The Challenge
Agents Weren’t Designed for Cloud Native Applications
Agent-based containers and Kubernetes security solutions only provide coverage of cloud workloads that have an agent installed. With the ephemeral nature of cloud-native applications, it is simply not feasible to install agents on every asset, inevitably leading to security gaps. Vendors offering a choice between agents and agentless approaches only add to the complexity and often have hidden limits on their ‘agentless’ capabilities. In addition, legacy solutions only cover cloud workloads and miss risks in the cloud control plane, such as misconfigurations and overly permissive identities.
Partial deployment of agents causes serious blind spots and agents can have a significant performance impact on applications
Security and DevOps teams need to spend countless hours installing, configuring, and maintaining agents, creating organizational friction.
No insight into cloud configurations and identities leaves important security gaps.
Our Approach
Scalable Security for Containers and Kubernetes
Unlike other solutions, Orca is completely agentless and fully deploys in minutes with 100% coverage, providing wide and deep visibility into risks across every layer of your cloud estate. This includes cloud configurations, container images, the Kubernetes control plane, as well as your applications. Orca combines all this information in a Unified Data Model to effectively prioritize risks and recognize when seemingly unrelated issues can be combined to create dangerous attack paths.
Build
Container images and IaC templates are scanned on the developer desktop or as part of regular, continuous integration (CI) / continuous delivery (CD) workflows.
Deploy
Registries are continually monitored to ensure application images are secure before deployment, with guardrail policies in place to prevent insecure deployments.
Run
Production environments are monitored for risks with contextual alerts and risk prioritization, as well as integrations with ticketing and notification tools.
Additionally, Orca continuously checks for misconfigurations across multi-cloud estates to ensure controls are set securely and comply with best practices and industry and regulatory standards.
Agentless container and Kubernetes security
Orca’s patented SideScanning™ technology is a radical new approach that addresses the shortcomings of agent-based cloud security solutions.
- Orca collects data directly from your cloud configuration and the workload’s runtime block storage out-of-band.
- Within minutes, Orca finds and prioritizes your most critical cloud risks, including vulnerabilities, malware, misconfigurations, lateral movement risks, IAM risks, and sensitive data at risk.
- Unlike other solutions, Orca combines workload-deep intelligence with cloud configuration metadata all in one platform.
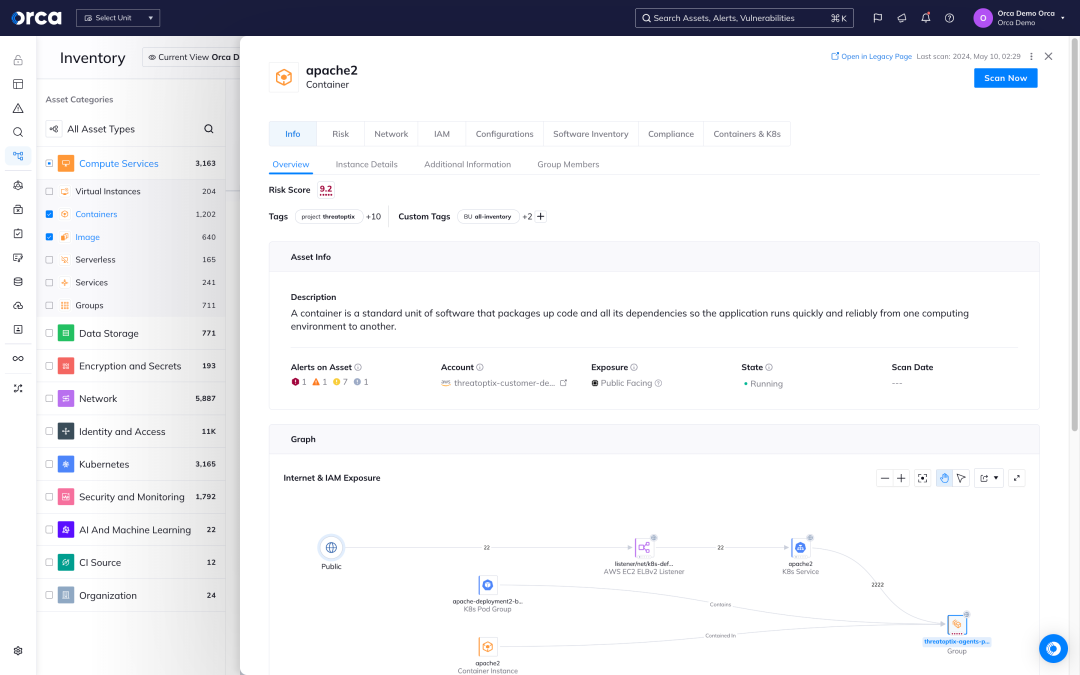
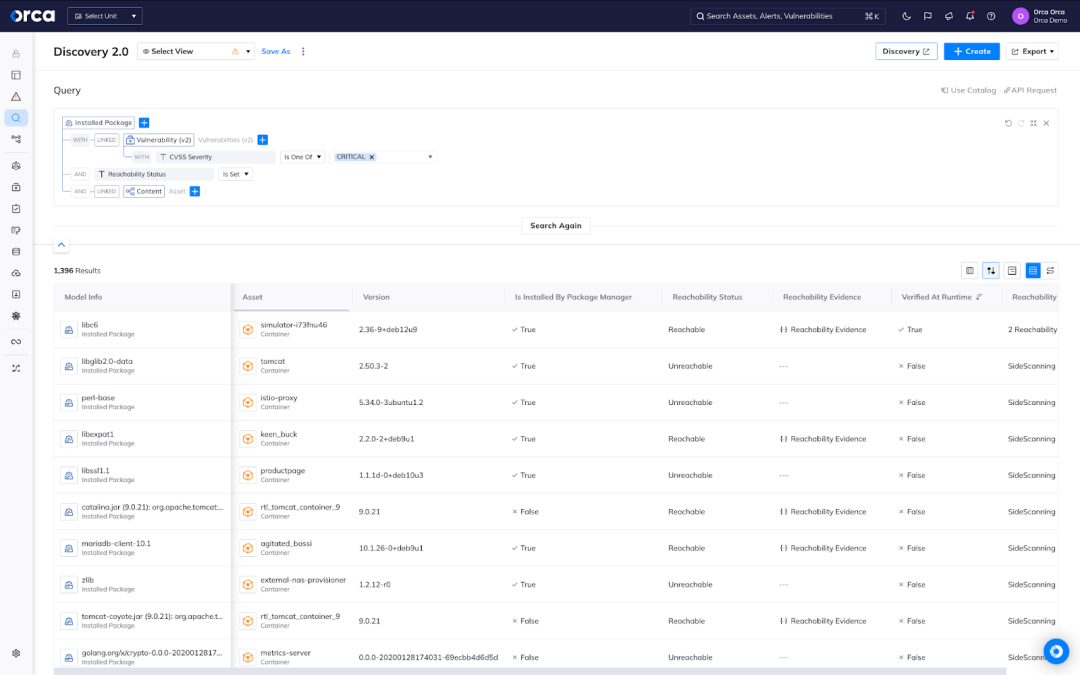
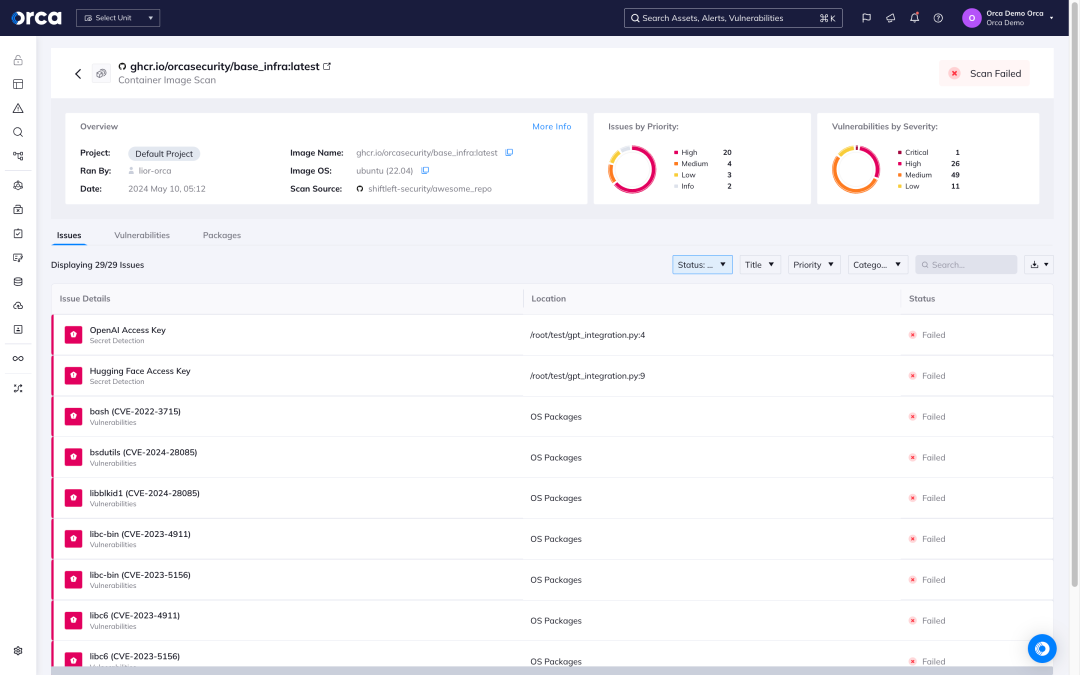
Vulnerability management across hosts and images
Orca creates a full inventory of your cloud environment and leverages 20+ vulnerability data sources to discover and prioritize vulnerabilities across your entire cloud estate.
- Orca’s workload inventory includes information on OS packages, applications, libraries, as well as versions and other identifying characteristics.
- Unlike other solutions that simply report on the CVSS score, Orca considers the context of cloud assets, their connections and risks, while also performing Agentless Reachability Analysis, to understand which vulnerabilities need to be addressed first.
- In rapid response situations such as Log4Shell, Orca allows you to quickly identify vulnerable cloud assets and prioritize patching the ones that pose the greatest risk to the business.
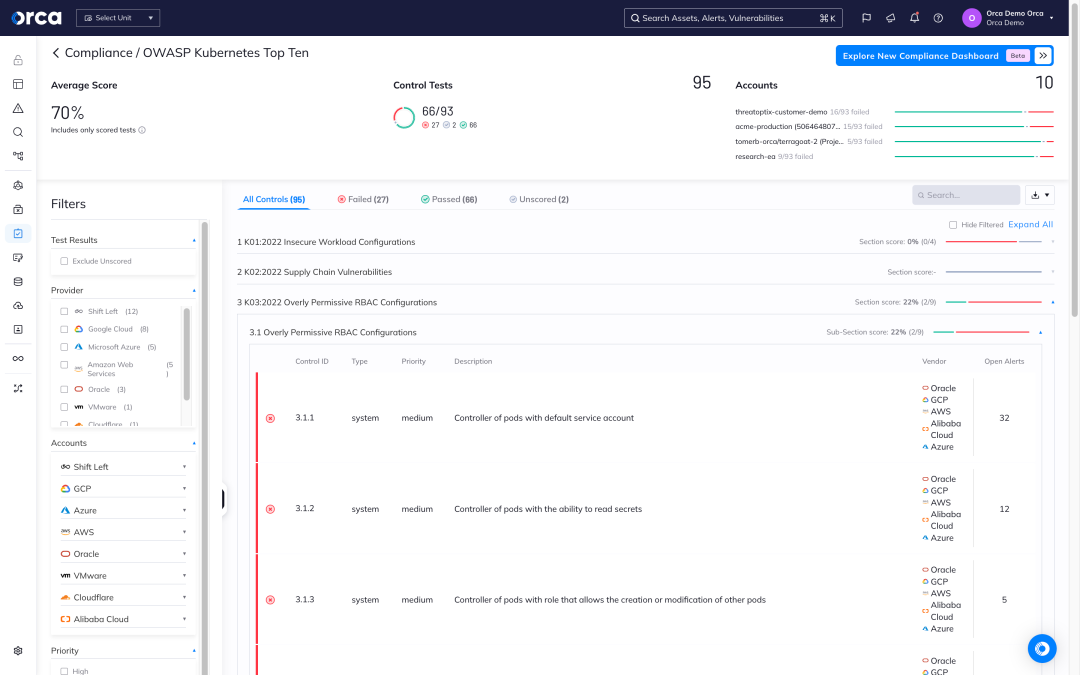
Full stack compliance for your entire application
Orca supports over 100 out-of-the-box compliance templates enabling fast, effective compliance and reporting. For modern cloud native applications, leverage and customize the Center for Internet Security (CIS) Benchmarks, including Docker, Kubernetes, Linux and more.
- Leverage pre-built compliance templates for vital industry frameworks, such as PCI-DSS, HIPAA, GDPR, SOC 2 and more
- Quickly and effectively enable CIS Benchmarks, supporting Linux and Windows hosts, Docker, Kubernetes, and other cloud native technologies
- Integrate compliance checks into the CI/CD lifecycle to enforce compliance policies and best practices
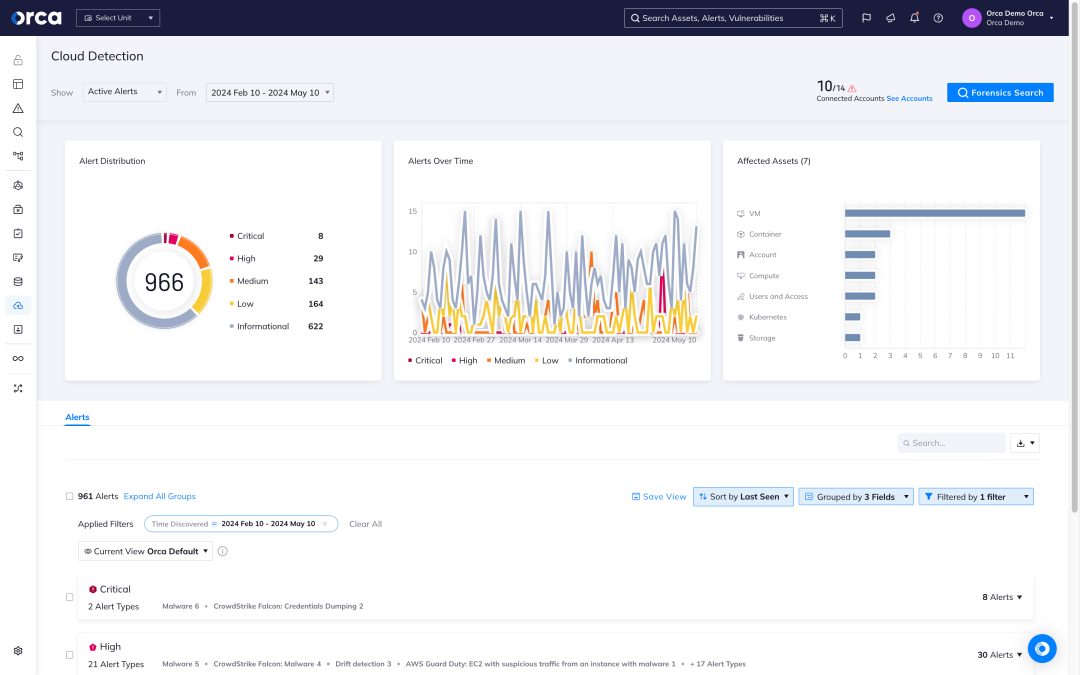
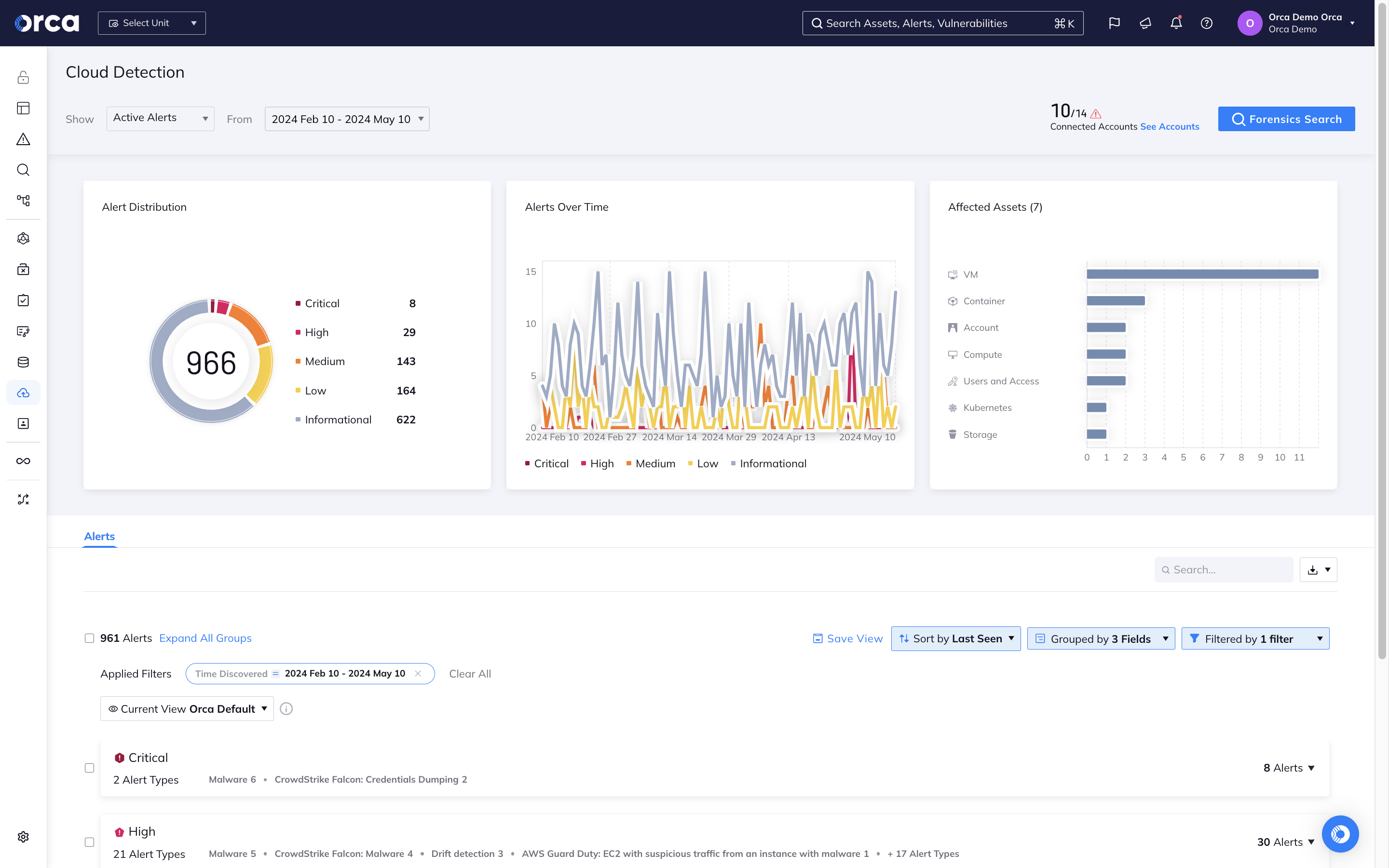
Detect and respond to cloud attacks
With Orca’s CDR capabilities, organizations can detect, investigate, and respond to cloud attacks in progress:
- Detect: Receive alerts when changes and anomalies occur that indicate possible malicious intent versus normal behavior, automatically prioritizing events that endanger the company’s most critical assets.
- Investigate: Research malicious activity to quickly gain insight into whether the events are malicious and if any of the organization’s critical assets are in danger.
- Respond: Intercept cloud attacks by leveraging remediation steps and automatically assigning issues using Orca’s 20+ third-party technical integrations (including SOAR, notifications, and ticketing systems).