The Challenge
Partial Coverage, Compliance Gaps, and Disparate Solutions
Multi-cloud compliance calls for complete, continuous coverage of your entire cloud estate. However, relying on tools that require agents and approach compliance on a per-asset basis results in gaps in coverage, increased cybersecurity risk, organizational friction, and failed audits. In addition, using multiple point solutions or poorly integrated offerings only increases manual work correlating data and aligning policies.
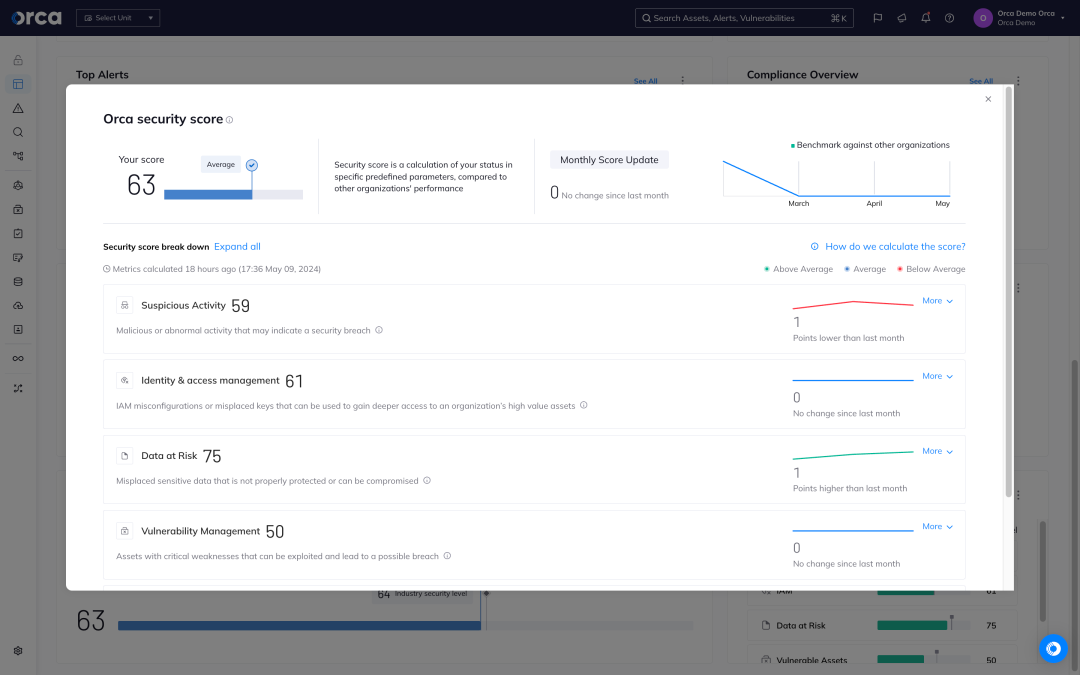
Compliance is not achievable without 100% coverage of your entire cloud estate. On average, less than 50% of assets are covered by agent-based solutions.
Most CSP native security tools are specific to each platform, resulting in the need to maintain and align policies across disparate solutions.
Although dedicated compliance solutions exist, they often require manual processes, lack remediation techniques, and do not provide the ability to create custom frameworks.
Our Approach
Single Platform for Multi-Cloud Security and Compliance
Unlike other solutions, the agentless-first Orca Platform deploys in minutes, and ensures 100% continuous coverage of your entire cloud estate, automatically covering any newly added assets. Orca performs out-of-the-box and customizable compliance checks across cloud workloads, configurations, identities, and data, ensuring that security and compliance policies in all cloud provider platforms are aligned. Orca further simplifies the task of maintaining continuous compliance by effectively prioritizing issues, providing automated and guided remediation, and integrating with your existing tools and workflows.
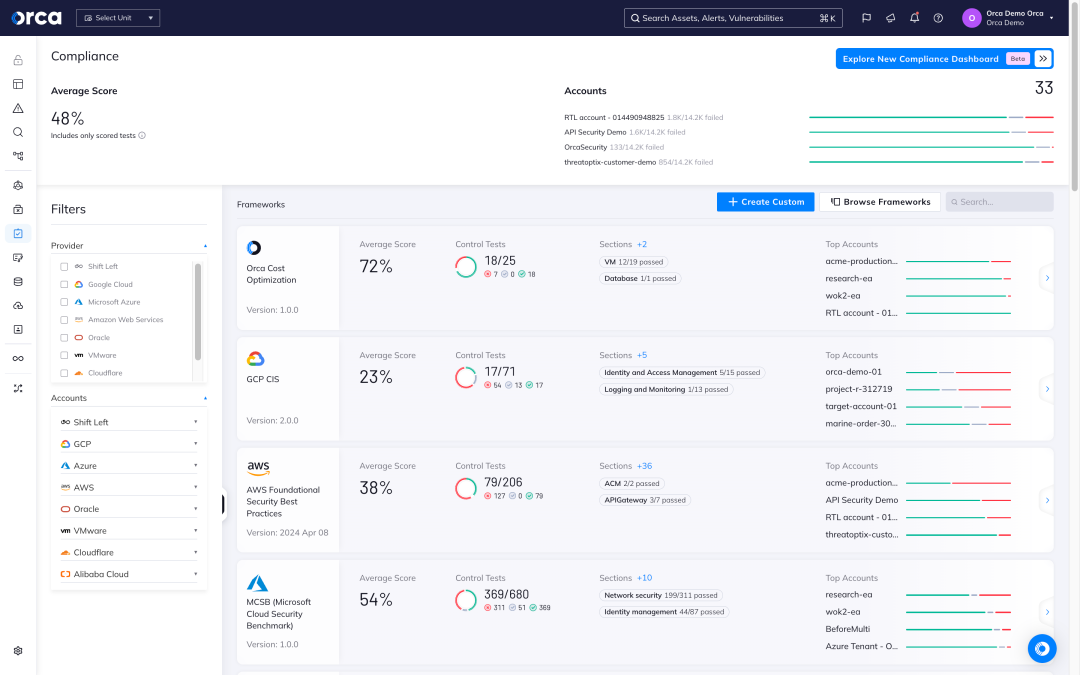
Centralize cloud compliance across AWS, Azure, Google Cloud, Kubernetes, Alibaba Cloud, and Oracle Cloud with Orca’s comprehensive management dashboard.
Leverage continuous compliance checks across your entire cloud, including storage buckets, network configurations, identities, data, workloads and applications, APIs, and more.
Easily identify and remediate issues from a single automated solution to reduce manual audits and compliance management.
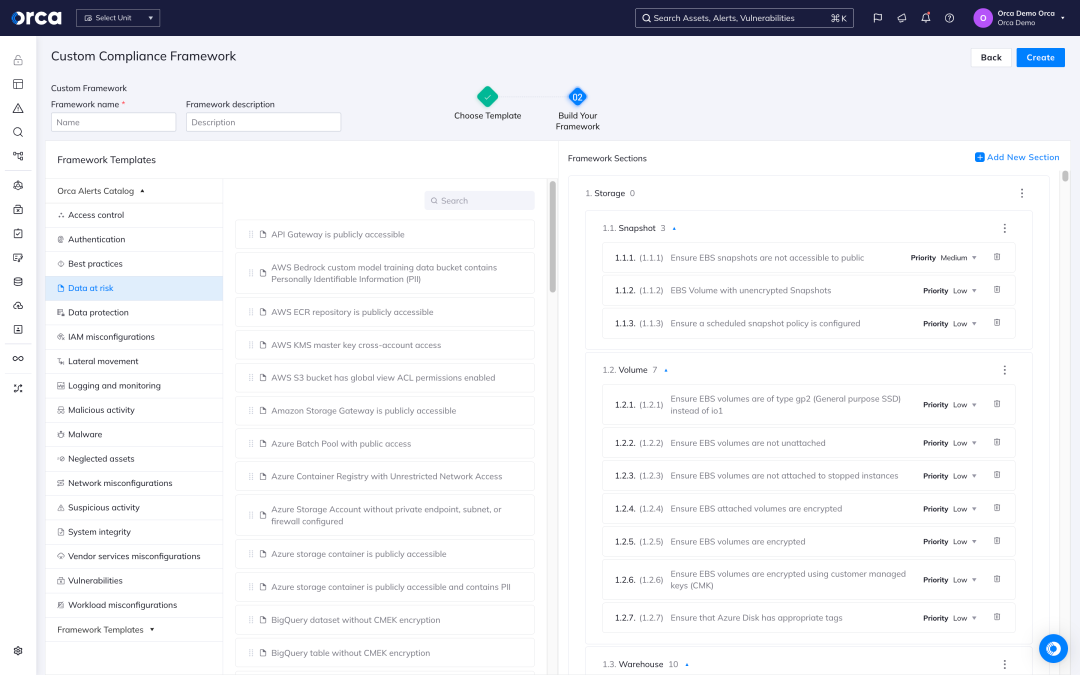
Easily tailor frameworks to your needs
Recognizing that one size does not always fit all, Orca also offers users the ability to configure custom compliance frameworks.
- Use existing templates or build new frameworks from scratch.
- Make tweaks to existing frameworks, combine rules from two or more frameworks, or set up your own rules and controls.
- Customize notification schedule, prioritization of controls, and other settings.
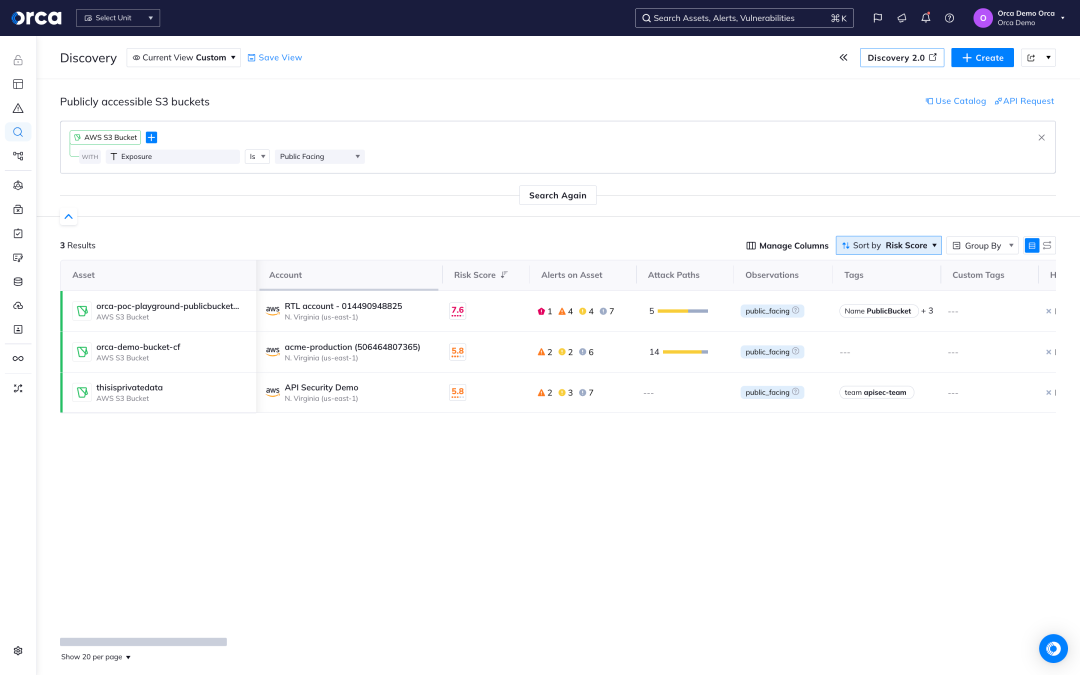
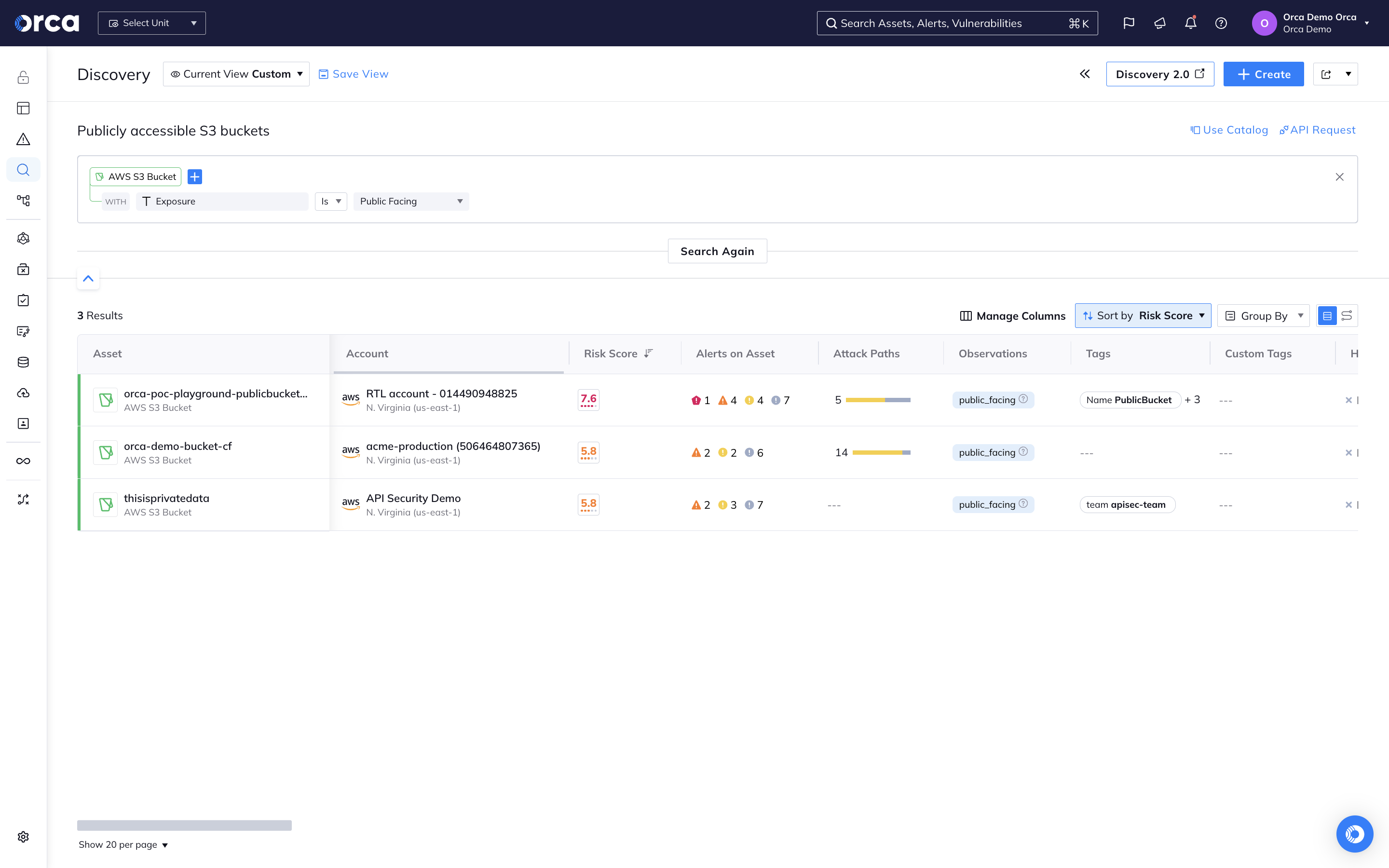
Find and protect sensitive data
Orca scans your entire cloud estate to discover sensitive data that is not properly protected and causes a compliance gap.
- Understand where sensitive data resides in your cloud, including PII stored in managed, self-hosted, and shadow data stores and files.
- Meet key data privacy mandates such as PCI-DSS, GDPR, HIPAA, SOC 2, and CCPA.
- Leverage Orca risk prioritization to ensure that issues endangering your sensitive data and other business critical assets are addressed first.
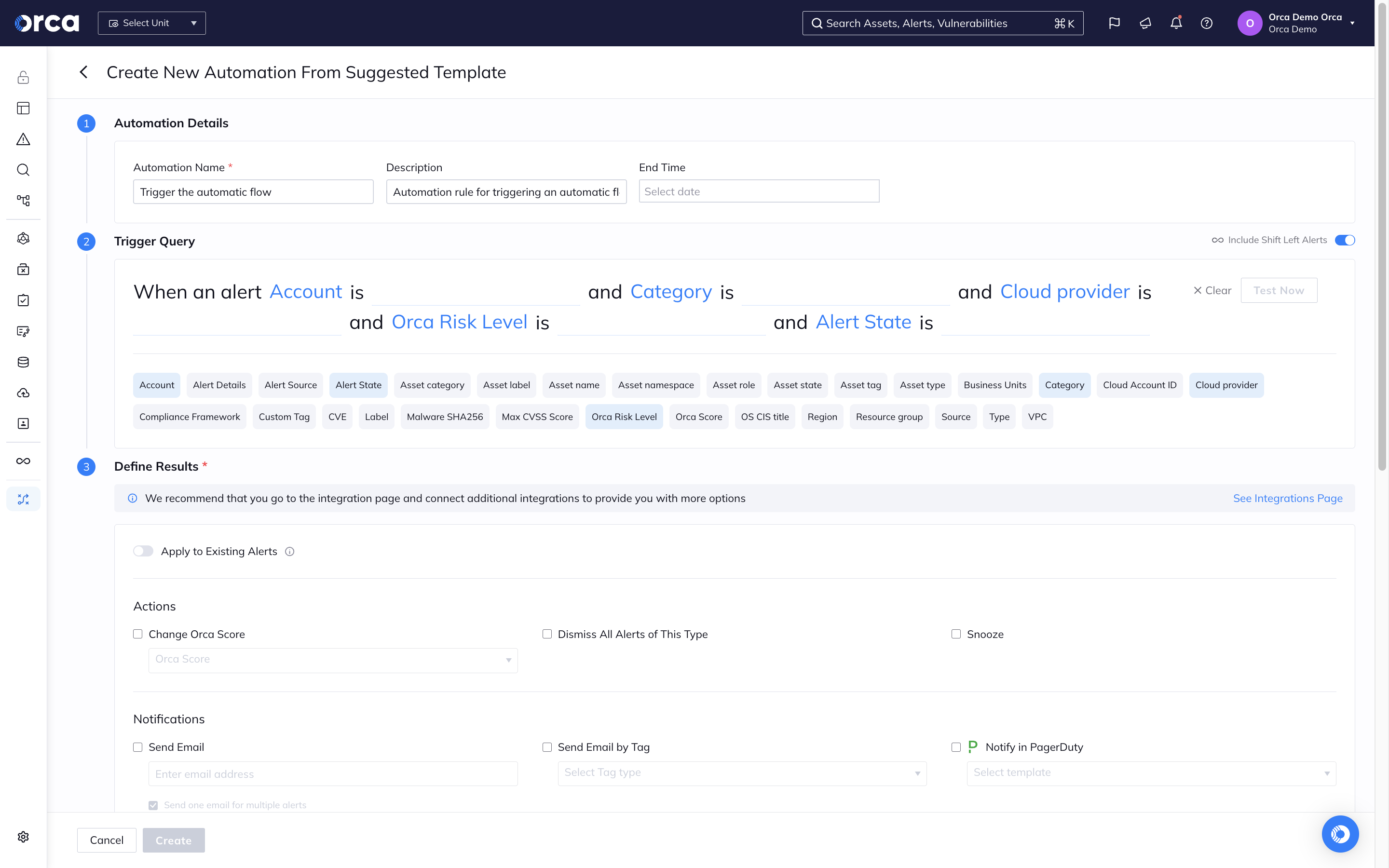
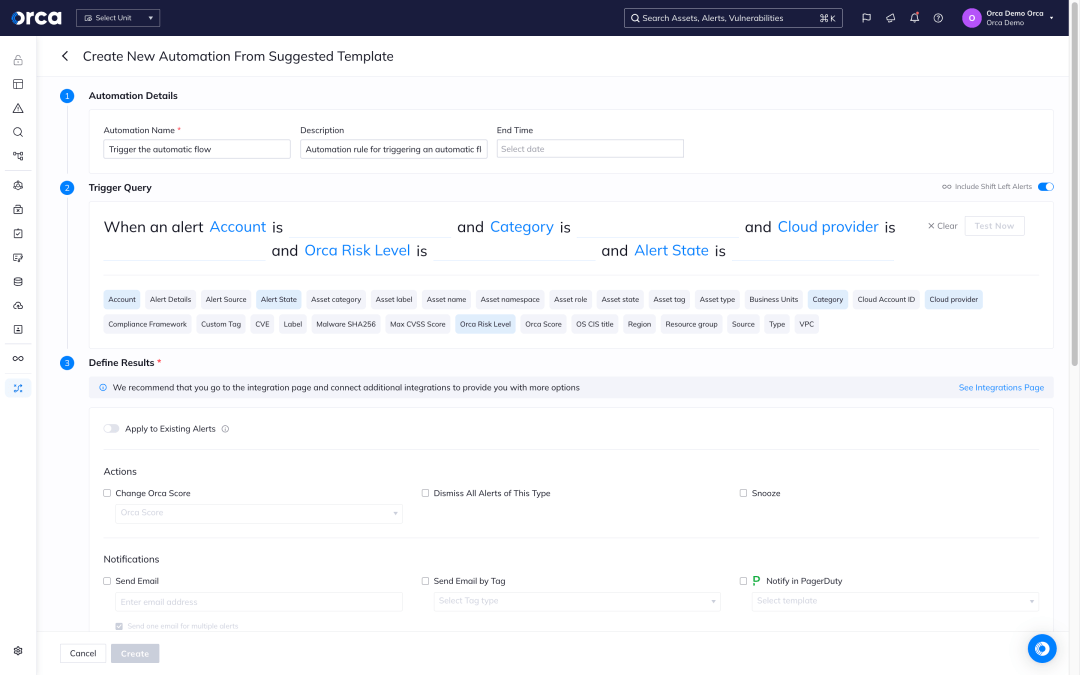
Automate remediation workflows
Using Orca’s many technical integrations, organizations can integrate compliance alerts into their existing remediation workflows, ensuring that issues are automatically assigned and processed by the right teams.
- Automatically forward compliance alerts to email, PagerDuty, OpsGenie, or Slack, or assign issues through ticketing systems, such as Jira or ServiceNow.
- Address risks quickly with automated and AI-powered guided remediation to avoid compliance violations.
- Rich contextual information is provided with alerts to allow remediation teams to operate independently and efficiently.
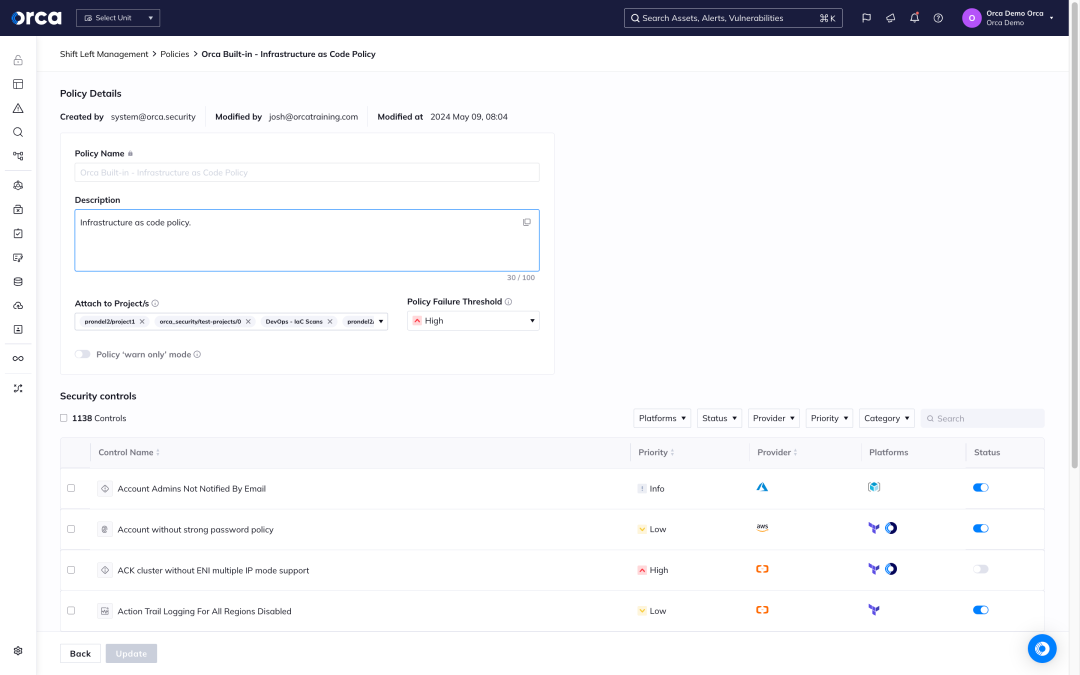
Avoid releasing non-compliant applications
Orca provides compliance checks across the full software development lifecycle (SDLC), including IaC template, container image, and container registry scanning, so teams can:
- Detect risks early in the development life cycle and address them before they are released into production.
- Predict whether code changes could create dangerous attack paths when combined with existing risks in the production environment.
- Correlate production risks back to the pre-deployment image or IaC template that was originally used to create the production instance.
Simplify compliance reporting
Orca generates comprehensive reports to allow teams to easily understand and communicate which controls need to be addressed to improve compliance posture and report on their progress.
- Report on compliance status to both internal stakeholders and auditors—with extensive customization capabilities.
- Share executive summaries to provide evidence of compliance progress and trends over time.
- Generate ad hoc or scheduled reports in CSV, JSON, and PDF formats and automatically share through email, Slack and other channels.