Stay Agile with Your Technology Company’s Cloud Security
Get flexible security with unlimited visibility across your entire multi-cloud estate. Orca Security provides cloud-forward technology companies instant-on security and compliance for AWS, Azure, and GCP—without the gaps in coverage, alert fatigue, and operational cost of agents.
The Challenge
Traditional Technology Company Cloud Security Solutions Slow Teams Down
Most cloud security solutions can’t keep pace with technology companies operating in the cloud, and managing siloed tools makes scalability out of the question.
Rapid innovation requires a security solution that can operate quickly, rendering legacy solutions a poor fit.
Technology is ever-changing, making risk prioritization difficult.
Fast growth makes it challenging to ensure full visibility into expanding cloud estates.
Empower your technology company with unified cloud security for high-tech
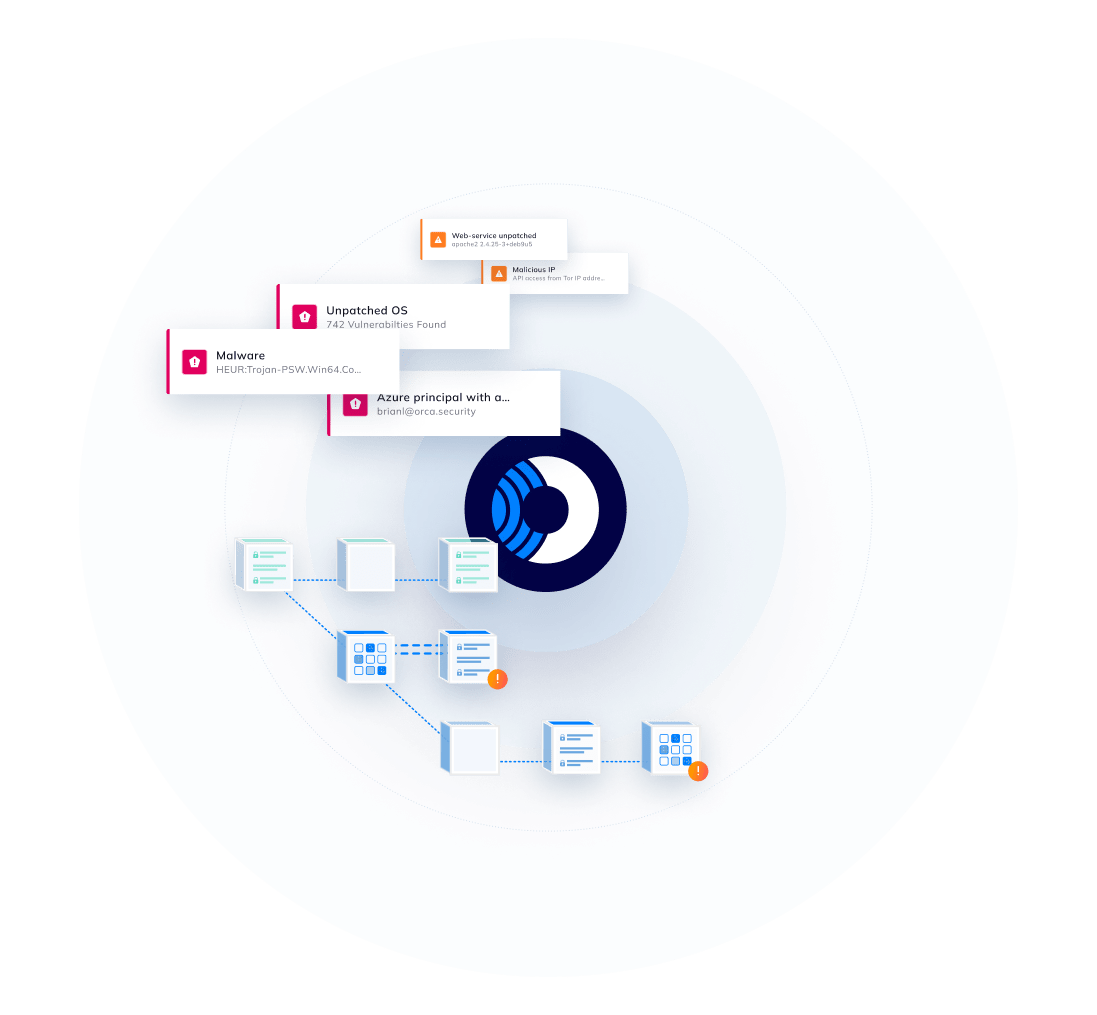
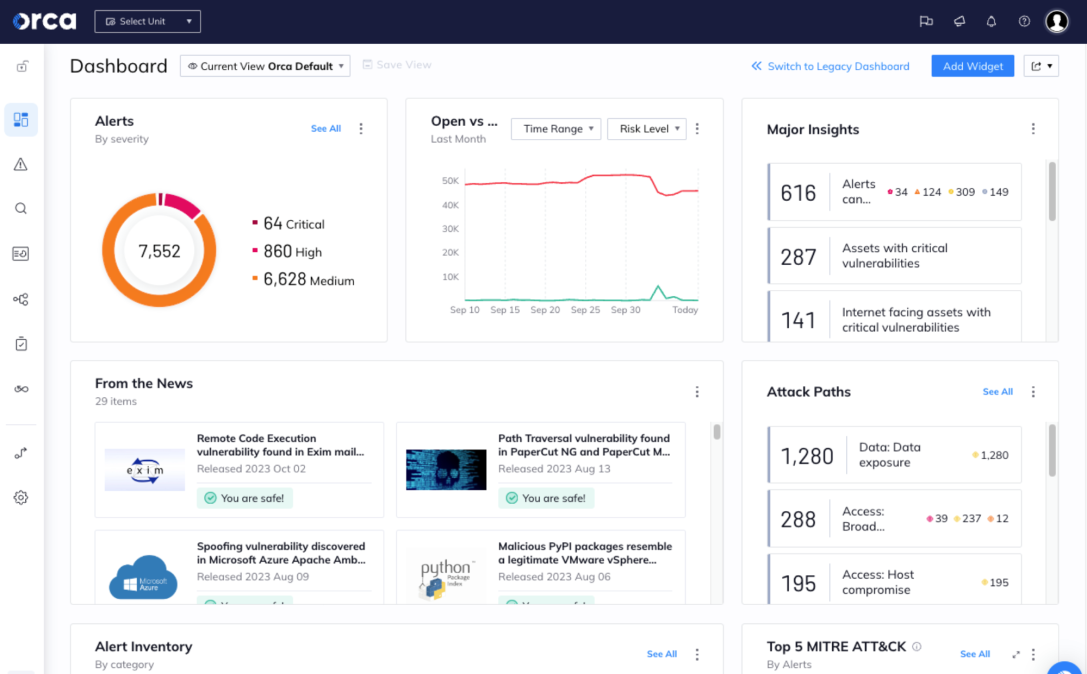
Orca’s patented SideScanning™ technology performs a deep scan of your cloud estate, detecting risks in workloads that other solutions can’t.
- A unified cloud security platform provides complete coverage to reduce security and compliance risks, alert fatigue, and TCO.
- Within minutes, Orca surfaces critical and prioritized cloud risks, including malware, misconfigurations, lateral movement risk, API risk, IAM risk, and unsecured sensitive data.
- Unlike legacy agent-based tools, Orca scans all assets—even custom OS versions and idle, paused, and stopped workloads.
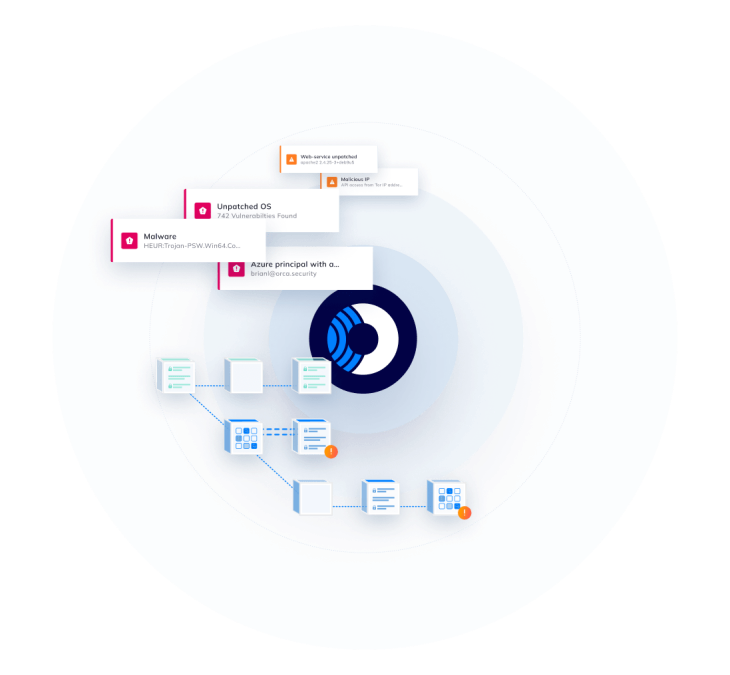

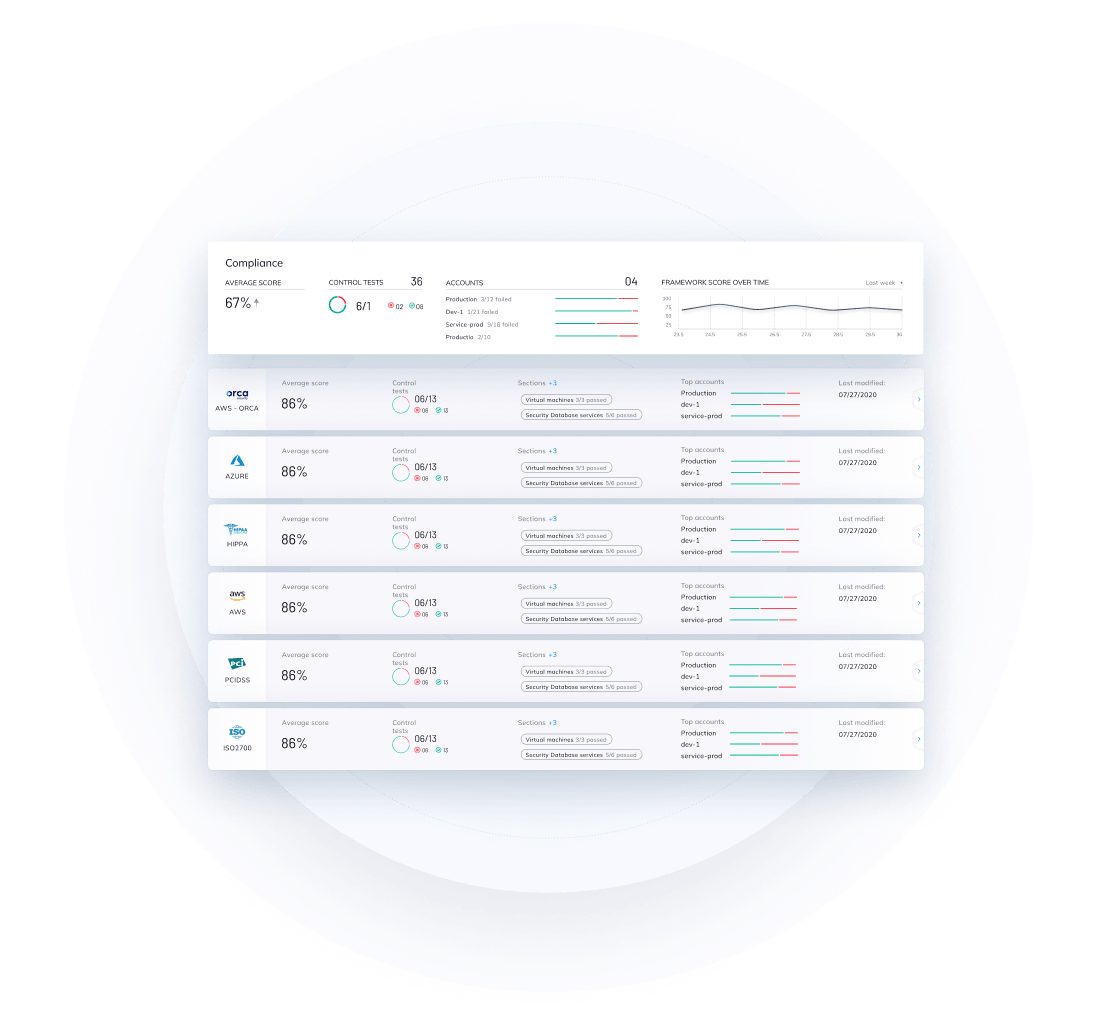
Effortlessly achieve compliance and regulation requirements for your technology company
Meet industry standards and regulatory requirements by demonstrating your ability to identify and protect sensitive data as well as detect vulnerabilities, malware, and improperly secured secrets — all from a single platform.
- Meet a vast array of compliance and data privacy mandates such as PCI-DSS, SOC 2, GDPR, NIST 800-53, HIPAA, and more.
- Orca supports a wide range of CIS control benchmarks including Apache CIS, AWS CIS, Azure CIS, Docker CIS, GCP CIS, Linux CIS, and Windows CIS.
Leverage Orca’s built-in compliance templates, or customize them to meet your specific needs.
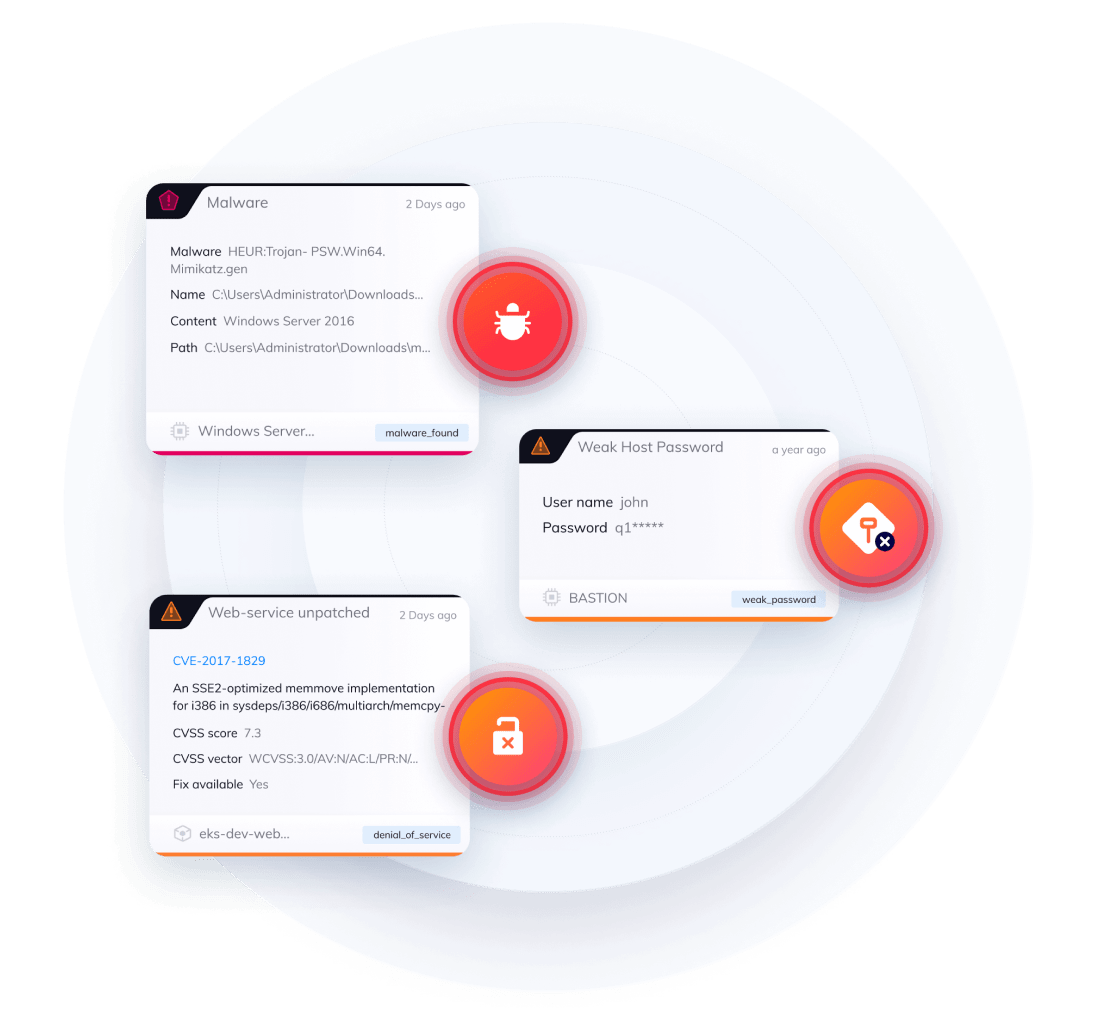
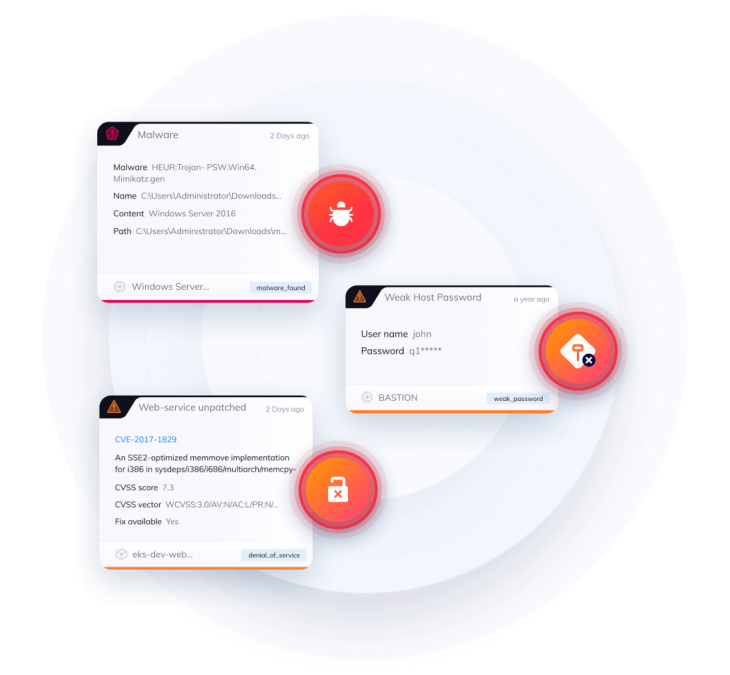
Prioritize critical technology services issues with context-aware security alerting
Unlike other tools that operate in silos, Orca sees the big picture and prioritizes risk based on context, allowing you to focus on truly critical issues.
- Orca considers the severity, accessibility, and business impact of a security issue to prioritize the critical few that pose the greatest risk.
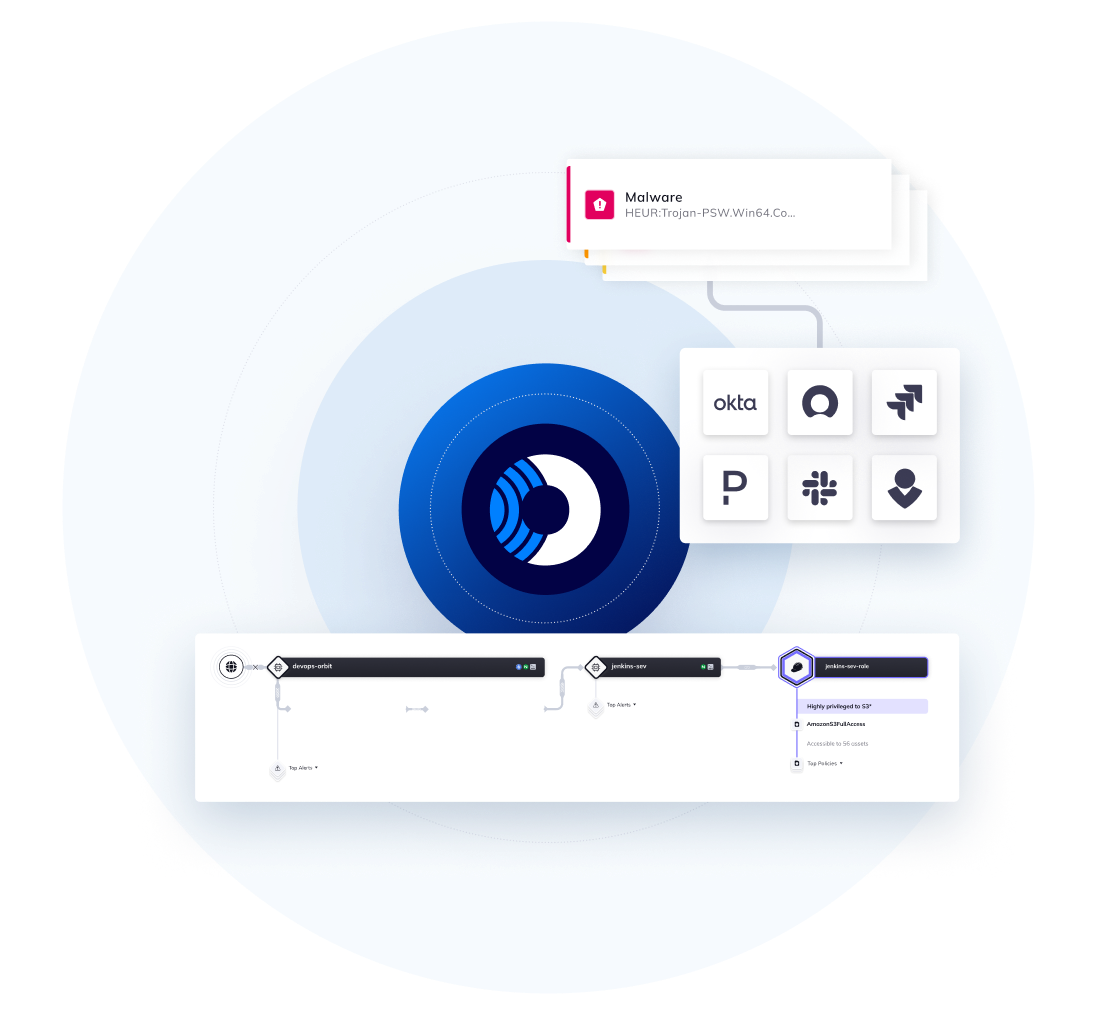
- Attack vector graphs enable you to see your cloud estate from an attacker’s perspective so you can stay one step ahead of your adversaries.
- Orca provides a precise path to remediation, empowering security teams to quickly address cloud security risks.

Develop a strong cloud security strategy for your high-tech company with actionable security intelligence
Query your cloud estate data to automate the investigation and assignment of cloud security issues to expedite remediation, improve efficiencies, increase ROI, and maintain regulatory compliance.
- Leverage 2,000+ built-in queries, or customize them to create your own with Orca’s intuitive and flexible query builder — no development experience needed.
- Forward alerts to email, PagerDuty, OpsGenie, or Slack, and perform automated ticketing with Jira or ServiceNow.
- Empower remediation teams to quickly resolve issues with alerts that include rich contextual information.