It’s been a busy year in cloud security. We’ve seen data breaches, tens of thousands of new vulnerabilities, and an ever-increasing complex environment with organizations deploying on multiple cloud platforms and cloud-native services.
The Orca Research Pod has been equally busy. We discovered seven major vulnerabilities on public cloud platforms which were subsequently fixed, continually analyzed the security of public cloud assets being scanned by the Orca platform, and observed attacker tactics and techniques in the wild.
Based on our research from this past year, we predict an increase of the following five cloud security threats in 2023:
1. Brute Force Attacks in the Cloud
It’s no secret that the internet is continuously being scanned by malicious actors. They can easily discover a public facing asset with an open port. Consequently, it’s only a matter of time until an attacker will try to hack into the asset with a brute force attempt or other available exploits. The reason for this exploit could be for information exposure or even just to deploy a cryptominer, which could provide the attacker with great financial gains, even if only deployed for a short period of time.
In the past year, we saw a 31% increase in the number of brute force attacks against organizations compared to 2021, with spikes corresponding to major geopolitical and socioeconomic events.
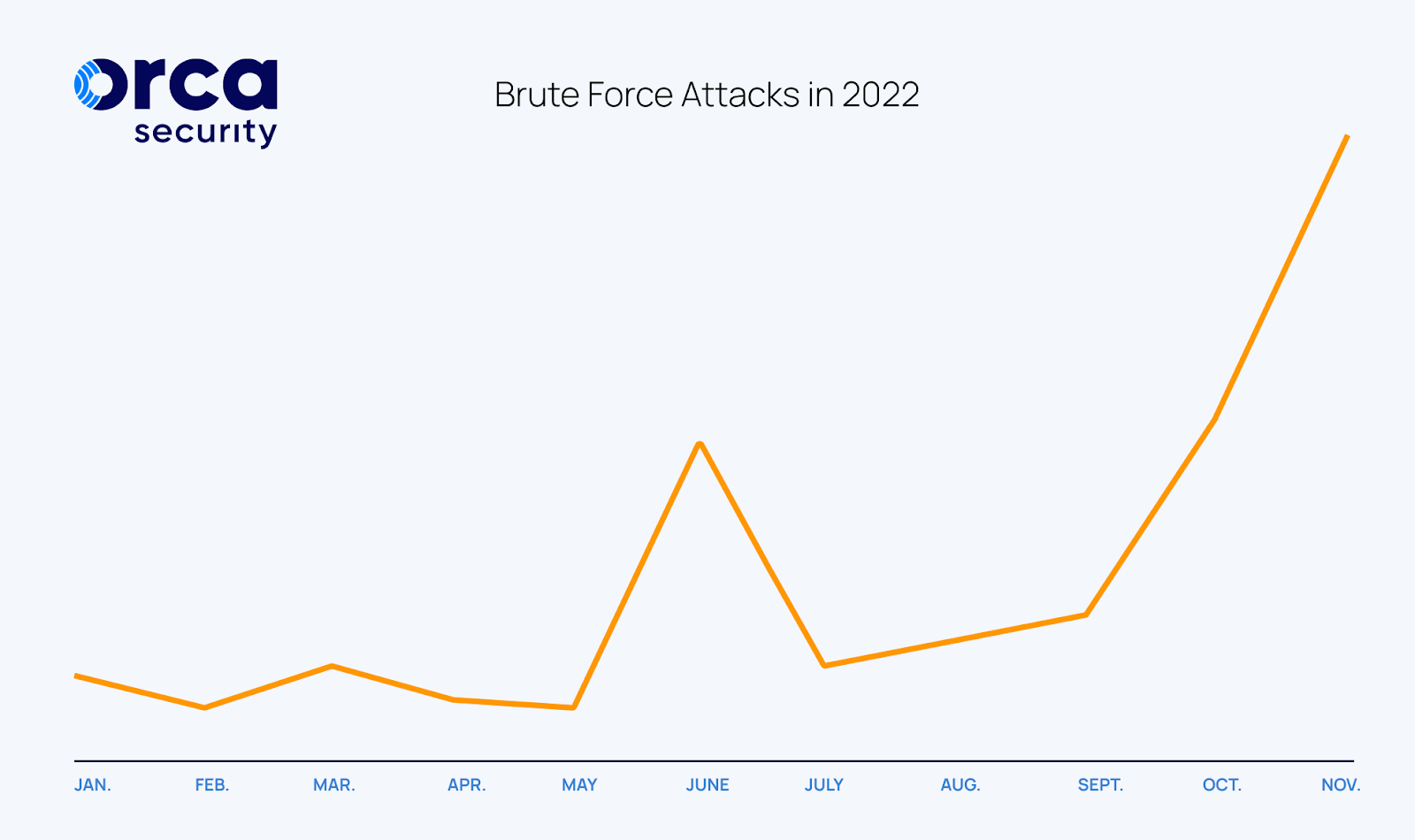
In the graph above you can see the number of brute force attacks detected by Orca in 2022. The first spike in the number of attacks, which was a 60% increase compared to the previous 6 weeks, is seen around the end of February, which coincides with the Russian invasion of Ukraine. The second one was in June, following the EU ban of Russian Oil, and the third and largest peak was in early November, around the same time of the U.S. midterm elections. We believe that these spikes are certainly no coincidence, and that we can expect similar activity in 2023, coinciding with geopolitical and global socioeconomic events. This means that organizations should be on heightened alert during major global events and on the lookout for anomalous events and behaviors in their cloud environments.
2. API Threats
With the increasing usage of applications that rely on computational communications, the number of APIs (Application Programming Interfaces) has grown exponentially. Yet, the awareness of how and when to secure APIs remains low and largely neglected.
As shown in our 2022 State of the Public Cloud Security report, a staggering 70% of the organizations had a Kubernetes API server that was publicly accessible, leaving API servers exposed to reconnaissance attempts and potential zero-day attacks.
Analyst firms, including Gartner, have been warning that we should expect API server attacks to increase in coming years, and we already saw some examples of this in 2022. In light of this, we expect that API Security and Application Security will be a top priority for organizations and CISOs in 2023.
3. Misconfigured and Shadow Data Stores
With the sheer growth of data volume, the majority of which is stored in the cloud (now 60% according to research by Statista), the data attack surface is dramatically increasing year over year. In the cloud, data is stored in databases, storage buckets, or blobs. During the past year we’ve seen severe breaches from these cloud services, almost exclusively caused by misconfigurations.
In our 2022 State of the Public Cloud Security report, we found that 72% of organizations have at least one bucket with public “read” permissions, and 36% of the organizations keep unencrypted secrets and personally identifiable information (PII) in these cloud services.

Shadow data is another growing challenge, since it is easy for developers to copy data to other locations in the cloud without even realizing that it may contain sensitive data or that the controls attached to it could be lost when the data is moved. Often, IT and security teams do not have a complete handle on all their data stores in the cloud, which is basically a disaster waiting to happen.
4. CI/CD and Supply Chain attacks
CI/CD environments are similarly attractive targets for attackers. From dependency confusion in npm and python packages, to vulnerable and dangling maintainters, all are new ways to attack organizations. Earlier this year, the first protestware deployed these types of tactics, showing us how easily this could be accomplished.
In addition, cybercriminals can exploit these packages in the same way for crypto mining purposes. We know that cybercrime increases during economic downturns and that criminals love mining in the cloud (did somebody say computational power for free?). With the economy slowing down this upcoming year, and the constant rise in cybercrime lucrativeness, we can confidently predict an increase in CI/CD and supply chain attacks for 2023.
5. Critical vulnerabilities
Since 2017, there has been a constant increase of known CVEs, based on the National Vulnerability Database (NVD). In the upcoming year we will keep seeing more and more vulnerabilities, which means that organizations will face even more patching work. Therefore, prioritization and the understanding of which vulnerability should be patched first will be even more important.
In addition to vulnerabilities on the application side, we will also continue to see vulnerabilities being discovered in cloud provider infrastructures. In fact, the Orca Research Pod has discovered 7 major vulnerabilities in public platforms this year alone, and has worked with cloud vendors to assist them in getting them fixed.
The Best Policy: Be Prepared
However much we try to predict what will happen in 2023, unfortunately there is no crystal ball. The best policy for organizations is always to be as prepared as possible: know where your most valuable cloud assets are, which weaknesses could endanger them, and then address these as fast as possible.
Understand that no matter how much you patch and secure configurations, there is still a possibility that an attacker could gain access to your environment. However, by reducing the opportunity of lateral movement and ensuring your most valuable assets are robustly protected, the potential attack damage can still be kept to a minimum.
We’d love to help you assess the security of your cloud environments on AWS, Azure, Google Cloud, and Alibaba Cloud, so you can understand how prepared you are. Take our free, no obligation risk assessment and let Orca Security scan your entire environment with only a quick 10-minute setup needed. You will be able to use the platform for 30 days and receive a detailed summary of your cloud security risks explained by an Orca expert.
Let us help you face the new year in the cloud with confidence!






