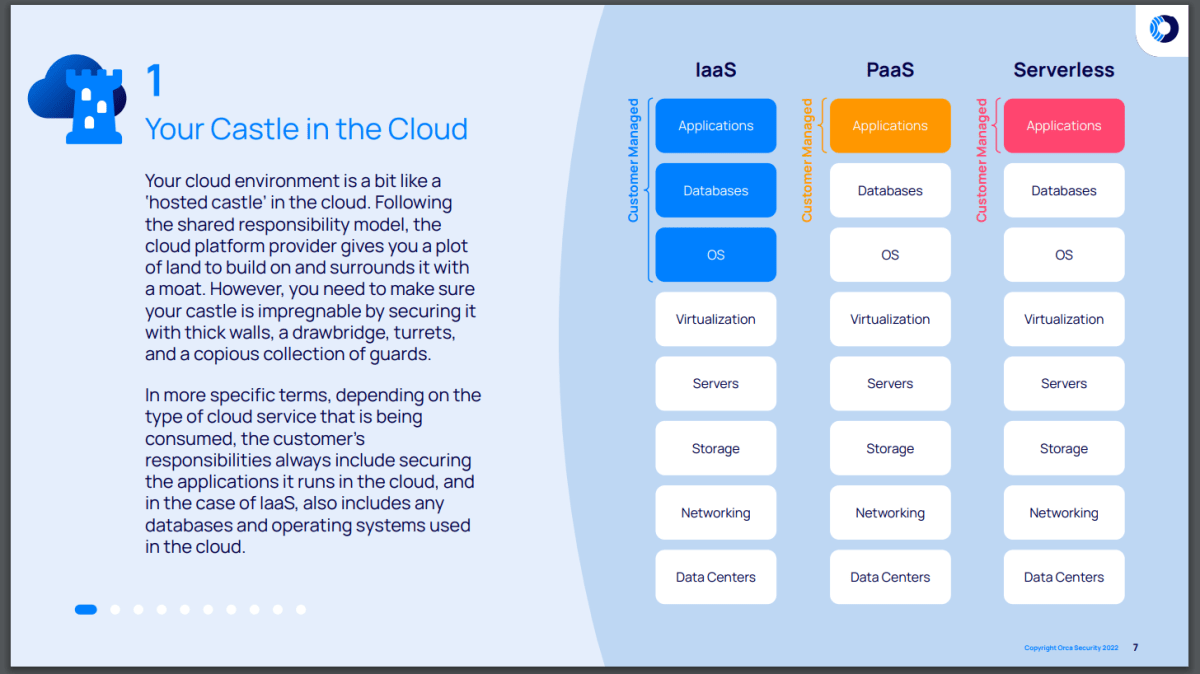
The Shared Responsibility Model
The Shared Responsibility Model is an established agreement between an organization and cloud service provider (CSP) that determines each party’s responsibility for securing the cloud and everything stored or running within it. The model creates a system of accountability and spreads the burden of security across both the CSP and organization.
The Shared Responsibility Model depends on the type of cloud computing service provided by a CSP to an organization. They include the following:
- Infrastructure-as-a-Service (IaaS): The CSP provides compute, networking, and storage resources on-demand to an organization, which they pay for based on utilization. In this arrangement, the CSP is responsible for securing the infrastructure (data centers, storage, servers, virtualization) of the cloud, leaving organizations responsible for securing their applications, databases, and operating systems.
- Platform-as-a-Service (PaaS): The CSP provides the same services as IaaS, but also database management systems, development tools, and more. PaaS is a service model designed to support the full application lifecycle, where organizations pay for using cloud resources. In this model, organizations are only responsible for securing the applications and services they develop, leaving all other obligations to the CSP.
- Software-as-a-Service (SaaS; serverless): The CSP provides both IaaS and PaaS, as well as a cloud-based application that organizations pay to use. The CSP manages the full SaaS offering and is responsible for securing it. However, the organization must secure their configurations and data.
Types of cloud security solutions
Cloud security depends on multiple solutions designed to address one or more of its areas. In this section, we briefly examine each of these solutions, including their major features and benefits.
- AI Security Posture Management (AI-SPM): Enables organizations to effectively secure the AI services, models, packages, and other resources used in the cloud. AI-SPM addresses a variety of security risks related to AI usage, including misconfigurations, vulnerabilities, sensitive data risk, and more.
- API Security: Protects APIs from threats, vulnerabilities, misconfigurations, exposures, and other risks. It uses technology to continuously inventory APIs (including shadow APIs), and detect and remediate API risks.
- Cloud Infrastructure Entitlements Management (CIEM): Manages access rights and permissions for cloud resource entities. CIEM (pronounced “KIM”) solutions enable organizations to implement the principle of least privilege (PoLP), which ensures users only get access to the resources they strictly need to perform their jobs.
- Cloud Detection and Response (CDR): Focuses on detecting cloud attackers who have breached the security controls of cloud resources and applications. CDR solutions provide continuous monitoring and alerting of malicious activity in cloud environments, enabling security teams to investigate and respond to in-progress cloud attacks.
- Cloud Native Application Protection Platform (CNAPP): Provides full coverage of multi-cloud environments, comprehensive risk detection, effective risk prioritization, remediation, and more. A newer alternative to previous cloud security products, CNAPPs consolidate several point solutions in cloud security and unify their capabilities in one platform, including each one included in this list.
- Cloud Security Posture Management (CSPM): Facilitates the detection and remediation of risks and any misconfigurations and compliance violations in cloud infrastructure, enabling organizations to reduce their attack surface.
- Cloud Workload Protection Platform (CWPP): Focuses on securing server workloads in the public cloud. CWPP solutions discover and detect risks in cloud workloads, including vulnerabilities, malware, at-risk sensitive data, and more.
- Container and Kubernetes Security: Enhances the security of containers and Kubernetes deployments by implementing continuous monitoring, secure cluster configurations, access controls, container image security, and network security.
- Data Security Posture Management (DSPM): Detects sensitive data, such as PII (Personal Identifiable Information), PHI (Personal Health Information), financial data, intellectual property, and more, and analyzes and remediates any associated security risks and compliance issues.
- Multi-Cloud Compliance: Enables organizations to adhere to regulatory and voluntary standards by identifying, monitoring, remediating, and reporting on cloud security risks on a continuous basis.
- Shift Left Security: Incorporates security and testing into the early phases of the software development lifecycle (SDLC). This includes Infrastructure-as-Code (IaC) Security, secrets detection, Software Composition Analysis (SCA), Static Application Security Testing (SAST), container image scanning, as well as Source Code Management Posture Management (SCM-PM) capabilities.
- Vulnerability Management: Identifies, analyzes and helps remediates issues in cloud infrastructure, services, and applications that attackers can exploit. It focuses on early vulnerability detection and mitigation, as well as software hardening.
AI Security Posture Management (AI-SPM)
AI Security Posture Management (AI-SPM) enables organizations to securely leverage AI models and Large Language Models (LLMs) in their business. It involves several important activities to protect against AI risks across the application lifecycle. They include:
- Scanning the entire cloud estate and inventorying all AI models and packages deployed in the cloud.
- Ensuring the configuration of AI services, models, and packages are properly secured, including those pertaining to network security, data protection, access controls, and IAM.
- Detecting sensitive data in AI models or training data and generating alerts.
- Detecting secrets and access keys stored in code repositories and generating appropriate alerts.
- Facilitating the remediation of AI risks, both in cloud and development environments.
API Security
API Security calls for adopting technology that allows organizations to implement and sustain a strong API management framework. APIs are a top attack vector for data breaches in enterprise web applications. API Security focuses on several important practices, including:
- Discover and inventory APIs.
- Detect and remediate API risks.
- Support API Security at runtime.
- Encrypt API requests and responses.
- Implement API gateways.
- Implement access controls.
- Identify vulnerabilities.
- Use quotas and throttling.
- Validate API parameters.
- Build threat models.
Cloud Detection and Response (CDR)
CDR helps organizations gain the visibility and awareness of in-progress cloud attacks, accelerate and enhance their response, and limit the scope and severity of incidents. CDR provides capabilities focused on four stages of detection and response:
- Detection: Continuous monitoring and alerting of attacks across cloud services.
- Investigation: Detailed insight into malicious activity, timeline of events, and forensics to determine appropriate response.
- Response: Capabilities that contain and neutralize cloud threats, including in-progress attacks.
- Resilience: Insights and capabilities that facilitate post-mortem investigation and remediation. This includes patching, encryption, enforcing stricter IAM policies, and other activities that harden the cloud environment.
Cloud Infrastructure Entitlements Management (CIEM)
CIEM enables organizations to successfully manage identity and resource access across rapidly changing cloud environments. The solution strengthens cloud security posture and offers benefits such as compliance assurance, scalable entitlements visibility, cloud permission rightsizing, and automated detection and remediation of access risks.
CIEM solutions continuously scan cloud environments and detect the following risks:
- Privileged roles with cross-account trust.
- Inactive Identity and Access Management (IAM) roles with admin privileges.
- Unattached privileged policies.
- Privileged inactive identities.
- Most active roles with cross-account trust.
- Compromised assets with privileged IAM permissions.
Cloud Native Application Protection Platforms (CNAPPs)
CNAPPs have emerged to address the challenges of using siloed traditional cloud security solutions. CNAPPs offer several advantages, including improved cloud risk management, comprehensive cloud visibility, lower total cost of ownership and licensing costs, enhanced compliance, and support for DevSecOps (i.e., Shift Left Security). CNAPP combines the capabilities of CSPM, CWPP, CIEM, DSPM, API security, and more.
CNAPPs perform the following activities to provide complete visibility, coverage, and protection:
- Provide a full and continuous inventory of cloud assets and applications.
- Identify all risks and compliance issues in the cloud environment, create alerts, and prioritize issues for remediation.
- Continuously monitor the cloud environment to discover new assets, issues, and risks.
- Integrate security, DevOps, and developer tools to streamline and enhance workflows.
- Generate reports to assist with compliance efforts, internal and external communications, and other purposes.
For example, the Orca Cloud Security Platform is an agentless-first, natively developed CNAPP that provides full coverage of multi-cloud estates combined with comprehensive risk detection. The solution detects security risks at every layer of your cloud estate, prioritizes the most critical risks, and provides teams multiple options for fast, efficient, and simple remediation.
Cloud Security Posture Management (CSPM)
CSPMs help protect against cloud misconfigurations, including unrestricted access controls, mismanaged secrets, unreviewed default values, and more. They help security teams remediate misconfigurations and maintain compliance by monitoring the cloud control plane and ensuring that it aligns with defined security policies. Organizations use a CSPM to:
- Maintain inventory of cloud resources, services, and data.
- Ensure cloud compliance.
- Define and enforce security policies.
- Detect cloud misconfigurations and risks.
- Remediate cloud misconfigurations and risks.
Cloud Workload Protection Platform (CWPP)
CWPP tools provide visibility into and security for workloads. Traditional CWPPs require an agent to be installed on every asset to be monitored, which leads to incomplete coverage, high TCO, and performance degradation. However, modern CWPP solutions such as the Orca Platform provide 100% coverage of workloads without requiring a single agent.
CWPPs protect the data plane, and can detect and remediate vulnerabilities, malware, sensitive data, and other risks.
Container and Kubernetes Security
Container and Kubernetes Security enables organizations to detect and remediate security risks, prevent unauthorized access, and maintain a robust security posture. It involves several important practices, including the following:
- Scanning Infrastructure-as-Code (IaC) artifacts and container images at build time.
- Enforcing security policies that continually monitor container registries to ensure the security of application images and block risky builds to prevent insecure deployments.
- Continually monitoring product environments for risk, tracing some to issues originating from flawed source images or IaC artifacts for developer remediation.
Data Security Posture Management (DSPM)
DSPM solutions focus on securing sensitive data across cloud environments. DSPM solutions perform several important functions to ensure data security and integrity, including:
- Scanning and inventorying data across the cloud estate.
- Identifying where sensitive data lives and who has access to it.
- Discovering and eliminating shadow data to minimize the data attack surface.
- Preventing sensitive data exposure by addressing over-privileged access, data store misconfigurations, and other risks in the environment.
- Maintaining continuous multi-cloud compliance with sensitive data storage requirements.
Multi-Cloud Compliance
Multi-Cloud Compliance solutions help organizations adhere to regulatory frameworks and industry standards that govern the security and privacy of cloud computing, including the activity, data, assets, and applications associated with it. These solutions help organizations assure policy alignment across multiple public cloud environments.
Multi-Cloud Compliance solutions perform the following actions:
- Monitoring cloud environments for new security risks.
- Detecting risks and analyzing their severity dynamically using multiple criteria.
- Mapping security risks to compliance frameworks for easy synthesis and tracking.
- Facilitating the remediation of risks through system-generated instructions, code, and other tools.
- Providing flexible reporting capabilities, offering the ability to generate ad hoc reports, schedule recurring ones, as well as choose from multiple formats.
Shift Left Security
Shift Left Security enables organizations to prevent vulnerabilities and other security risks in runtime. It focuses on implementing security policies and controls that catch vulnerabilities and misconfigurations in the early stages of the SDLC, when developers can fix and address issues most efficiently and cost-effectively.
Shift Left Security entails the following activities:
- Continually scanning developer artifacts for vulnerabilities and misconfigurations.
- Establishing security policies that set and enforce guardrails for developers.
- Continuously monitoring container registries.
- Prioritizing risks and issues detected in development.
- Tracing runtime risks to their code origins for developer remediation.
Vulnerability Management
A critical aspect of cloud security, Vulnerability Management involves the continuous monitoring, assessment, and detection of vulnerabilities in cloud environments. It also involves prioritizing and facilitating the remediation of vulnerabilities.
Because security teams can only address approximately 10-15% of the vulnerabilities they encounter each month, an effective vulnerability solution requires the following:
- Vulnerability scanning that covers the entire cloud estate, including the control and data planes of multi-cloud environments.
- Dynamic and continual vulnerability analysis that accounts for severity, likelihood of exploitation, exposure, sensitive data, and other factors.
- Automated patch remediation policies that automatically fix known vulnerabilities and protect against exploits.
- Advanced reporting that provides full visibility and insight into vulnerabilities across cloud deployments.
The role of Orca Security as a cloud security solution
Orca Security is an agentless-first cloud security solution that identifies, prioritizes, and remediates security risks and compliance issues across multi-cloud environments. A natively built CNAPP, the Orca Cloud Security Platform helps organizations effectively secure their cloud and applications across their entire lifecycle.
Complete coverage with a unified cloud security solution
As a unified cloud security solution, the Orca Platform provides full visibility into your cloud estate. It leverages Orca’s patented SideScanning Technology™ to scan all cloud assets including virtual machines, cloud storage buckets, containers, serverless functions, and much more. SideScanning creates a comprehensive risk profile of your entire cloud estate—without sending a single packet over the network or running a single line of code in your environment.
Proactive risk management
Unlike other cloud security solutions, the Orca Platform continually analyzes detected risks across a variety of factors. These factors determine the danger that a particular risk presents and include the following criteria:
- Severity of the risk
- Difficulty of exploiting the risk
- Past exploitations of the risk
- Exposure of the risk
- Access to sensitive information
Additionally, Orca detects and analyzes the interconnected risks between cloud assets. These create attack paths that threat actors can exploit to potentially endanger high-value assets. The Orca Platform not only identifies attack paths, but analyzes their criticality, prioritizes them as appropriate, and facilitates their remediation.
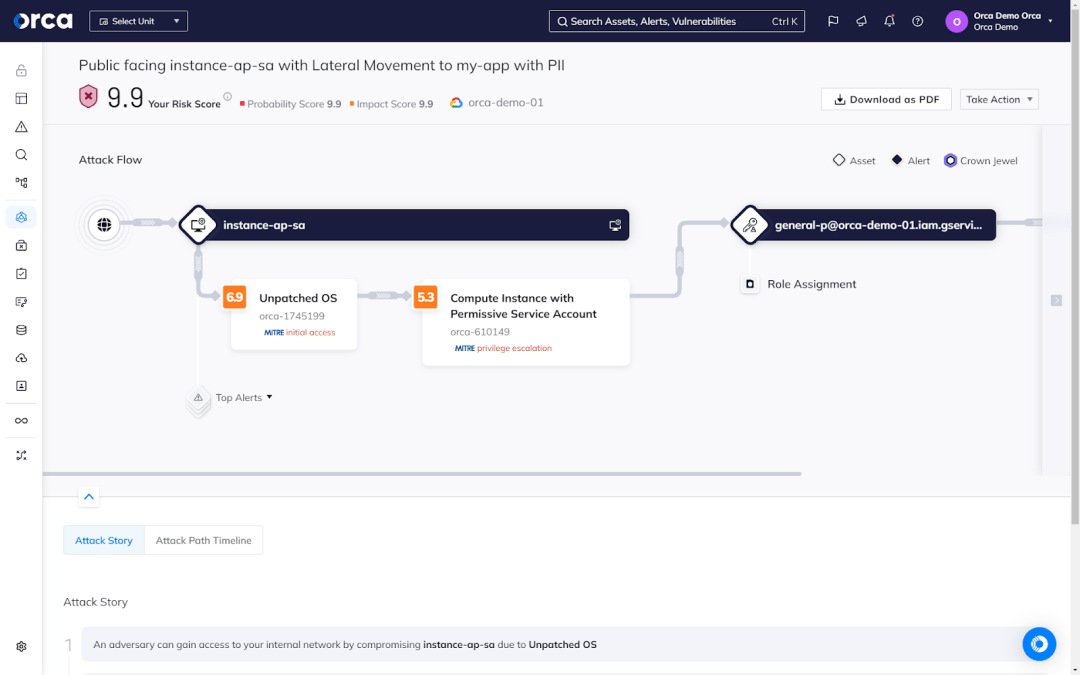
Continuous compliance, auditing, and reporting
Compliance is an essential priority for organizations of all sizes and industries across the world. The Orca Cloud Security Platform enables organizations to achieve and sustain compliance across their multi-cloud environments.
The Orca Platform automatically maps cloud risks to more than 160 regulatory frameworks and industry standards. After selecting a framework, organizations can see their compliance status immediately, including a full list of controls where they are compliant and non-compliant.
Orca also offers the following capabilities:
- Two-way integrations with ticketing systems: Each Orca alert provides the ability to generate and assign a ticket in Jira or ServiceNow without leaving the Orca Platform.
- Comprehensive reporting: Teams can generate ad hoc reports on-demand, or schedule one-time or recurring reports to be sent. They can also customize the format, frequency, and distribution channel for reports.
- Automated workflows: Teams can also build automated workflows that automatically perform tasks based on predefined criteria. This includes changing an alert score, generating a notification, creating and assigning a ticket, and more.
- Filterable views: Teams can filter compliance frameworks to view them by business unit, department unit, cloud environment, and more. This ensures organizations can focus their compliance efforts based on relevance.
- Customized frameworks: Orca enables organizations to combine multiple frameworks or parts of frameworks to meet their bespoke compliance needs. Orca also allows organizations to build their own frameworks from scratch using a library of more than 2,200 alerts covering a full range of cloud security use cases.
- Fast and simple remediation: For each alert, Orca offers multiple options for remediation, including suggested instructions developed by Orca’s security analysts, auto-remediation options for certain risks, and AI-driven Remediation. That latter generates recommended code and instructions using generative AI.
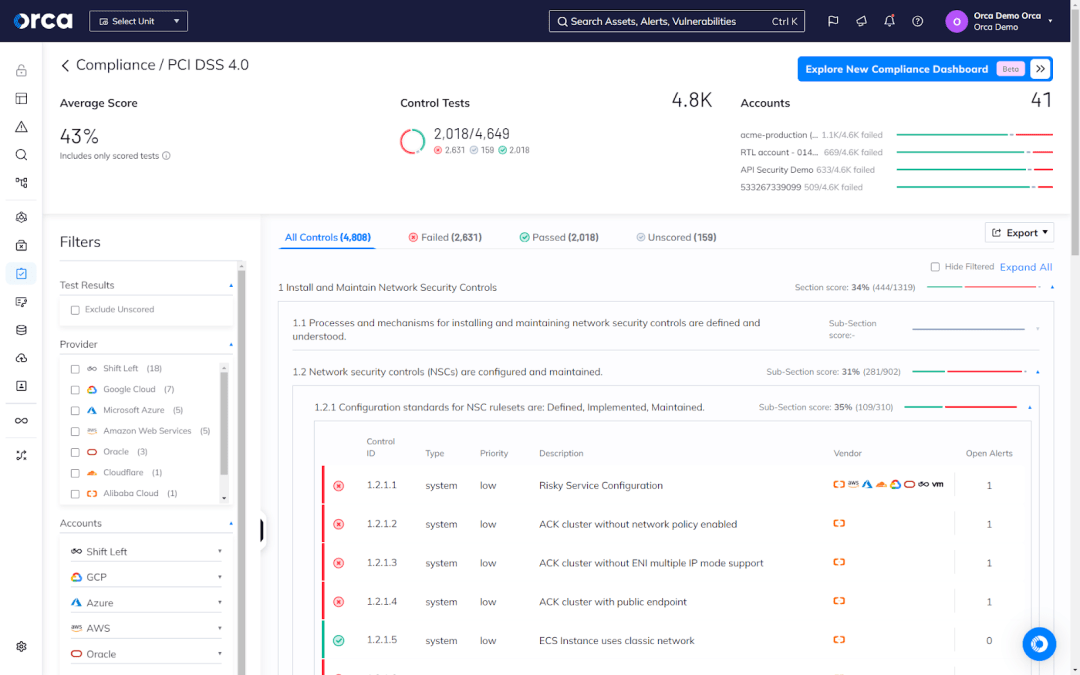
Key considerations when choosing a cloud security solution
Cloud security solutions vary significantly based on their type, vendor, and applied use. Look for solutions that possess at least the following characteristics:
Full and unified visibility
You can only protect what you can see. Cloud security requires complete visibility across your cloud assets and risks, as well as the ability to identify how they interrelate and connect. This last part allows you to effectively understand how risks and assets interrelate and truly determine the potential impact of a compromise or exploit.
Risk prioritization
More often than not, cloud security solutions overwhelm security teams with alerts that lead to fatigue, distraction, or confusion. That’s why organizations should look for solutions that generate alerts that accurately convey the danger a risk presents. This requires dynamically and continually assessing risk from multiple dimensions.
Scalability and flexibility
As explored previously, cloud environments are dynamic and constantly changing. To account for this elasticity, organizations need cloud security solutions that offer scalability and flexibility in terms of the cloud infrastructure, applications, data, identities, and other components they cover.
As an example, the Orca Cloud Security Platform automatically detects anytime a new repository is onboarded, and automatically scans it continually. This helps prevent drift and shadow development.
Ease of integration
Cloud security requires an ecosystem of fully integrated solutions—including those that extend beyond security. That’s because cloud security requires cross-functional collaboration among security practitioners, DevOps, and developers. Organizations should look for cloud security solutions that provide deep, two-way integrations with DevOps and developer tooling across the full application lifecycle.
Automation and AI capabilities
Security teams are almost always overwhelmed and overburdened by security risks. Solutions that offer automation and AI-driven capabilities help compensate for shortages in skills, knowledge, and capacity.
When evaluating solutions in this regard, look for technology that enables you to build automations that perform repetitive tasks that don’t require human intervention. Also, look for solutions that leverage AI to assist with and accelerate critical tasks, such as searching for a cloud asset or remediating a critical risk.
For example, the Orca Platform offers AI-Driven Search, in which users can quickly and easily understand the assets and risks across their cloud estate. For example, users can ask simple questions in plain language to find all their virtual machines with sensitive data exposure. The feature supports queries in more than 50 languages.
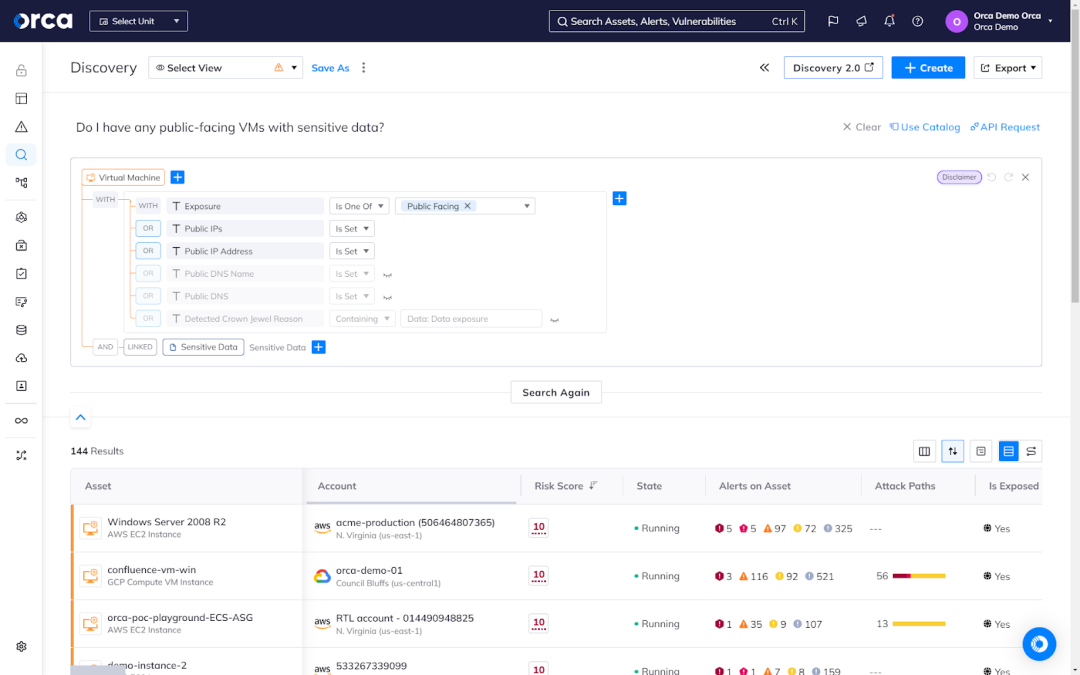
Additionally, Orca also offers AI-Driven Remediation, which allows users to generate remediation code and instructions on-demand, both tailored to their preferred remediation process.
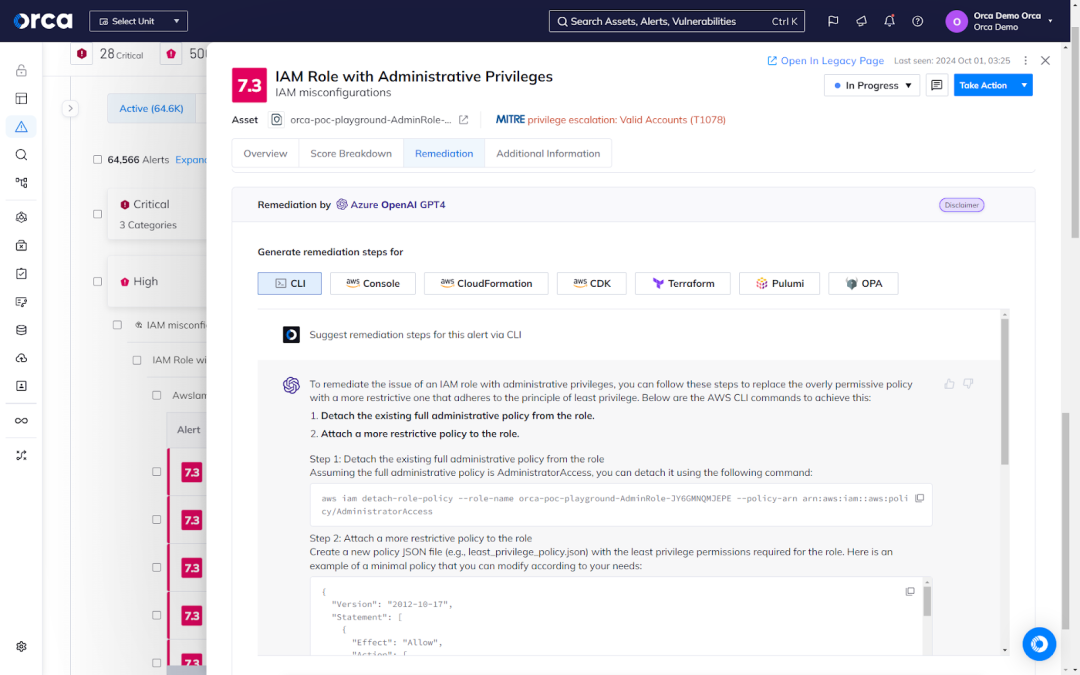
Cost and efficiency
Cloud security is an essential investment for organizations of all sizes and types. Yet it can also become a prohibitive expense if companies choose solutions with inadequate capabilities.
Best practice is to look for solutions that maximize efficiency and productivity. This comes primarily from risk prioritization, automations, and AI-powered capabilities. Additionally, consider solutions that integrate multiple point solutions, as they consolidate licensing feeds and lower your total cost of ownership (TCO).
Last, favor technology that can measure your cloud utilization and help you reduce your overall cloud spend. Some cloud security solutions offer this capability, which can boost your return on investment (ROI).
An independent analysis by TAG Cyber Report, a cybersecurity analyst firm, determined that Orca Cloud Security Platform generates a 207% annual ROI for organizations based on the factors previously mentioned.
Multi-cloud compatibility
Using more than one public cloud is common for many organizations. That explains the importance of multi-cloud compatibility, or the ability to integrate with and work across two or more environments offered by multiple CSPs. Considering that AWS, Azure, and GCP retain most of the market share in cloud services, ensure your solution is compatible with these organizations at the very least. But also look for solutions that support Oracle Cloud, Alibaba Cloud, and Kubernetes.
Conclusion
Cloud computing demands effective cloud security solutions. They represent a primary measure to protect your digital innovation, assets, and continuity. Yet as this guide illustrates, they differ drastically in terms of their features, use cases, and effectiveness. Awareness of these differences can help you make a more informed decision and find the right technology for your organization. This translates into one of the most effective and important measures to protect your cloud innovation, assets, and continuity.
FAQs
How do cloud security solutions work?
Generally, cloud security solutions inventory cloud assets and risks, provide continuous monitoring, prioritize risk, facilitate timely remediation and mitigation, and support compliance and reporting.
What is the biggest threat to security on the cloud?
Misconfigurations are the top cloud security risk. This type of risk happens when cloud services, assets, and other resources are not properly configured, often resulting in permissive access or controls, unnecessary exposure, exposed sensitive data or secrets, and more. In Orca’s 2024 Cloud Security Strategies Report, 57% of executives rated misconfigurations as the leading cloud risk.
What is a cloud-native solution?
A cloud-native solution enables organizations to develop, build, test, deploy, and maintain applications in a cloud environment. These solutions allow organizations to deliver and support modern applications across their lifecycle using cloud resources and infrastructure.
What is a hybrid cloud solution?
A hybrid cloud solution combines an on-premise and a public cloud environment, enabling organizations to share applications and data between them. A hybrid cloud solution is different from a multi-cloud one, which combines two or more public cloud environments from at least one CSP.
Are public or private clouds more secure?
Cloud risks affect both public and private clouds. The security of each depends on a variety of factors, including the type of security policies, technologies, and practices employed by an organization.







