The cloud security landscape is constantly evolving, and traditional approaches to security may no longer be effective in today’s fast-paced cloud-native environment. While security teams may be able to identify a risk, finding the origin of the risk – the piece of code that needs to be adjusted, and the developer that owns it – can be a painstaking process. This is even harder in larger organizations.
Since inception, the Orca Cloud Security Platform has aided security teams by providing 100% frictionless coverage of their cloud environment, surfacing cloud misconfigurations, vulnerabilities, lateral movement, active infections and more. By prioritizing these risks, security teams can avoid long lists of alerts to focus on vital attack paths that span risk categories and clouds. Now, the Orca Platform is the first cloud-native application protection platform (CNAPP) to automatically link cloud risk detections in production with the development pipeline, dramatically simplifying and accelerating the remediation process for security incidents.
Orca’s new capabilities support Infrastructure-as-Code templates and containers, with the ability to trace a production misconfiguration or vulnerability directly to the original source code repository that was the source of the alert or risk, even down to the exact line of code that is at the root of the identified risk. Thus, Orca eliminates the need for security teams to spend time tracing the source artifacts and their respective owners, greatly reducing Mean Time to Resolution (MTTR) and freeing up valuable time for higher-value activities.
Gartner: A CNAPP Must Track Artifact Ownership and Provenance
In fact, Gartner states that this is one of the requirements that a CNAPP platform should offer. In their recent 2023 Market Guide for Cloud-Native Application Protection Platforms, Gartner recommends that security leaders responsible for cloud security strategies should:
“Ensure the right person/team is tasked with remediating an identified risk, by requiring CNAPP offerings to understand ownership and provenance of development artifacts. At a minimum, the CNAPP offering must understand what developer/development team created the artifact, when it was scanned, when it was deployed, and who has since changed or modified it.”
– 2023 Gartner Market Guide for Cloud-Native Application Protection Platforms (CNAPPs)
At the time of writing, Orca Security is the first CNAPP vendor to offer cloud artifact tracking as part of a comprehensive Cloud Security Platform.
Challenge: Security Teams Identify Cloud Risks, but then Spend Time and Resources Finding the Owner
Traditionally, cloud vulnerabilities and misconfigurations have been fixed where they live – if a web server was found to have a critical vulnerability, somebody would patch it at 3 am and, if necessary, reboot it. In the cloud, though, it’s not so simple. In order to effectively use the scale of the cloud, both workloads and infrastructure use a declarative paradigm, using artifacts such as Dockerfiles and Terraform to describe the desired state. In this world, patching a running container or changing the configuration of live infrastructure doesn’t solve the issue as they might be overwritten by a new build at any point in time. Instead, we have to fix the source of the issue, in other words, the container image or IaC template that included the risk and then redeploy it. Additionally, with Infrastructure as Code templates, drift can occur which leads to many misconfigurations.
This means that remediating risks in the cloud is often more difficult than it was in traditional environments because somebody has to correlate the observed problem with the code that it originated from, as well as the owner.
At least, it used to be more difficult.
Solution: Orca’s New Cloud to Dev Capabilities
Orca Security’s new Cloud to Dev capabilities now allow security teams to instantly see which container image or IaC template is the source of the detected risk, along with its owner(s), and will even pinpoint the line that needs to be fixed. For example, when a vulnerability is detected in a running container, Orca will identify the source code repository and the Dockerfile responsible for adding the vulnerable package.
This means that security issues can instantly be assigned to the responsible development teams for fast remediation and avoids security teams having to waste time tracing the source and respective owners. With these new capabilities, Orca greatly reduces the organization’s Mean Time to Resolution (MTTR) and at the same time frees up valuable time for security teams allowing them to focus on higher-value activities. Orca can even recommend a pull request to fix the issue or automatically surface a ticket in Jira for remediation.
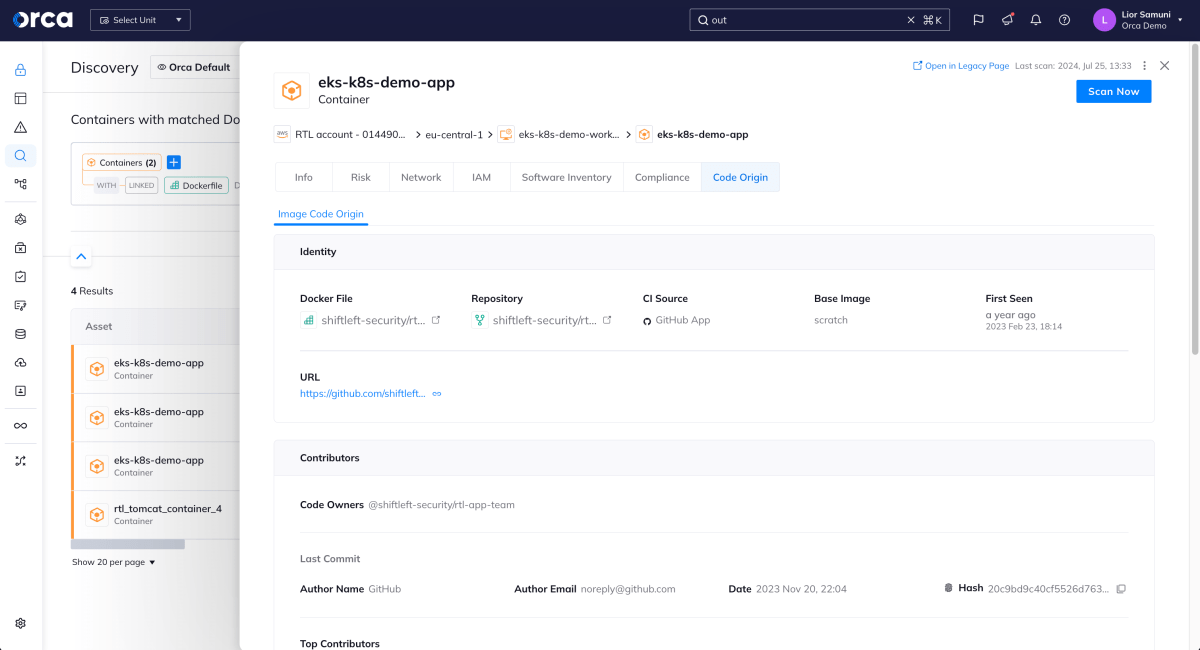
Increased visibility and management of IaC assets
In addition to the benefits mentioned above, Orca Security’s Cloud to Dev approach will also allow for increased visibility and management of cloud assets through the use of Infrastructure as Code (IaC). Orca Security will scan your IaC code to provide insight into the state of cloud assets and their configurations. For each managed cloud asset, Orca Security can reference the corresponding IaC module to ensure that the asset is properly configured and that there are no discrepancies between the desired state and the actual state of the asset.
Additionally, Orca warns about unmanaged assets or drifts from the IaC configuration, allowing for quick remediation. Misconfiguration alerts related to cloud assets can be addressed through Orca’s IaC integration. When a misconfiguration is detected, Orca can suggest fixes to the corresponding IaC module. This provides a streamlined approach and ensures that the desired state of the infrastructure is maintained over time.
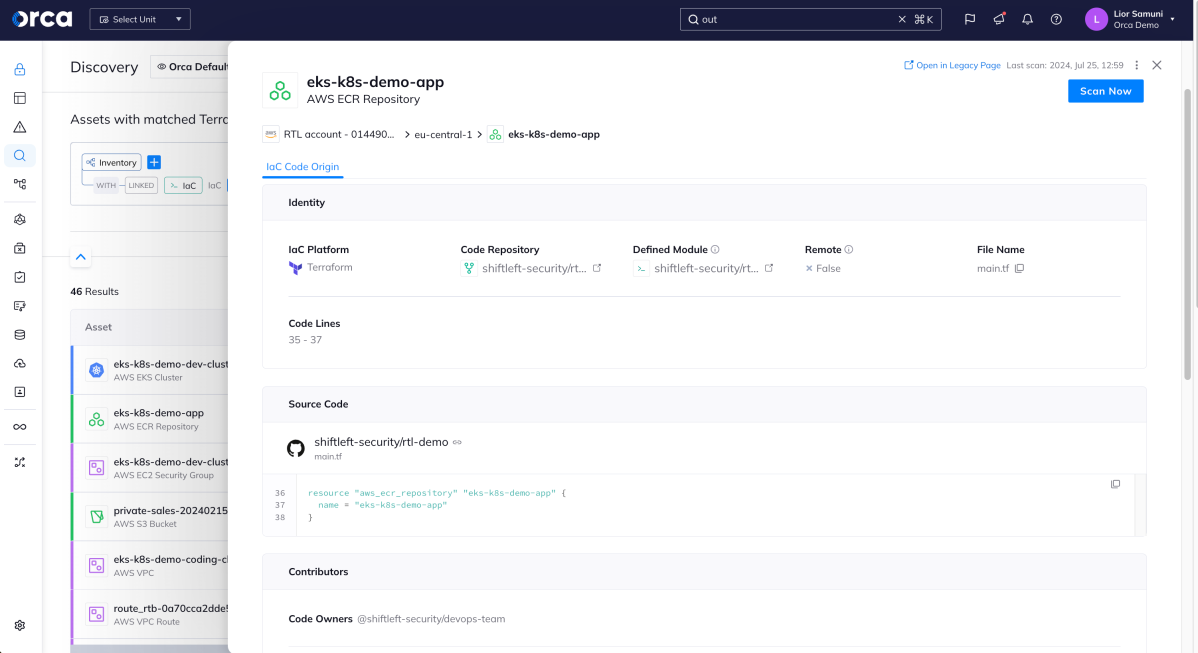
Grouping risks by source
Tieing production risks to the source code comes with an additional major benefit – the ability to group risks by source. So for example, you might see that a particular container image containing a risk has been deployed many times in production. By fixing one container image, a great number of production risks can be resolved in one go, providing the greatest risk reduction with the least effort.
Meet the Orca GitHub app
Orca’s GitHub app allows security teams to quickly onboard GitHub repositories, accounts, and organizations without manual configuration. The GitHub app allows teams to frictionlessly automate scanning application code and Infrastructure as Code (IaC) for embedded secrets, vulnerabilities in dependencies, and violations of security policy and best practice.
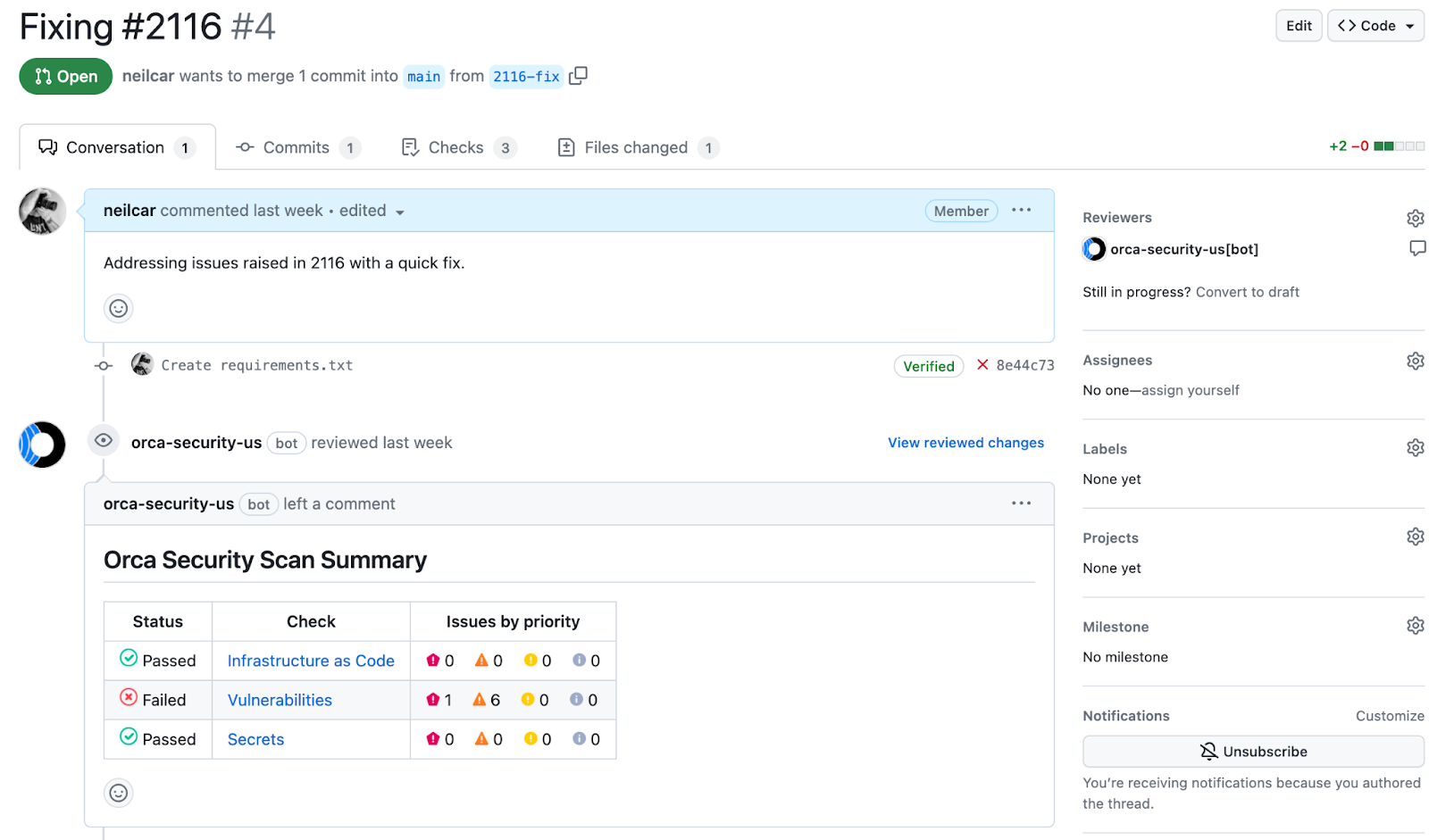
Detecting Unmanaged Assets
In addition to the benefits mentioned above, Orca’s Cloud to Dev capabilities also help organizations implement an everything-as-code approach, which greatly reduces the risk of errors and security risks, as well as improve developer efficiency. Since Orca provides a complete inventory of cloud assets and their source artifacts, Orca can identify resources that aren’t managed by code, enabling organizations to respond quickly to unmanaged assets.
Want to find out more about Orca’s Cloud to Dev Capabilities?
The Orca Cloud Security Platform identifies, prioritizes, and remediates risks and compliance issues across your cloud estate spanning AWS, Azure, Google Cloud, Alibaba Cloud, Oracle Cloud, and Kubernetes. To find out more watch a 10-minute demo video of the Orca Platform.
Ready to get hands on? Sign up for our free, no-obligation, 30-day risk assessment, get set up in 30 minutes and experience first-hand how Orca can save your security and development teams valuable time and dramatically improve your cloud security posture.





