Visibility is a foundation of any cloud security platform. Security teams need to easily identify—both broadly and granularly—all of their cloud resources across cloud accounts, whether they are compute instances, images, alerts, vulnerabilities, IAM user and policies, network services, or others. Security practitioners also need to be able to query and filter on cloud asset properties, and do this with ease, since in some cases time is of the essence (for instance in a zero-day situation or ongoing attack).
For this purpose, the Orca Cloud Security Platform includes a Discovery Query Builder that empowers security teams to quickly and efficiently query their cloud environments up to the deepest granular level, enabling them to make data-driven decisions based on this information.

Furthermore, Orca’s Unified Data Model enables context-aware analysis of detected weaknesses across the entire cloud estate, allowing organizations to fully understand where their most critical assets are and prioritize the risks that endanger those assets.
What is Orca’s Discovery Query Builder?
The Orca Query Builder provides a user-friendly approach to creating queries without requiring a deep understanding of the database structure or knowledge of any query language. It’s an easy way to understand your cloud risks, either through pre-built query templates, or building your own searches.
Orca’s intuitive query builder can be used to create custom alert queries or leverage over 2,000+ system queries that are available out-of-the-box, in order to:
- Query data to filter or search for assets
- Search and investigate security issues
- Monitor compliance violations
Getting Answers to Granular Questions: Three Examples of Orca Discovery Queries
Just having access to cloud resource data is not enough. Even though dashboards are a valuable and common way to present data, what’s also needed is a quick and easy way for security and compliance teams to query the data to find immediate answers to questions such as:
- Which Internet-facing assets are exposed to critical risks?
- What permissions have not been used for over 90 days?
- Which assets are vulnerable to a new zero-day vulnerability?
Below we’ll look at three examples of queries to demonstrate the value of Orca’s Discovery Query Builder.
1. Identifying VMs that are internet-facing and contain PII
The first use case is identifying all compute services, in this case let’s limit it to virtual machines, which are internet-facing and contain personally identifiable information (PII). These VMs require you to pay heightened attention to them, as they could represent a high risk. It would be a good idea to investigate why these are configured as such.
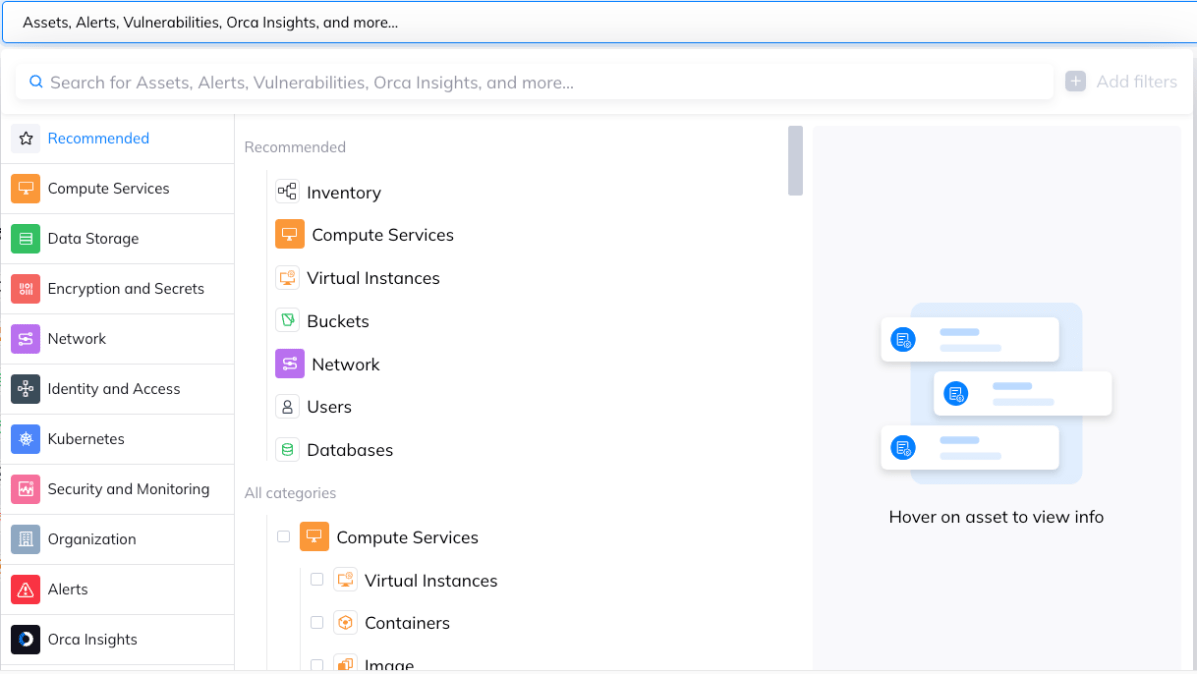
In the Discovery section on the Orca Platform, you’ll find an opening menu of cloud resource categories, and as we can see in the screenshot below, we can start with choosing ‘Virtual Instances’.
Note that the ‘Virtual Instances’ category is a great example of how Orca enables security teams to operate in multi-cloud environments – even though virtual machines may have different attributes and even names across different cloud providers, Orca rolls up the AWS EC2 instances, the Azure Virtual Machines, the GCP Virtual Machine Instances, and a variety of other types of VMs into a single category that we can work with here without complication.
That immediately brings us to the query builder main section, and by using the search bar, I’ve easily filtered these VMs by adding “is internet facing” as well as “has PII”.
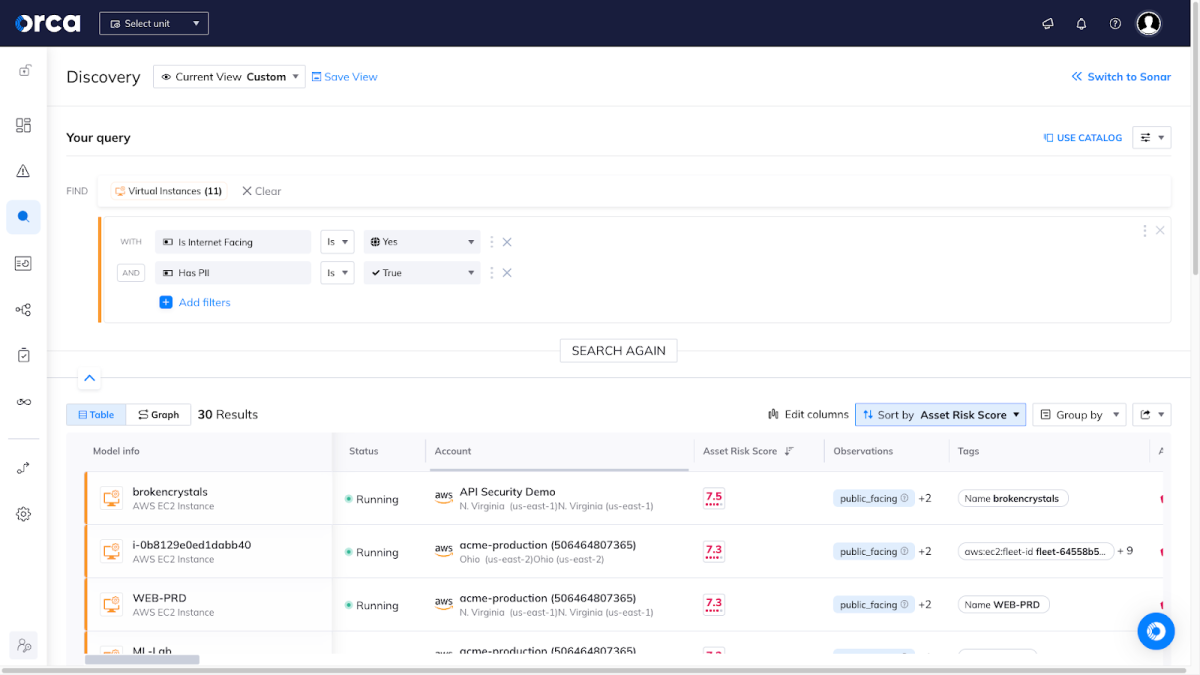
It’s important to mention here that because Orca has already scanned these VMs, we now know which cloud accounts they are located in, whether or not they are internal or public-facing, and we know whether they contain sensitive data such as PII. The Discovery builder is just an easy way to present that data.
The query results are listed by default according to the Asset Risk Score (which ranges from 1.0 to 10.0), from highest to lowest. The score indicates the risk level they pose to the organization, giving you the granularity needed to understand the severity and urgency of the alerts on each asset.
Naturally, we’ll want to investigate the ones with the highest Asset Risk Score. If we click on the AWS EC2 instance ‘brokencrystals’ we’ll open a new tab with a dedicated asset page, showing the various security risks attached to that asset, which category they fall under, network information, and more.
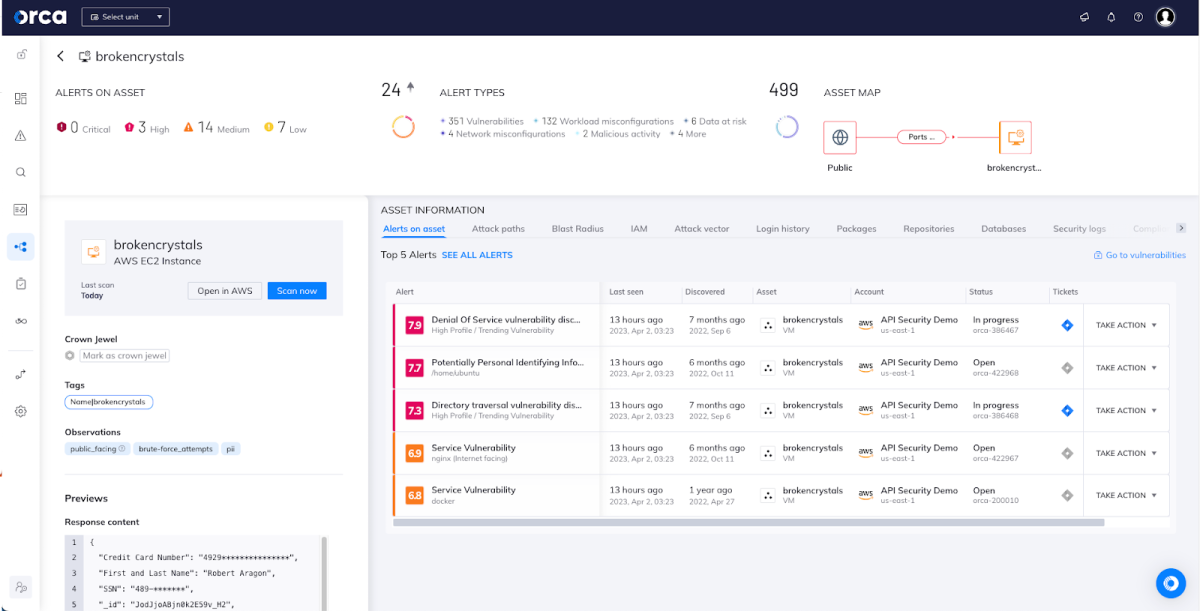
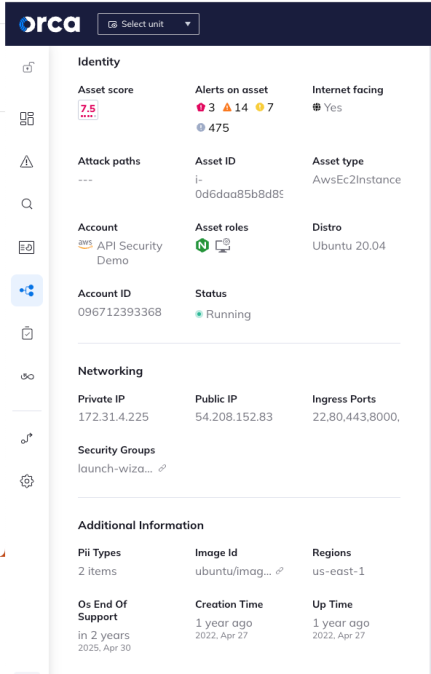
While it’s valuable to know that the asset has risks and that it may be open to the Internet, Orca also takes it a step further and uses an external network scanner to show that the endpoint is available and returning an answer – in this case, we can see that it’s returning sensitive data in the payload that our scanner received in response!
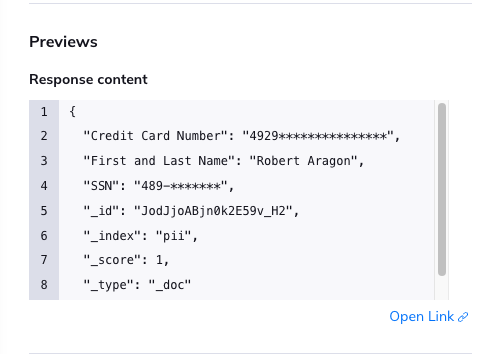
All of this information is valuable to security and compliance teams responsible for ensuring that sensitive data is protected, as well as to help teams understand which assets pose the highest level of risk, enabling them to remediate accordingly.
2. Investigating unused IAM roles and credentials
Our second use case involves querying our cloud estate for IAM unused roles and unused credentials for the last 30 days.
This information can be helpful for either of the following reasons:
- General security hygiene and ensuring that IAM policies adhere the principle of least privilege (PoLP)
- In the case of a security incident, as part of the triage and remediation processes
One cool feature inside the Discovery query builder is the catalog of pre-built queries. These save users even more time (in an already easy to use tool) and remind them of valuable queries to consider. As this example of ‘Roles that haven’t been used in 30 days’ is part of this catalog (as part of the Identity and Access category), it’s worthwhile just to briefly show what it looks like.
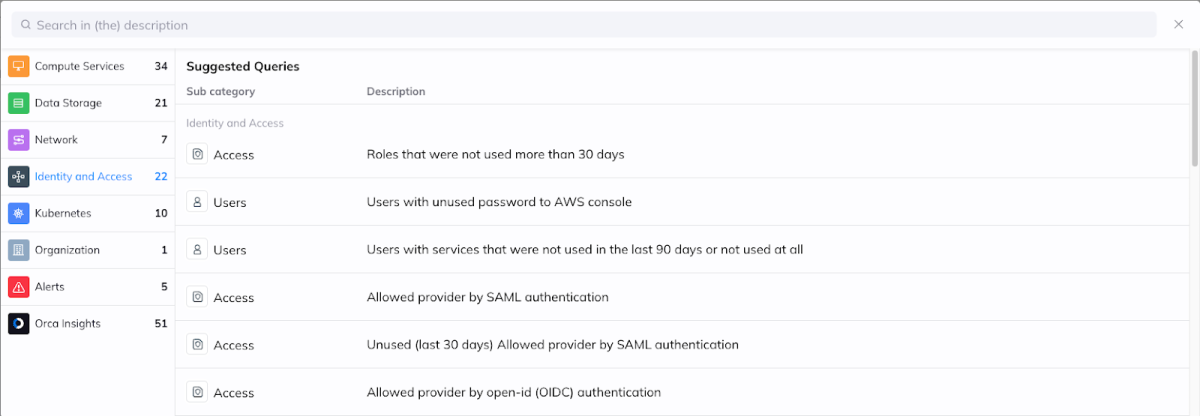
In addition, the catalog queries are also shown when searching for a specific word in the Discovery search bar.
Here is what the actual query and results look like:
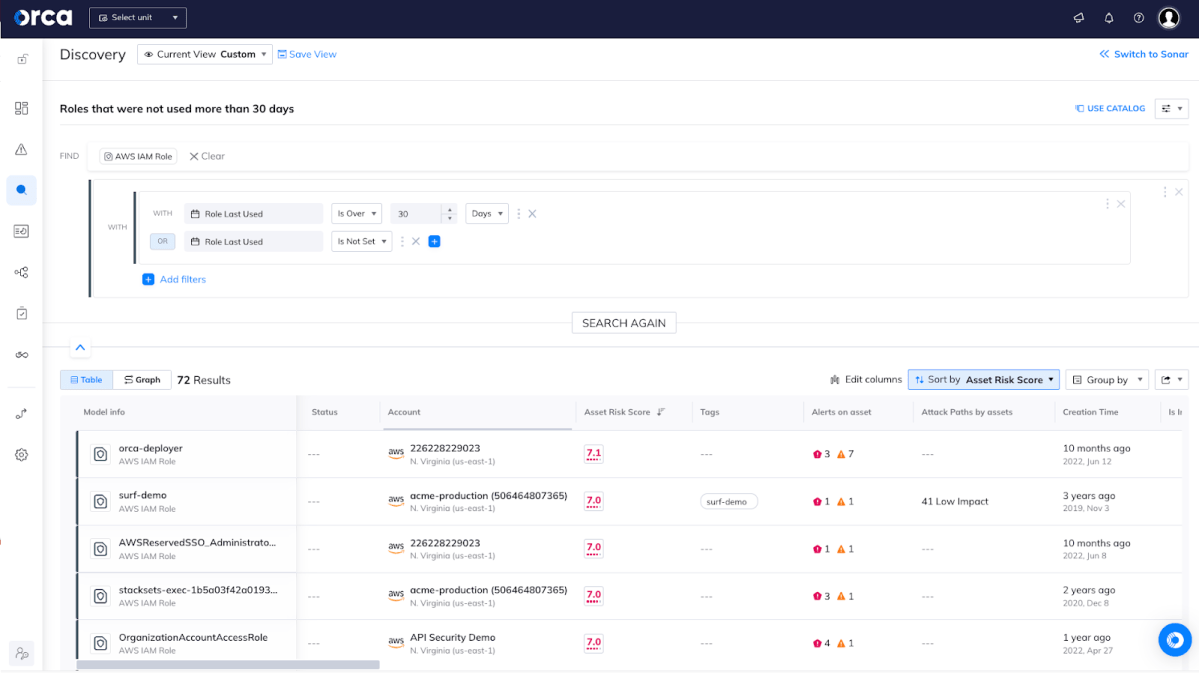
Once again, you can see the results listed according to the highest Asset Risk Scores, in this case the AWS IAM Role ’orca-deployer’ (all screenshots in this article are from the Orca Security demo environment). It’s ranked the highest likely due to the 10 total risks attached to that role.
Upon further investigation, it appears that this role has gone unused for more than 90 days, and can be assumed by an AWS identity which is not part of the account.
It is worthwhile for a security team member to look into why this unused role still exists. Removing orphaned and unused IAM roles eliminates the risk that a forgotten role will be used accidentally to allow unauthorized users access to AWS resources.
3. Obtain a full inventory of assets and resources that contain a dependency
Our final use case consists of using Discovery to quickly and easily obtain a full inventory of assets and resources that contain a dependency. This would help security teams to prepare ahead of a potential vulnerability disclosure before all the details surrounding that vulnerability are published, or to rapidly investigate known vulnerabilities after.
For example, the OpenSSL Vulnerability that was revealed in October 2022, was already generating rumblings in online security forums before the official announcement. OpenSSL is a toolkit to secure network communications and is widely used by Internet servers, including the majority of HTTPS websites. Similar to the Log4j vulnerability, OpenSSL is often included as a software dependency inside larger compute services. Having a quick and easy way to gain visibility into which systems include OpenSSL can be super important.
Using Orca’s Discovery, we’ve chosen ‘Compute Services’ that has a linked ‘Installed Package’ that contains ‘OpenSSL’ in the name. We quickly see 245 results.
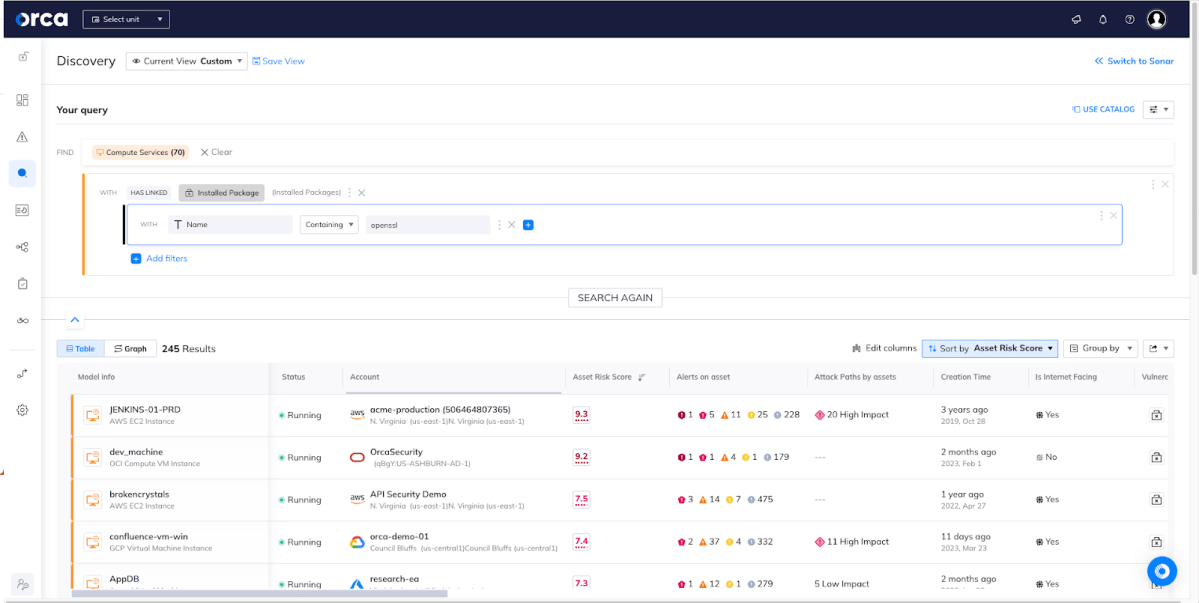
Furthermore, as in the OpenSSL vulnerability example, Orca’s Discovery query builder can also:
- Show you which versions of a particular dependency are installed in your organization’s cloud estate (in the October 2022 vulnerability, the vulnerable versions were 3.0-3.0.6),
- Understand which assets need to be prioritized for patching: Internet-facing assets, or assets that could create an attack path to your most critical assets should always be patched first.
- After patching, verify that all vulnerable assets have been updated to the unaffected versions.
All of this is to say that Orca’s Discovery provides quick and comprehensive access to critical information at the time of need.
Start Using Orca’s Discovery Query Builder Today
Orca Discovery provides an easy and effective way for cloud security engineers, compliance auditors, and DevOps engineers to query their entire cloud environment and gain broad visibility. In a couple of clicks, you can select assets, infrastructure, applications, and other objects and further filter them by means of an intelligent filtering component.
If you are an Orca customer, you can immediately begin leveraging the value of the Discovery Query Builder by clicking on the discovery icon on the left navigation bar and begin building and saving some of your most valuable and frequent queries.
If you are not an Orca customer and would like to see our Discovery Query Builder in action, schedule a demo, or sign up for a Free Risk Assessment and experience the comprehensiveness and simplicity of securing your entire cloud estate with Orca’s agentless platform.






