The Challenge
Cloud Data Security Tools Fall Short
With data scattered across multiple clouds and data stores, security teams need continuous visibility into where their sensitive data resides, who has access, and which data is at risk. Existing data security tools, however, are lacking in essential areas, such as automated data discovery, integrating data intelligence with other cloud risks, or delivering DSPM telemetry without requiring additional tools and integrations.
Legacy DLP tools rely on overburdened IT teams for manual data classification and struggle to keep pace in the cloud.
DSPM-only tools lack the wider context of cloud misconfigurations, vulnerabilities, exposed APIs, lateral movement risks and other threats.
Platforms that require integration with third-party data security tools lead to higher costs, contradicting alerts, and inefficiency.
Our Approach
Detect and Prioritize Cloud Data Security Risks with Context
The Orca Cloud Security Platform performs continuous discovery of data stores across your cloud estate, and alerts to security and compliance risks, without requiring any additional tools. Instead of focusing solely on data security, Orca delivers a comprehensive, context-driven picture of sensitive data exposure, enabling organizations to prioritize risks effectively, reduce alert fatigue, and stay focused on what matters most–from a single platform.
Gain full awareness of data storage assets, sensitive data, and attack paths in your multi-cloud estate, including shadow data.
Fast and frictionless deployment–get an accurate data inventory in minutes without the need for agents, additional tools or integrations.
Be alerted to critical data-related risks, including missing encryption, overly permissive identities, and susceptibility to lateral movement, along with remediation recommendations.
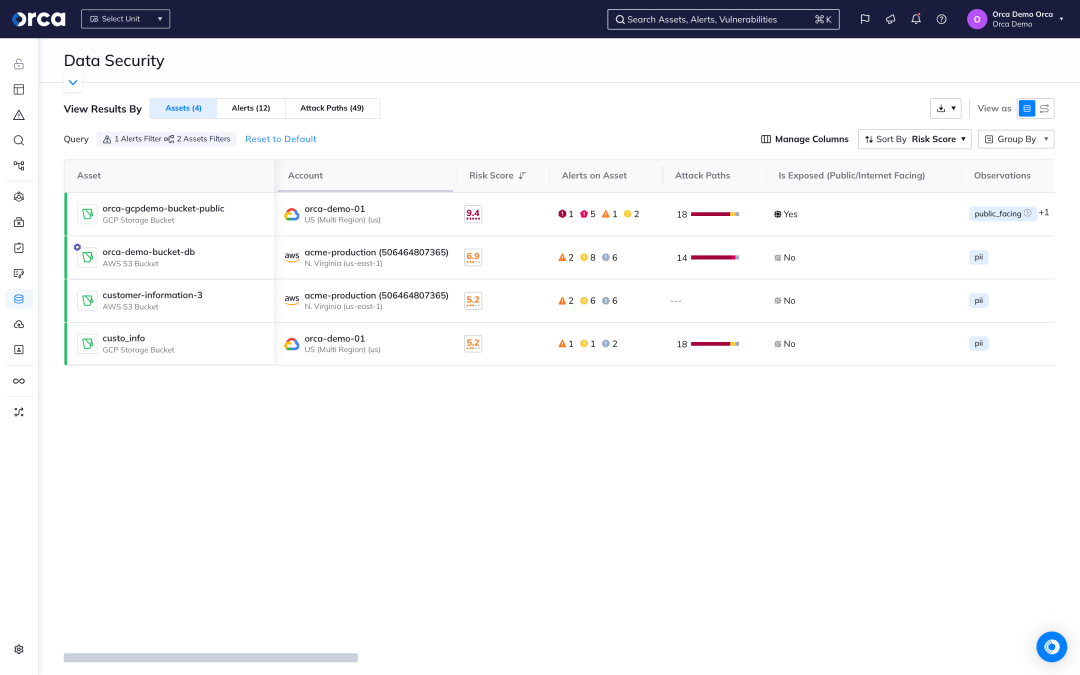
Discover and classify data in your cloud
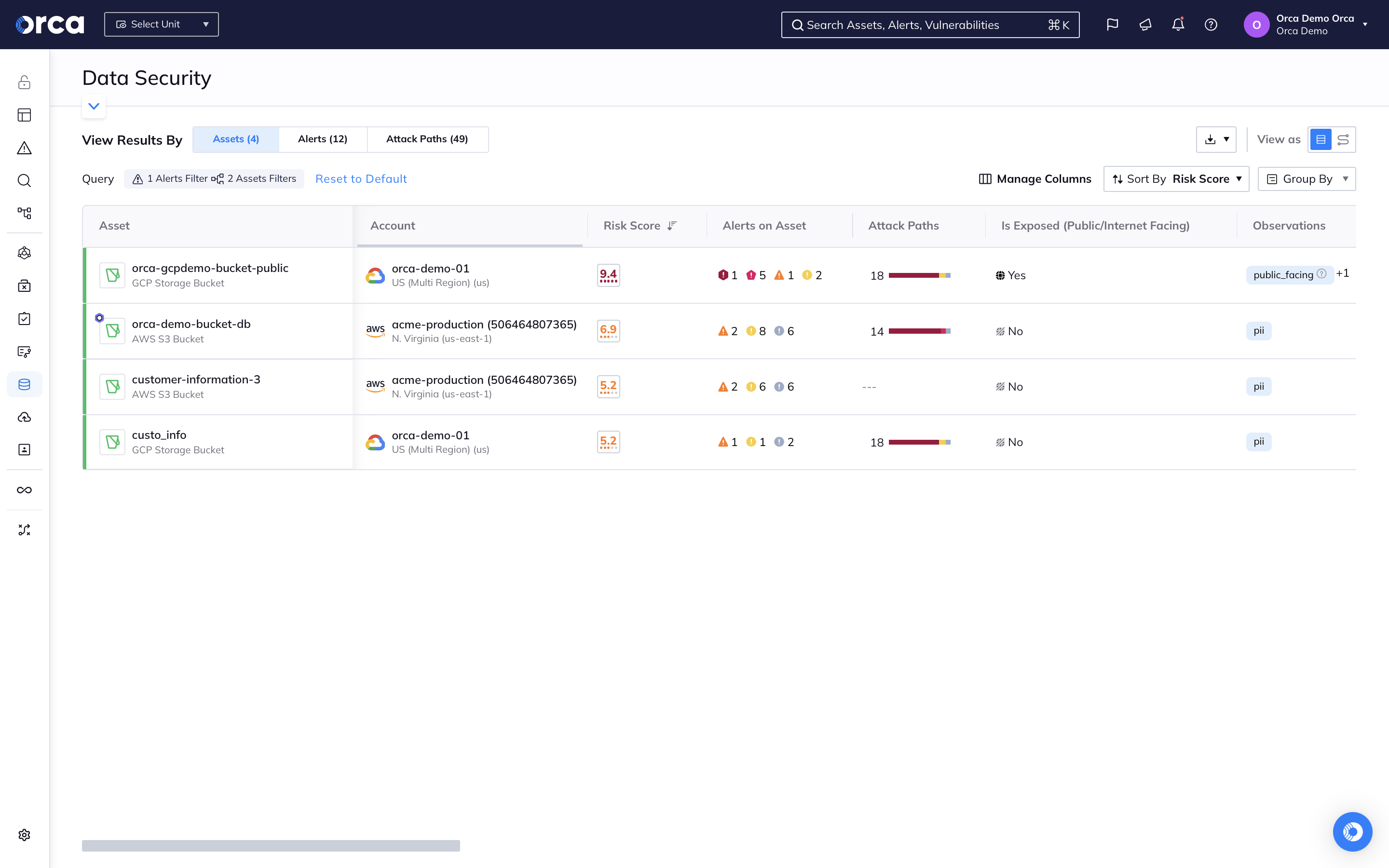
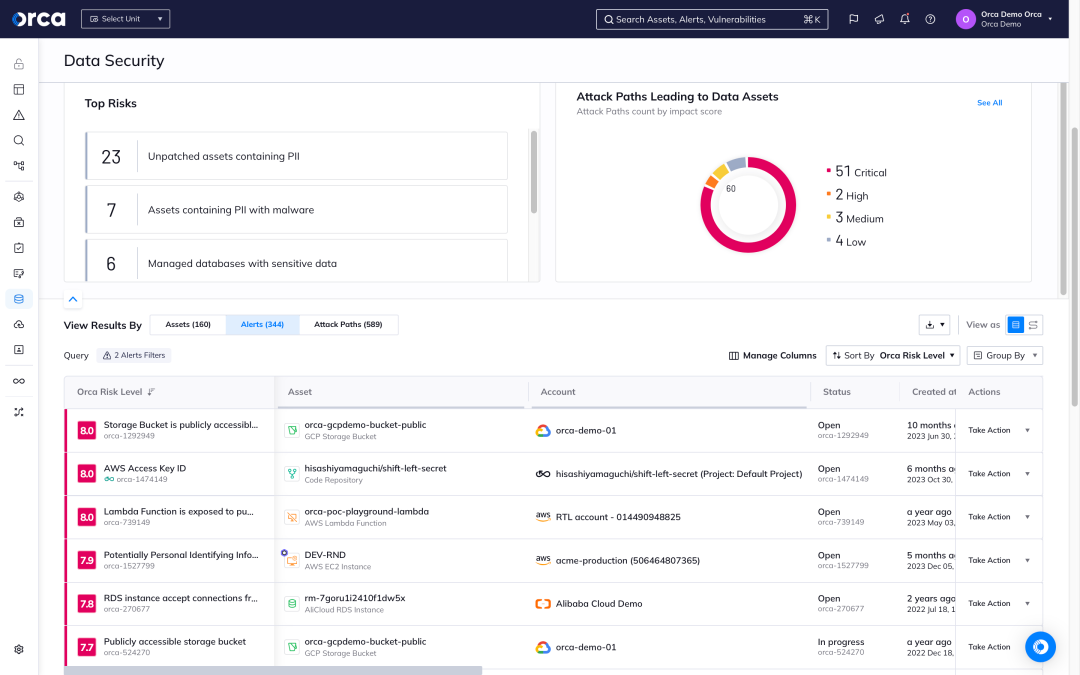
Orca’s DSPM dashboard provides data security teams with an overview of their cloud data stores, sensitive data, and security and compliance alerts. Orca scans managed, unmanaged, and shadow data, giving security teams wide and deep visibility into where their data resides.
- Get a multi-cloud inventory of data storage assets—including databases, and files in virtual machines, storage buckets, and containers.
- Know which data stores contain sensitive data and of what type—including PII, PCI, PHI, or financial information—for both security and regulatory purposes.
- Leverage interactive graphs that show the location and relationship between data stores and other cloud entities.
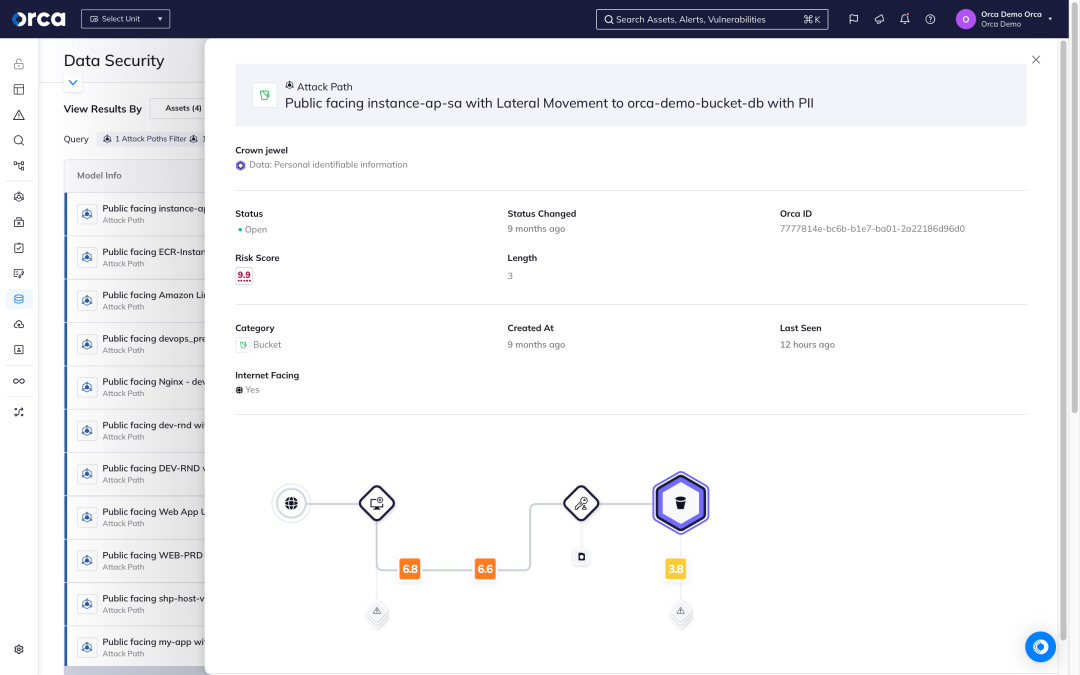
Shrink the data attack surface
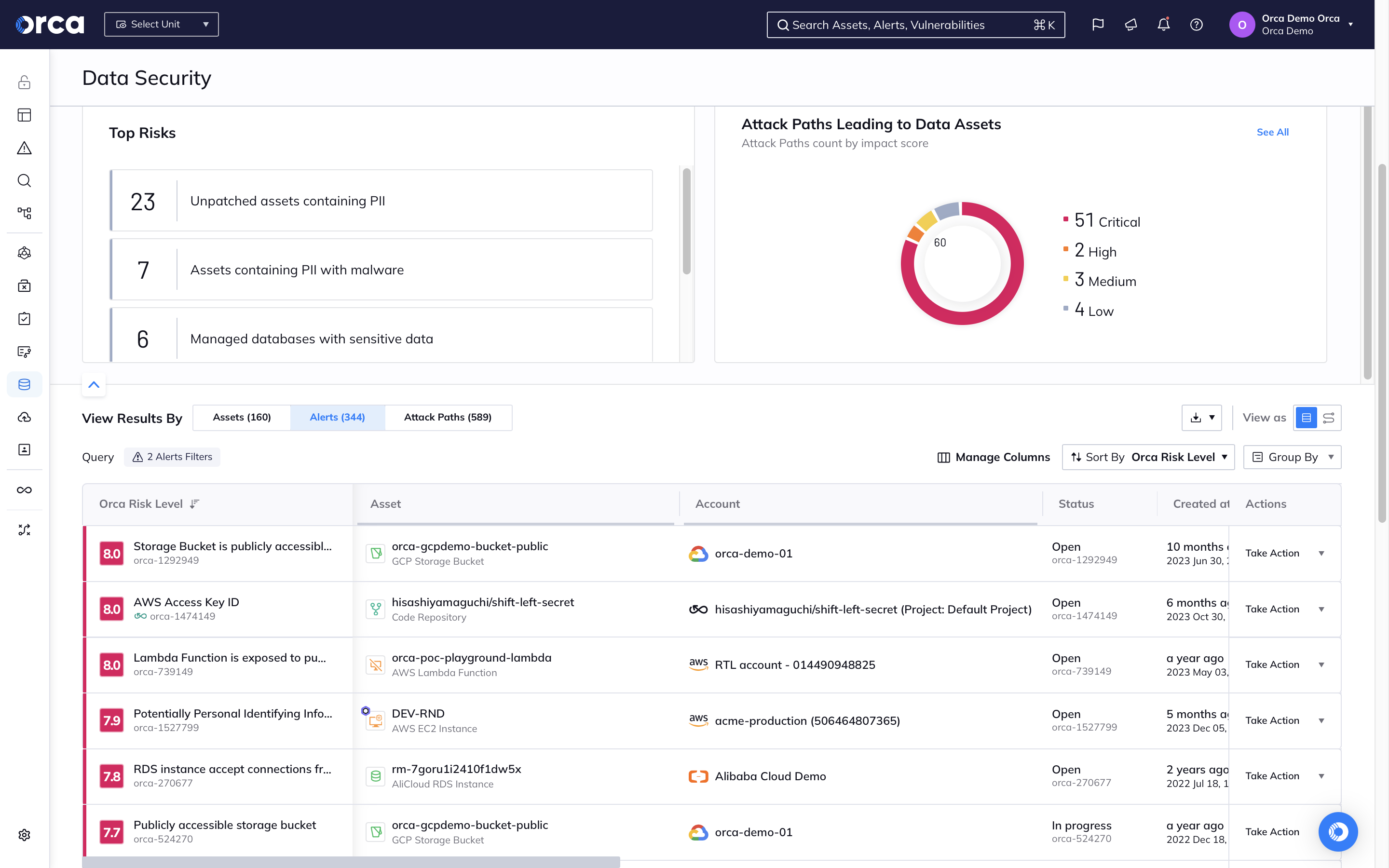
Orca scans the entirety of your cloud estate, surfacing direct and indirect data risks, allowing security teams to take preventive steps to reduce their data attack surface.
- Detect and prioritize risks that endanger sensitive data on managed and self-hosted databases, and every workload across your cloud estate.
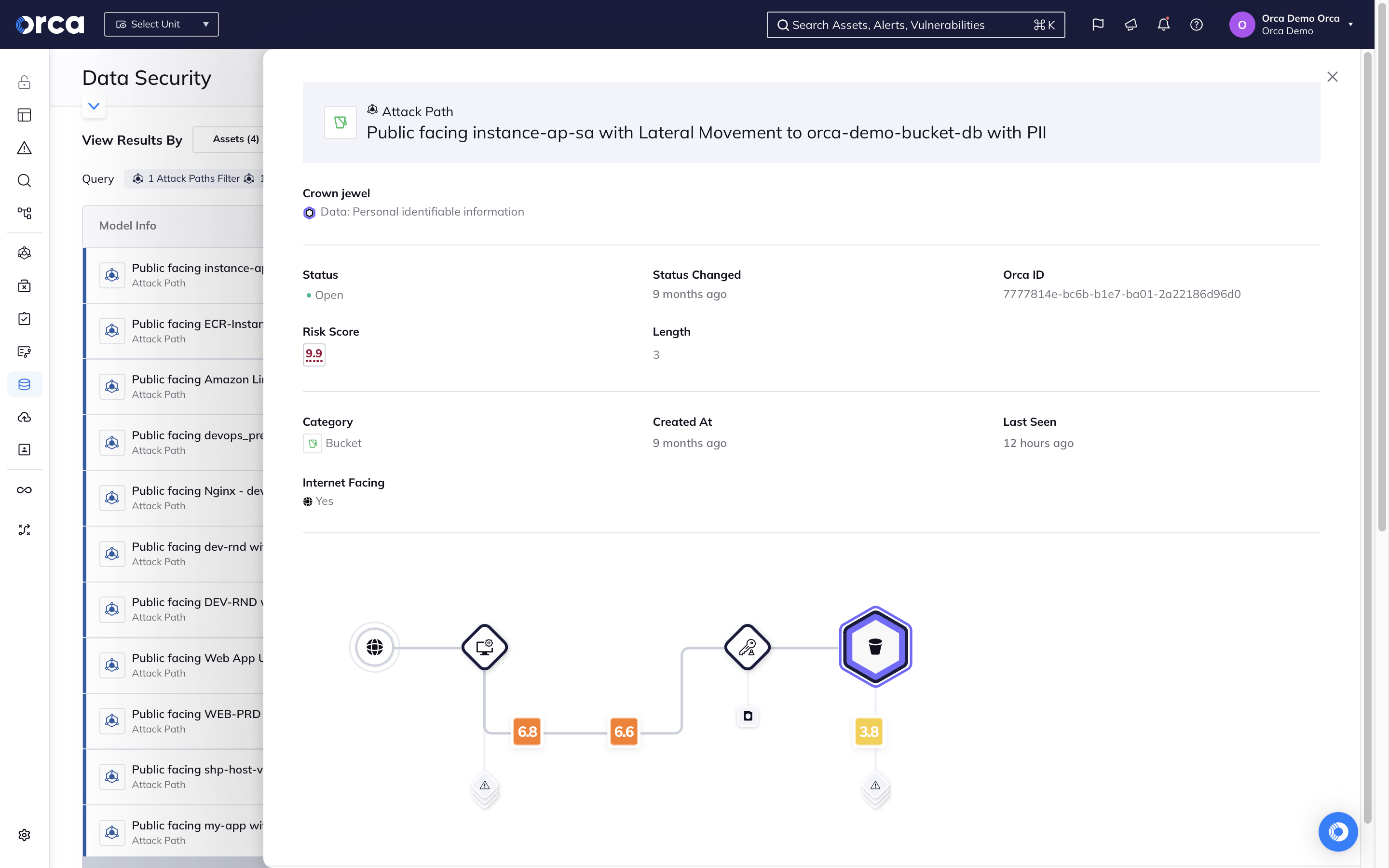
- Understand how dangerous attack paths can be formed through the combination of data misconfigurations with other cloud risks including vulnerabilities, malware, lateral movement risks, and API risks.
- Leverage actionable risk telemetry, indicating the location of sensitive data and masked data samples for efficient triaging and remediation.
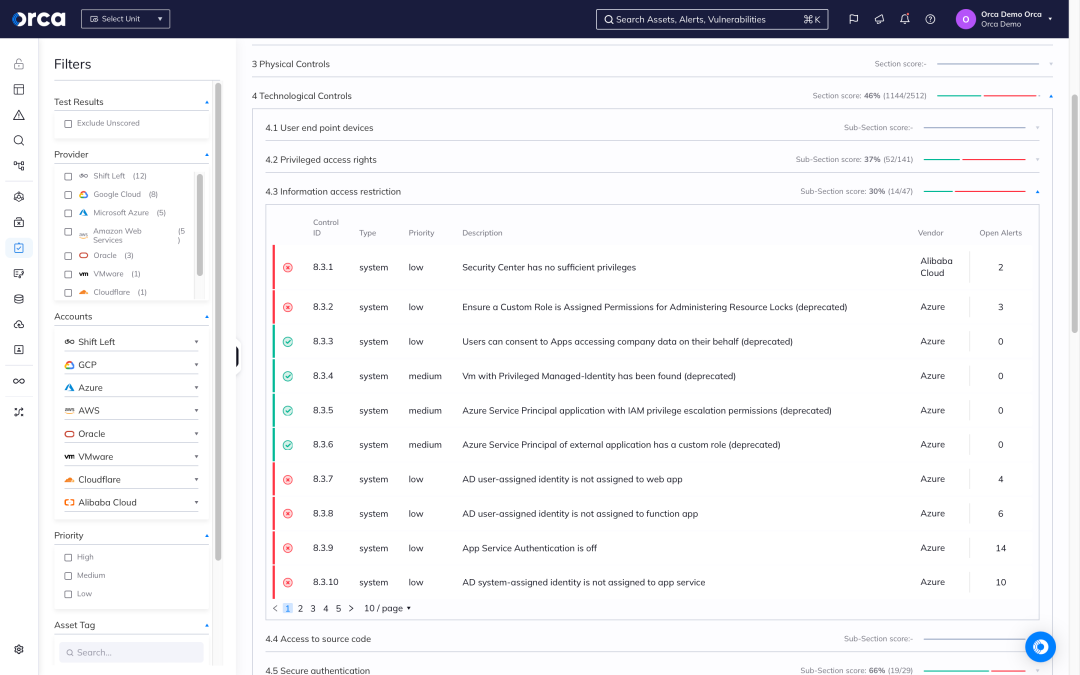
Ensure continuous data compliance
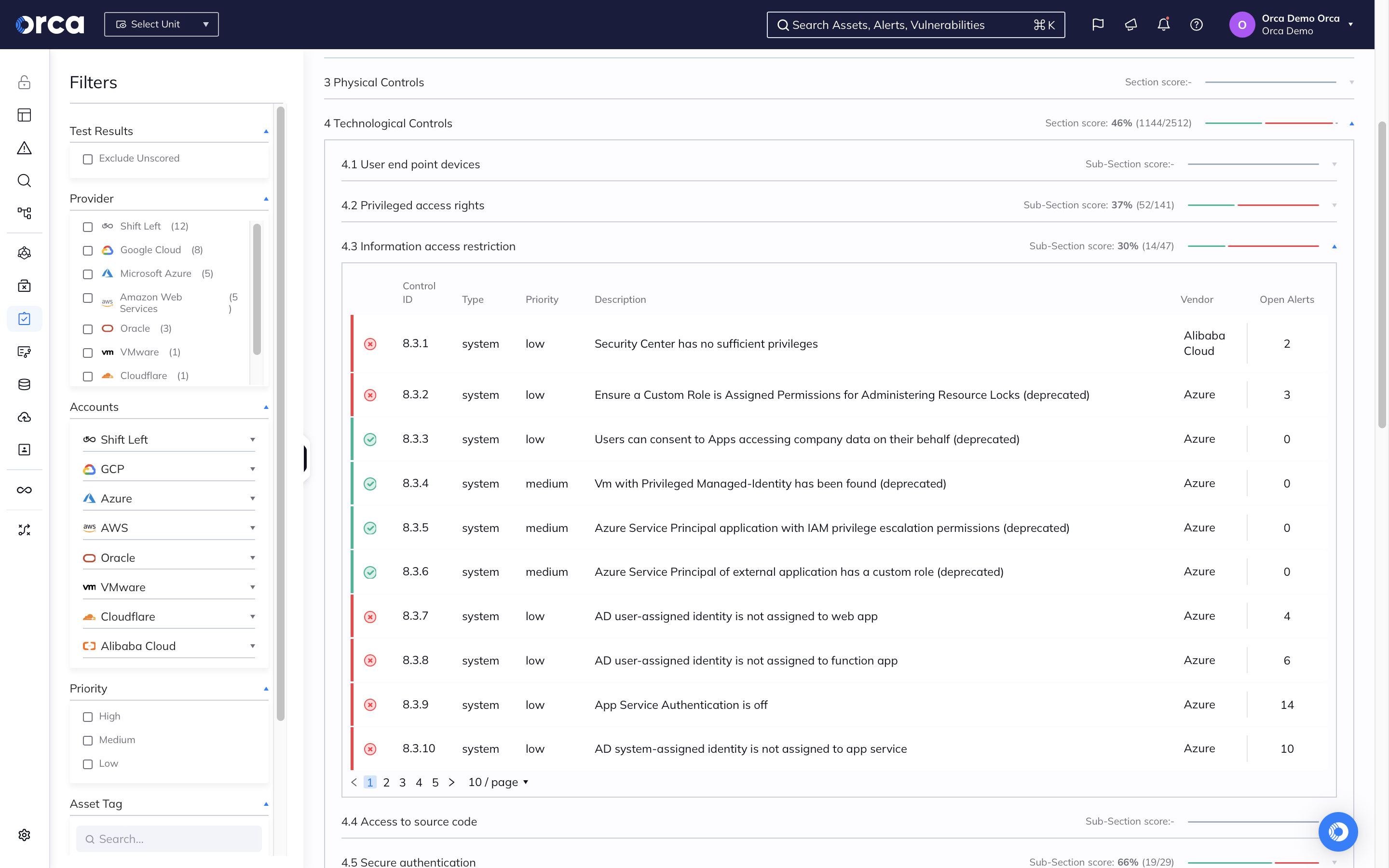
Orca provides a single, unified cloud security platform for verifying that sensitive data stores comply with regulatory frameworks and industry benchmarks, including data privacy requirements.
- Be alerted when the storage of sensitive data violates compliance regulations.
- Leverage 150+ out-of-the-box templates—or build custom frameworks—to quickly understand and measure compliance across clouds.
- Stay ahead of audits and adhere to common compliance frameworks such as PCI-DSS, GDPR, HIPAA, and CCPA.
Monitor data activity
Orca continually monitors for suspicious activity that could endanger your organization’s sensitive data, so you can quickly investigate and triage any potential breaches.
- Be alerted to active anomalous access patterns and other suspicious events and behaviors that could indicate potential data exfiltration attempts.
- For every alert, a detailed timeline of events is provided, as well as recommended remediation steps, enabling you to rapidly lower security risks.
- Keep a real-time inventory of all cloud data, including its location and security posture. Across the entire Software Development Lifecycle.
Orca Helps Keep Your Data Safe
Frequently Asked Questions
Data Security Posture Management (DSPM) is a cloud security solution that detects sensitive data, such as PII (Personal Identifiable Information), PHI (Personal Health Information), financial data, intellectual property, and more, and analyzes and remediates any associated security risks or compliance issues.
In 2022, Gartner first introduced the category name “Data Security Posture Management (DSPM)” in an effort to classify a new breed of data security solutions. Unlike legacy data security technologies, DSPM takes a cloud-native approach to securing data in the cloud.
Securing sensitive data is one of the main focal points of cloud security. While enterprises are increasingly moving their data to the cloud, security teams are given the unenvious task of keeping this data secure.
A 2022 Forrester report on The State Of Data Security found that 46% of security decision-makers whose organizations experienced a breach in the previous year said that PII was targeted. Additionally, during a time of global pandemic, 36% said that protected health information (PHI) was a common type of data that was compromised.
DSPM solutions perform several important functions to ensure data security and integrity, including:
- Scanning and inventorying data across the cloud estate.
- Identifying where sensitive data lives and who has access to it.
- Discovering and eliminating shadow data to minimize the data attack surface.
- Preventing sensitive data exposure by addressing over-privileged access, data store misconfigurations, and other risks in the environment.
- Maintaining continuous multi-cloud compliance with sensitive data storage requirements.
Despite its benefits, DSPM also presents important technological challenges, including:
- Lack of unified context: DSPM, when offered as a standalone solution, lacks wide risk visibility into the cloud estate. This leads to an incomplete awareness of the factors that may put sensitive data at risk, such as API misconfigurations, workload vulnerabilities, or other cloud misconfigurations.
- Tool sprawl: Standalone DSPM solutions require organizations to purchase additional cloud security solutions for complete coverage. This forces security teams to use and manage a siloed solution, decreasing productivity through inefficiencies and duplicative work, while increasing licensing costs.
- Legacy solutions: Organizations may rely on data loss prevention (DLP) tools for their DSPM needs. As a legacy solution originally designed for on-prem environments, DLP provides a limited inventory of sensitive data and where it lives in the cloud, requiring security teams to manually classify data to prevent data leakage.
In contrast, as a CNAPP, Orca combines DSPM, CSPM, CWPP, CIEM and more in a single platform, and provides full-stack visibility of your cloud estate—that is, visibility that spans the cloud infrastructure, OS, application, and data layers—ensuring you have complete security and compliance coverage.
Orca Cloud Security Platform provides the key capabilities of a DSPM solution, and our comprehensive approach to cloud security means that data security is natively included in a single cloud security platform, without requiring any further integrations.
In addition, as opposed to DSPM tools that focus solely on data security, Orca takes a holistic view that combines data intelligence with other cloud risks. This includes vulnerabilities, malware, misconfigurations, lateral movement risks, identity and access risks, API risks, and more. This comprehensive insight allows Orca to highlight how indirect as well as direct risks can lead to exposed sensitive data.
Orca’s SideScanning™ technology, which collects data from the workload runtime block storage without requiring agents, performs a complete data risk analysis with no performance impact. This provides security teams with comprehensive visibility of their data storage across the entire cloud estate, including misplaced sensitive data stores and shadow data.