How Orca Security Compares to Prisma Cloud
Orca Leads with a Purpose-Built Platform
Since 2019, Palo Alto Networks has made 8 acquisitions, such as RedLock, Twistlock, and Bridgecrew, as part of Prisma Cloud–putting all of these different, standalone products together in a single UI. This strategy offers organizations many features but poor usability, reliance on agents, difficulty in onboarding, and endless operationalization challenges. With Orca Security, we’re focused on a single, comprehensive Cloud Security Platform that enables powerful cloud security outcomes for any organization.
Features

Deployment
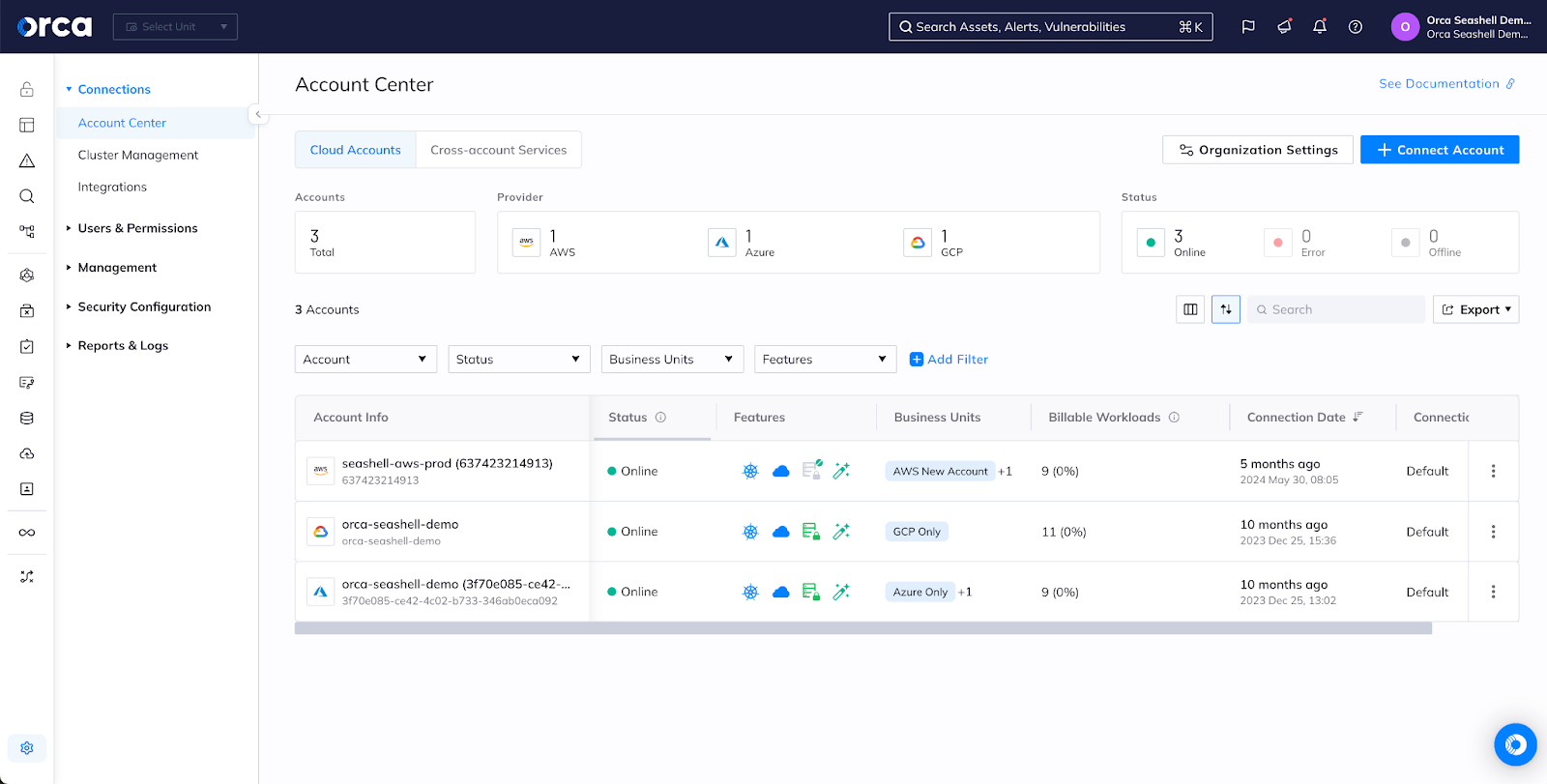
Easy Onboarding
Simple 3-step activation model scans your cloud accounts, assets, workloads, data, and identities across multiple clouds without having to deploy agents
Difficult Activation and Optimization
Multi-stage activation includes onboarding users to multiple locations. Agent-based Defender deployments need to be done alongside every single workload
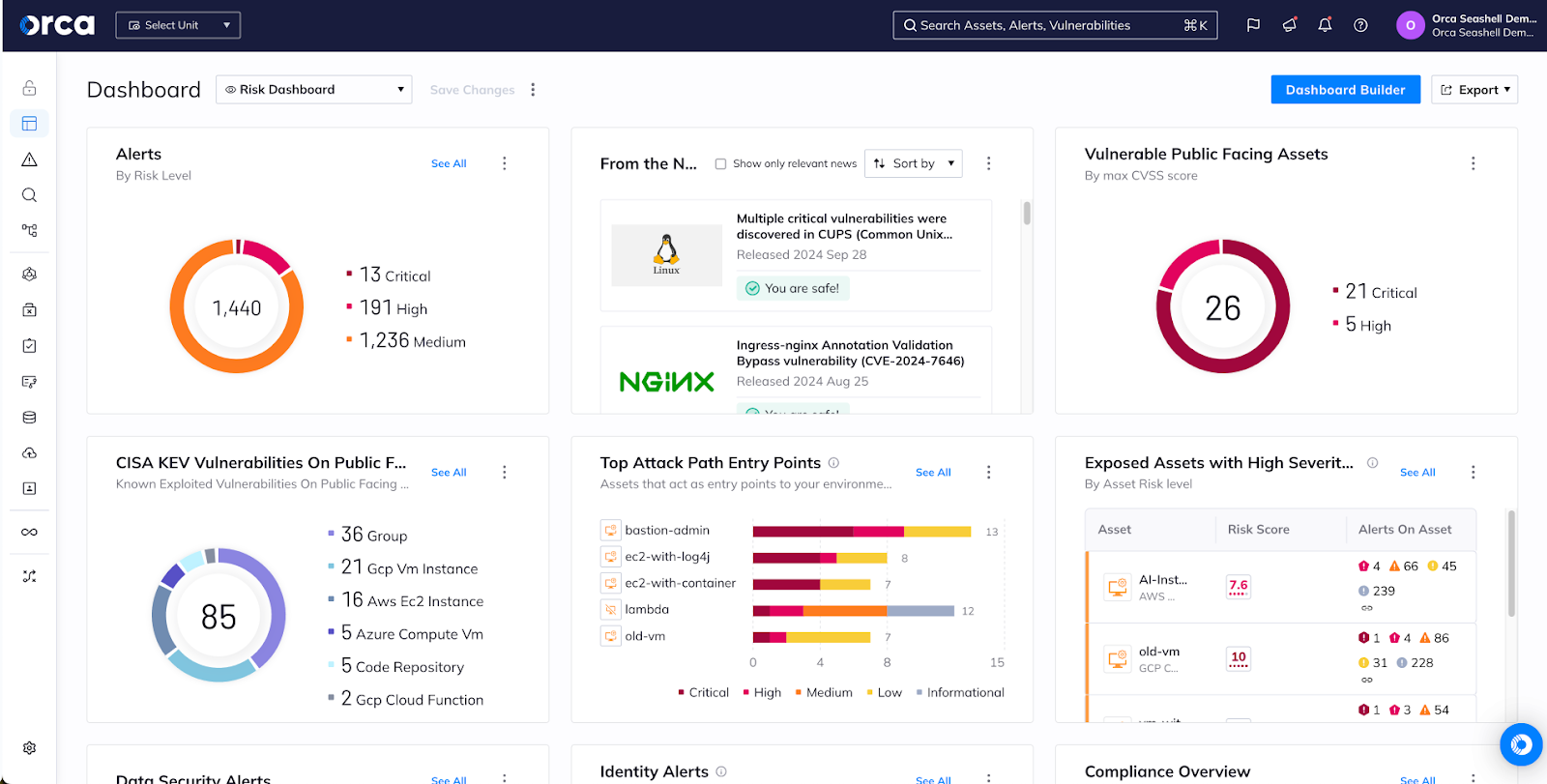
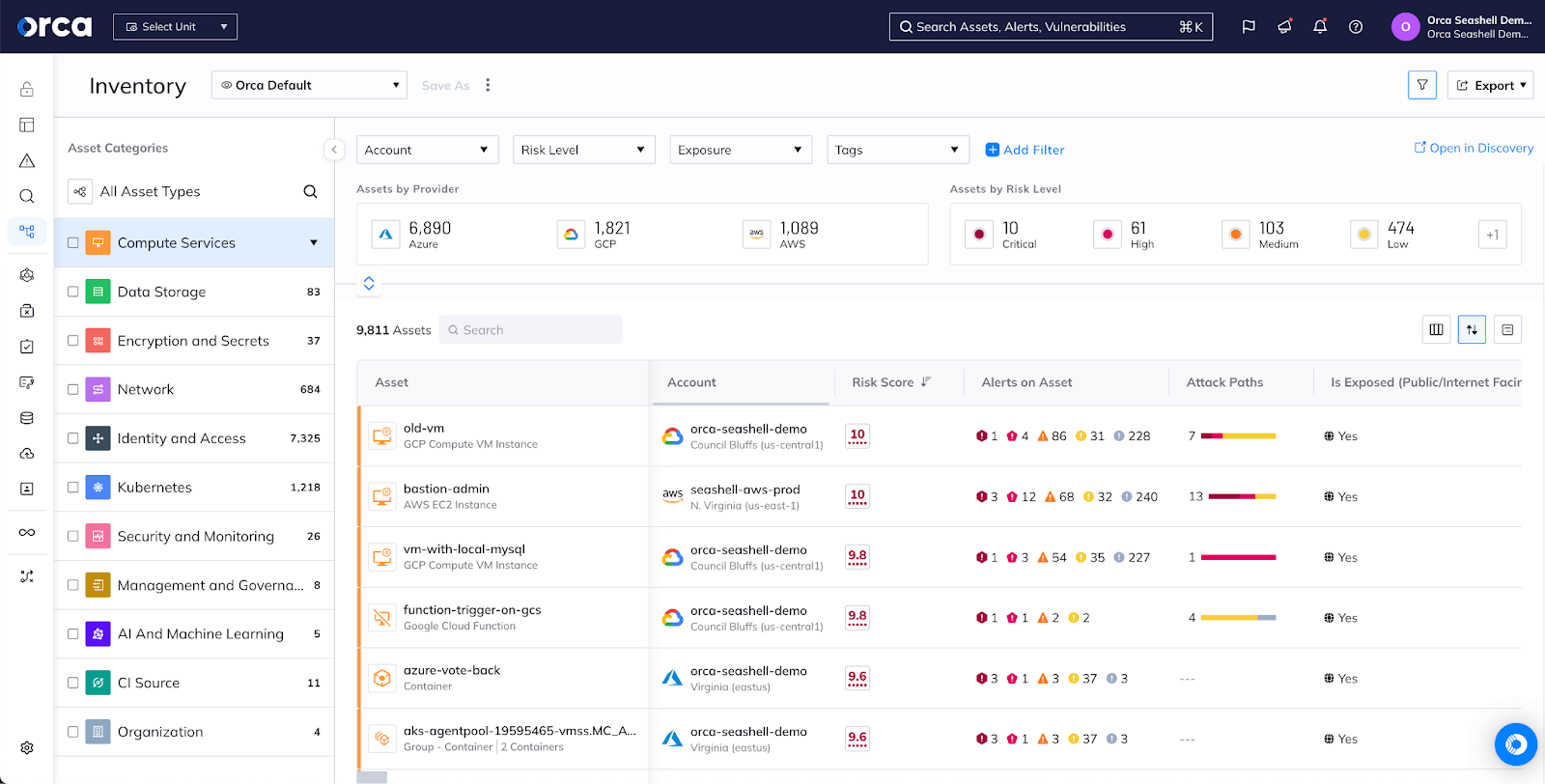
Asset Inventory
Unified
Continuously monitor public cloud services and configurations, entitlements and identities, workloads and applications, all from a single dashboard
Fragmented
Separate tabs for critical parts of the product due to separation between RedLock and Twistlock acquisitions. “Darwin” release adds limited, combined dashboards that don’t work very well.
Compliance
Centralized
125+ compliance frameworks with all data and policies shown in a single dashboard for seamless reporting
Lots of Windows to View
Many frameworks, but findings spread across several locations between cloud infrastructure compliance (RedLock) vs. cloud workloads (Compute/Twistlock) adds management overhead
PII Detection
Seamless and Comprehensive
Automatic detection of PII across buckets, VMs, and databases
An Additional Subscription for Limited Coverage
You pay more to only get coverage of AWS S3 buckets and Azure Blobs
Shift Left Security
Unified with Context
One CLI and dedicated Shift Left Dashboard for viewing all of your container image and IaC scans. Unified policy management of all your CI/CD policies
The Opposite of Unified
Disintegrated capabilities from Twistlock and Bridgecrew leave results and policies spread across multiple windows and locations. Build policies are disconnected from runtime policies due to multiple acquisitions
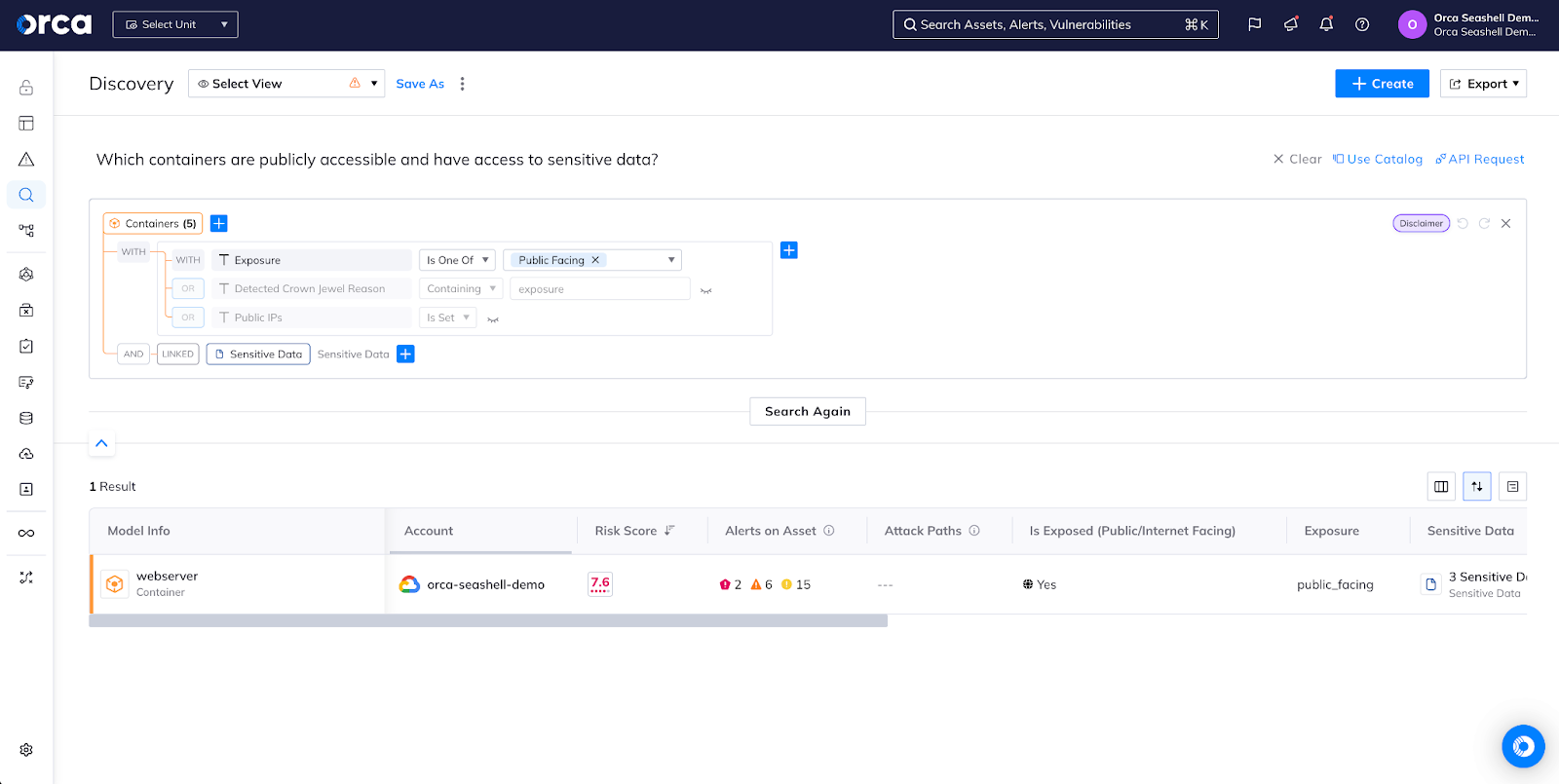
API Security
Simple and Comprehensive
Automated inventory of all interconnected APIs and web domains. Capabilities integrated with agentless SideScanning technology, nothing new to activate. Prioritize risks, including external exposure, mapped to OWASP API Security Top 10 and contextualized with all other risks
Activate Another Module
Web Application and API Security (WAAS) module requires Defender agent to be installed and activated, adding overhead and costs. API Security requires traffic mirroring or Defender agent. Risks are siloed, not shown in context to other cloud issues
A purpose-built platform to simplify cloud security
To secure the cloud, security teams want to easily onboard cloud accounts, quickly activate security capabilities, and avoid operational overhead from traditional, agent-based solutions–ensuring comprehensive coverage across the entire cloud tech stack.
With Orca Security, you benefit from a purpose-built Cloud Security Platform that addresses all of your cloud risks and features our patented SideScanning technology that covers your entire cloud estate without agents
Prisma Cloud by Palo Alto Networks was stitched together by endless acquisitions, including Evident, RedLock, Twistlock, PureSec, Aporeto, and Bridgecrew. This results in a complicated user experience and agent-based deployments that lack comprehensive coverage and are difficult to operationalize.
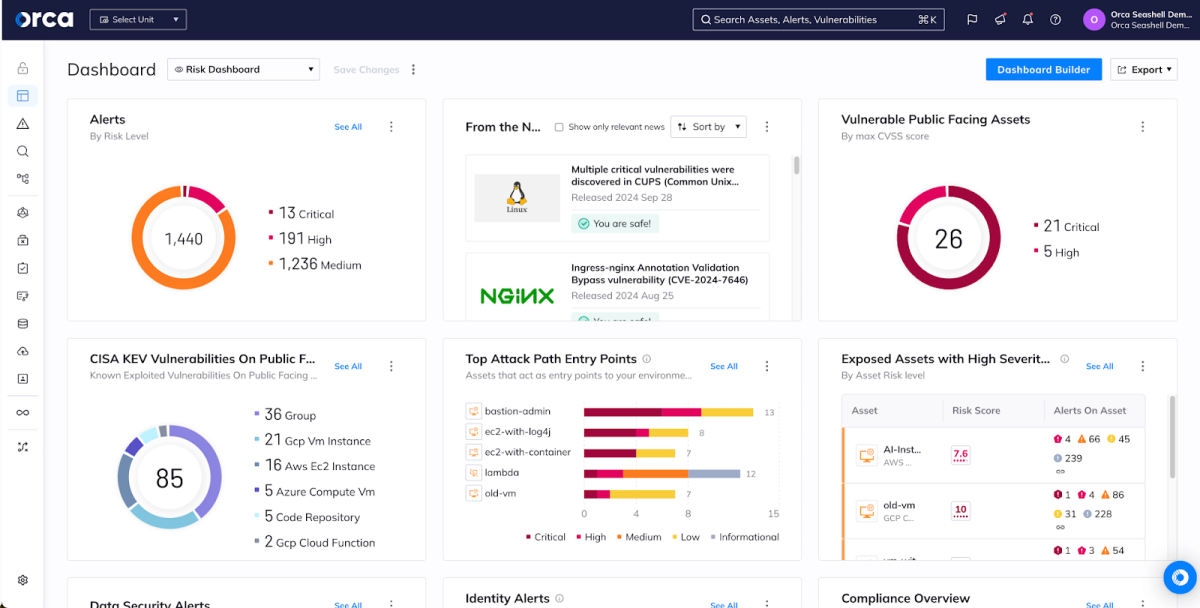
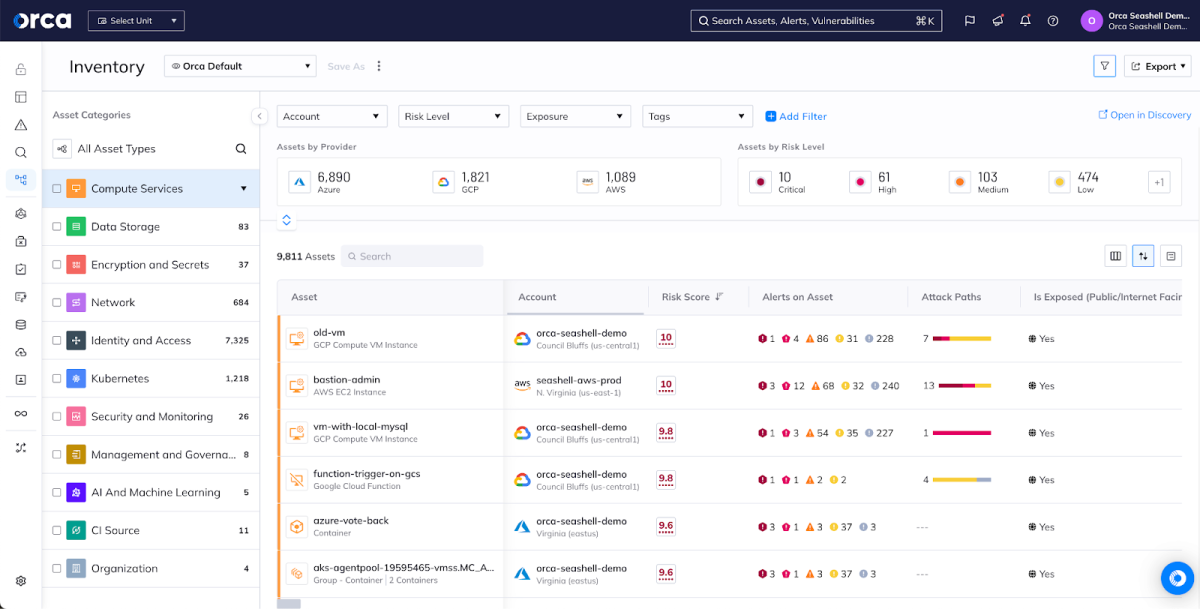
The agentless security pioneer
Orca’s patent-pending SideScanning technology quickly and easily scans all of your Linux and Windows workloads, including cloud VMs, containers and Kubernetes applications, and serverless functions, without the need to deploy and update agents like Prisma Cloud Defender. This provides you with instant-on security and complete coverage for all your workloads and applications that Prisma Cloud can’t match. Palo Alto grafted an ‘agentless’ option into Prisma Cloud but it offers limited coverage, complicating deployment instead of simplifying it.
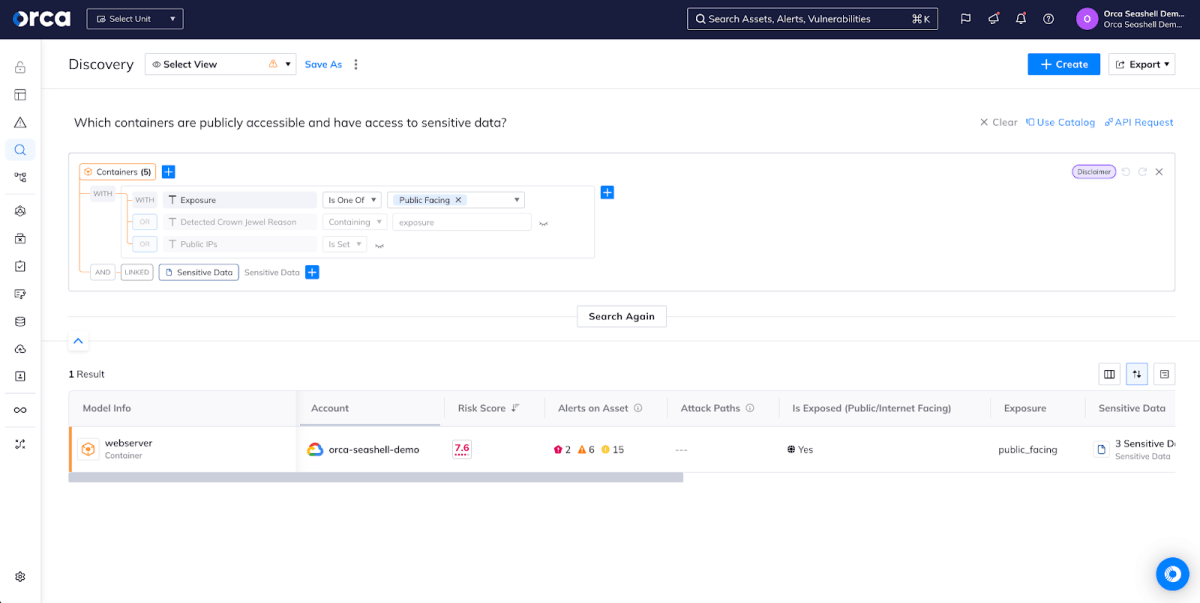
A unified data model
The Orca Platform brings all of your data into a unified, easily-queryable location. With Orca’s Unified Data Model, you can view assets, compliance status, risks, and security incidents from one dashboard, rather than constantly hopping between multiple redundant screens within Prisma Cloud or learning a complicated new query language (RQL). Orca is built from the ground up to give you control of your data.
Simple, predictable pricing and best-in-class support
Orca takes a simple pricing approach that allows you to focus on securing your cloud environments and applications rather than worrying about calculating “credits”. We’re also available when you need us to help you scale your business with confidence.