WHY A NEW APPROACH IS NEEDED
Agent-Based Solutions Don’t Work in the Cloud
Agents require tedious integration with each workload, causing dangerous blind spots, high TCO, performance degradation, and limiting the ability of your already overworked IT and DevOps teams to move at cloud speed. Vendors that offer an ‘agentless’ option in addition to their agent-based solution, often have hidden limitations and increase complexity even more.
Partial deployment of agents causes serious blind spots. On average, we found that less than 50% of assets are covered by agent-based solutions.
Before risks can be detected, agent-based solutions require installation on each workload, which is simply not feasible given the ephemeral nature of the cloud.
If security does not integrate effortlessly with DevOps workflows, priority mismatches and confusion about team responsibilities will lead to frustration and remediation delays.
Running agents on workloads has a significant impact on asset performance and system resources, especially if assets need multiple agents installed for different point solutions.
HOW ORCA SIDESCANNING WORKS
Cloud Security Purpose-Built for the Cloud
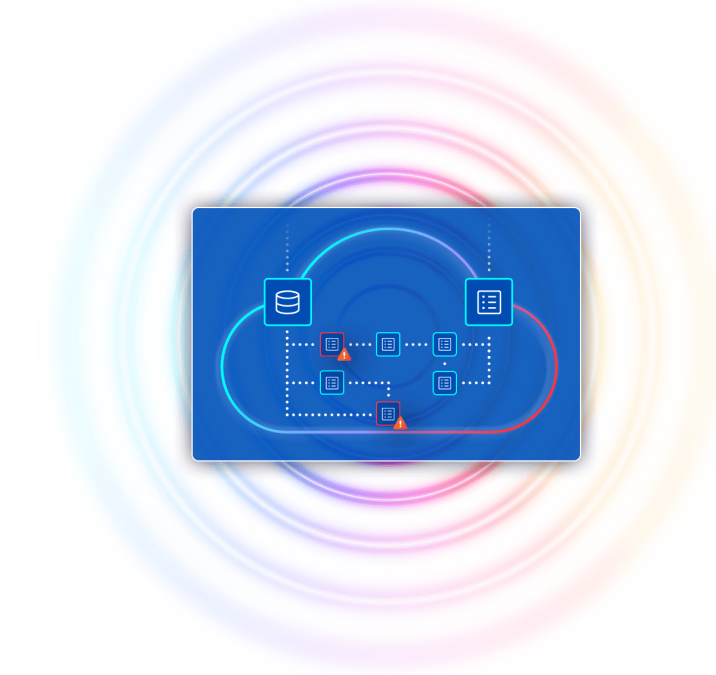
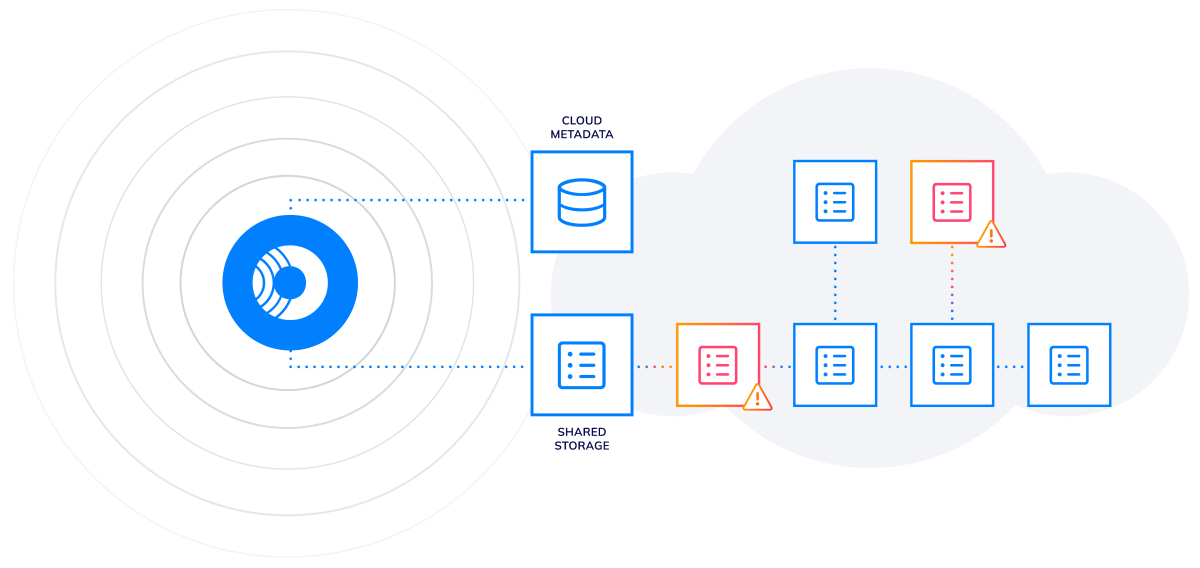
Orca’s SideScanning is a revolutionary new approach that addresses the shortcomings of agent-based solutions by collecting data from the workloads’ runtime block storage without requiring agents. Orca then reconstructs the workload’s file system – OS, applications, and data – in a virtual read-only view, and performs a full risk analysis with zero performance impact on the workloads themselves.
Fast deployment
The agentless-first Orca Cloud Security Platform is configured in minutes, and in under 24 hours delivers a complete risk profile of your entire cloud estate without sending a single packet over the network or running a single line of code in your environment.
100% continuous coverage
Because Orca does not rely on agent deployments, Orca covers all assets including VMs, containers, and serverless, as well as cloud infrastructure resources such as storage buckets, VPCs, and KMS keys – and automatically includes new assets when they are added.
Full-stack visibility
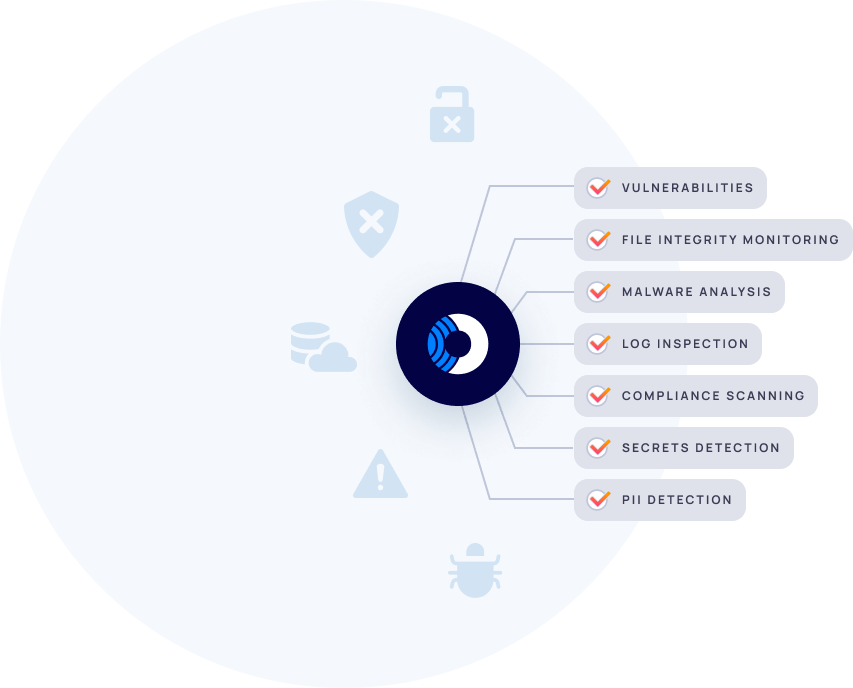
Orca detects risks across Linux and Windows hosts, containers, Kubernetes, and serverless functions to surface vulnerabilities, compliance issues, FIM, log inspection, and more — augmented with wider cloud context to deeply understand risk.
An ‘MRI’ for your cloud estate
SideScanning is a bit like a medical MRI scanner – instead of using needles and scalpels, the MRI machine diagnoses health issues through non-invasive scanning of organs and tissue. SideScanning is similar in that it scans all cloud assets and their interconnectivity, providing deep and wide visibility into the entire cloud estate, without affecting the assets in any way.
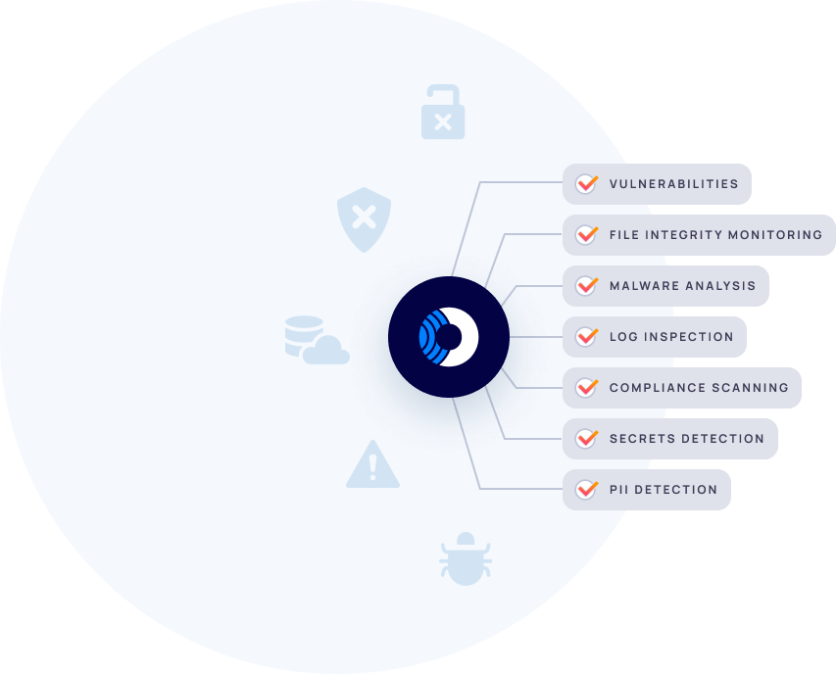
Capturing workload telemetry no other solution can
SideScanning covers all major workload types, including Linux and Windows VMs, containers and container images, and serverless functions. While most solutions only identify basic vulnerabilities, Orca provides detailed data on compliance issues, log inspection, file integrity monitoring, malware analysis, and more to offer telemetry that other solutions lack.