The Challenge
Incomplete Visibility
Monitoring APIs and related security risks across multi-cloud environments requires comprehensive visibility and continuous API discovery, but existing solutions dedicated to the protection of web traffic and APIs typically require agent-based or network-based controls to get deep visibility. The result is high maintenance costs, incomplete coverage, limited API inventory, scalability challenges and lack of wider cloud security context.
Solutions requiring agents lead to blind spots, an incomplete API inventory, scalability problems, performance degradation and high TCO.
API Security point solutions lack wider context on cloud misconfigurations, workload vulnerabilities, malware, lateral movement exposures or other risks.
Maintaining multiple security solutions and correlating data leads to alert fatigue and missed alerts.
Our Approach
Complete API Discovery, Posture Management, and Drift Detection
Unlike other solutions, the Orca Cloud Security Platform provides security teams with a full inventory of APIs and related web domains in their cloud estate, as well as API-related security and compliance risks, without a single agent. Instead of viewing siloed API risks, Orca also considers other risks, including vulnerabilities, misconfigurations, malware, the location of sensitive data, and lateral movement risk, to effectively prioritize the API risks that present the greatest danger to your cloud estate.
Comprehensive Coverage
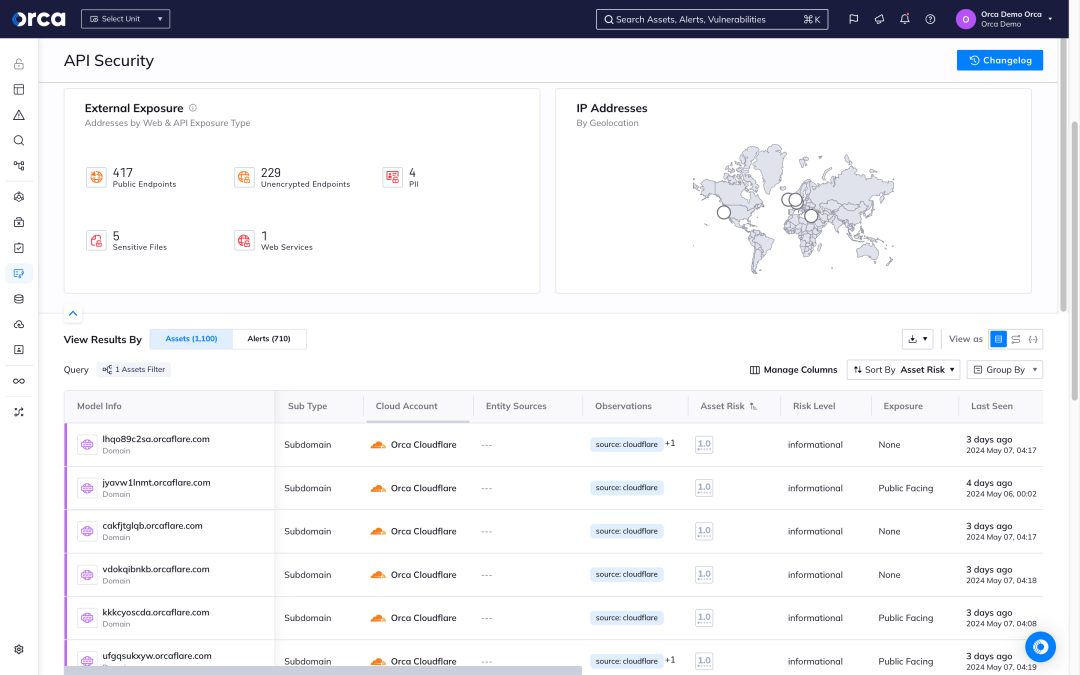
Gain an extensive view of the API attack surface across your cloud estate, including newly added assets, without blind spots.
Quick and Accurate
Fast and frictionless deployment – get an accurate API inventory in minutes without the need for agents, edge workers, or bringing in a vendor to analyze your logs.
Risk Prioritzation
Orca effectively prioritizes risks by leveraging its insights into APIs as well as risks found in cloud workloads, configurations and identities, to understand the risk combinations that pose the greatest danger.
Orca leverages its SideScanning™ technology and comprehensive insights into cloud workloads and configurations to provide security teams with a 360-degree view of APIs and related risks, effortlessly scaling as your cloud estate grows.
Continuous API discovery and inventory
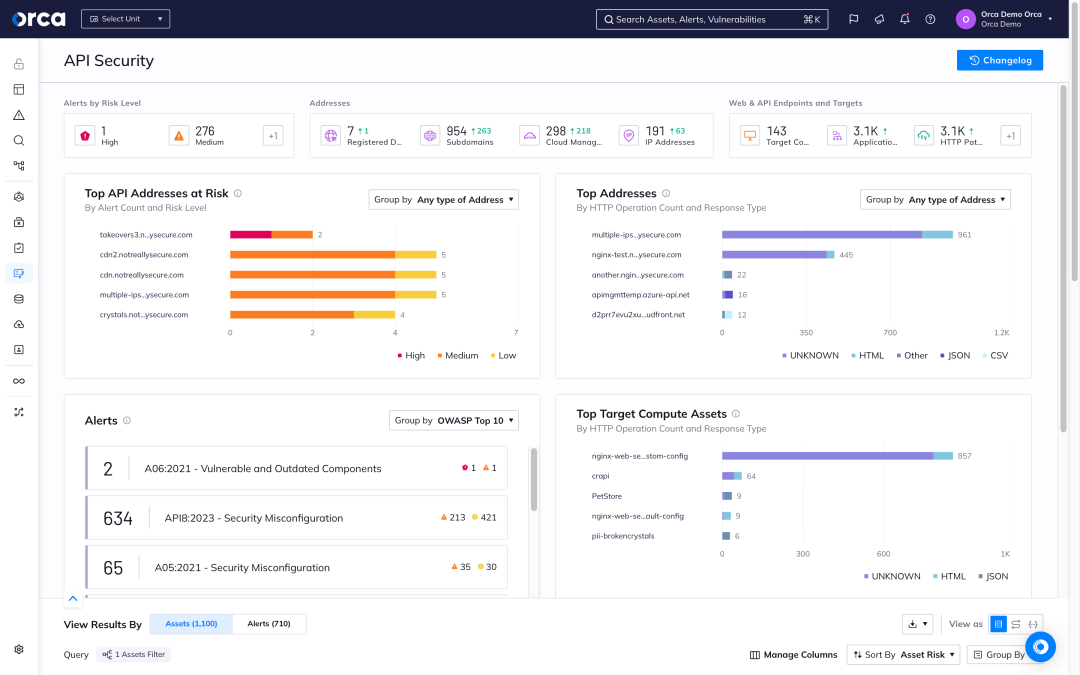
Orca’s API dashboard provides cloud and application security teams with an overview of all high-level API data and alerts. Orca’s API discovery is automatic and continuous and provides complete visibility into all the APIs deployed in your cloud.
- Track and analyze your managed and unmanaged API assets, including applications, domains, subdomains, path groups, users, and API endpoints.
- Consult interactive API maps showing all API endpoints, requests, and server responses.
- Get a real-world picture of publicly exposed APIs with screenshots for quick in-app view.
- Get answers to questions such as: “What assets are accessible from the Internet, and what do they expose? Or “How many API endpoints contain access to personally identifiable information (PII)?”
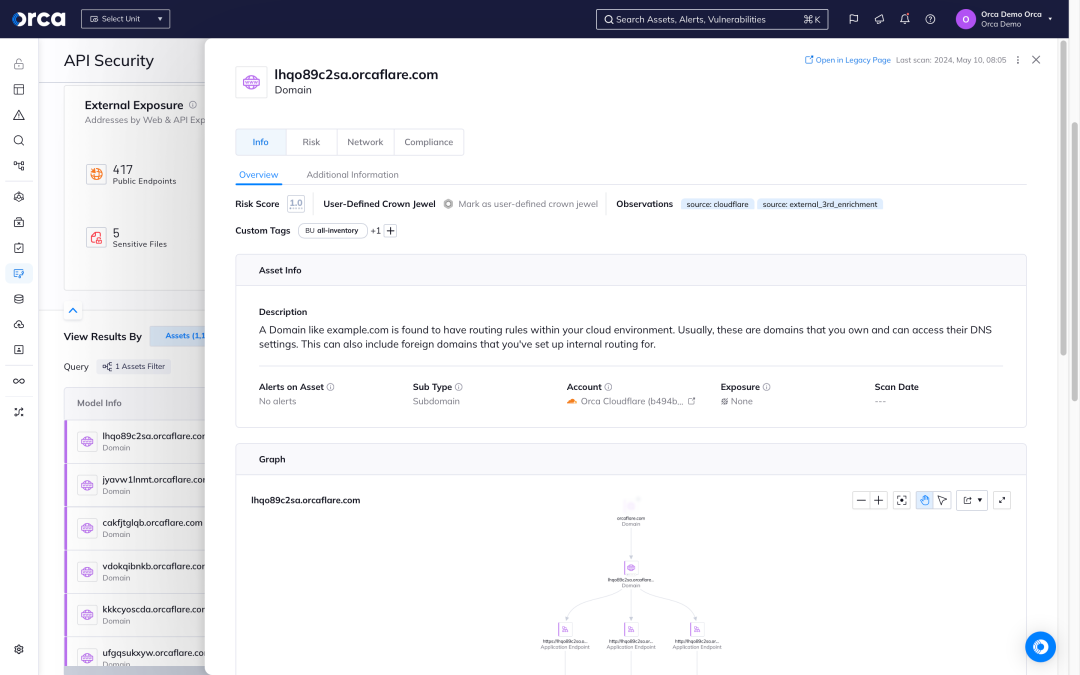
API security risk prioritization and compliance
Orca scans your entire cloud estate and surfaces potentially hazardous API security risks—including alerts from the OWASP API Security Top 10—providing actionable data and remediation suggestions.
- Prioritize risks and accelerate mitigation actions with severity scores and valuable context-based data such as the location of PII, API public exposure, and more.
- Easily identify “what is externally exposed, that shouldn’t be?” with automatic suggestions.
- Take preventive steps to reduce the API attack surface. Search for the risks associated with a particular domain or subdomain, or alerts over a particular time period.
- Stay ahead of audits and adhere to common compliance frameworks like PCI-DSS with linked-alerts provided by Orca.
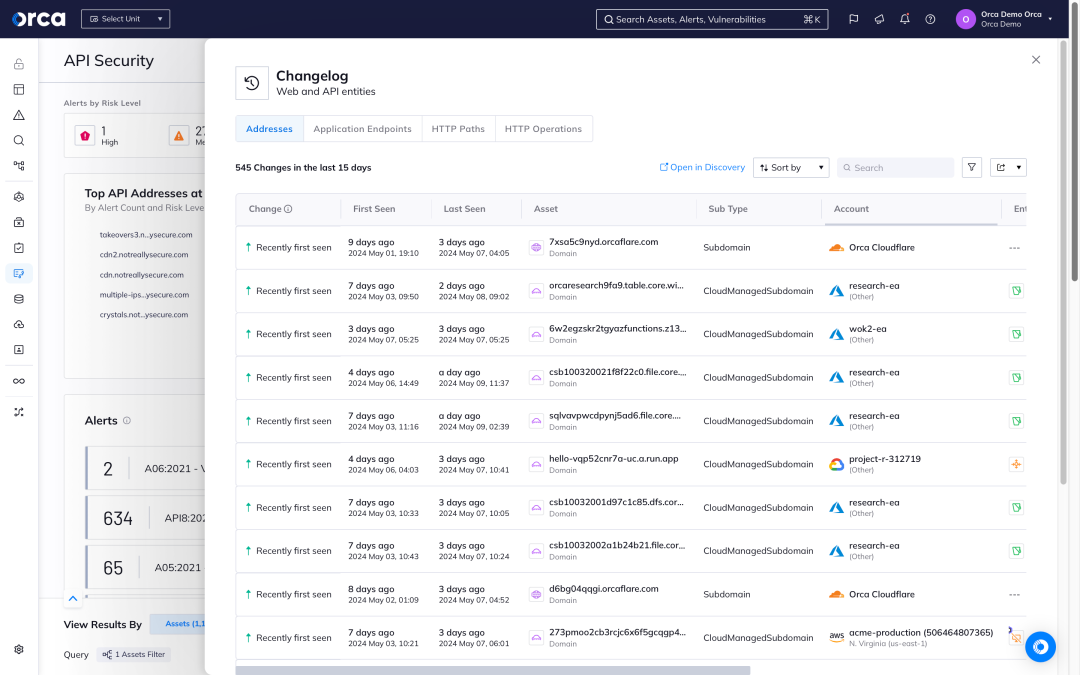
API security drift detection and management
Orca ensures that potentially risky API changes and behaviors aren’t missed by security and governance teams.
- Continuously monitor API behavior and usage and alert teams to potentially unwanted API drift.
- Easily track newly added and removed applications, domains, subdomains, API paths, and API operations on those paths.
- Access a Swagger documentation view that can be used to easily compare intended API policy vs. current usage.
Complete and Prioritized Cloud Risk Intelligence
Frequently Asked Questions
API Security protects APIs from threats, vulnerabilities, misconfigurations, exposures, and other risks. The discipline combines strategies, solutions, and practices to continuously discover and inventory APIs (including shadow APIs), detect and remediate API risks, and identify added and deleted APIs as well as API drift.
Cloud-native application protection platforms (CNAPPs) have emerged as a popular solution for API Security in the cloud, integrating it with other necessary cloud security capabilities.
Demand for application programming interfaces (APIs) continues to skyrocket with hundreds of thousands of new applications being introduced every day. The popularity of APIs among developers and entrepreneurs have made them attractive targets for hackers to exploit.
APIs are a top attack vector for data breaches in enterprise web applications. API risks can disrupt or even suspend business continuity, presenting operational, financial, reputational, and regulatory consequences.
API Security calls for adopting technology that allows organizations to implement and sustain a strong API management framework. Once implemented, API Security focuses on several important practices, including:
- Discover and inventory APIs
- Detect and remediate API risks
- Support API Security at runtime
- Encrypt API requests and responses
- Implement API gateways
- Implement access controls
- Identify vulnerabilities
- Use quotas and throttling
- Validate API parameters
- Build threat models
Traditional API Security tools present several challenges, including:
- API sprawl: The inability to effectively inventory APIs, preventing organizations from discovering rogue endpoints.
- Lack of visibility into unmanaged APIs: Unmanaged APIs create vulnerabilities that can lead to security incidents.
- Understanding high vs. low priority API risks: API Security tools lack visibility into the cloud plane or workload data. As a result, they can’t effectively communicate or contextualize API risks.
- APIs change fast and often: The speed of cloud-based application development and growing adoption of CI/CD processes make it unrealistic to manually track changes in APIs. Each API change requires the manual reconfiguring of traditional security tools.
- Understanding API risk exposure is difficult: As a result of incomplete API inventories, not keeping track of API changes, and incomplete insight into context, organizations can’t easily get answers to their API exposure questions.
However, Orca Cloud Security Platform solves these problems by offering agentless API Security in combination with comprehensive insights into cloud workloads and configurations to provide security teams with a 360-degree view of APIs and related risks, effortlessly scaling as your cloud environment grows.
Orca Cloud Security Platform offers API Security that instantly helps organizations identify, prioritize, and address API misconfigurations and security risks across their entire cloud estate, without requiring agents or network changes. Within minutes of deploying the solution, Orca provides a complete and continuously updated inventory of managed and unmanaged APIs, contextualized alerts on potentially risky API drift and changes, and insight into API misconfigurations and vulnerabilities with actionable remediation steps.
Orca combines detected weaknesses in APIs with other identified cloud risks to effectively prioritize the API risks that are most critical. The result allows security teams to focus on the time-sensitive alerts that matter most, saving time, accelerating response, and eliminating alert fatigue.