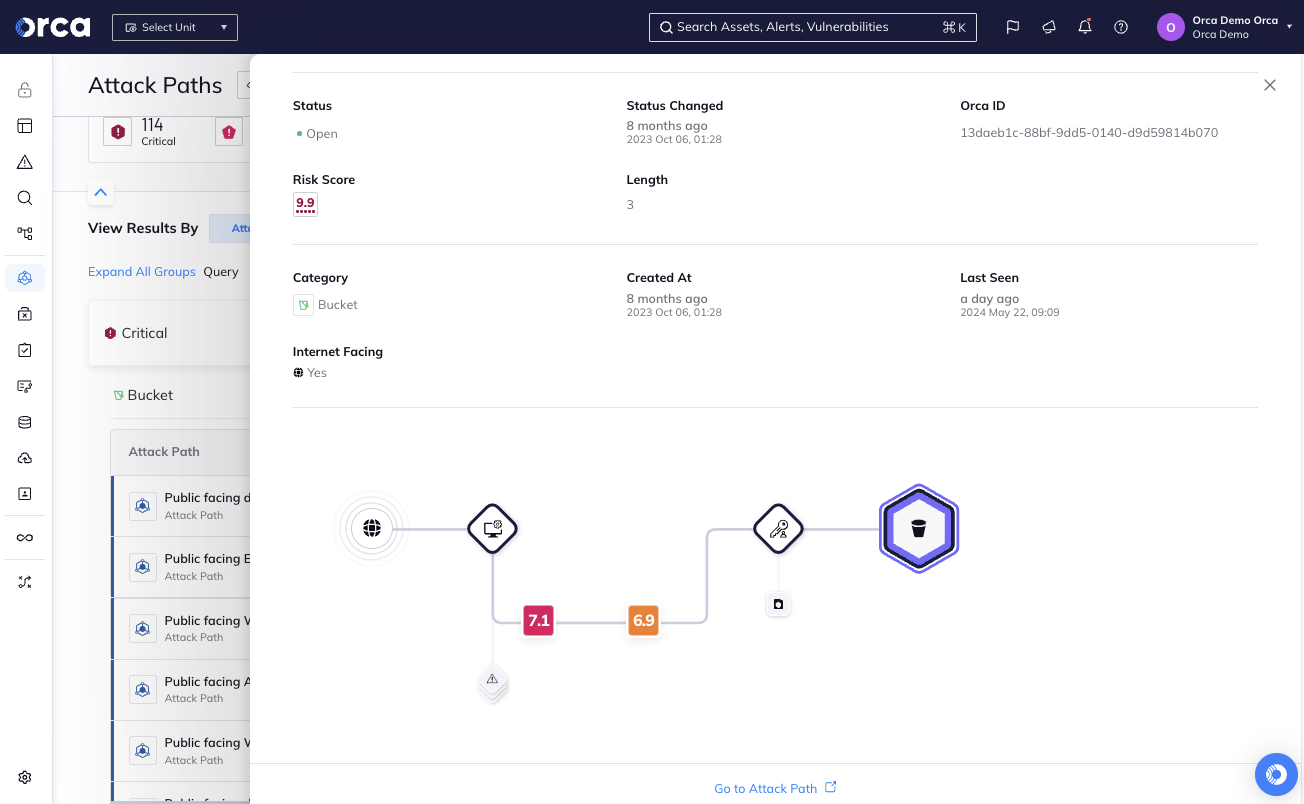
Orca Security Media Kit
Media contacts, screenshots, logos, CEO headshots, and our boilerplate.
Brand Assets

Orca Security Logo
Download contains PDF, PNG and SVG files for print and digital use.
Brand Guidelines
Documentation for our partners on how to use the Orca logo, colors and typography.

CEO
Download the official headshot of Gil Geron, Co-Founder and CEO of Orca Security.
About Orca Security
At Orca Security, we’re on a mission to make it fast, easy, and cost effective for organizations to address the critical cloud security issues so they can operate in the cloud with confidence.
Orca Security delivers the industry-leading Cloud Security Platform that identifies, prioritizes, and remediates security risks and compliance issues across your cloud estate spanning AWS, Azure, Google Cloud and Kubernetes.
The Orca Platform connects to your cloud environment in minutes with our patent-pending Sidescanning technology to provide you and your teams with complete coverage across all cloud risks – spanning misconfigurations, vulnerabilities, identity risks, data security, and advanced threats. All of this data is populated into our unified data model, which automatically prioritizes the very few attack paths that put the organization in real risk, empowering teams to focus on what actually matters.
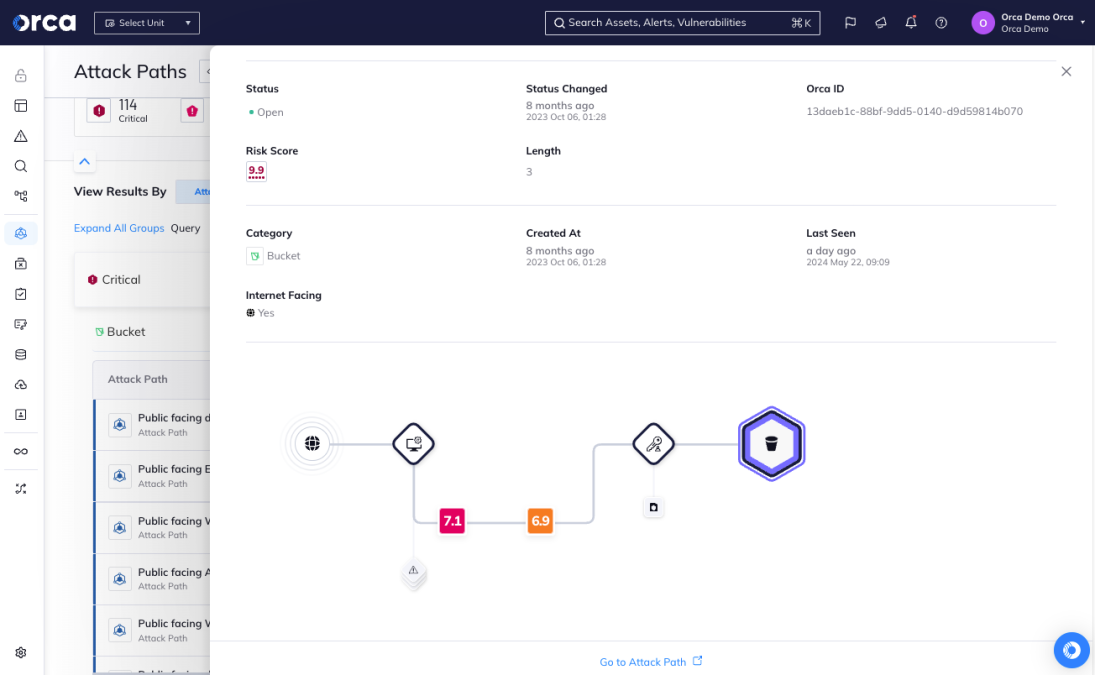
Press Inquiries
For press inquiries, please reach out to our PR team:
For regular news and updates, please follow us on social media: