Migrating on-premises resources to the cloud can provide many benefits for organizations including a faster path to innovation, simpler access to applications and resources, and cost reductions. Early cloud adopters didn’t lose much sleep over malware, as attackers continued to focus efforts towards on-premises data centers where most if not all of an organization’s sensitive data was stored. Although movement to the cloud was cautious at first, it has gained significant momentum in the last few years, especially since the COVID-19 pandemic has made working from home commonplace.
Cloud security challenges
This rapid movement of organizations to cloud platforms and technologies has compressed the timelines that many had initially envisioned for cloud adoption, including the need to address a number of pressing security issues.
Adversaries are also migrating to the cloud
As more sensitive workloads and data continue to migrate to the cloud, cyber criminals and malicious actors are refocusing and sharpening their efforts to attack them. So it’s no surprise that over the past year, we have seen a significant spread of malware in cloud environments. Bad actors have discovered that they too can leverage the power of the cloud by compromising cloud applications and assets with malware and Trojans. After establishing a foothold, they use command and control servers to manipulate cloud applications and other resources to move laterally towards the most lucrative assets.
Shared responsibility confusion
Although the shared responsibility model of cloud security has been with us almost since the beginning of public cloud computing, many organizations are still confused about where the cloud provider’s security responsibility ends, and where their responsibility begins. Securing cloud workloads against malware attacks is a persistent area of confusion and the questions are universal: Won’t our cloud provider protect us against malware? How much, if any, of our constrained IT budget and personnel should we expend on cloud malware detection? How can we get sufficient security coverage? How much effort are attackers devoting to spreading malware in the cloud?
Supply chain attacks—a stealthy way to spread cloud malware
Supply chains are most commonly considered to be a network of resources supporting a product from design to manufacturing to delivery. The software development process also utilizes the supply chain concept, and today’s complex software supply chains often take advantage of the easy scalability of cloud resources.
Software development supply chains, especially when leveraging cloud resources, present opportunities for attackers to infect the software as it moves through the development process. Attackers often leverage malware Trojans or even write their own custom malware to carry out multi-staged attacks. In addition, the continuous integration and deployment (CI/CD) workflows used by developers to speed new software and updates into production can also make software supply chains more vulnerable and difficult to monitor.
It’s no wonder that supply chain attacks are on the rise, having inflicted considerable damage on many public and private organizations. Recently, SolarWinds customers were compromised when widely distributed update packages were infected with malicious content. And now customers of Kesaya, another IT management software company, have been hit with ransomware demands enabled via a supply chain attack. It is believed the adversaries distributed the malware to Kesaya’s customers by exploiting multiple vulnerabilities in Kaseya’s Vector Signal Analysis software. Both of these supply chain attacks resulted in rapid infection of a wide range of victims who remained unaware of malicious content distributed by trusted entities until it was too late.
CWPP and CSPM solutions are incomplete
When a cloud workload protection platform (CWPP) security agent discovers malware on a cloud resource, the typical response is to stop the asset and/or delete the malicious file. But what about neighboring resources? Did unprotected keys or other permissions enable lateral movement? Did the malware discover unencrypted credentials that allowed direct access to sensitive data? Assessing risk is difficult when using security agents with no insight into connected assets. Also agent-based solutions have an inherently high total cost of ownership due to difficult deployment and continuous maintenance.
Similarly narrow in scope, traditional CSPM tools don’t scan assets for malware and only identify simple control plane misconfigurations, resulting in limited insight into overall workload risk posture.
Eliminating malware in the cloud
So cloud malware is an unfortunate reality. Threat actors have learned to leverage the power of the cloud to spread malware for their own benefit. What can you do right now to protect your organization? Let’s start with some best practices.
Best practices to help stop cloud malware:
- Update, update, update — ensure that all of your systems have the latest patches and updates installed, especially assets exposed to the public internet. In this never ending game between attackers and defenders, this may be the simplest way to help shift the odds to your favor.
- Fortify your defenses — enforce good security hygiene practices across your cloud environment:
- Use the “least privilege” approach when configuring IAM for cloud resources.
- Use multi-factor authentication for secure log-in.
- Encrypt your data, both at rest and in transit, wherever possible.
- Discover all publicly connected resources and regularly scrutinize their need to be public.
- Awareness — Although this seems obvious it is often overlooked. Many organizations have received unintended news coverage because of a salesperson who decided to click an unfamiliar link, a veteran software engineer who kept secrets in a clear text file on his desktop, or a technical support person who left a storage bucket publicly exposed. Train your employees to be aware of risk to ensure they are part of your defenses.
Best practices form the foundation for good security hygiene, but often aren’t enough when attempting to secure complex and dynamic multi-cloud estates with public-facing assets. To maintain a strong security posture and keep up with compliance demands in these environments, you may need a partner. This is where Orca Security can help.
Orca Security discovers cloud malware
Orca Security provides full cloud visibility for our customers. Using SideScanningTM technology, we deliver a clear view of all files residing on cloud resources — including malware — from simple instances to complex container deployments inside of orchestration clusters and frameworks. Complete cloud visibility allows us to apply advanced mechanisms to scan all resources and alert when malicious files are discovered.
The Orca scanner detects both known and unknown threats by performing a deep scan across the entire file system using a sophisticated third-party malware detection engine that performs both heuristic and signature-based detection. Orca’s heuristic detection enables discovery of polymorphic malware, something that security solutions that only compare malware hashes can’t do.
Often, we discover malware that may have been resident for months or years without the customer’s knowledge. Our technology also detects malicious files on stopped machines, allowing remediation before they are returned to a running state. Orca also scans cloud storage such as Amazon S3, and container image repositories for malware.
Antimalware scanning is performed entirely on the Orca side, so it won’t affect your production workloads. Since the Orca scanner runs on an Orca host, it can’t be tampered with by any malware that might be running on the machine being scanned. This enables Orca to detect advanced threats, such as rootkits, that might otherwise evade agent-based scanners.
Extensive malware intelligence
Orca scans huge volumes of malware files on a daily basis, allowing us to build a comprehensive database including the state, type, and even origin of malicious files found on customer cloud resources. We encounter many versions of malware during our scans and frequently compile useful insights for our customers. Here are some examples:
- Most common malware file types found (not including Eicar test files):
- .ppt (Microsoft Powerpoint files)
- .bin (binary file)
- .msi (Microsoft Windows package file containing installation information)
- .exe (Windows executable file)
- Most common malware types found:
- Generic Win32 Trojans
- Generic PowerShell Trojans
- Generic Scripts Trojans
- Downloader Trojans
- Top resources where malware was discovered:
- Ubuntu 65%
- Windows Server 20%
- Debian 6%
- Alpine 3%
- State of resource where malware was discovered:
- Running 65%
- Stopped 35%
- Number of internet facing resources with malware:
- Only 20% (implies that internet-facing resources are not typically the end target)
- Percentage of assets infected with malware also containing personally identifiable information (PII):
- 75%
Risk context and alert prioritization
In addition to extensive malware detection capabilities, Orca also detects the weaknesses that malware and adversaries can exploit such as vulnerabilities, misconfigurations, exposed data, secrets, authentication issues, and lateral movement risk. And unlike agent-based tools and legacy vulnerability scanning solutions, Orca recognizes that risk is much more than just the severity score of the underlying malware or security issue. In reality, it also depends on the accessibility and business impact of the at-risk asset. By building a graph encompassing all your cloud assets, software, connectivity, and trust relationships, Orca properly prioritizes risk and alerts for your unique cloud environment. And if your organization is subject to regulatory frameworks requiring malware scanning, such as PCI-DSS, Orca can help you demonstrate compliance.
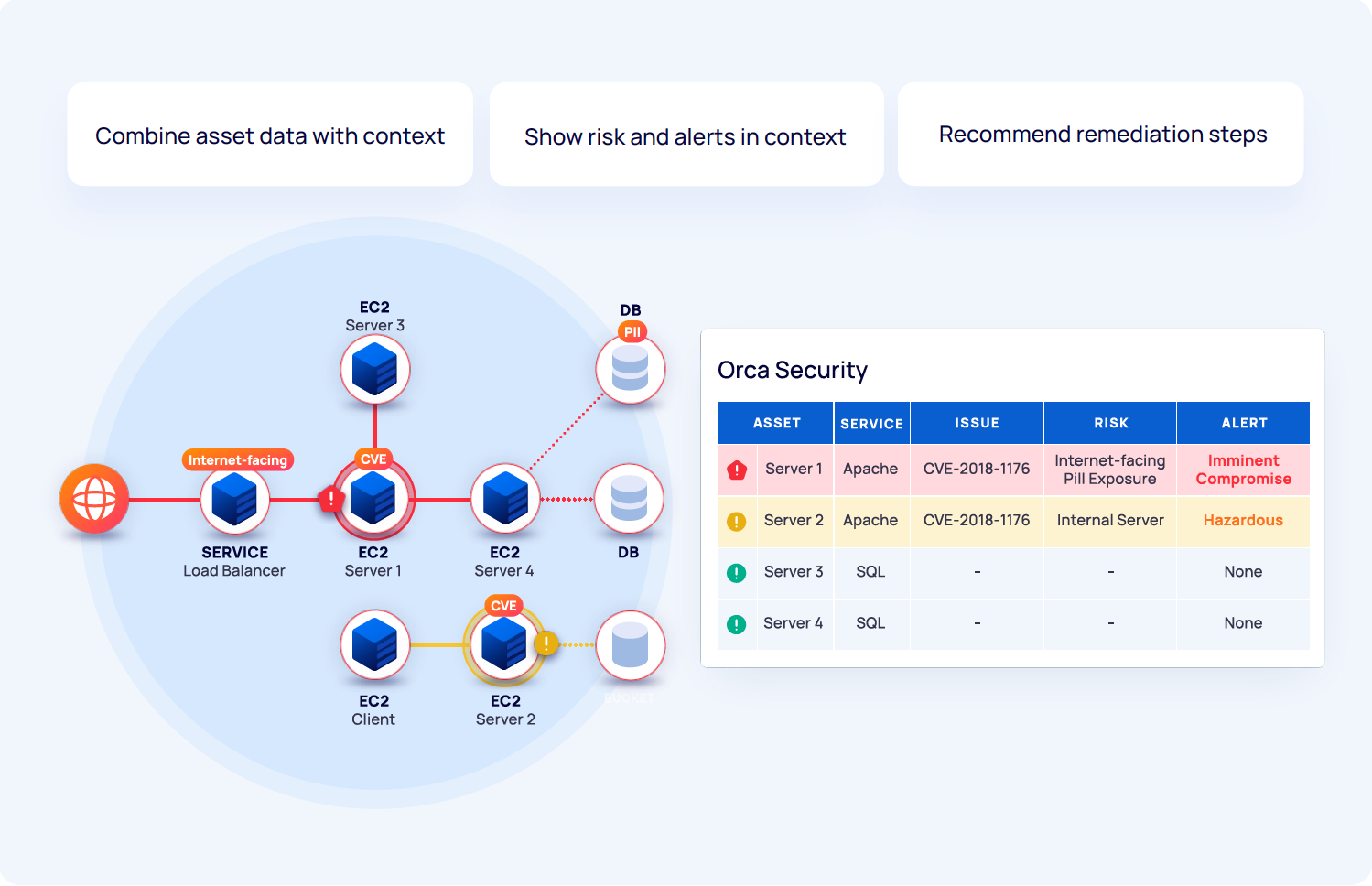
Figure 1: Orca combines asset and data characteristics with contextual information to prioritize risk and alerts in your environment
Orca also provides attack maps to vulnerable assets and data that demonstrate the most likely paths of exploit, along with actionable remediation instructions so you can quickly fix the issues that matter most.
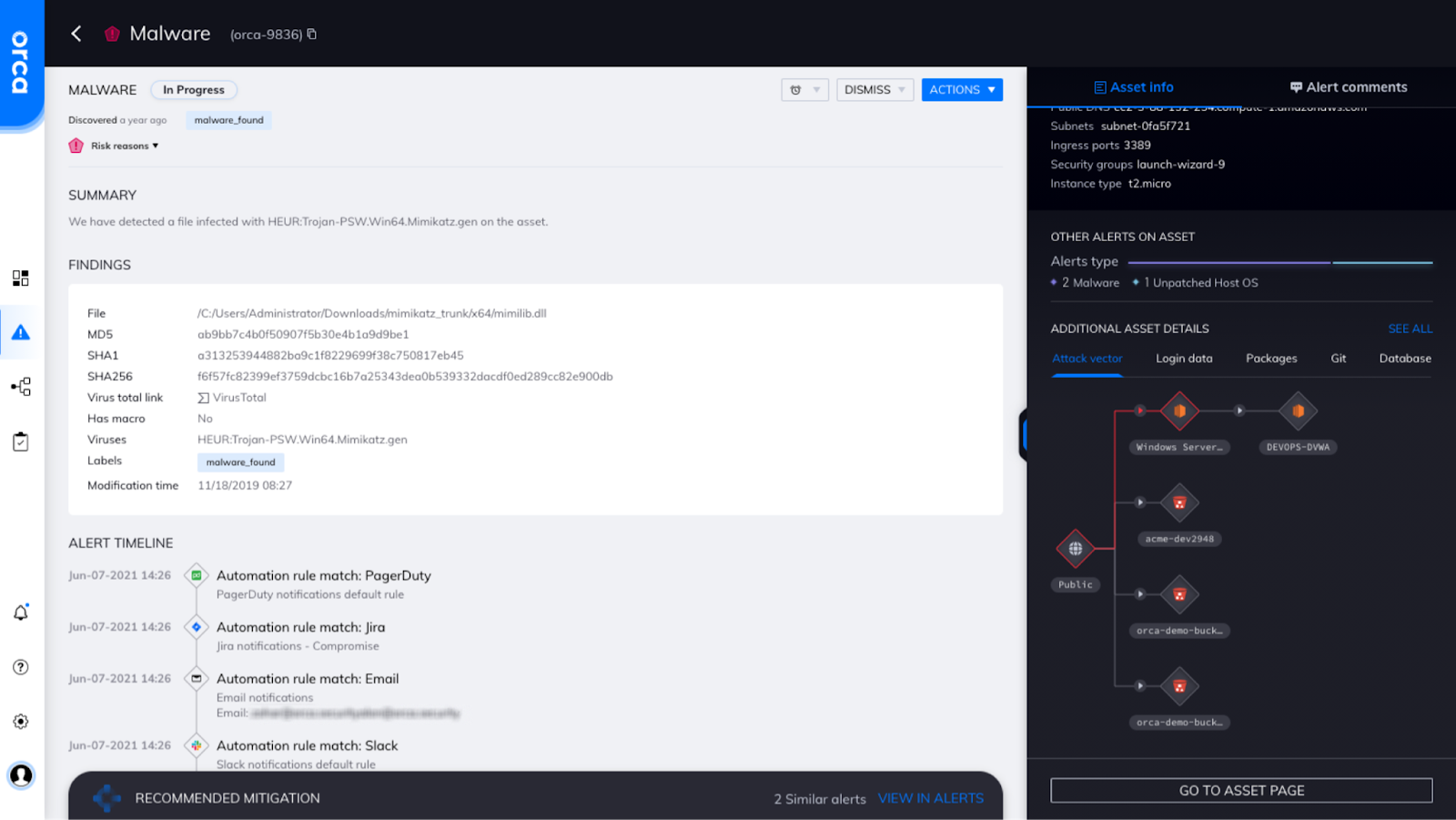
Figure 2: Orca malware alert showing alert timeline and probable attack vector map.
Protecting supply chains and CI/CD workflows
Orca’s non-intrusive frictionless technology and full stack visibility enables seamless monitoring of software supply chain pipelines to help discover malware before application deployment. With Orca, you can monitor your workflows for a wide range of issues from malicious files to identity and access management (IAM) hygiene.
Summary
Whether just beginning your cloud journey or a cloud-first organization, Orca Security can help to ensure that any malware resident on your workloads or being introduced into your environment via a supply chain attack or other vector is quickly discovered and put into the proper risk context. Orca provides instant-on security and compliance for IaaS platforms AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents. Orca detects and prioritizes risk in minutes ﹣ not months ﹣ and is trusted by global innovators, including Databricks, Lemonade, Gannett, and Robinhood.
For more information on Orca Security benefits we suggest reading:





