Securing sensitive data is one of the main focal points of cloud security. Recognizing the importance of protecting data in the cloud, Orca’s patented SideScanningTM technology has always included capabilities to detect and alert security teams to sensitive data at risk, including personally identifiable information (PII) and financial data. In addition, Orca’s attack path analysis enables teams to understand how attackers can combine different weaknesses in the cloud environment to reach an organization’s most valuable assets: sensitive data and crown jewels.
Today, we are excited to announce that we have now significantly expanded our cloud data security coverage and capabilities, launching a comprehensive offering of Data Security Posture Management (DSPM) as part of the Orca Cloud Security Platform.
Orca’s DSPM capabilities allow organizations to identify, prioritize, and address data-related misconfigurations and security risks in managed and unmanaged cloud data stores, as well as in files on virtual machines, containers, and storage buckets across their multi-cloud environments. These enhancements enable organizations to take preventive steps to further reduce the data attack surface and triage anomalous data-related events across their cloud estates including AWS, Azure, Google Cloud, and Alibaba Cloud, from a single comprehensive cloud platform, without requiring any additional tools.
Fully agentless, Orca leverages its patented SideScanning™ technology and deep insights into cloud workloads and configurations to provide security teams with a comprehensive understanding of their data storage estate and related risks.
Why DSPM is so important
While enterprises are increasingly moving their data to the cloud, security teams are given the unenvious task of keeping this data secure. A 2022 report from Enterprise Strategy Group states that “The amount of sensitive classified data in public clouds is expected to nearly double over the next 24 months, yet more than half of organizations believe notable portions of their sensitive data stored in public cloud services is insufficiently secured.”
Unfortunately, sensitive data is a top target for cyberattackers, whether for resale purposes, ransomware attacks, or other nefarious motives. In a 2022 Forrester report on The State Of Data Security, 46% of security decision-makers whose organizations experienced a breach in the previous year said that PII was targeted. Additionally, during a time of global pandemic, 36% said that protected health information (PHI) was a common type of data that was compromised.
Securing sensitive data in the cloud is hindered by several challenges: Data is scattered across multiple cloud service providers and data stores, and developers can replicate and create data stores whenever they want, resulting in shadow data–with perhaps different configurations and permissions than originally intended. These challenges result in weak and incomplete visibility into where sensitive data resides, who has access, and which data is at risk.
In order to protect their organization’s data, security teams need to have the ability to:
- Have full insight into where their data is stored in the cloud
- Know where sensitive data resides and who has access to it
- Shrink the data attack surface by discovering and eliminating shadow data
- Prevent sensitive data exposure by addressing data store misconfigurations, overprivileged access, and other direct and indirect risks in the environment
- Maintain continuous compliance with sensitive data storage requirements
Current cloud data security tools are lacking
There is no shortage of software vendors in the data security space, from legacy tools that focus on data loss prevention (DLP) to tools focused on on-premises data centers, and a plethora of new startup companies that are purely focused on DSPM. While each offering has some benefits, these tools are lacking in essential areas, such as limited data discovery, a lack of integration between data intelligence and other cloud risks, and requiring additional tools and integrations for DSPM telemetry.
Data Loss Prevention (DLP) tools
Typically network or endpoint-based, DLP solutions have primarily focused on applying protection measures against data leaks through controlled egress points. But they typically lack the ability to create an inventory of sensitive data and where it resides, and rely on the IT teams to do manual data classification to prevent data leakage. With many of these solutions architected before the cloud existed, the proliferation of data in the cloud and data sprawl result in a DLP failing to keep pace. Furthermore, once data leaves the point of control, a cloud DLP solution no longer has visibility or control over that data.
Point DSPM tools
Although they have their merit, DSPM tools focus too much on the micro level, lacking the wider breadth of risk context that can impact sensitive data in the cloud. They can scan a database and identify PII, but can they see how a misconfigured API might expose that information? Do they know about a workload vulnerability that might create an attack path to sensitive data? Can they identify other cloud infrastructure misconfigurations that would add to the attack surface? The answer is no.
In addition, focusing solely on DSPM requires cloud security and compliance teams to purchase and manage yet another solution in their already large security stack and process even more security alerts to find out which issues should be prioritized. Analyst firms are observing that enterprises are increasingly looking for ways to reduce spend and avoid siloed tools in favor of more comprehensive cloud security and compliance solutions. Data security is a case in point.
Platforms that require third-party DSPM tool integrations
There are cloud security companies that offer partial or incomplete DSPM capabilities on their own, and rely on additional integrations with third-party DSPM or data management vendors. For organizations, this can lead to duplicate or contradicting alerts, as well as false positives. In addition, these bundled offerings often result in increased costs, complexities regarding DSPM maintenance, a lack of clarity about which vendor to turn to when something is not working properly, and a weaker customer experience.
How Orca’s DSPM is different
While the Orca Platform provides the key capabilities of a DSPM solution, our holistic approach to cloud security means that data security is natively included in a single comprehensive cloud security platform, without requiring further integrations.
In addition, as opposed to DSPM tools that focus solely on data security, Orca takes a much wider view and combines data intelligence with other cloud risks–including vulnerabilities, malware, misconfigurations, lateral movement risks, identity and access risks, and API risks–allowing Orca to highlight how indirect as well as direct risks can lead to exposed sensitive data.
Orca’s SideScanning™ technology, which collects data from the workload runtime block storage without requiring agents, performs a full risk analysis with zero performance impact. This provides security teams with comprehensive visibility of their data storage estate, including any shadow and misplaced sensitive data stores that security teams may not have been aware of.
Orca Security DSPM: maximize data security governance
Orca Security provides organizations with a comprehensive cloud security platform that offers the following core DSPM capabilities:
Inventory of data storage assets
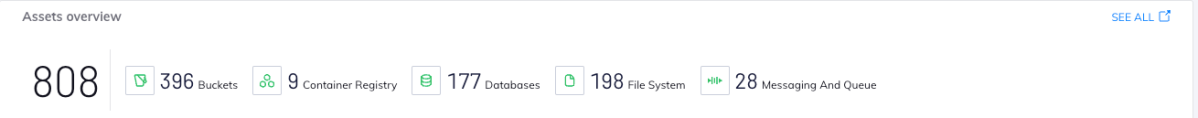
Orca provides an inventory of managed data, unmanaged data, and shadow data, giving security teams visibility as to where data resides. This includes discovering data in both managed and self-hosted databases, as well as data stored in files on virtual machines, storage buckets, and containers.
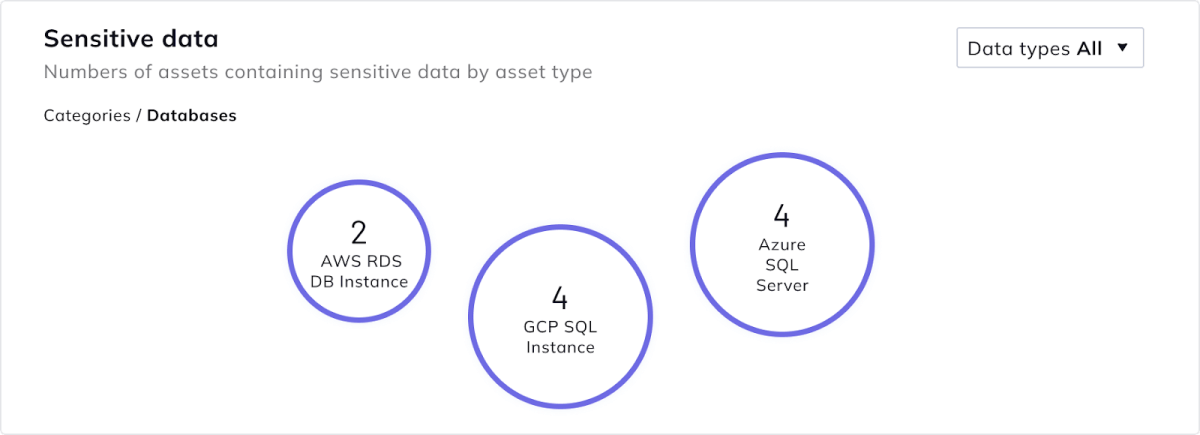
Sensitive data classification
Orca analyzes the content of these databases and files in order to determine if sensitive data, such as personally identifiable information (PII), is included in the data store. Orca then classifies the type of sensitive data into various categories, including:
- PII (personally identifiable information), including social security numbers, email addresses, phone numbers, etc
- PCI (payment card information), including credit card numbers, CVVs, etc.
- PHI (private health information), including insurance provider information, drug names, etc.
- Dev: Sensitive data such as secrets, tokens, usernames, and passwords
- Custom: Data that is uniquely sensitive to a particular company (coming soon)
Data risk and compliance analysis
Orca identifies, prioritizes, and suggests mitigation actions for data security and compliance risks, including unencrypted sensitive data, direct and indirect external exposure, and overly permissive identities, allowing teams to take preventive steps to reduce their data attack surface.
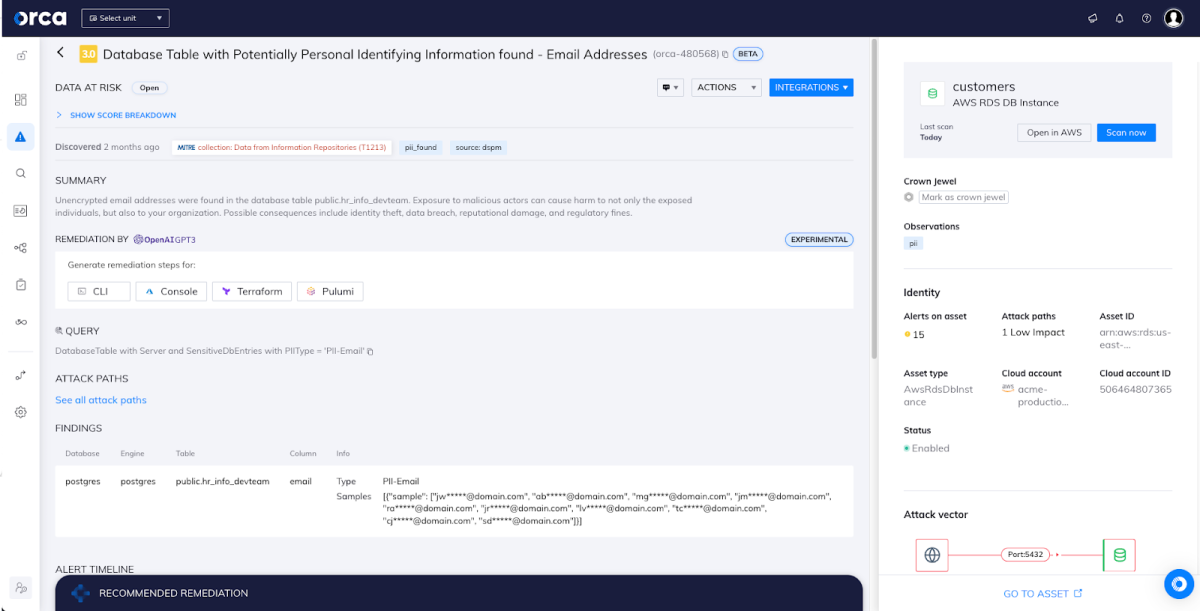
Beyond preventive risk management, Orca’s DSPM is fully integrated with our Cloud Detection and Response (CDR) capabilities, alerting organizations to active anomalous access patterns and other suspicious events and behaviors that could indicate potential data exfiltration attempts. This helps SOC and incident response teams with more efficient triaging and faster time to remediation.
In addition, Orca alerts compliance teams to non-compliant configurations of sensitive data stores in their environment, enabling them to take remediation actions. Orca includes support for 80+ compliance frameworks, including PCI-DSS, GDPR, HIPAA, and a wide range of CIS benchmarks.
A closer look at Orca’s DSPM features
So what does Orca’s Data Security Posture Management look like? Below we have highlighted a few of the main features.
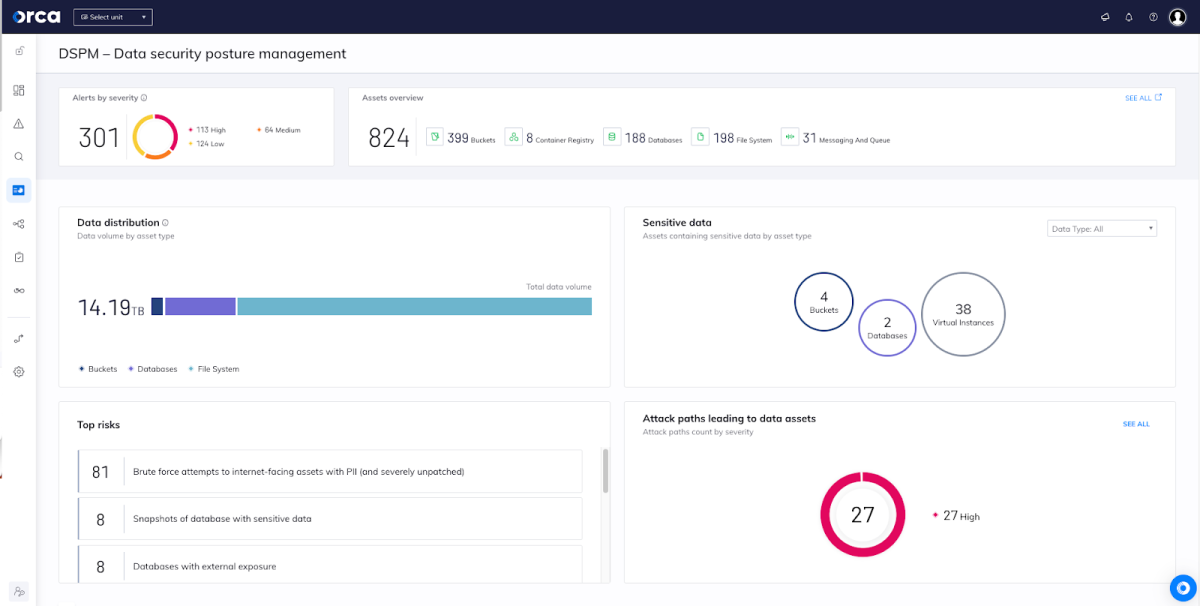
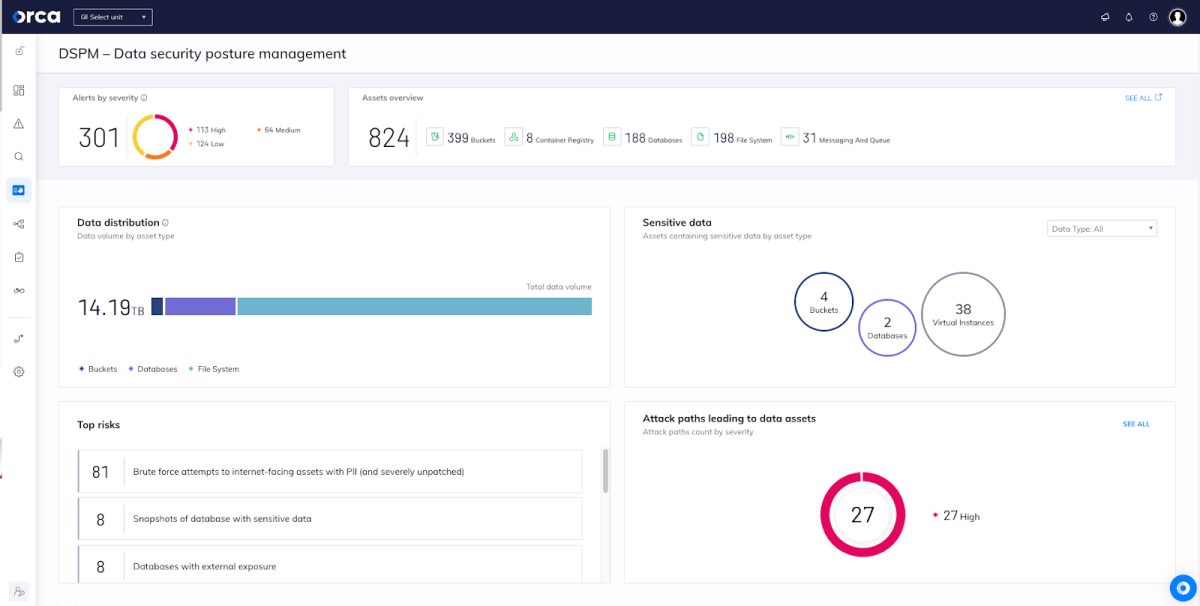
New DSPM Security View
A new ‘security view’ dashboard focused specifically on data security telemetry is your headquarters for all information related to data stores, sensitive data, and related risks. A user-friendly, easily consumable source, the dashboard provides an overview of:
- Sensitive data risk alerts: grouped by severity, helping teams prioritize risks quickly.
- Full inventory of data store assets: (databases, buckets, container registries, etc.), providing wide visibility of the cloud data estate.
- Data distribution: grouped according to asset type, giving further data awareness.
- Data store assets with sensitive data: grouped according to asset type, strengthening data security visibility.
- Attack paths: prioritized according to risk score
- Full list of assets and security alerts related to sensitive data at risk
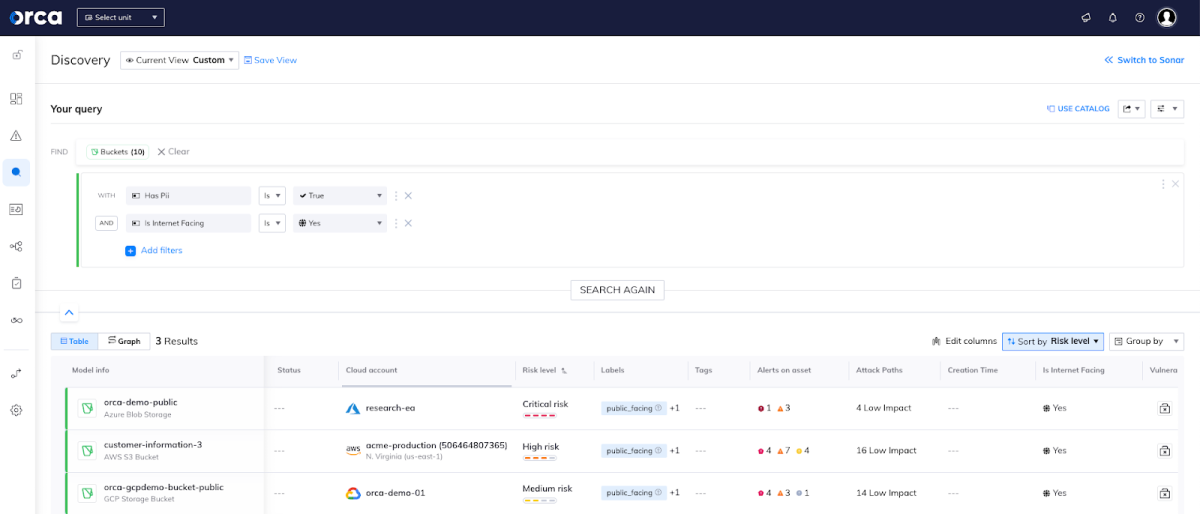
Easily Query DSPM assets and risks
While information on all data stores and sensitive data risks are highlighted in the DSPM security view, they are also accessible via both our advanced search query engine and the Orca Discovery Query Builder, allowing security engineers to get answers to granular, specific questions on their data estate.
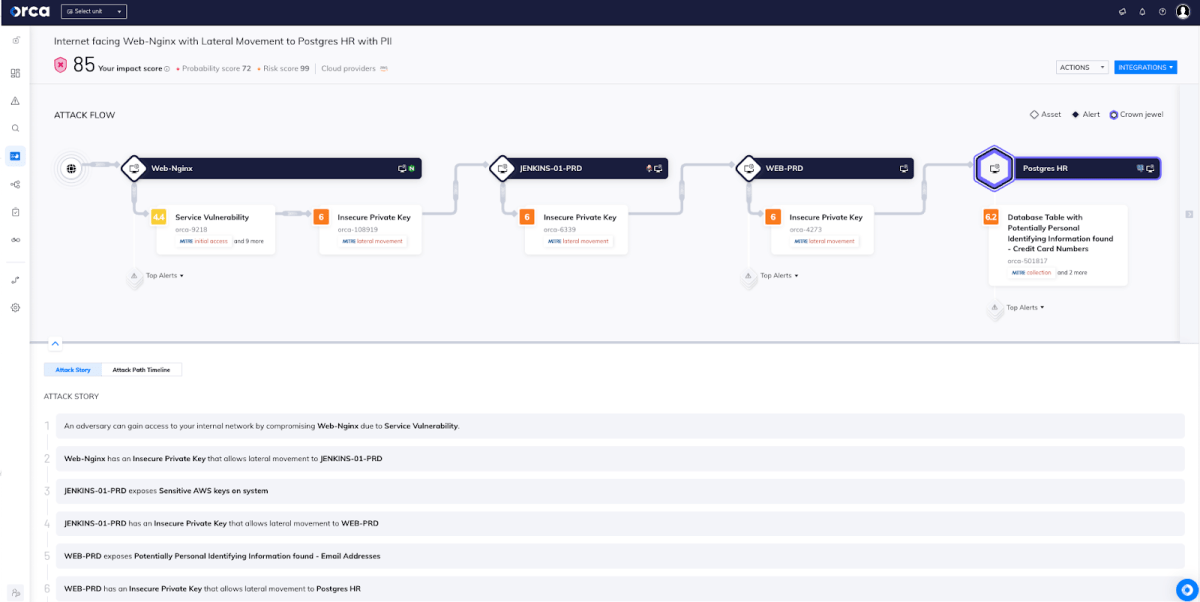
View data within Attack Path Analysis
Applying Attack Path Analysis, Orca warns when attackers could combine different weaknesses in the cloud environment to expose sensitive data. Each attack path is automatically scored based on a number of criteria, including exploitability, severity, and business impact. This allows security teams to focus on remediating the risks that pose the greatest danger to the organization’s sensitive data, reducing alert fatigue and preventing potentially damaging data breaches.
Integrations with Ticketing and SOAR
As with all capabilities of the Orca platform, security and compliance teams can leverage Orca’s out-of-the box integrations and API capabilities to fit data security management into their existing workflows, ensuring fast remediation and avoiding confusion about team responsibilities.
Orca integrates with SIEM and SOAR solutions for fast investigation and remediation (e.g. Splunk, Sumo Logic, IBM Qradar, Torq, and Brinqa) and offers several ticketing and notification integrations with providers such as Slack, PagerDuty, ServiceNow, and Jira.
Learn more about Orca’s DSPM capabilities
Update: Orca’s DSPM capabilities are now generally available (April 24, 2023). Interested in learning more? Register for our on-demand webinar, Understanding DSPM to Help Manage Your Cloud Data Risk. You can also read our eBook, The Top 5 Mistakes to Avoid When Managing Sensitive Data in the Cloud.
Ready to try it out in your own cloud environment? Sign up for a Free Risk Assessment or Request a Demo to see how quickly and easily the Orca Cloud Security Platform can help you identify and address potential cloud data risks.