How Orca Security Compares to Tenable Cloud Security
Comprehensive, Easy Cloud Security
Orca isn’t just the original cloud security platform, it’s also the platform with the broadest, deepest coverage of all aspects of cloud security. Tenable’s Cloud Security service, based on the Ermetic acquisition, is incomplete in comparison.
Features

Deployment
Easy Onboarding
Simple 3-step activation model scans your cloud accounts, assets, workloads, data, and identities across multiple clouds without having to deploy agents
Less Easy Onboarding
Onboarding some cloud platforms to Tenable Cloud Security may require manual effort and many steps
Asset Inventory
Unified
Continuously monitor public cloud services and configurations, entitlements and identities, workloads and applications, all from a single dashboard
Identity-Obsessed
With its roots in Ermetic, Tenable Cloud Security overindexes on identity, making it correspondingly harder to understand everything else
Compliance
Comprehensive
125+ compliance frameworks with all data and policies shown in a single dashboard for seamless reporting
Limited
A limited number of frameworks that lack visibility across infrastructure, data, identities, and workloads
Attack Path Analysis
Automated and Interactive
Interactive dashboard, with automated impact score, surfaces toxic combinations of risks so teams can prioritize and fix the top 1% of issues. All risks mapped to the MITRE ATT&CK framework
Only “Toxic Combinations”
Tenable Cloud Security doesn’t show multistage attack graphs across all assets & risks, focusing instead solely on the combination of factors in a single asset
PII Detection
Seamless and Comprehensive
Automatic detection of PII across all cloud resources with integration into risk prioritization to ensure the largest risks to data are addressed
Disintegrated
While Tenable identifies sensitive data, this intelligence isn’t comprehensively integrated to prioritize risk
Shift Left Security
Unified with Context
One CLI and dedicated Shift Left Dashboard for viewing all of your container image and IaC scans. Unified policy management of all your CI/CD policies
Limited
Tenable Cloud Security only has limited support for Infrastructure-as-Code scanning in shift-left
API Security
Simple and Comprehensive
Automated inventory of all interconnected APIs and web domains. Capabilities integrated with agentless SideScanning technology, nothing new to activate. Prioritize risks, including external exposure, mapped to OWASP API Security Top 10 and contextualized with all other risks
Another Blind Spot
Tenable Cloud Security lacks integrated API scanning capabilities, leaving security teams with the challenge of identifying deployed APIs, detecting changes, and finding shadow API endpoints deployed
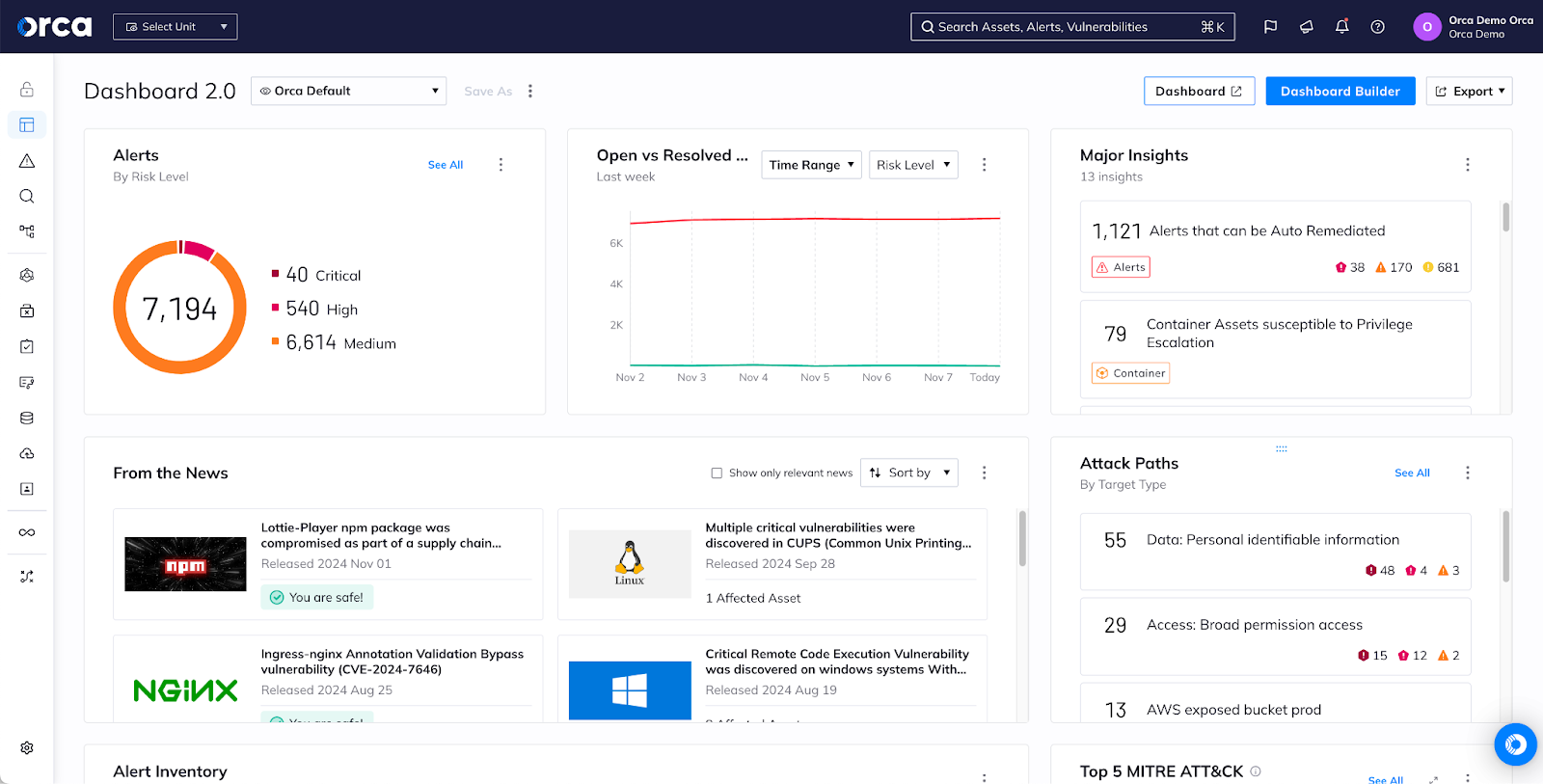
A purpose-built platform to simplify cloud security
To secure the cloud, security teams want to easily onboard cloud accounts, quickly activate security capabilities, and avoid operational overhead from traditional, agent-based solutions–ensuring comprehensive coverage across the entire cloud tech stack.
With Orca Security, you benefit from a purpose-built Cloud Security Platform that addresses all of your cloud risks and features our patented SideScanning technology that covers your entire cloud estate, including AWS, Google Cloud, Azure, and Alibaba Cloud, without agents.
With Tenable, Tenable Cloud Security often requires more work to deploy and configure; additionally, to unlock the platform, Tenable wants you to use (and pay for) their entire platform in Tenable One.
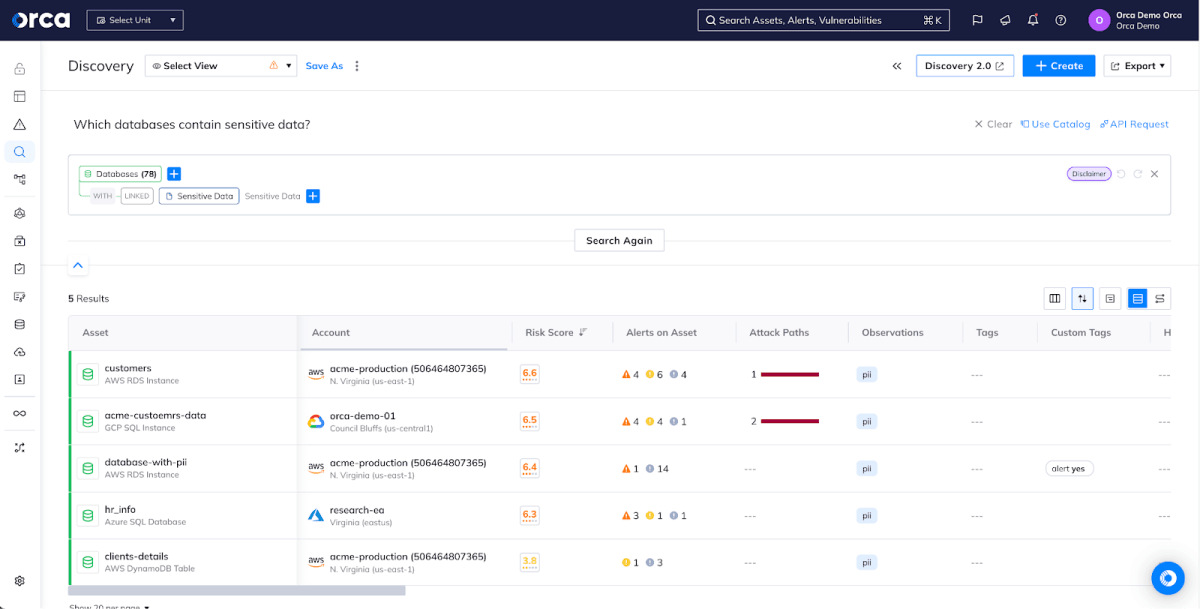
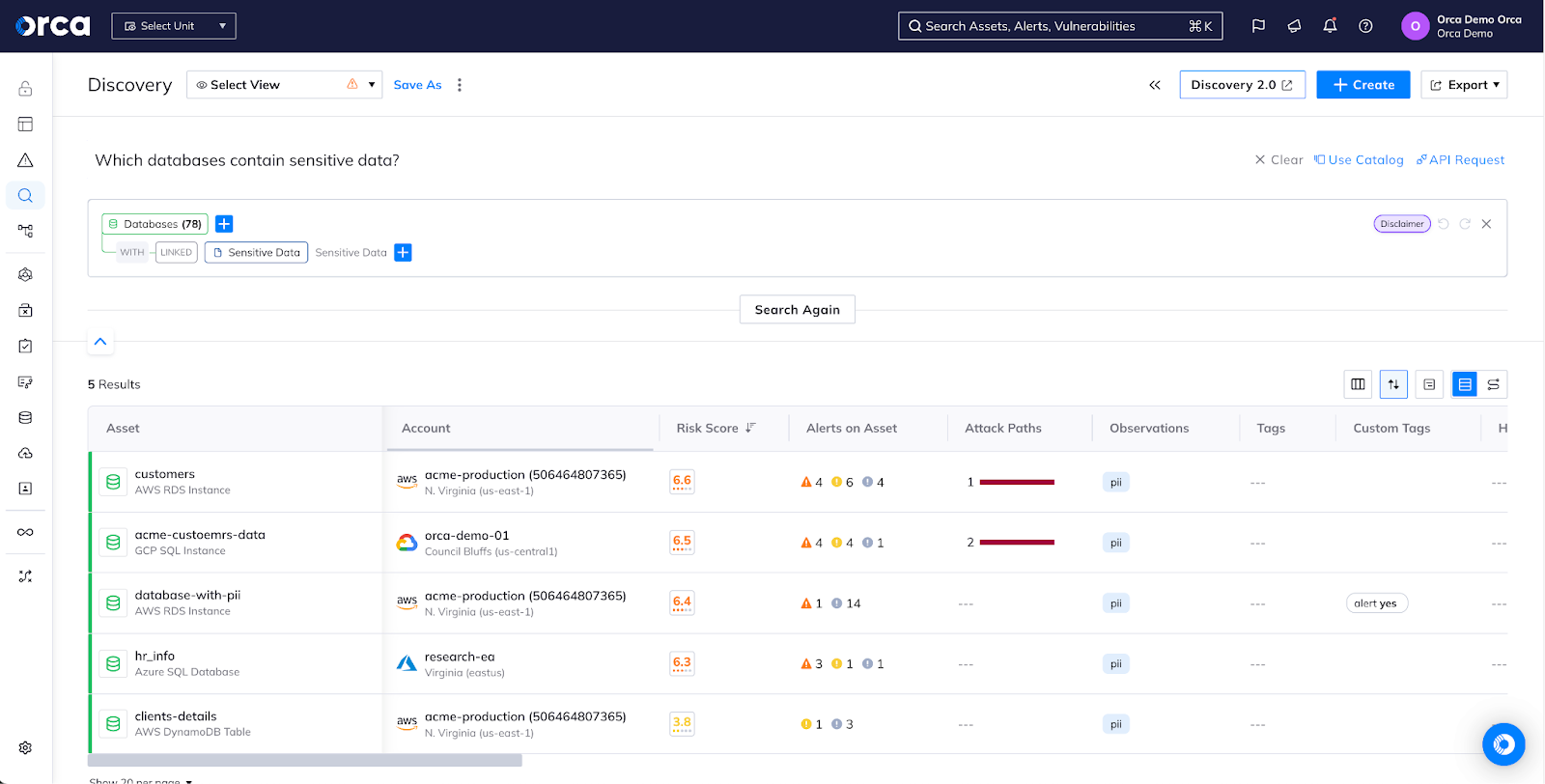
The full picture
Tenable Cloud Security only shows you a portion of everything you’ve deployed in the public cloud, missing key components such as API endpoints and detailed attack paths, leaving you with only a partial picture of what’s deployed, vulnerable, and misconfigured. Additionally, Tenable lacks flexible tools for querying the inventory it does have, making it much more difficult to investigate problems and answer questions.
Orca Security builds a detailed inventory of your cloud and uses this rich context to effectively prioritize problems. Orca’s Discovery allows you to find what you’re looking for no matter how complex the question and Discovery AI makes use of cutting-edge technology to answer natural language questions quickly without training an AI on your data.
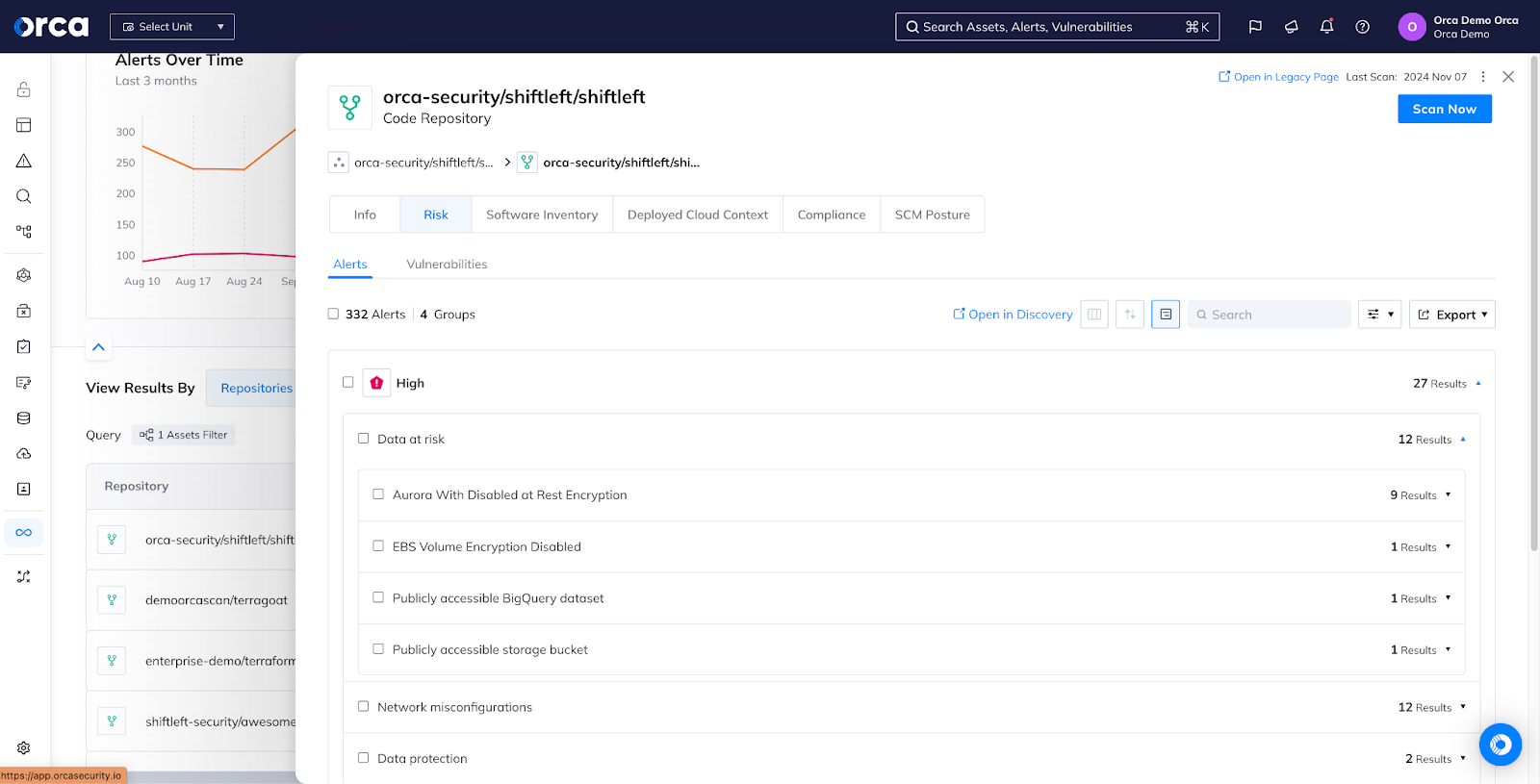
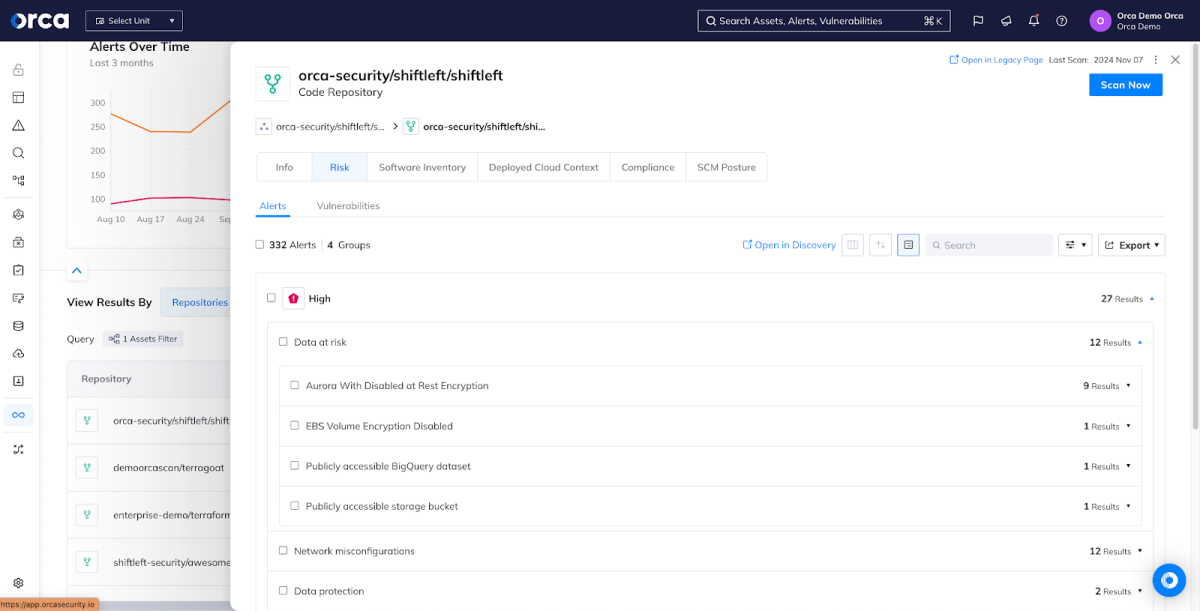
Move security policy earlier in the lifecycle
The Orca Platform includes advanced shift-left capabilities that detect vulnerabilities, misconfigurations, and secrets in source code, container images, and Infrastructure as Code (IaC), enabling security teams to apply policy early and avoid deploying costly mistakes to the cloud. Orca also monitors the posture of source code management platforms to ensure that the platforms used to store and build applications are as secure as the platforms they run on.
Tenable Cloud Security includes only limited IaC scanning.
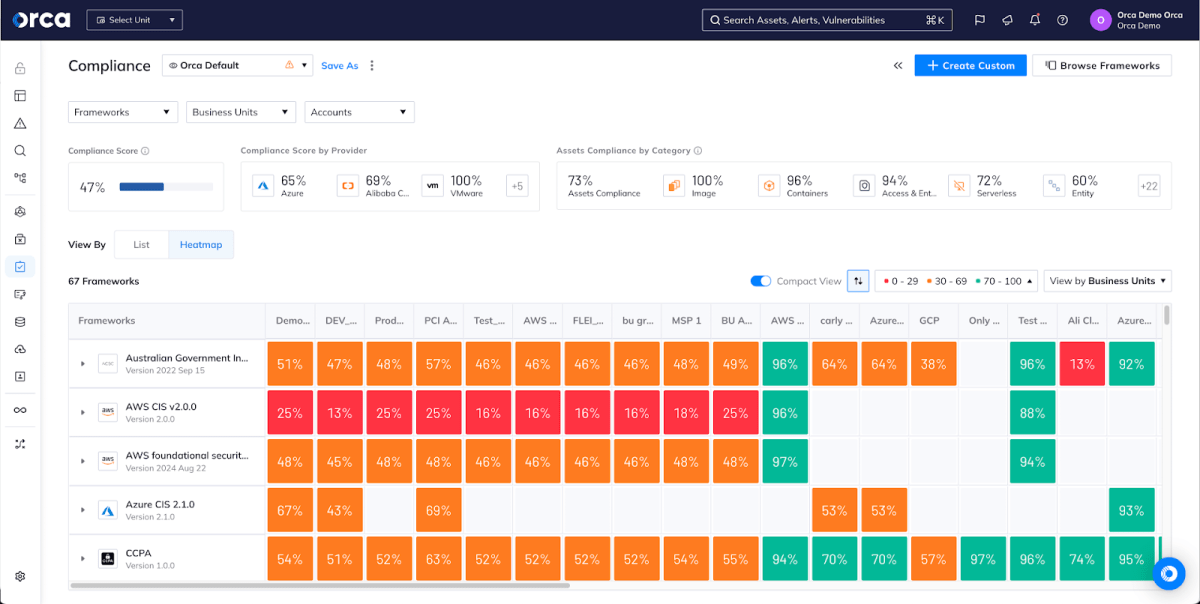
Comprehensive compliance for your entire cloud
Orca supports over 125 compliance frameworks, as well as our own Orca Best Practices and custom frameworks. This ensures that you can view compliance in a single dashboard and report covering your cloud infrastructure, data, identities, workloads, and more.