
How Orca Security Compares to Rapid7
Customers choose the power and simplicity of Orca Security over Rapid7 InsightCloudSec
A purpose-built platform for comprehensive cloud security
With Orca Security, you benefit from a purpose-built Cloud Security Platform that addresses all of your cloud risks and features our patented SideScanning technology that covers your entire cloud estate without agents. Orca continues to innovate and provide visibility into wherever threats may live in your cloud environment, including everything from IAM to API endpoints.
InsightCloudSec was built by combining acquisitions and, as such, insights and functionality isn’t tightly integrated, forcing you to work harder for less intelligence. For some features, such as VM vulnerability scanning, Rapid7 requires you to buy other subscriptions or add-ons
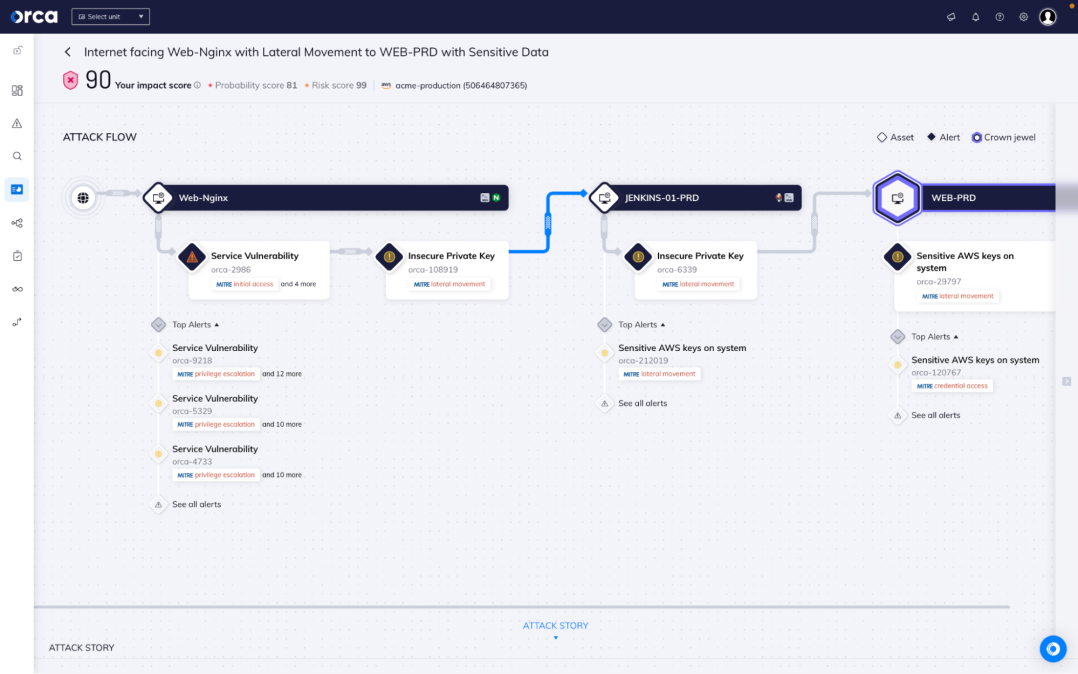
SideScanning enables deeper insight
Orca’s patented SideScanning technology quickly and easily scans all of your Linux and Windows workloads, including cloud VMs, containers and Kubernetes applications, and serverless functions. Rapid7 doesn’t scan inside running assets, relying solely on external information, and can’t provide this deep insight into your workloads. Within the Orca UI, you can view detailed risk prioritization information about all of your assets with context to understand your greatest risks and the impact to your business.
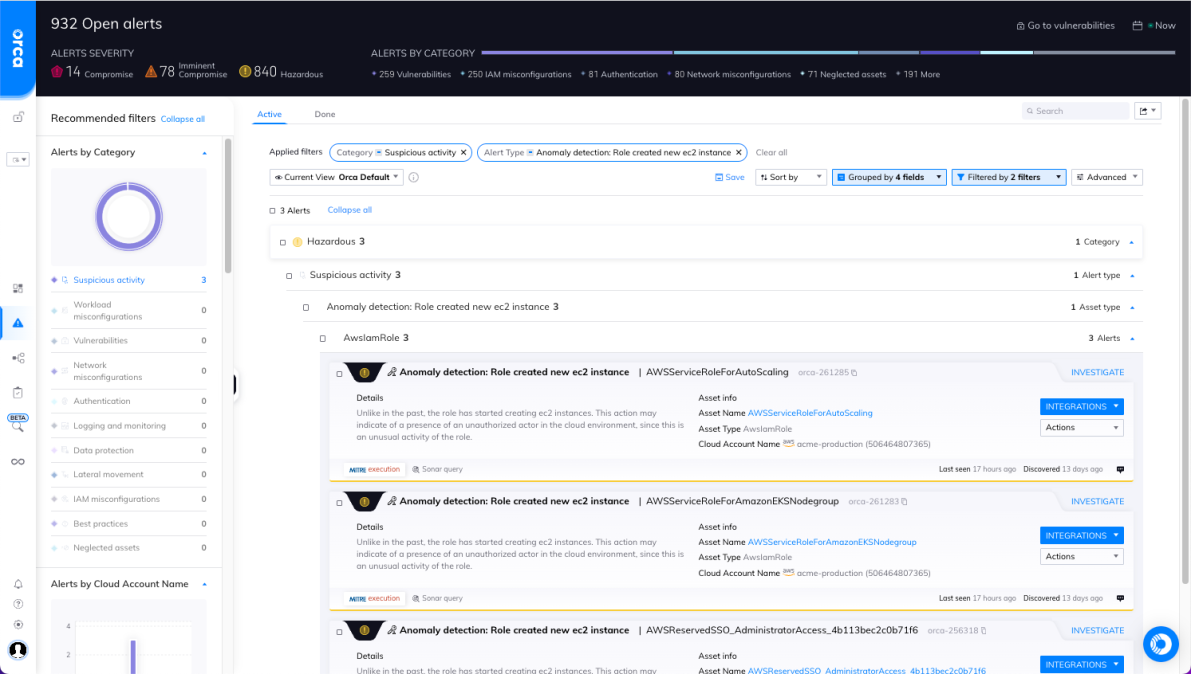
Unified data for risk prioritization
The Orca Platform brings all of your data into a unified, easily-queryable location. With Orca’s Unified Data Model, you can view assets, compliance status, risks, and security incidents from one dashboard across cloud infrastructure and workloads.
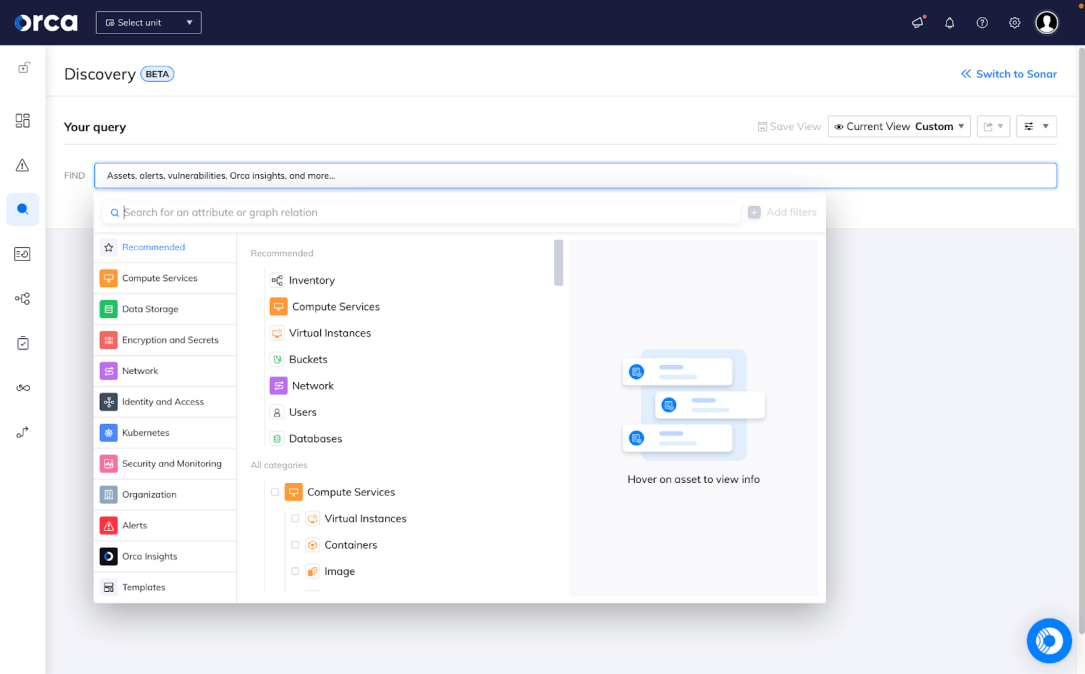
Identify sensitive data in your cloud
Orca Security automatically identifies and classifies data such as PII(Personally identifiable Information), credit card numbers, and PHI(Protected Health Information) in storage buckets, VMs, and databases. When you combine this with automated attack path analysis, Orca shows you where critical information is at risk even if it would take an attacker multiple steps to get to it. Rapid7 can’t compare.
Features

Vulnerability Management
Simple & Complete
With a single, agentless deployment, assess vulnerabilities across all VMs and containers in your cloud environment
Fragmented
VM scanning requires an additional subscription to InsightVM and findings are in a separate console. Container scanning only covers containers in Kubernetes and requires additional, per-cluster configuration.
Asset Inventory
Unified
Continuously monitor public cloud services and configurations, entitlements and identities, workloads and applications, all from a single dashboard
Incomplete
No identity & entitlement info without an additional subscription. No API endpoint info
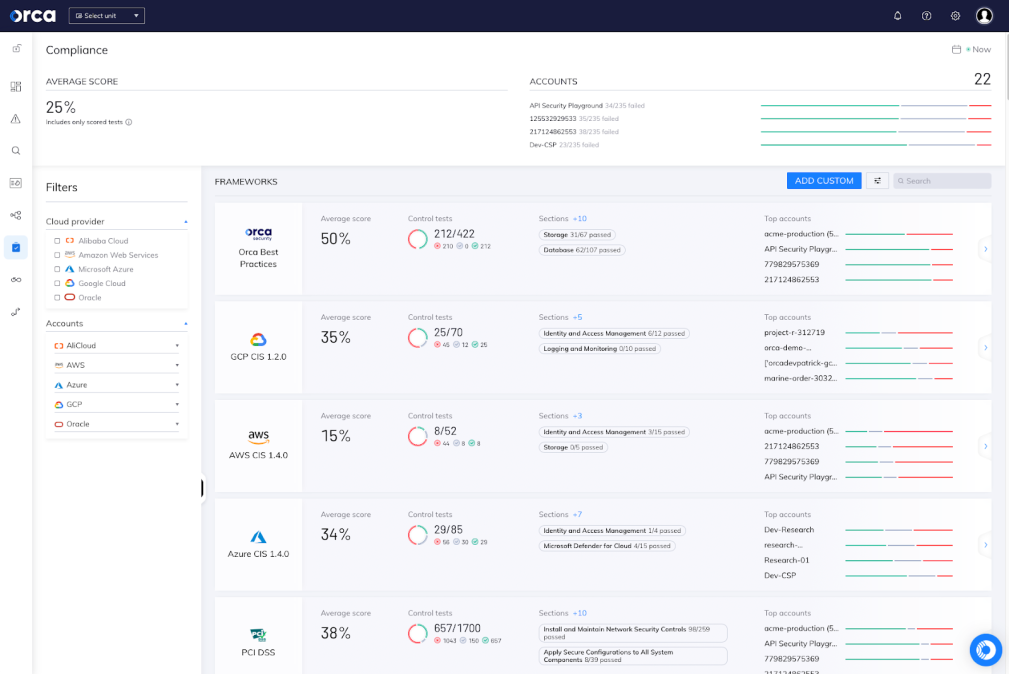
Compliance
Comprehensive
100+ compliance frameworks with all data and policies shown in a single dashboard for seamless reporting
Basic Coverage
Fewer compliance frameworks, covering only cloud infrastructure, leaves your auditors doing far more work
Attack Path Analysis
Automated and Interactive
Interactive dashboard, with automated impact score, surfaces toxic combinations of risks so teams can prioritize and fix the top 1% of issues. All risks mapped to the MITRE ATT&CK framework
Very Limited
“Layered Context” only shows assets exposed to the Internet. This doesn’t help identify the combinations of configurations & vulnerabilities that attackers use to compromise critical resources.
PII Detection
Seamless and Comprehensive
Automatic detection of PII across all cloud resources
No Sensitive Data Detection
With no data classification at all, InsightCloudSec leaves you guessing on critical assets.
API Security
Simple and Comprehensive
Automated inventory of all interconnected APIs and web domains. Capabilities integrated with agentless SideScanning technology, nothing new to activate. Prioritize risks, including external exposure, mapped to OWASP API Security Top 10 and contextualized with all other risks
No API Security
InsightCloudSec doesn’t assess exposed API endpoints or provide meaningful views of what is deployed & running.



