The Challenge
Existing Cloud Security Tools Lack Context and Create Alert Fatigue
Cloud environments and cloud native applications are the cornerstone of every company’s quest to scale their business and deliver value to their customers. Yet, existing cloud security solutions create challenges in scalability, ease-of-use, and risk prioritization–that’s why DevOps and security teams embrace the Orca CNAPP Platform that offers a revolutionary way to overcome these challenges.
Traditional agent-first approaches lead to overhead and friction for DevOps and security teams, while leaving visibility gaps for workloads where agents aren’t deployed.
Alert fatigue from solutions that produce long lists of alerts without context or effective risk prioritization burns teams out and results in missed critical alerts.
Separate point solutions for each layer of the tech stack and application development stage provide poor overall visibility, create more overhead and require manual correlation.
The Orca Approach to Cloud Security
Designed for organizations operating in the cloud who need complete, centralized visibility of their entire cloud estate and want to waste less time sorting through alerts and instead focus on remediating the actual risks that matter most, Orca Security is the leading agentless CNAPP that allows security teams to work smarter, not harder.
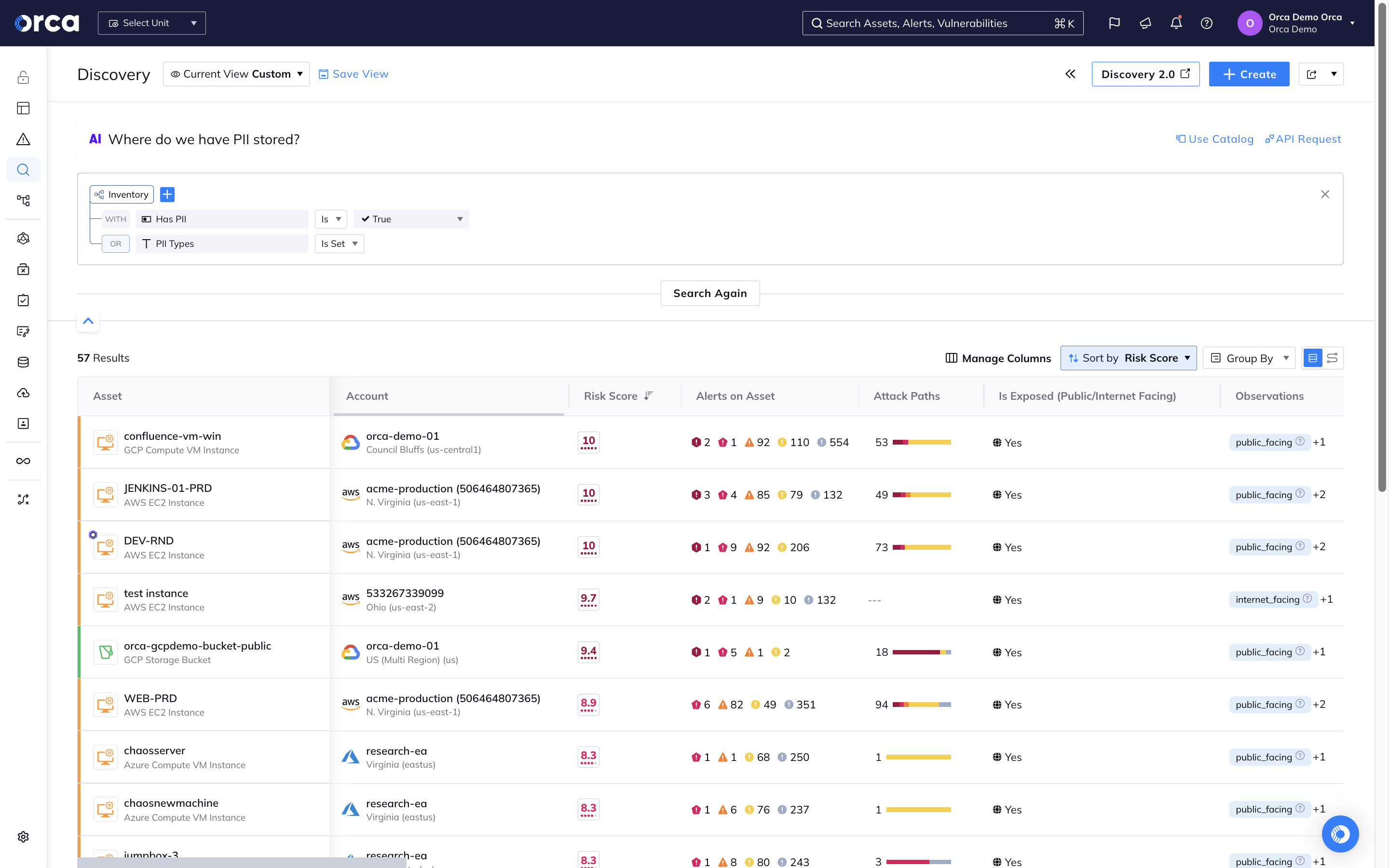
Understand and prioritize all your cloud security risks
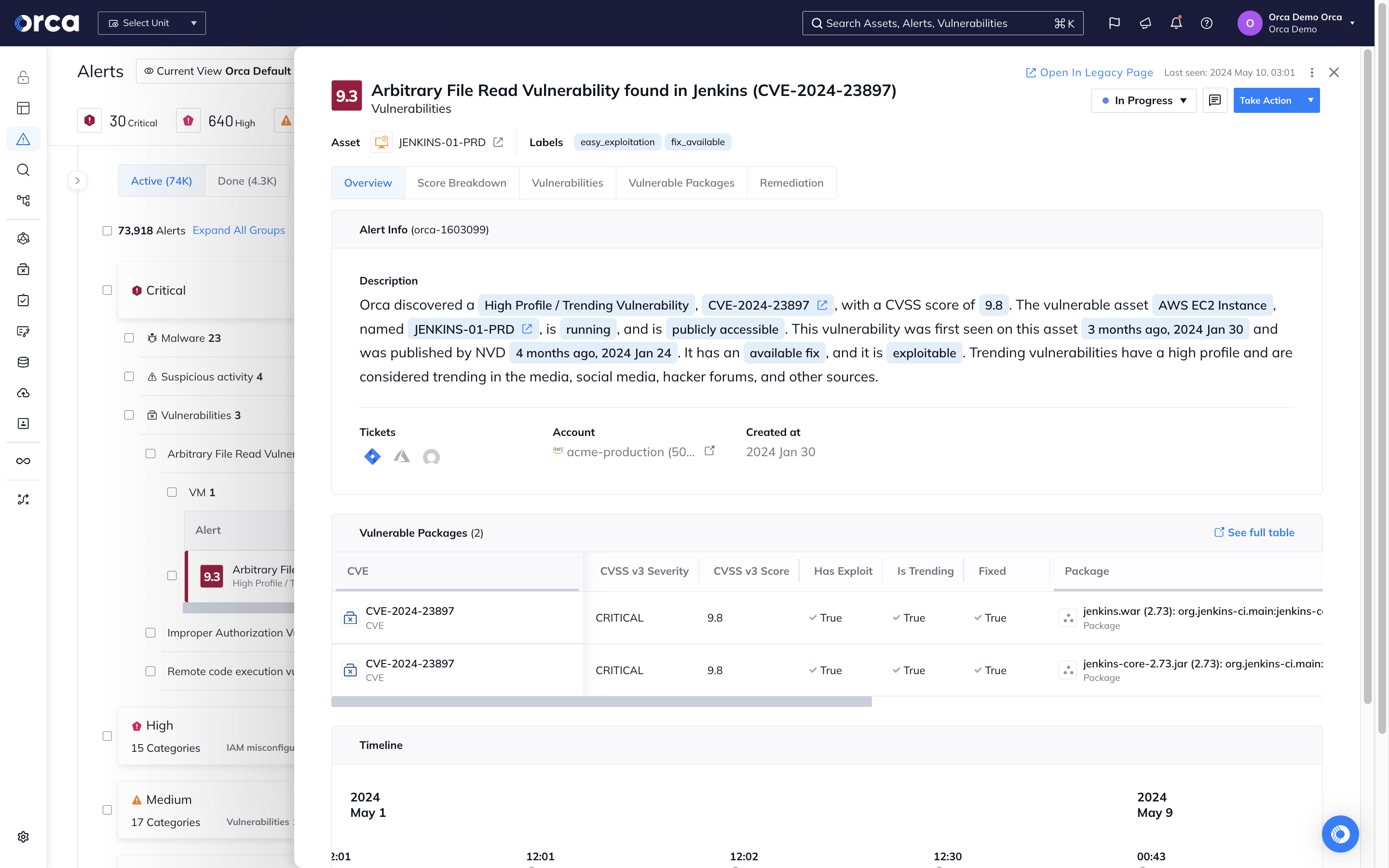
Orca’s patented SideScanning™ technology is a radical new approach that addresses the shortcomings of traditional agent-based cloud security solutions.
- Orca collects data directly from your cloud configuration and the workload’s runtime block storage out-of-band.
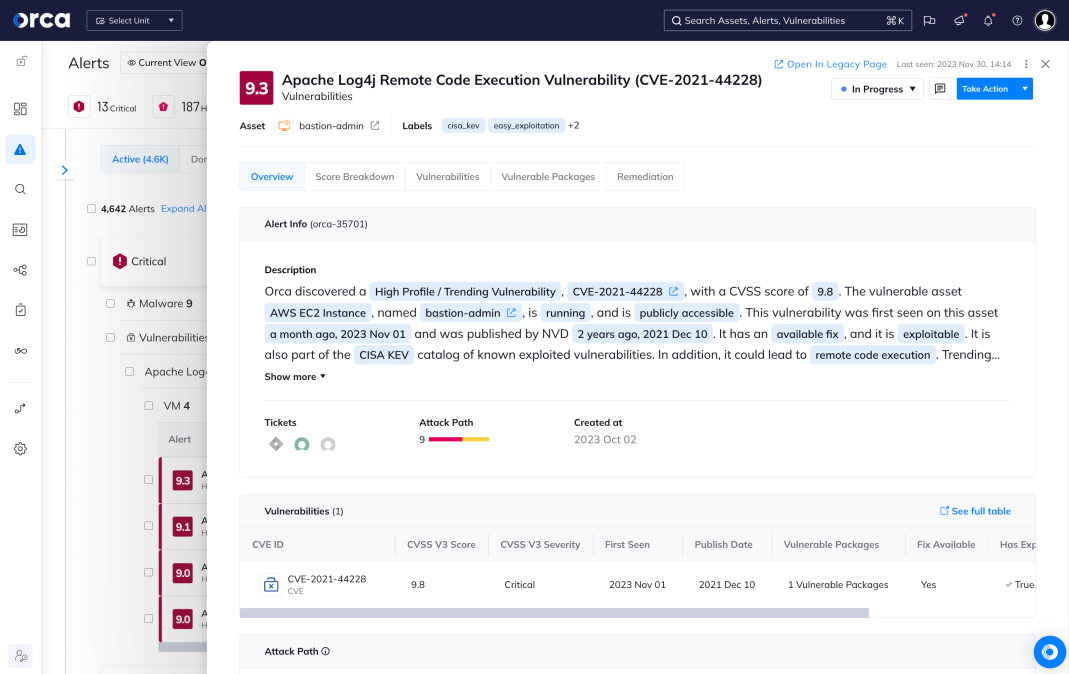
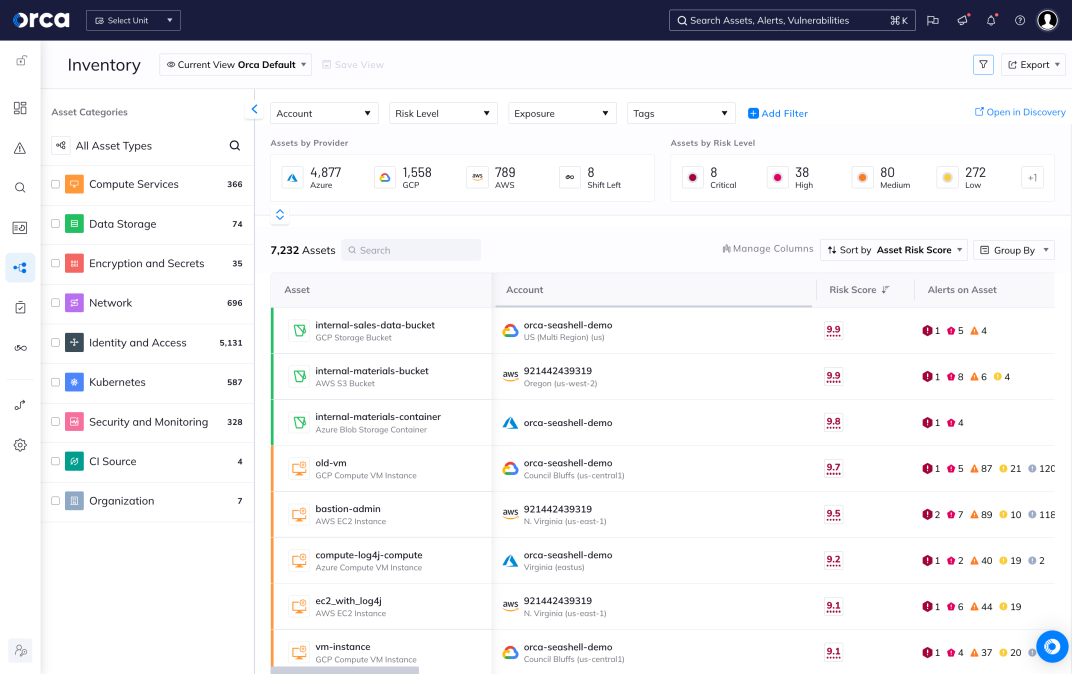
- Within minutes, Orca finds and prioritizes your most critical cloud risks, including vulnerabilities, malware, misconfigurations, lateral movement risks, IAM risks, sensitive data at risk, and suspicious activities.
- As a purpose-built CNAPP, Orca combines workload-deep intelligence with cloud configuration metadata in a truly unified data model.
- With Orca you can easily query your entire environment to investigate risks and remediate issues.
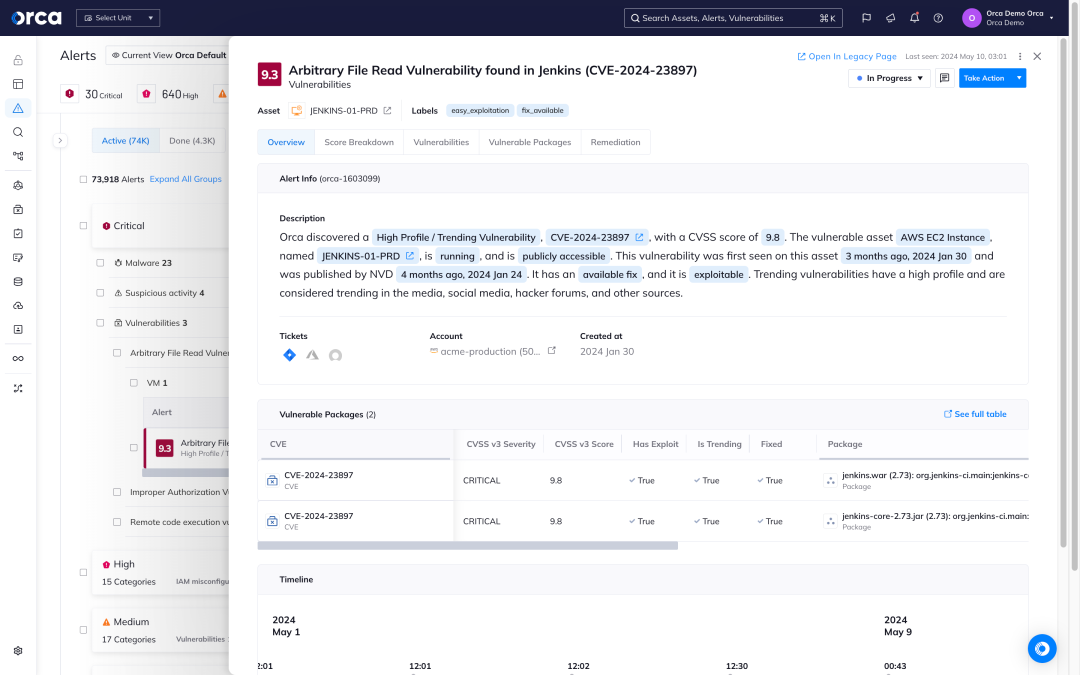
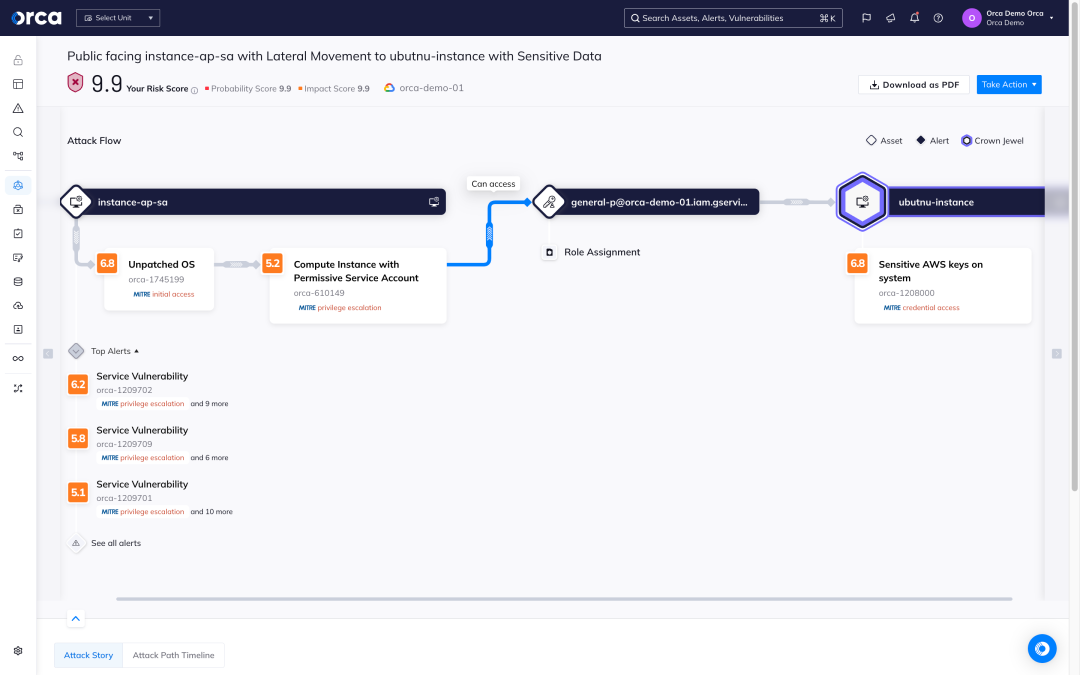
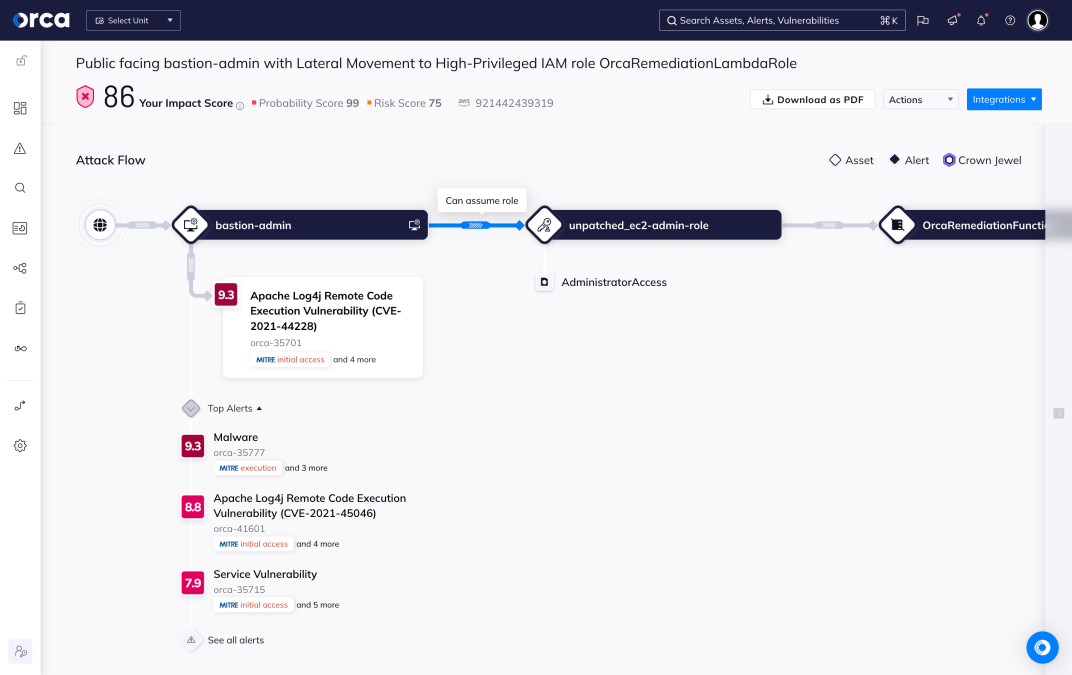
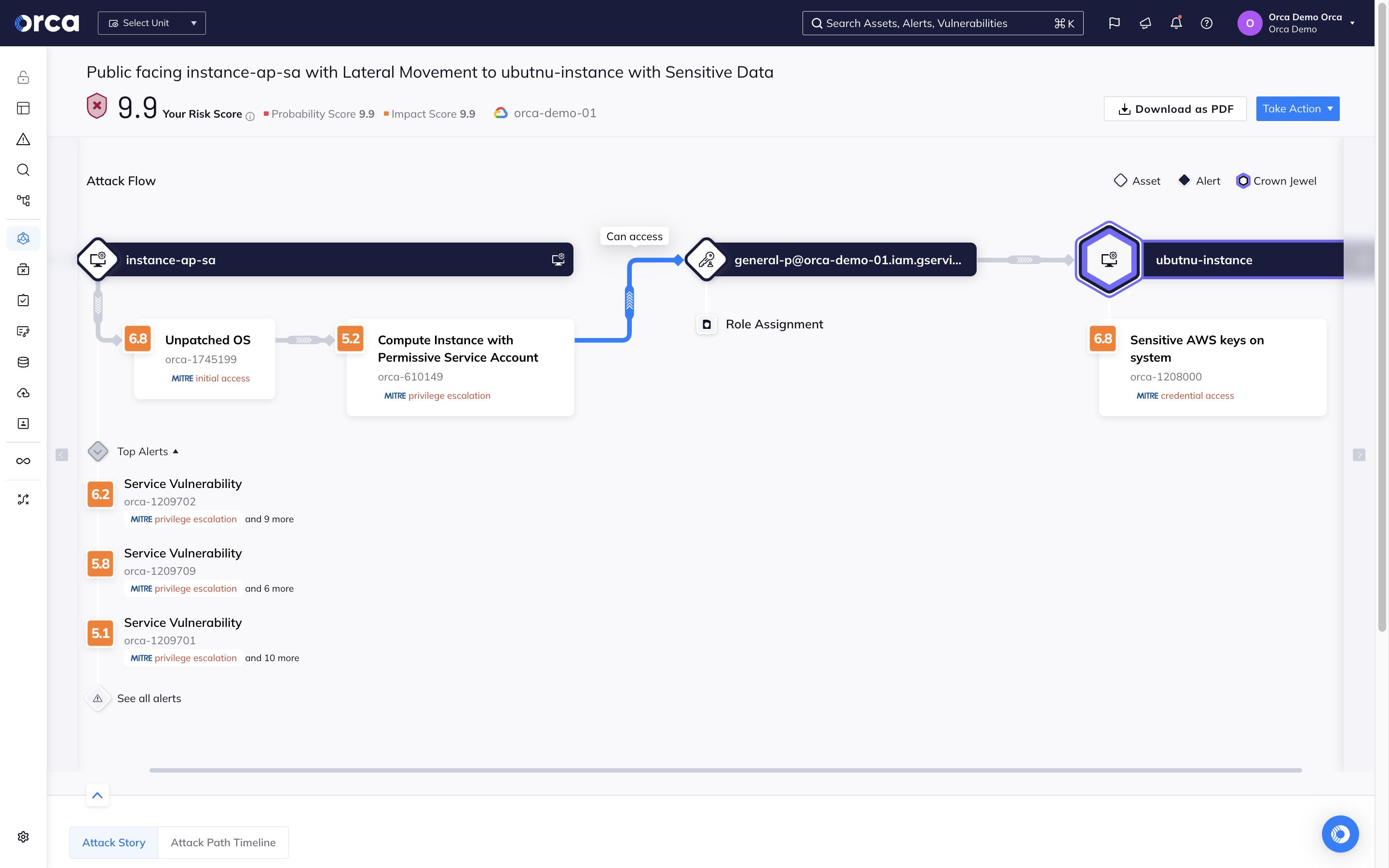
Strategic remediation with attack path analysis
With multi-cloud Attack Path Analysis, Orca helps security teams work smarter and utilize their resources in the most effective way. Instead of trying to fix all risks, which is simply impossible, Orca shows teams which cloud security risks:
- Endanger their most critical business assets
- Are part of the most attack paths with the highest severity
- Affect the most cloud assets
- Are exposed by the most cloud assets
Armed with this intelligence, security teams will instantly know where their time is spent best, relieving alert overload and burnout, as well as dramatically improving security outcomes.
Accelerate cloud security outcomes with AI
The Orca Platform widely leverages AI to enhance detection of risks, simplify investigations, and speed up remediation – saving cloud security, DevOps, and development teams time and effort, while significantly improving security outcomes:
- Accelerate cloud security remediation by applying AI-generated instructions created for the platform of your choice.
- With cloud asset search that is as intuitive as asking a question, teams across the organization are empowered to make data-driven decisions.
- Quickly apply identity policies to effortlessly right-size permissions and entitlements.
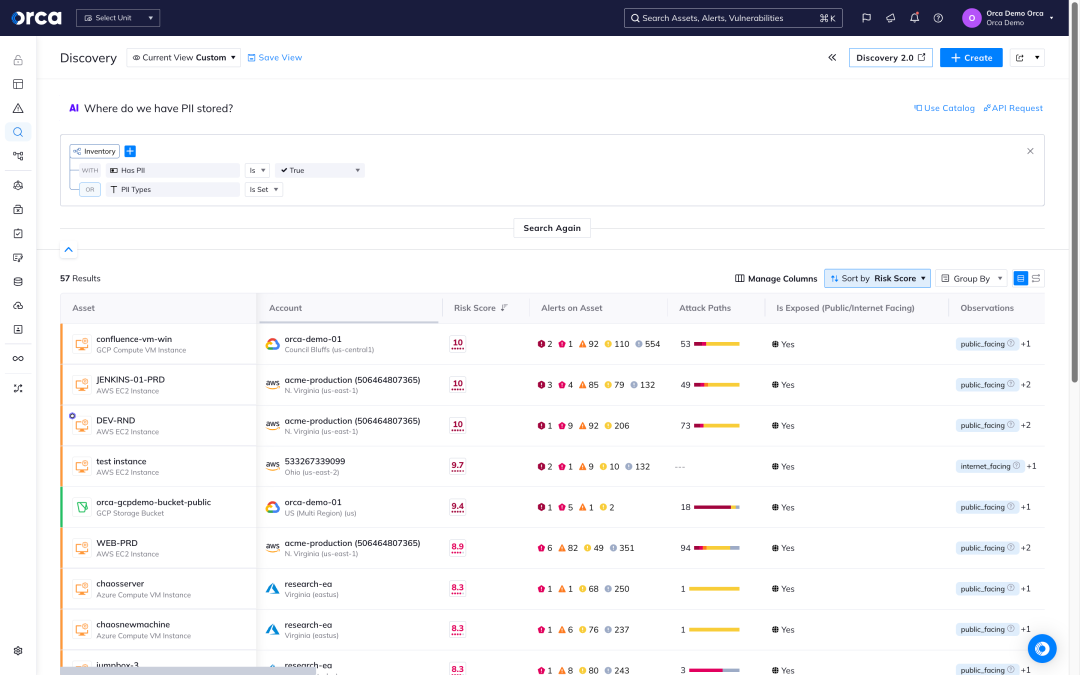
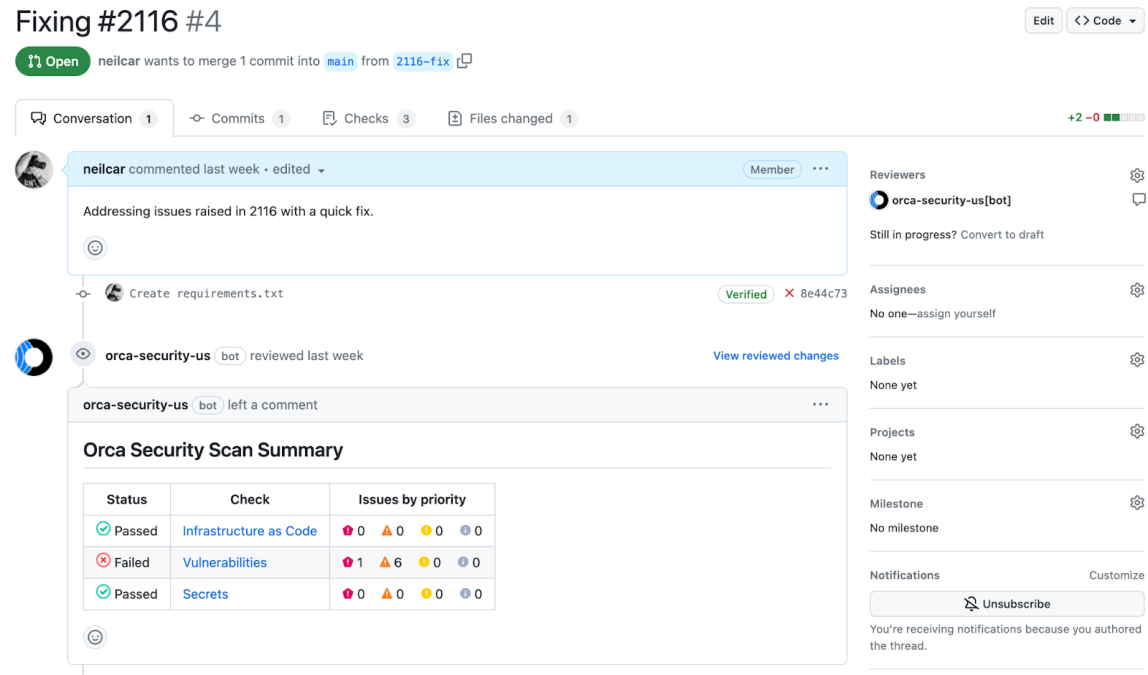
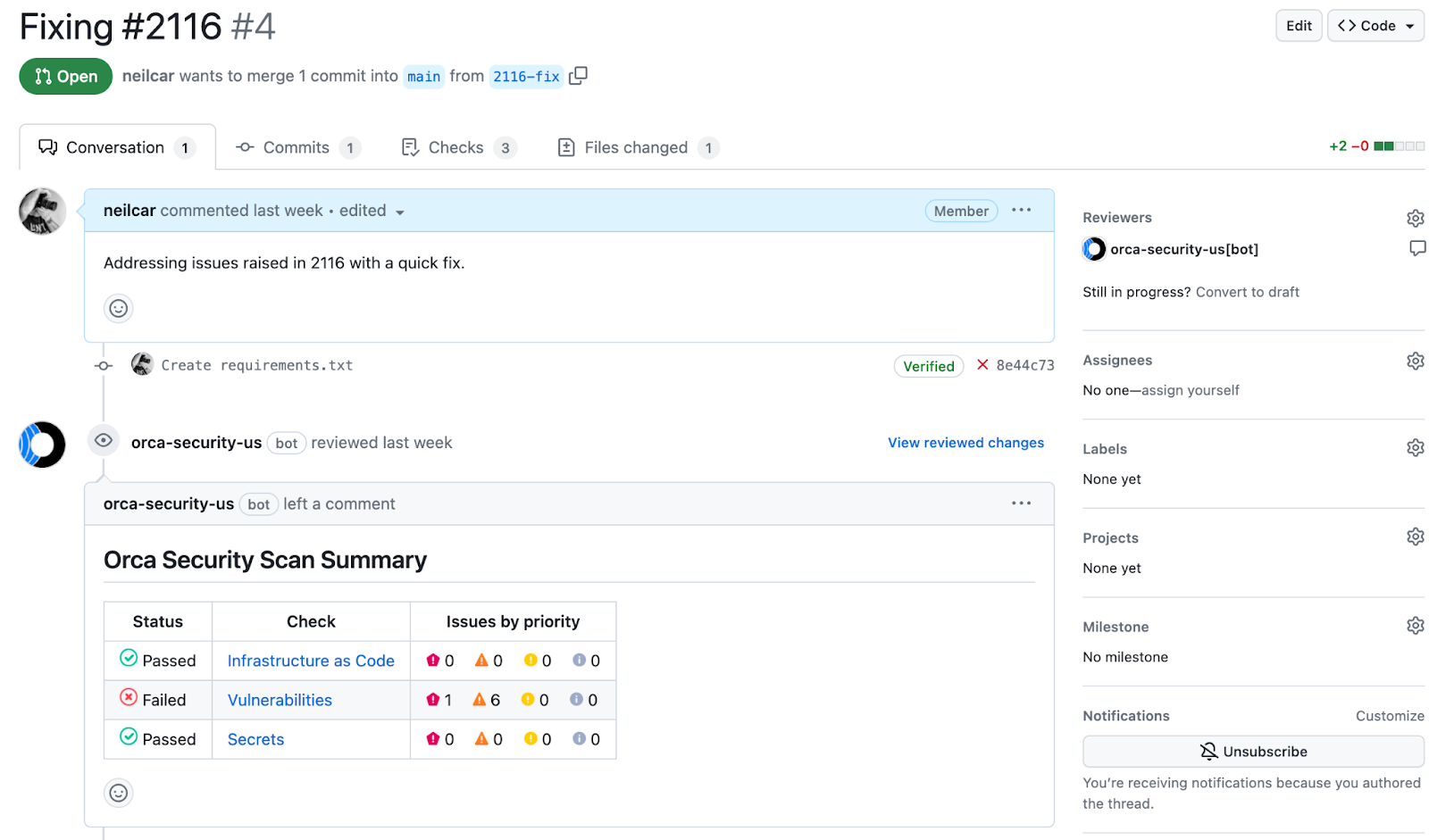
Security across the full application lifecycle–and back again
Securing cloud native applications starts in development by identifying vulnerabilities and misconfigurations as code is built, before it’s deployed to production. Yet, security teams still need to coordinate with development and DevOps for remediation – now made possible with Orca.
- Orca allows organizations to apply security policies early in the development process to avoid issues making it to production.
- Automatically run compliance and security checks as part of the CI/CD process, including IaC template and container image scanning.
- Orca traces findings from the production environment to their code origins, greatly accelerating the remediation of risks in cloud-native applications.