We are very excited to announce that the Orca Cloud Security Platform now includes the industry’s first fully agentless API Security capabilities to help organizations identify, prioritize, and address API-related misconfigurations and security risks across their multi-cloud environment.
Why API Security is so important
APIs (Application Programming Interfaces) serve as the connections between computer programs, web applications and mobile applications. Application development teams build APIs to create integrations and to fetch the data needed to facilitate application operations.
With light-speed adoption of APIs in recent years, threats of misuse and malicious attacks can cause application disruptions or lack of service, resulting in potential lost revenue, customer frustration, and potential leakage of sensitive data. Gartner writes that “API security challenges have emerged as a top concern for most software engineering leaders, as unmanaged and unsecured APIs create vulnerabilities that could accelerate multimillion dollar security incidents.”
Apart from the threats themselves, just knowing which APIs are in your cloud workloads is complicated. Given the pace of cloud-based application development, it’s almost impossible to keep track of new and changed APIs. Application complexity leads to misconfigurations, as well as unmanaged and unsecured APIs that create vulnerabilities. In fact, Gartner predicts that by 2025, less than 50% of enterprise APIs will be managed. API Security, therefore, is greatly increasing in importance.
Current API Security tools are lacking
While there are a number of solutions dedicated to the protection of web traffic and APIs, they typically fall short for a number of reasons:
- They are either agent-based or network-based solutions, which leads to blind spots (you can’t see or analyze APIs on workloads that don’t have an agent), an incomplete API inventory, scalability problems, performance degradation and high TCO.
- They only utilize methods such as Web Application Firewalls (WAFs) or API Gateways that—while important—provide limited or incomplete API Security. Both WAFs and API Gateways present a challenge to organizations that need to route traffic through their API Gateway. Additionally, security teams may lack visibility into APIs that don’t reach the gateway.
- Point solutions have no insight into the wider context of cloud risks. Current API Security solutions do only that—API Security—with no wider context on cloud misconfigurations, workload vulnerabilities, takeover susceptibility, or other risks. This results in the need for security teams to manage another separate product in their already large security stack and process even more security alerts to find out which issues should be prioritized – without ultimately solving the correct problems.
How Orca’s API Security is different
Recognizing these challenges, and leveraging our patented SideScanning™ technology that has deep and wide insight into every cloud workload without requiring an agent, as well as dynamic public endpoints scanning, we have expanded the Orca Cloud Security Platform to include comprehensive API Security. With Orca’s new API Security capabilities, organizations can now obtain an updated inventory of all managed and unmanaged APIs, detect API-related misconfigurations and vulnerabilities, and be alerted to API drift and changes.
As opposed to agent-based solutions, or solutions that rely on a combination CDN workers and traffic mirroring, that only provide insight into the APIs on the servers that have agents installed, the Orca Platform leverages its agentless technology and comprehensive insights into cloud workloads and configurations to provide security teams with a complete inventory of all APIs in their cloud estate without any blindspots.
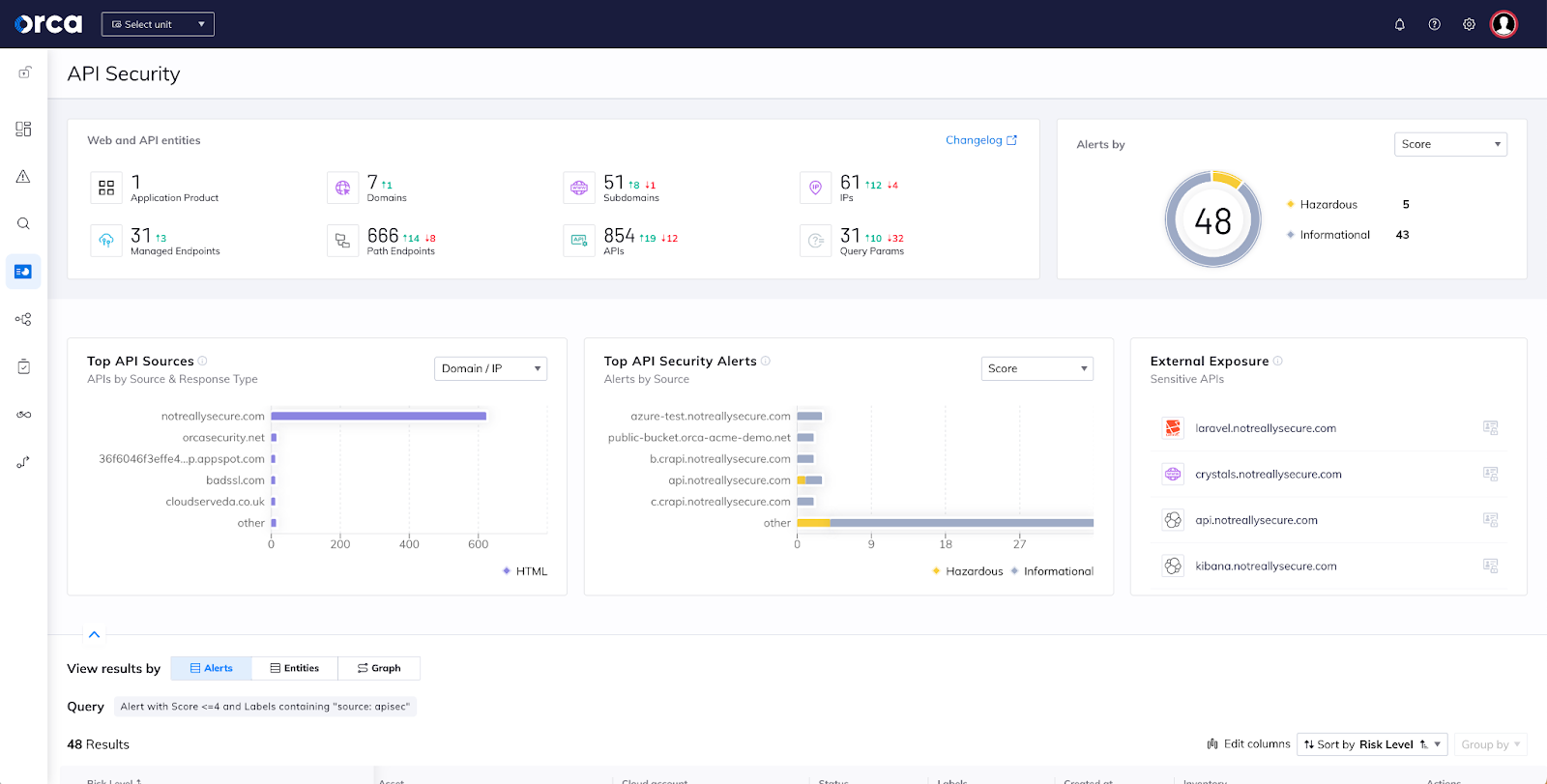
By combining detected weaknesses in APIs with other risks found in the cloud environment, such as vulnerabilities, malware, asset or identity misconfigurations, and potentially exposed PII, Orca has the necessary context to understand which API risks are the most critical so that security teams can focus on what matters most.
Orca delivers complete API Discovery and Security Posture Management
Within minutes, application security and cloud security teams can now have complete observability of API endpoints in their environment, manage API risks, and adhere to API security compliance requirements. As API usage continues to increase exponentially, and threat actors seek to exploit APIs as an attack vector, Orca enables organizations to take proactive and preventive steps to reduce their API attack surface.
Orca’s API Security provides organizations with the following capabilities:
- Inventory: Have an extensive view of the API attack surface with a continuously up-to-date inventory, without blind spots.
- Posture Management: Identify, prioritize, and address API security and compliance risks.
- Drift Detection: Identify recently added and deleted APIs and API drift.
All of Orca’s API Security capabilities are included in a single Cloud Security Platform, without the need for additional point solutions such as Vulnerability Management, Cloud Security Posture Management, Cloud Workload Protection, Cloud Infrastructure Entitlement Management or Cloud Detection and Response. The ability for security teams to access all this information from a single platform, greatly reduces learning curves and inefficiencies, and minimizes alert fatigue, allowing teams to instantly understand which risks in your cloud estate are the most pressing.
1. Continuous API discovery and inventory
API Security needs to start with full insight into which APIs are running in the cloud environment. After all, how can you protect something you don’t even know about? However, the speed of application development makes it incredibly challenging to keep track of new and changed APIs, or if an API is behaving differently than was intended.
Agent-based solutions struggle to keep up, since they can only see the assets where their agent has been installed. With Orca on the other hand, security teams gain continuous, unparalleled visibility with 100% coverage, and are quickly notified when a new API or service is added by development teams.
Orca’s API discovery is continuous, without the need for time-consuming agents, edge workers, or bringing in a vendor to analyze your logs.
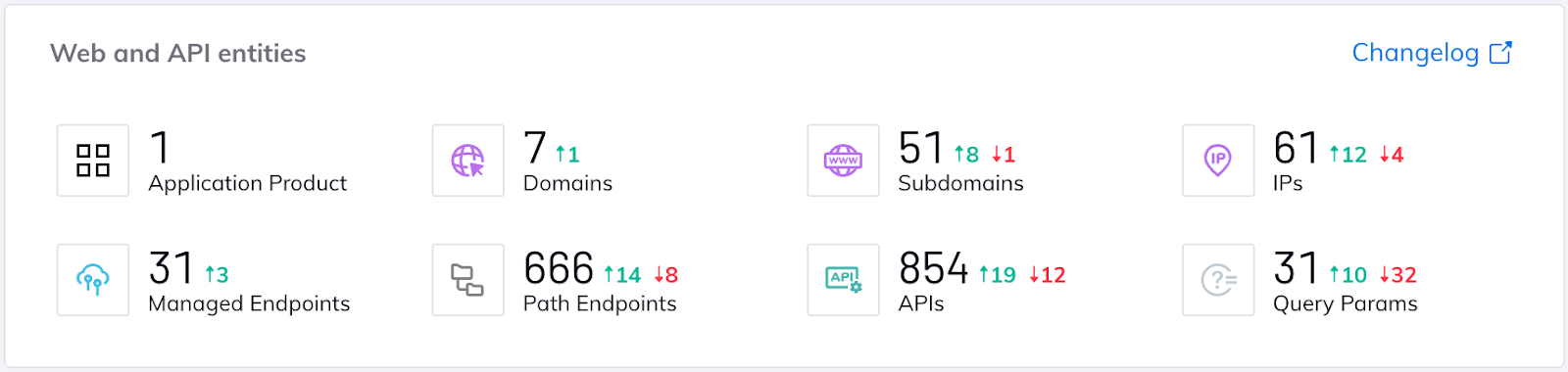
This wide and granular knowledge of your API estate includes the ability to track and analyze all of your API assets, including applications, domains, subdomains, path groups, users, and API endpoints. These include both managed and unmanaged APIs, as Orca is able to extract and analyze data from access logs of both managed (such as AWS API Gateway, Application Load Balancer) and unmanaged gateways (such as NGINX, Apache, and others).
API paths are displayed as an interactive graph with smart labels, allowing you to click on any domain, subdomains and connection to view more data. In this graph, you’ll be able to analyze the workloads, and access logs that are stored within them, to being able to see all API endpoints, requests, and server responses – consolidating all these logs into a coherent map in which you can see your entire API tree structure, and what is being configured and run.
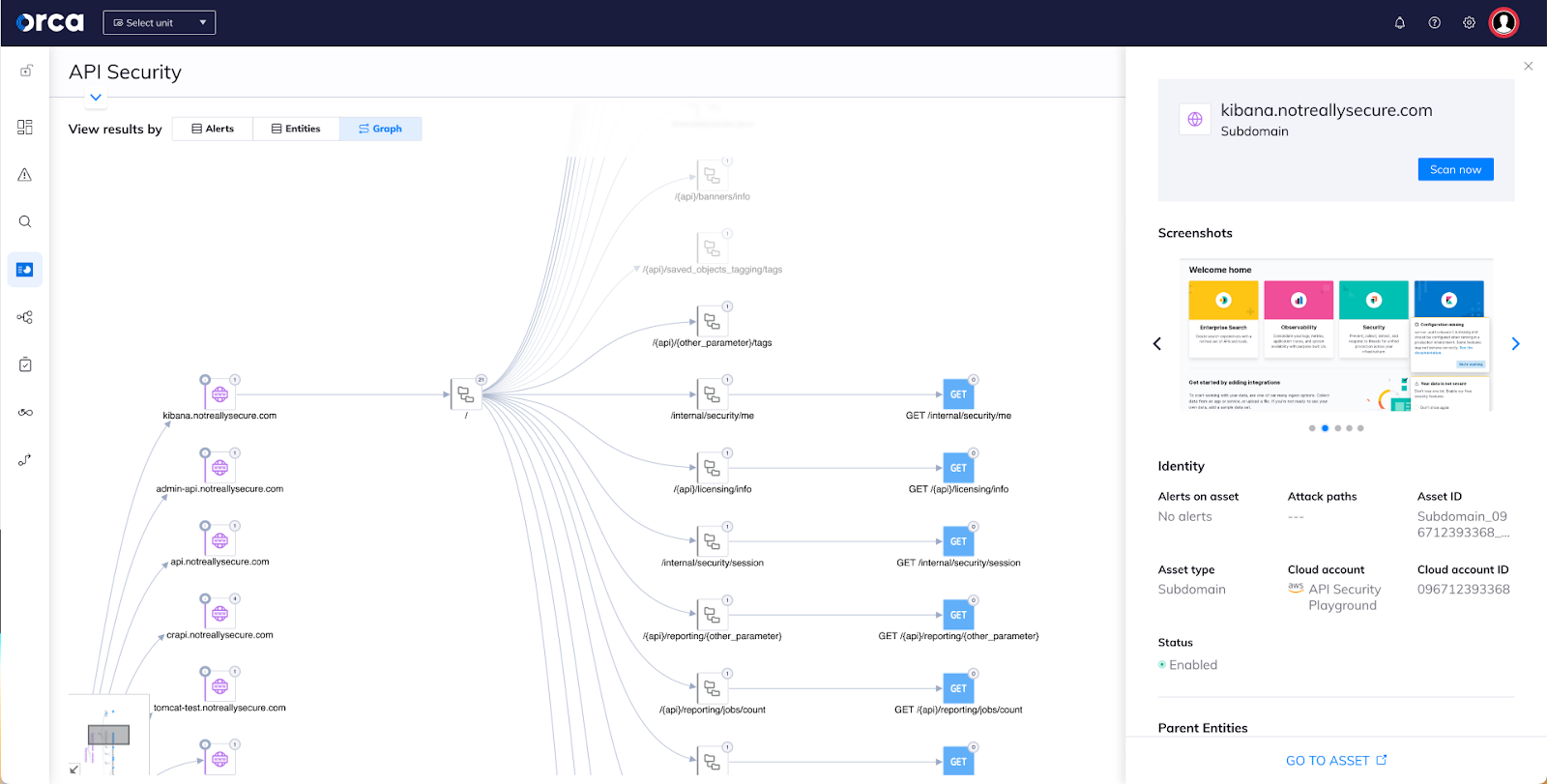
You can do a deep dive into assets and answer questions such as:
- What assets are accessible from the Internet, and what APIS / data do they expose?
- How many API endpoints contain access to personally identifiable information (PII)?
- How are my APIs implemented and connected with other API entities, starting from Applications or Domains?
- What are my APIs of a specific Application / Domain / Subdomain?
- What are my Application / Domain / Subdomain / APIs with some custom conditions?
- Which of my assets are subject to Domain / Subdomain takeover?
- Which of my API endpoints has a risk of BOLA exploit?
In addition, screenshots of domains and subdomains provide a real-world picture of a publicly exposed API.
2. API Security Posture Management
As API usage continues to increase exponentially, and threat actors seek to exploit APIs as an attack vector, Orca enables organizations to take preventive steps to reduce their API attack surface. The API asset data that Orca provides allows security teams to easily and continuously identify, address and prioritize all API risks and configuration-related vulnerabilities. Whether alerting to an API that exposes sensitive data externally, or a subdomain with a recent expiration date, each alert is given a severity score so that teams can prioritize risks accordingly and accelerate mitigation actions.
Alerts include mappings to risks in the OWASP API Security Top 10, for example Broken User Authentication or Security Misconfiguration. You can search the number of risks for a specific severity score, or you can search for the risks associated with a particular domain or subdomain, or alerts over a particular time period.
In addition, alerts can be grouped according to risk categories, such as authentication, neglected assets, data protection, malicious activity, and Orca Best Practices. Each alert, when clicked on, will provide a wealth of information such as alert findings, an alert timeline asset ID, asset ID, cloud account name, a summary of the alert as well as recommendations for mitigation.
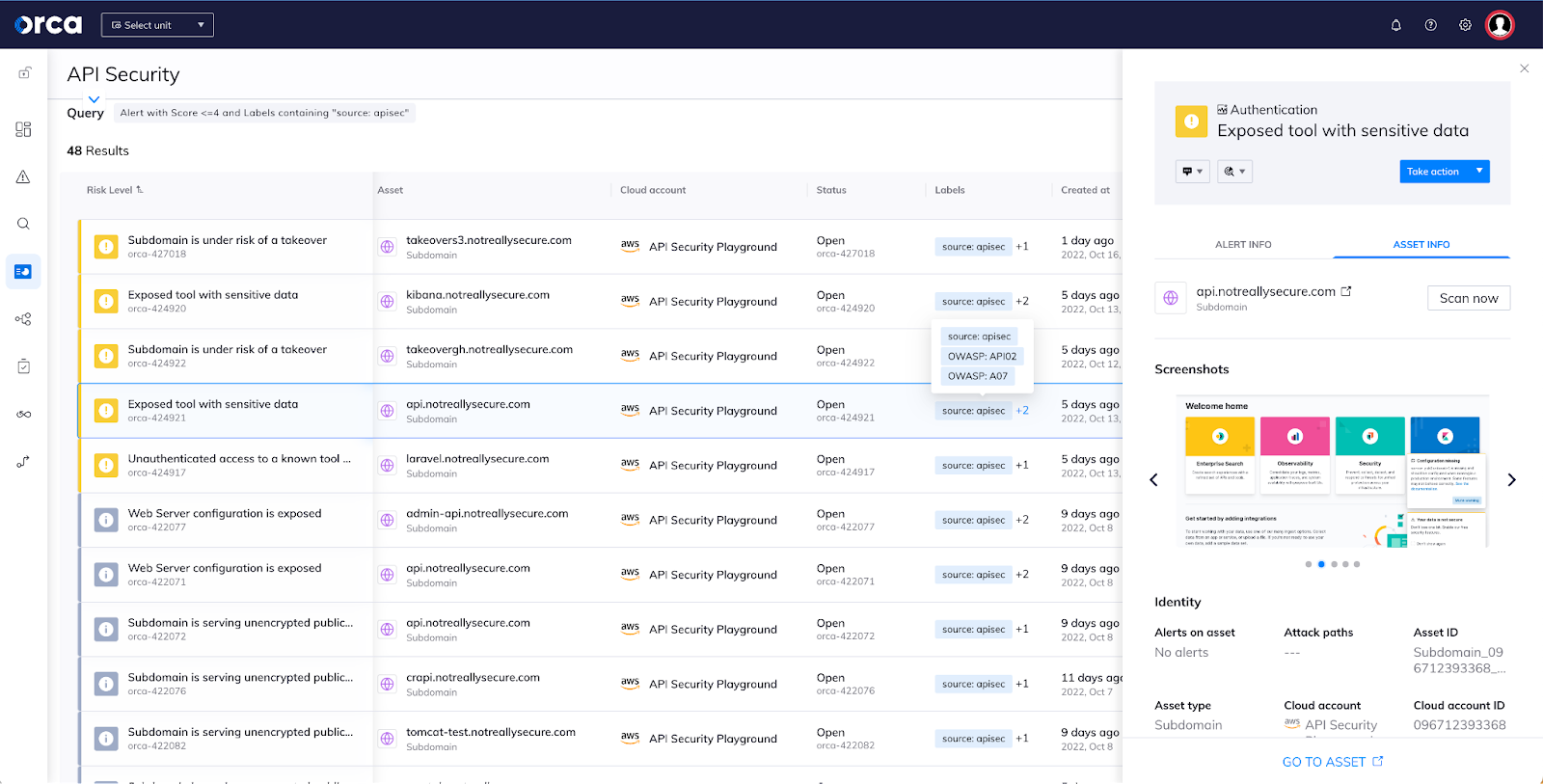
These alerts on misconfigurations and vulnerabilities help with compliance as well. Alerts linked to common compliance frameworks such as PCI-DSS help to aid governance and compliance teams to adhere to these frameworks and to stay ahead of audits.
3. API drift detection and management
Orca’s API Security capabilities include a summary of the newly added and removed applications, domains, subdomains, API paths, and API operations on those paths— in the last specified number of days.
But it goes beyond that. Based on specification data collected and analyzed in each API endpoint and related domains and subdomains, Orca generates a Swagger documentation view that can be used to easily compare intended API policy vs. current usage. This helps security teams communicate with their engineering and DevOps teams to ensure that both documentation is updated, as well as facilitate a further understanding of API changes and related risks.
Learn more about Orca’s API Security Capabilities
Interested in learning more about Orca’s API Security capabilities? Watch our recorded demo, or register for our upcoming webinar on November 16 at 11 am PST, “Securing APIs in Cloud Native Applications Best Practices.”
Ready to try it out for your own cloud environment? Sign up for a Free Risk Assessment to see how quickly and easily the Orca Cloud Security Platform can help you identify and address API risks.






