IAM Risk Detection
The Orca Cloud Security Platform detects, prioritizes, and continuously monitors for common and obscure identity and access management (IAM) misconfigurations across your cloud estate to meet stringent IAM compliance mandates and improve your cloud security posture.
The Challenge
Excessive permissions give attackers the keys
Poor identity and access management hygiene is a top cause of intentional and accidental exposures in public cloud environments. Threat actors constantly look for ways to exploit IAM misconfigurations such as overly permissive identities, poor password and credential practices, and accidental public exposure.
- 90% of organizations have at least one asset that enables lateral movement.
- 72% of organizations have unused IAM roles.
- 61% of organizations have a root user or account owner without MFA.
Our Approach
Shrink your attack surface with good IAM hygiene
Orca detects and prioritizes identity and access management misconfigurations such as weak and leaked passwords, exposed credentials, and overly permissive identities. Continuous IAM monitoring across your cloud estate prevents malicious and accidental exposure.
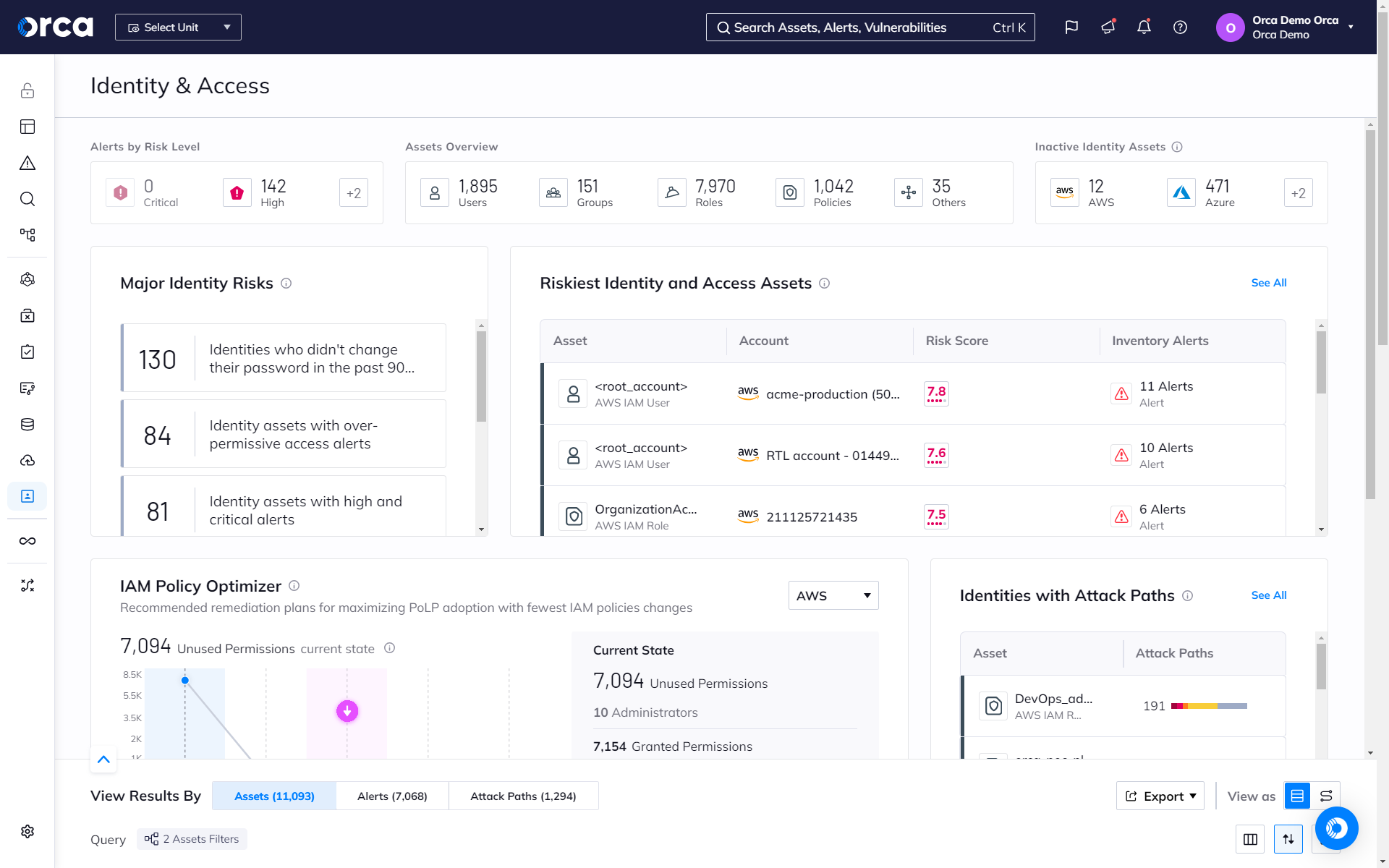
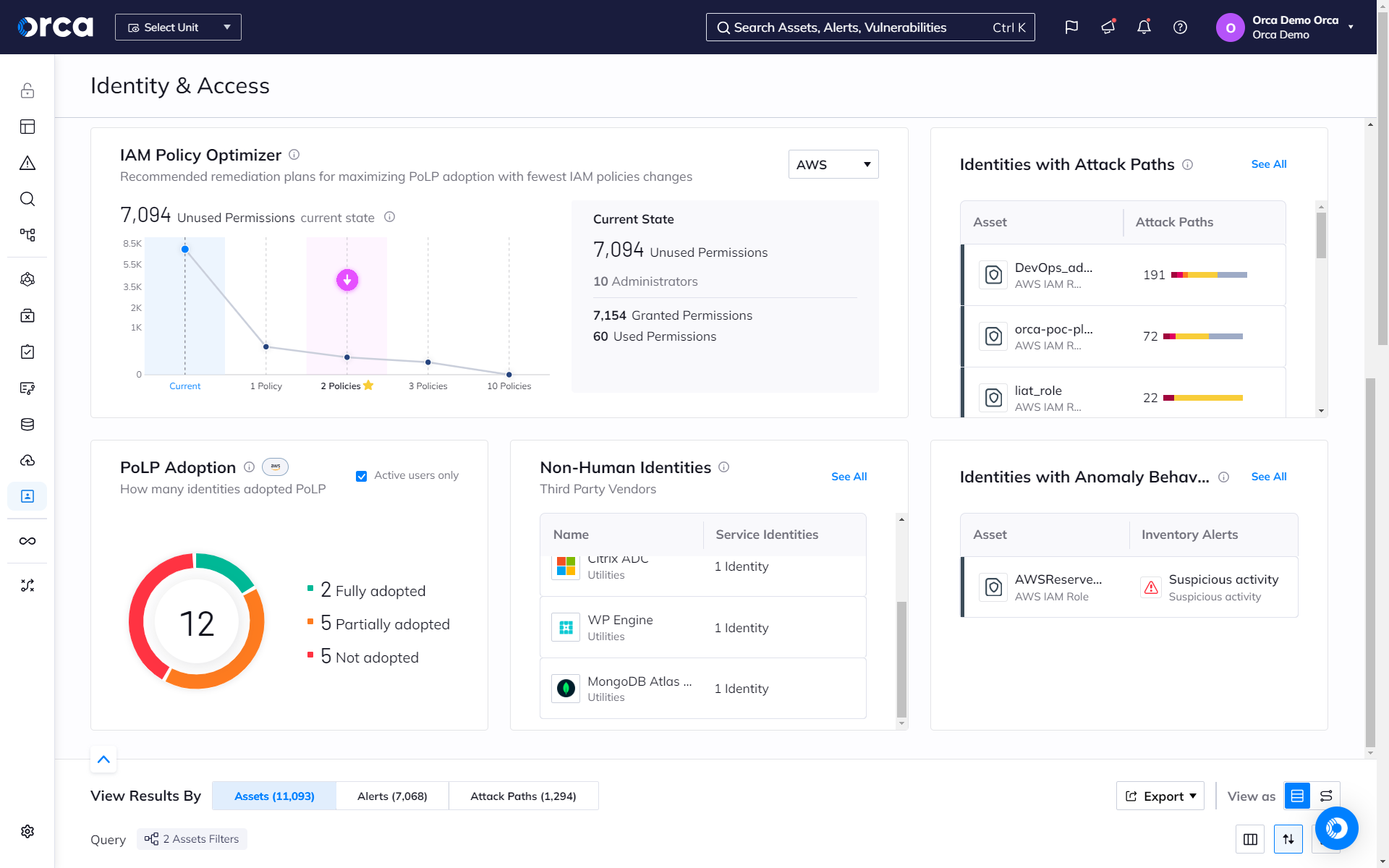
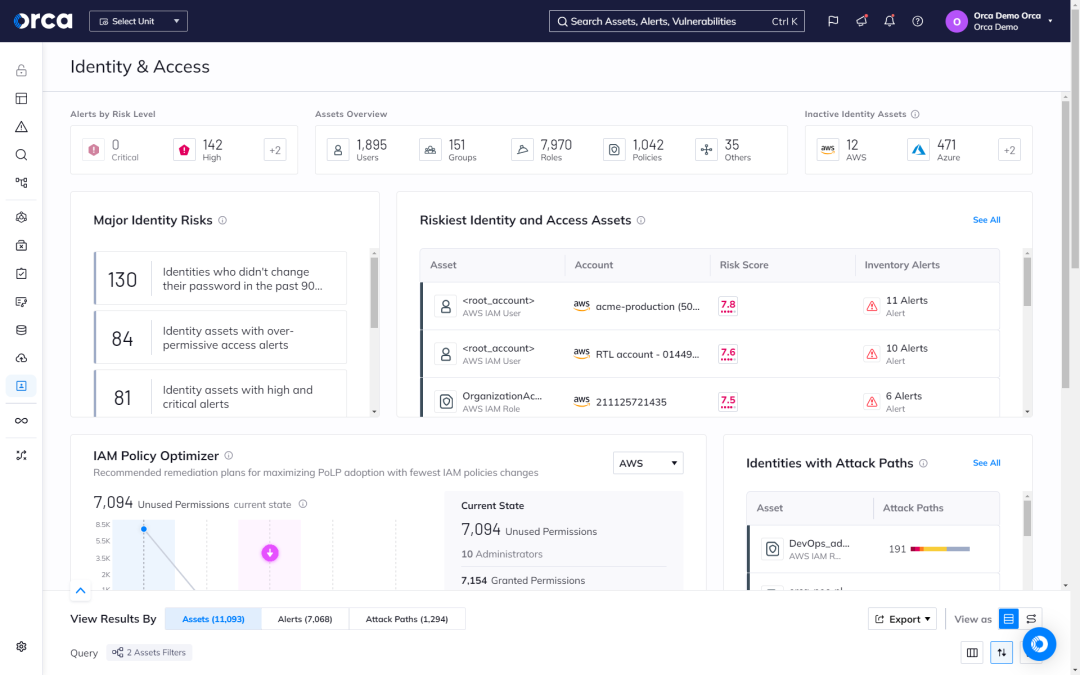
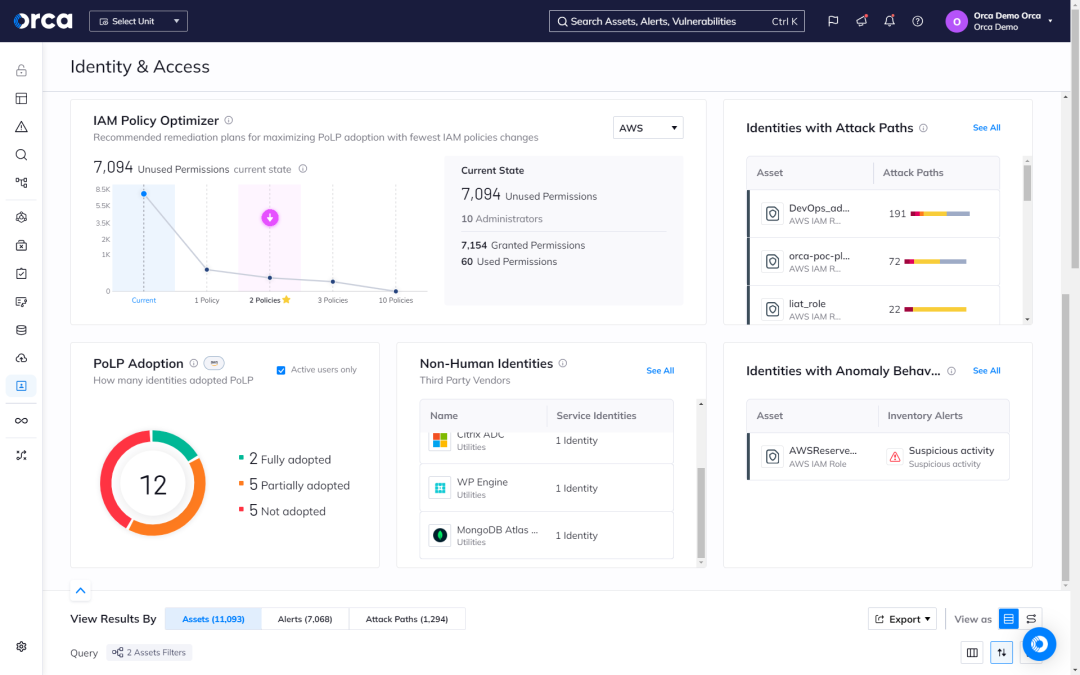
Optimize your IAM policies to limit privileges and improve hygiene
Orca leverages AI to determine the optimal IAM policy configuration that maximizes security with the fewest changes to policies, users, or roles. This saves time, limits privileges, and reduces the risks associated with unnecessary permissions and accounts.
- Orca presents recommended remediation plans for maximizing the adoption of PoLP (Principle of Least Privilege) with the fewest number of policy changes.
- Orca automatically provides optimized configurations as a downloadable file that can be uploaded to your cloud platform(s).
- On a granular level, Orca automatically makes policy recommendations for overly permissive identities or roles that teams can apply.
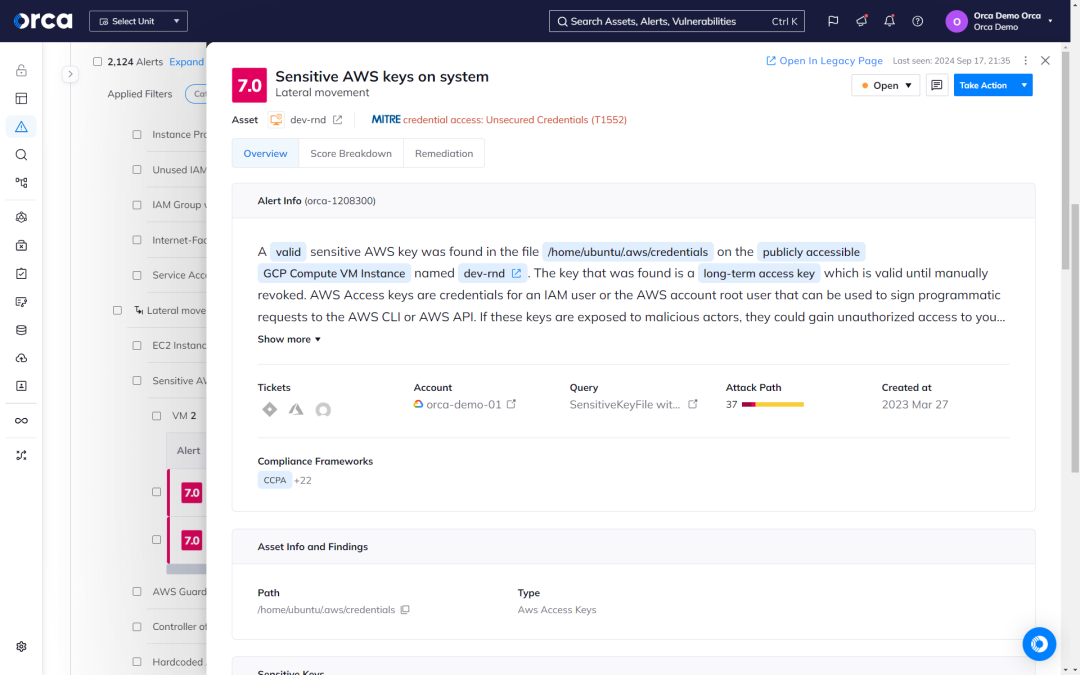
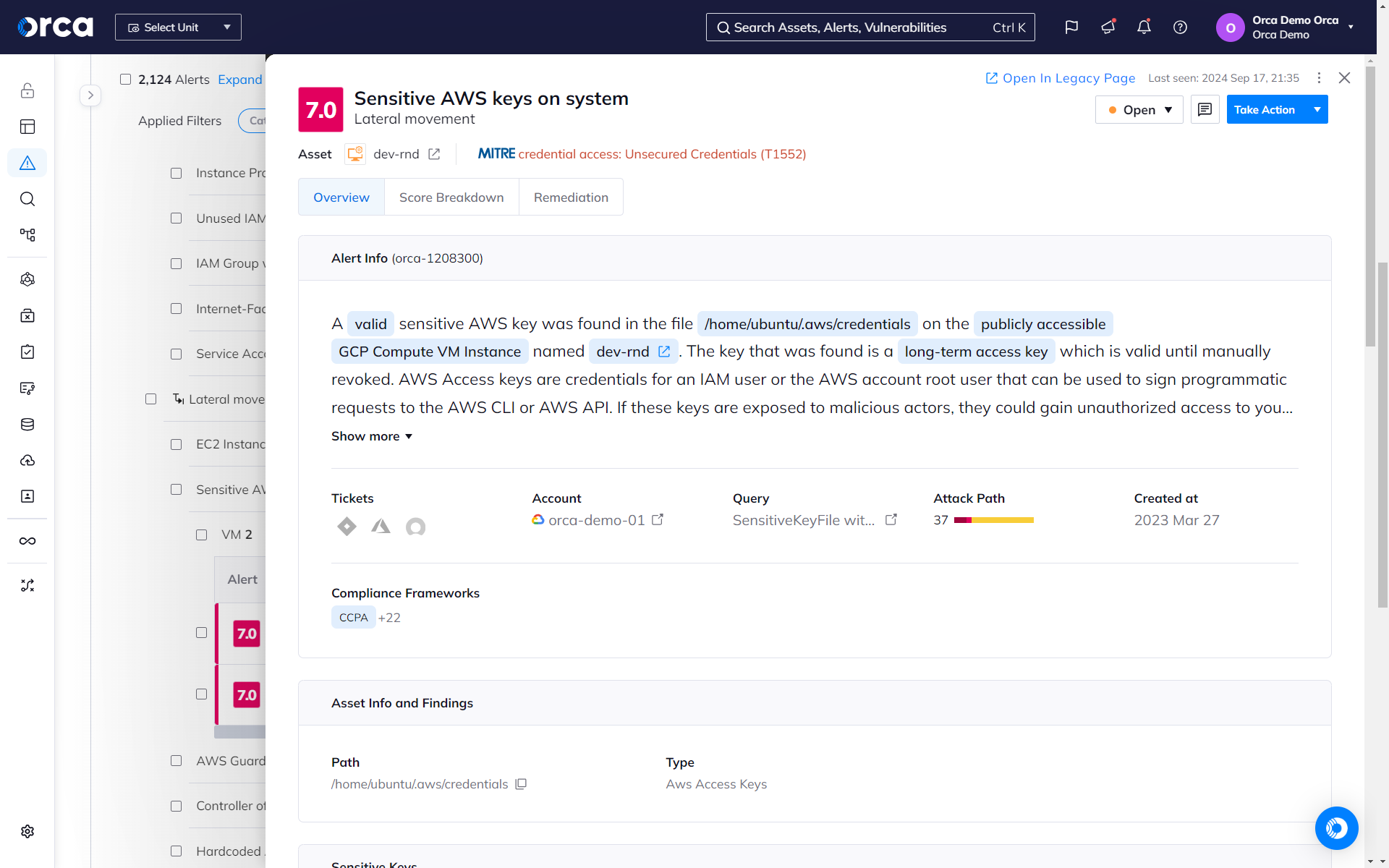
Find exposed keys before bad actors do
The Orca Platform scans your entire cloud estate for exposed keys, vulnerabilities, passwords in shell history, and other information that bad actors can use to move laterally in your cloud estate.
- Orca scans every machine’s file system for private keys, generates hashes of any discovered keys. Orca then scans all other assets for authorized public key configurations with matching hashes.
- Orca reveals key information including paths to insecurely stored keys, workloads attackers can access with exposed keys, and stored user accounts and permissions.
- Orca detects all remote access keys—including cloud service provider keys, SSH keys, and more—that might allow attackers to access additional sensitive resources.
Take control
of your identities
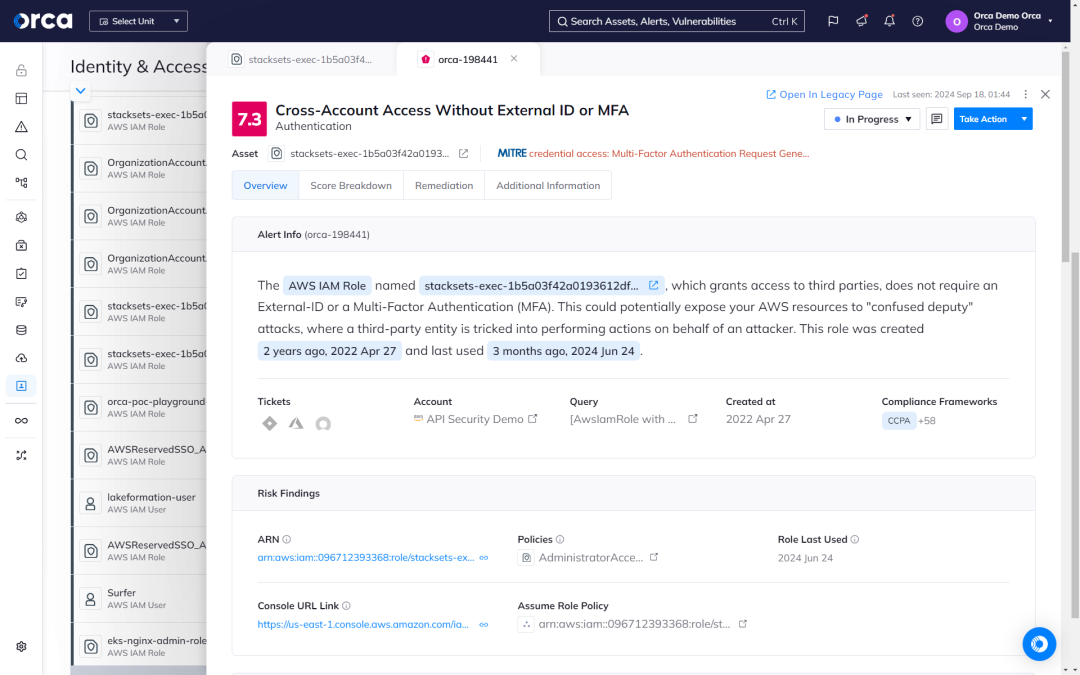
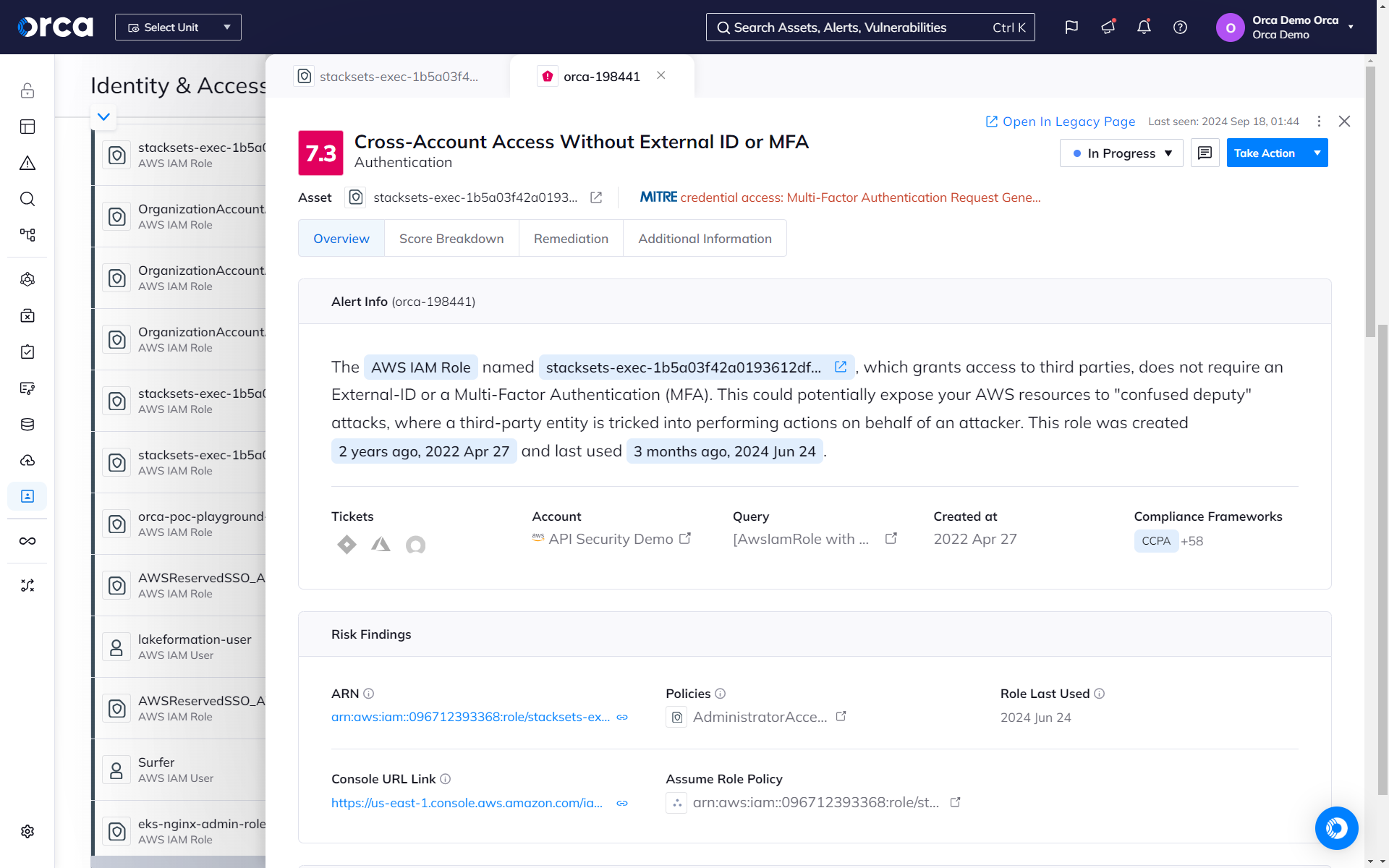
Orca’s Identity and Access dashboard helps organizations understand the relationship between access rights and cloud resources. Orca alerts when overly permissive identities are found and prioritizes them according to potential business impact.
- Orca monitors all identities, roles, groups, permissions, and policies deployed in your cloud environment.
- Orca alerts teams when security best practices, such as the principle of least privilege, are not adhered to.
- Get answers to questions such as: “Which human and machine identities have access to this Google Standard Storage resource?” or “Which AWS EC2 instances have access to an S3 bucket with PII data?”