Due to the common use of default policies, AWS cloud identities tend to have overly permissive policies which in most cases are unnecessary and significantly weaken an organization’s cloud security posture. Therefore, it is always recommended to follow the least-privilege principle, which entails limiting permissions to those that are strictly needed by the user or application to perform a task. On AWS this can be accomplished by defining policies that specify which actions an identity (user, group, or role) can take on specific resources and under specific conditions.
However, managing hundreds of Identity and Access Management (IAM) policies is time consuming and prone to misconfigurations. This is where Cloud Infrastructure Entitlement Management (CIEM) comes in. Gartner defines CIEM as ‘managing cloud access risk via administration-time controls for the governance of entitlements in hybrid and multi-cloud IaaS’. As a Cloud-Native Application Protection Platform (CNAPP), the Orca Cloud Security Platform incorporates CIEM to help organizations protect their cloud environments from identity threats.
Orca’s New IAM Remediation
We are pleased to announce that in addition to alerting security teams when overly permissive identities are detected, Orca is introducing a new CIEM feature called IAM Remediation. Orca’s IAM Remediation leverages Artificial Intelligence (AI) to perform prescriptive analytics and answer the question “What are the least policy changes that need to be made to achieve the maximum improvement in IAM posture?”. In addition, Orca provides detailed information on suggested policy changes as well as guided remediation.
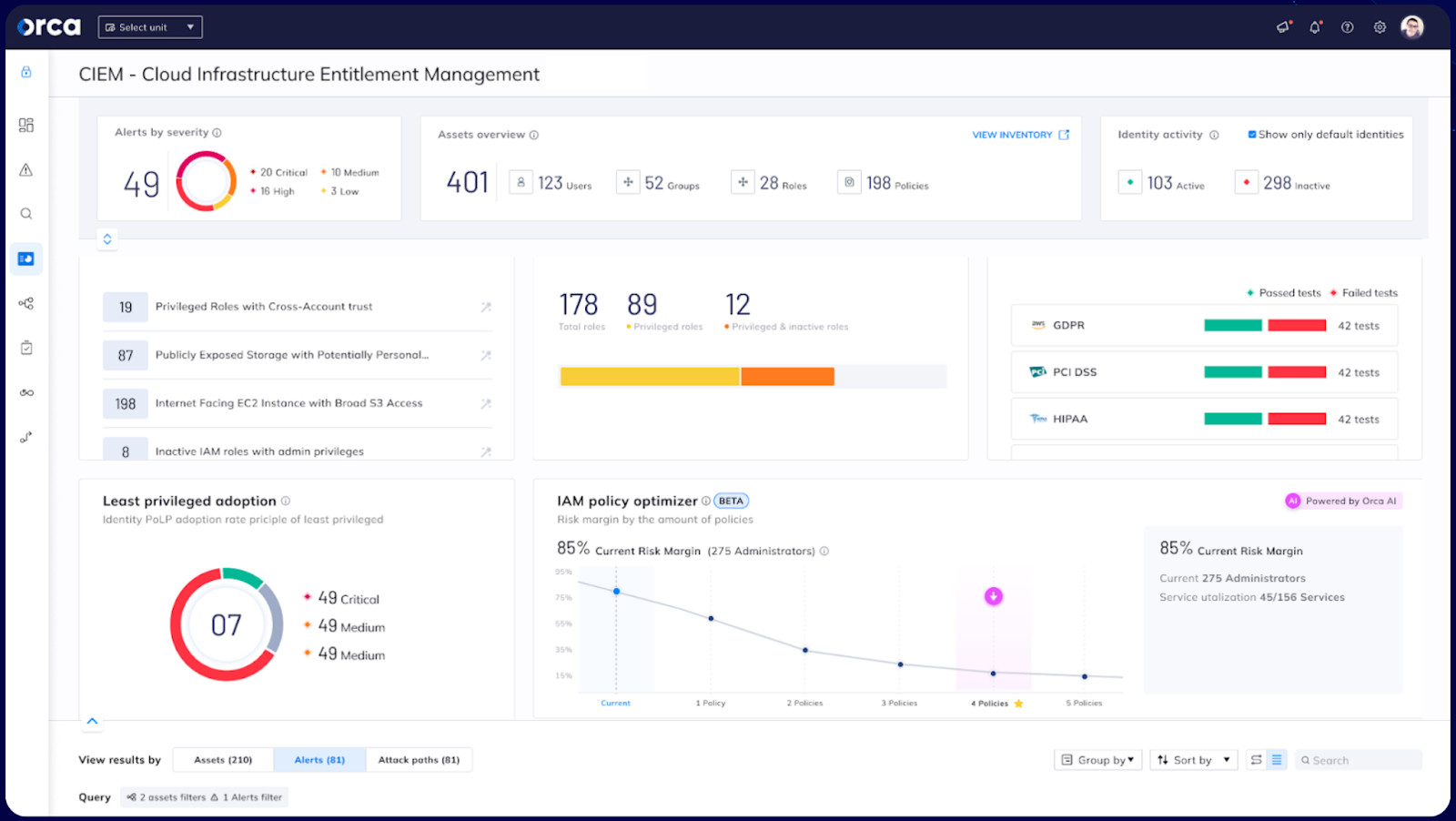
Orca Security CIEM Dashboard
AWS IAM Management
Let’s first start by looking at IAM Management in AWS. By configuring least-privilege policies for your IAM identities (groups, users, and roles), you can significantly reduce the risk of unauthorized access and lateral movement in your AWS environment. Although it saves time to use AWS default policies that grant permissions for common use cases, it is important to reduce these default permissions depending on your specific requirements. AWS managed policies have been created for general scenarios and do not always adhere to the principle of least privilege. They should be considered as ‘sample’ policies that need to be customized and tightened for actual use.
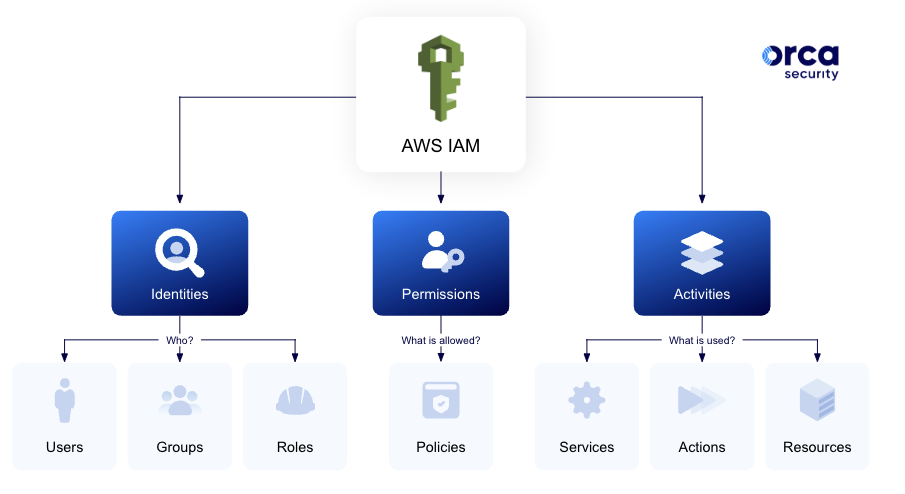
IAM in an Ideal World
To achieve the lowest risk margin and create a true least-privileged environment, organizations would have to assign a designated policy for each separate identity. However, imagine you are responsible for managing an AWS account with 2,000 users and 3,000 roles. If you were to strictly apply the principle of least privilege (PoLP), this would require you to create, manage and maintain 5,000 policies. This is simply not feasible for most organizations and many don’t even try to attempt this.
However, what if it was possible to apply the well known 80/20 rule to IAM? The principle that 80% of consequences (output) come from 20% of the causes (input), also called the ‘Pareto Principle’ after the economist Vilfredo Pareto. This is exactly what Orca’s IAM Remediation does: help organizations find the most desirable balance between output (risk reduction) and input (configuration and maintenance).
How IAM Remediation Optimizes AWS Identities and Permissions
By comparing existing IAM policies to actual policy usage from the previous 90 days Orca’s IAM Remediation recommends optimal policy configurations that provide the largest security improvements with the least amount of effort.
For instance, by analyzing identity behaviors, users that behave in the same way can be grouped together and assigned the same corresponding policy. In contrast, if users within the same groups are not using the same services, IAM Remediation will recommend splitting users and roles into smaller groups with a tighter corresponding policy.
For each policy change, Orca will calculate the percentage in risk reduction, allowing it to recommend those changes that achieve the highest risk reduction. In this way, Orca can ensure that a high level of IAM hygiene is maintained without overburdening security teams.
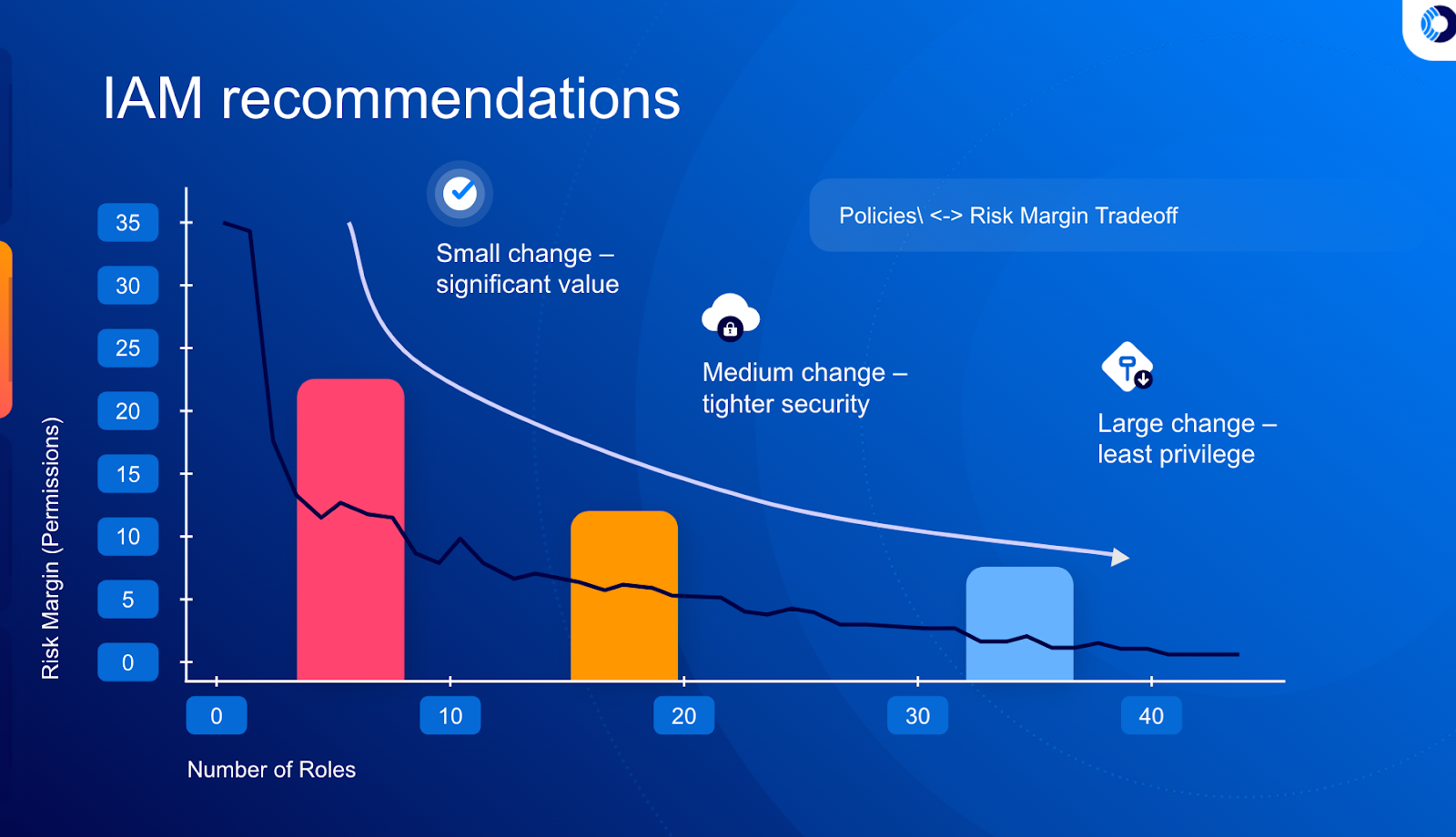
Orca calculates the tradeoff between policy changes and reduced risk margin
Orca’s IAM Remediation is found in the CIEM dashboard and displays the current IAM risk margin. For example, in the screenshot below it lists 85% as the risk margin, which is high. To find out how to decrease the risk margin, Orca users can click on ‘View Remediation Plan’.
The IAM Remediation dialog will be shown with suggested policy adjustments. On the right, the new plan details will be shown, including the new risk margin, number of policies to be created and the service utilization.
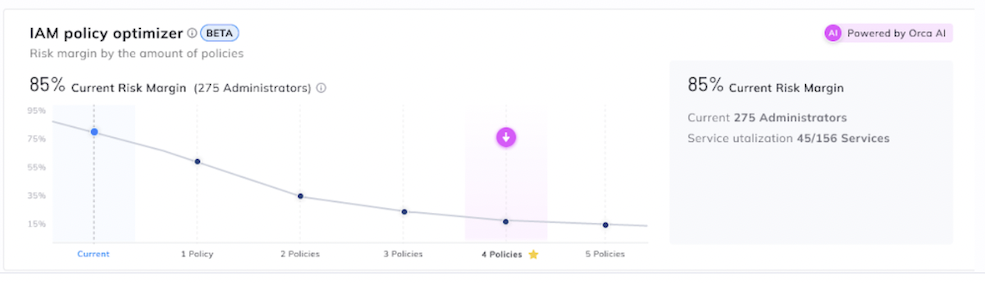
Orca IAM Remediation Dialog
The user will be able to slide the highlighted point on the graph to select the desired tradeoff between maintaining more IAM policies and decreasing the risk margin.
For instance, in the example above, with the newly selected IAM plan, 3 new policies will be created, reducing the risk margin by 95% . These improvements are achieved by generating just four new policies. To see the full details of the new policies to be created and download IAM remediation steps, click on ‘Export Policies’.
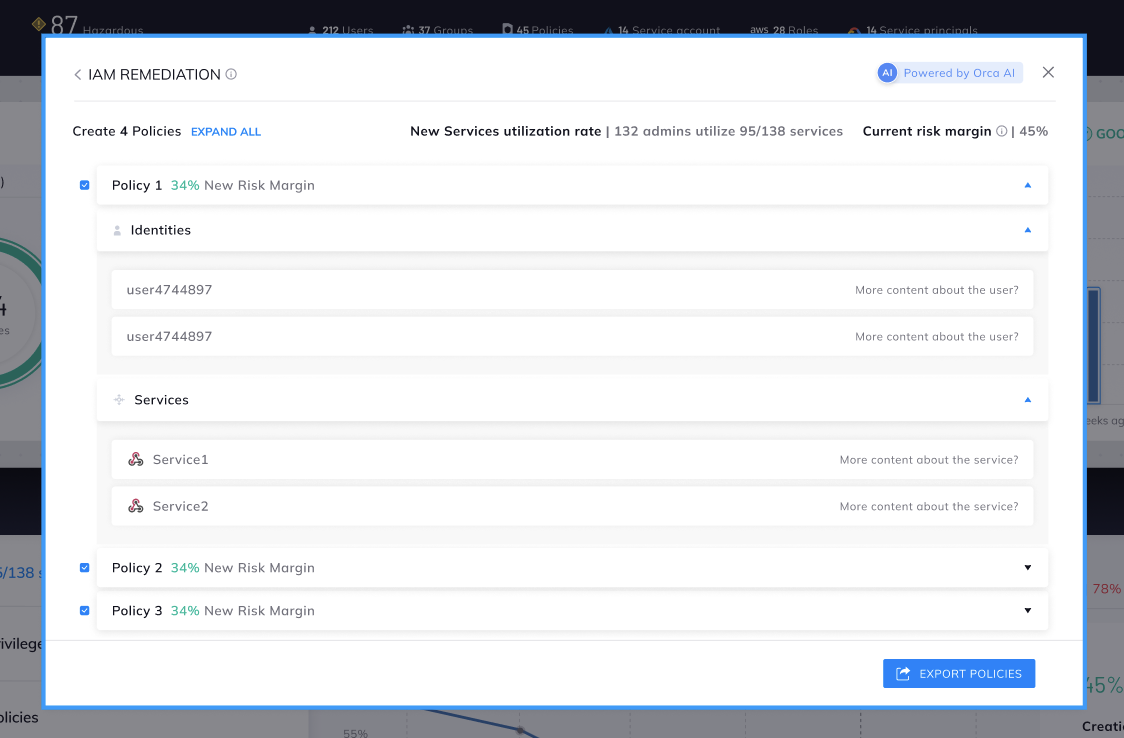
Details of suggested policy changes and the identity and service changes
In this example, the recommendation is to split administrators into different groups with their own policies. The diagram shows which identities should be assigned to each of the new groups, as well as the groups’ authorized services. The new risk margin for each policy is also listed. If you are happy with the recommendations, you can download the selected IAM plan as a file, convert it into AWS IAM policies, and deploy it into your cloud account.
Orca’s IAM Remediation is a cost-effective and practical way for organizations to achieve significant improvements in their cloud security postures while requiring only minimal effort.
Learn More About Orca’s New CIEM feature – IAM Remediation
Would you like to learn more about Orca’s IAM Remediation and find out what your current IAM risk margin is? Watch a recorded demo, or take our free, no obligation 30-day trial to try it out for yourself. Since no agents need to be installed, the Orca platform can be deployed in under 30 mins, and immediately start scanning your IAM policies as well as other risks across your cloud environments.





