Enterprises have moved to the cloud and adopted cloud-native architectures at a rapid pace. This dramatic shift has allowed organizations to scale more easily and ship code to production more quickly. However, cloud environments and applications can have numerous weaknesses – especially when used incorrectly – that can create risks for organizations and their security teams, including:
- Vulnerabilities in workloads and applications
- Misconfigurations of cloud infrastructure services, such as storage buckets
- Improper use and configuration of identities and cloud entitlements
Although many of these individual weaknesses can be detected by cloud security tools, most tools focus on a particular risk area, such as workloads, cloud service configurations or identity entitlements. This siloed approach means that the tools cannot see how risks can be combined with weaknesses in other layers of the technology stack to create dangerous attack paths. Until today, security teams have expected long lists of alerts that include top CVEs or notable misconfigurations where they lack context about multiple issues that really matter.
To fully understand where your organization’s most critical weaknesses are, it is important to view risks as an interrelated chain, rather than just siloed risks. By understanding which combinations are a direct path to your critical assets, security teams can operate strategically by making sure that the risks that break the attack path are remediated first. Orca Security does just that with its new Attack Path Analysis dashboard.
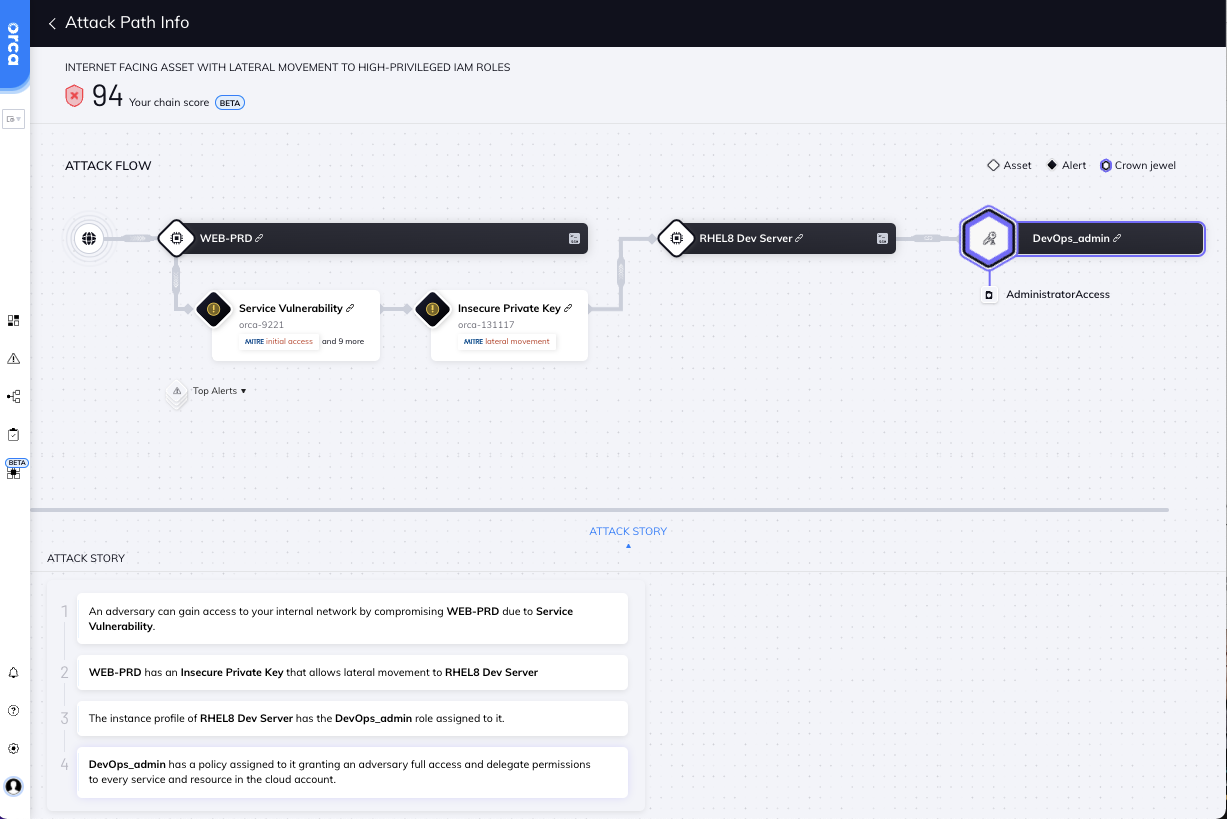
Orca shows the steps an attacker can take to reach the company’s crown jewels
Cloud Attack Path Analysis Automatically Correlates Multiple Alerts into One Interactive View
Orca defines Attack Path Analysis as the automatic identification of risk combinations that create dangerous attack paths that can be exploited by attackers. This includes representing attack paths in a visual graph with contextual data on all relevant cloud entities and their risks across vulnerability status, misconfiguration risks, trust and authorization, and data as well as the relations between them.
Orca then combines this information with the location of the organization’s most valuable assets, or ‘crown jewels’, and assigns each attack path a Business Impact Score. This allows security teams to immediately understand which attack paths are the most critical to the business, so they can remediate those first.
For attack path analysis to be truly beneficial, it is essential that the cloud security platform utilizes a unified data model that collects and correlates contextual data on each asset, including information on potential risks in the cloud workload and configuration as well as external and internal cloud connectivity.
Industry analysts are increasingly recognizing the value and need for more detailed attack path analysis as part of cloud security solutions. Gartner lists attack path analysis as one of the core capabilities of a Cloud-Native Application Protection Platform (CNAPP):
“Allow security departments to understand attack path analysis based on relationships — identities, permissions, networking and infrastructure configuration that would enable an attacker to target an application.” – Gartner, Inc., Innovation Insight for Cloud-Native Application Protection Platforms, Neil MacDonald and Charlie Winckless, August 25, 2021
Prioritize Attack Paths, Not Just Siloed Alerts
With Orca’s new attack path analysis and prioritization capabilities, security teams no longer need to sift through hundreds of siloed alerts to find out which issues need to be fixed and in what order, but instead can now focus on a much smaller amount of prioritized attack paths, or combinations of alerts, that endanger the company’s most critical assets. By prioritizing and scoring each attack path, Orca pinpoints exactly which risks need to be remediated to ‘break the chain’.
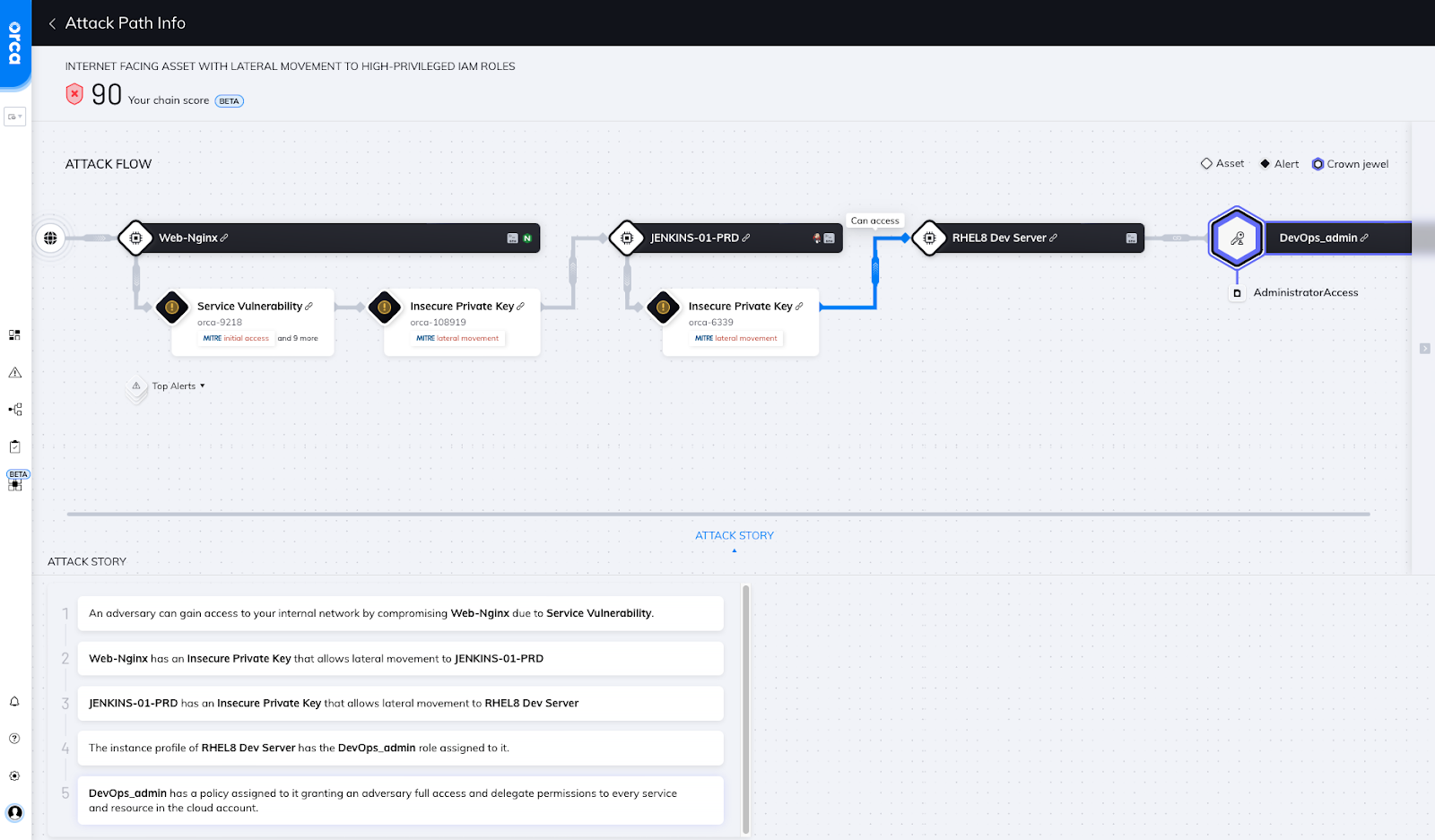
Attack path visualization of how an attacker can access sensitive company data
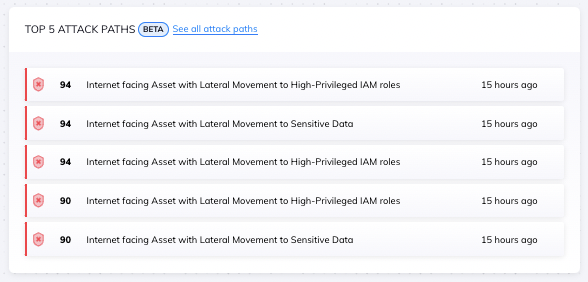
Orca shows the five most dangerous attack paths in the central Risk Dashboard
As shown in the screen above, Orca’s new Risk Dashboard lists the Top Five Attack Paths ordered by Business Impact Score to allow teams to quickly identify which issues need to be prioritized.
Orca Security Attack Path Scoring and Prioritization
Orca assigns an overall score (from 0 to 99) to each attack path and scores each attack vector that makes up the attack path. To calculate the score, Orca uses an advanced algorithm that takes the following factors into account:
- Severity: How severe is the underlying security issue? For example, what type of threat is it, how likely is it to be exploited, and what is the CVSS score?
- Accessibility: Is the attack path Internet facing? How easy is it to exploit the initial entry point to the attack path?
- Lateral Movement Risk: Is there lateral movement risk? If so, how easy is it to exploit, and how many hops do you need to reach your end goal?
- Access Level: Does the risk provide read only access, or read and write access? If the risk allows privilege exploitation, what level of privileges does it allow?
- Business Impact: How critical is the target that the attack path exposes? Is it Personal Identifiable Information (PII), or other sensitive information such as intellectual property? Is it a production server that is essential to the business?

How Orca Security scores attack paths
Orca’s Cloud Attack Path Visualization
Orca provides a visual representation of each attack path, along with detailed information on each attack vector. The attack story includes further information and context for each step in the attack path.
Each attack vector in the path includes tags for easy identification and filtering, including applicable MITRE ATT&CK categories.
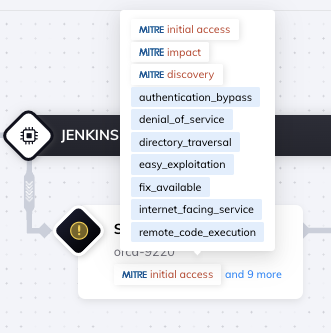
Orca shows detailed information for each step
Orca’s View into Business Impact
Instead of looking at attack paths starting from the cloud entry point, Orca investigates possible attack paths starting with the company’s crown jewels, placing the focus on avoiding damaging data breaches, rather than just treating all threats as if they are of equal importance.
To determine which assets are business critical, Orca automatically discovers sensitive data and critical assets. In addition, customers can tag and classify critical assets themselves. Orca’s “Crown Jewel” categories include Personal Identifiable Information (PII), secrets exposure, intellectual property, financial information, and other sensitive data. The attack paths that endanger the company’s crown jewels will receive a higher Business Impact Score so that remediation of these paths can be prioritized.
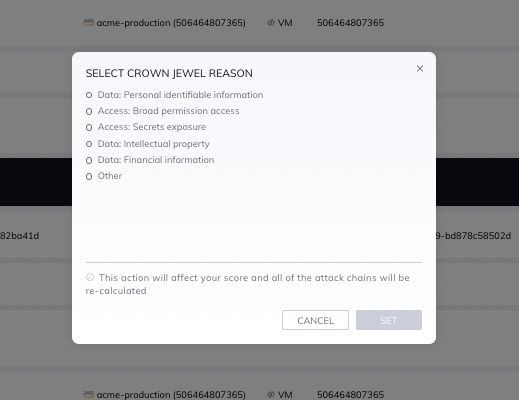
Orca users can tag the crown jewels in their environment
How Teams Remediate Smarter with Orca’s Cloud Attack Path Analysis
In addition to prioritizing and visualizing attack paths, Orca also shows security teams exactly which issues need to be remediated to diffuse the attack paths. Orca prioritizes issues for remediation if they are also part of other attack paths, allowing teams to ‘break’ several attack paths with a single remediation effort.
In short, Orca helps teams remediate more strategically, improving efficiency and ensuring that the truly dangerous issues are remediated faster, which in turn helps avoid damaging attacks and data breaches.
Learn More
Want to learn more about Attack Path Analysis and Prioritization? Visit our Context-Aware Security page, watch the 2-minute video Orca Bytes: Attack Path Analysis, or watch our Breaking Waves LinkedIn Live interview with Oren Sade, Technical Product Leader at Orca Security.
Want to get more hands on? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Security Platform can help you identify and address risks.