If your organization processes credit card payments, you are probably familiar with PCI DSS, a compliance mandate that was initially established in 2004. However, with the increasing adoption of cloud computing, more organizations are storing and processing credit card information in the cloud. This presents new compliance challenges since securing cloud environments requires a totally different approach than on-premise environments.
In this blog post, we will discuss the five best practices for ensuring PCI DSS compliance in the cloud. We will also discuss how Orca Security’s compliance capabilities help organizations meet PCI DSS requirements.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards that organizations processing credit cards must meet in order to protect cardholder data and prevent fraud. PCI DSS includes detailed technical prerequisites to safeguard and fortify payment card information throughout its processing, handling, storage, and transmission. Irrespective of size, all businesses involved in payment card data must adhere to these requirements and maintain PCI compliance, and failure to comply can result in hefty fines, legal penalties, and reputational damage.
PCI DSS Compliance Best Practices
Here are five important best practices that organizations should follow to ensure PCI DSS compliance in their cloud environments:
1. Choose a PCI DSS compliant cloud provider
The first best practice for PCI DSS compliance in the cloud is to choose a Cloud Service Provider (CSP) that is PCI DSS compliant. The CSP should provide a secure infrastructure with secure physical access controls, network security, data encryption, and security monitoring capabilities. Many CSPs will provide third-party audit reports to certify their products for PCI DSS. For example, here are some links that discuss PCI DSS compliance for popular cloud platforms: AWS compliance, Azure compliance, Google Cloud compliance, Alibaba cloud compliance, and Oracle Cloud compliance.
However, it’s important to note that this is only the start, and that organizations are still responsible for ensuring that the cloud assets and applications they run in their cloud are PCI DSS compliant.
2. Implement secure authentication and access controls
The second best practice is to implement strong access controls. Access controls are essential for ensuring that only authorized users can access cardholder data in the cloud. This includes strong authentication mechanisms such as multi-factor authentication (MFA), strong passwords, and password rotation policies.
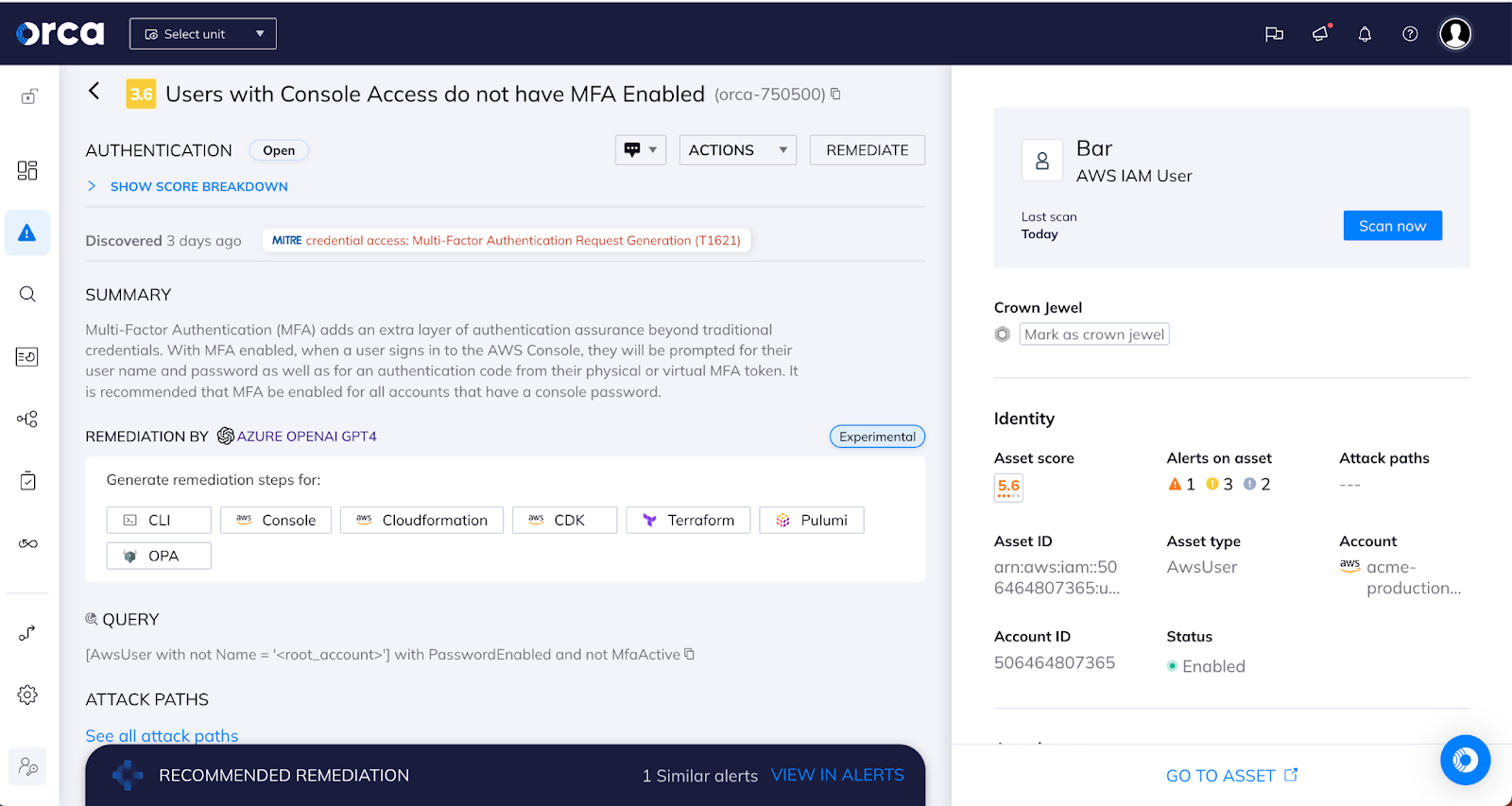
In addition to authentication mechanisms, organizations must also implement role-based access controls (RBAC) that limit access to cardholder data based on job responsibilities. RBAC ensures that employees only have access to the data necessary to perform their job functions. Access controls must also be reviewed regularly to ensure that access rights are up-to-date and aligned with organizational requirements.
3. Monitor the cloud environment for security threats
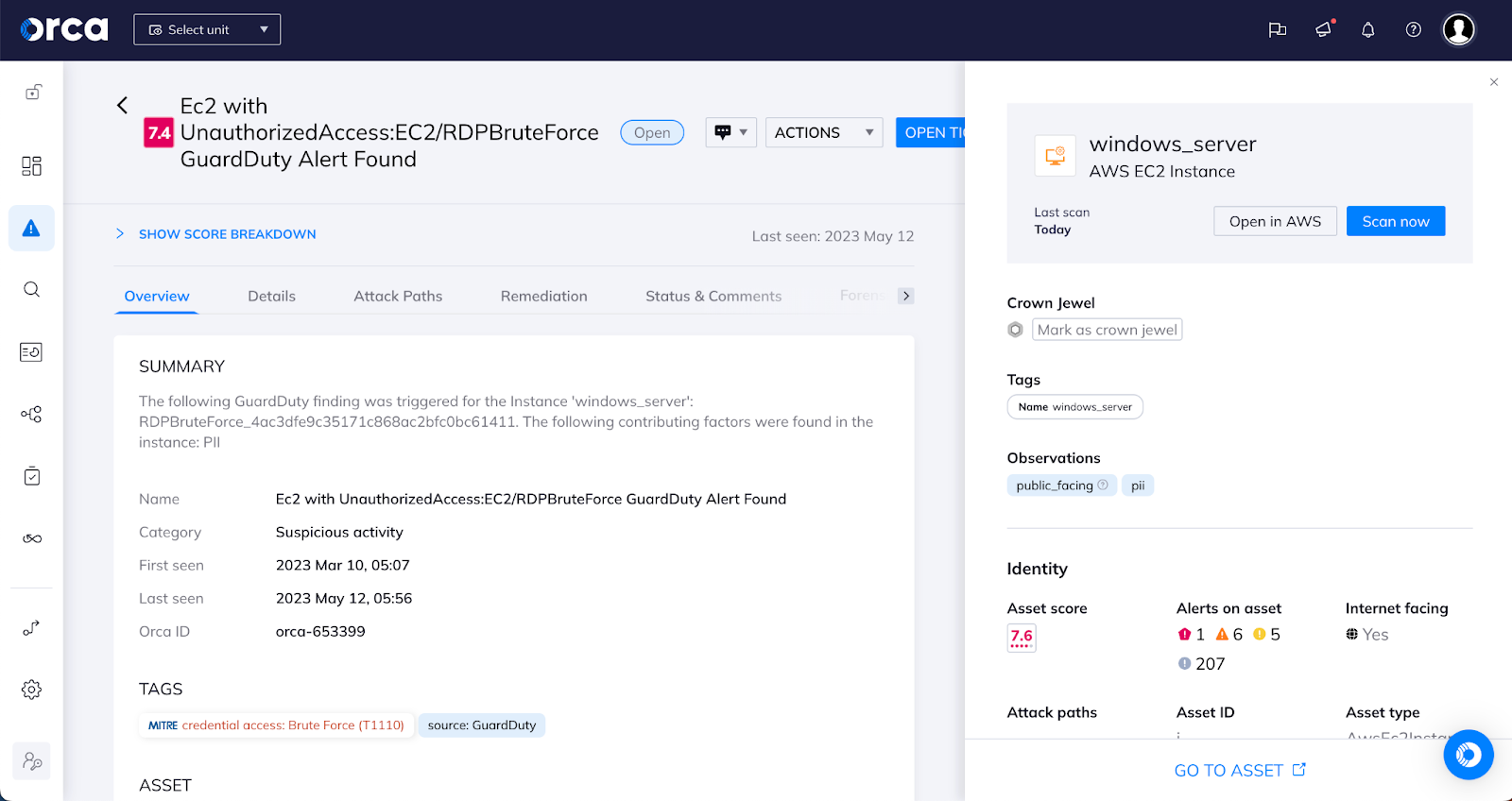
Next on the list is to monitor the cloud environment for security threats such as malware, hacking attempts, and unauthorized access attempts. This can be achieved by implementing security information and event management (SIEM) tools that provide real-time monitoring and analysis of security events.
Additionally, organizations must implement intrusion detection and prevention systems (IDPS) that detect and prevent attacks on the cloud environment. IDPS systems can detect and prevent attacks such as SQL injection, cross-site scripting (XSS), and distributed denial of service (DDoS) attacks.
Specifically focused on cloud attacks, Cloud Detection & Response solutions detect security incidents through continuous ingestion and analysis of cloud provider logs and threat intelligence feeds. When combining that data with the wider context of the cloud environment, false positives can be avoided and security practitioners have insight into valuable information to quickly facilitate the right response.
4. Encrypt all sensitive data
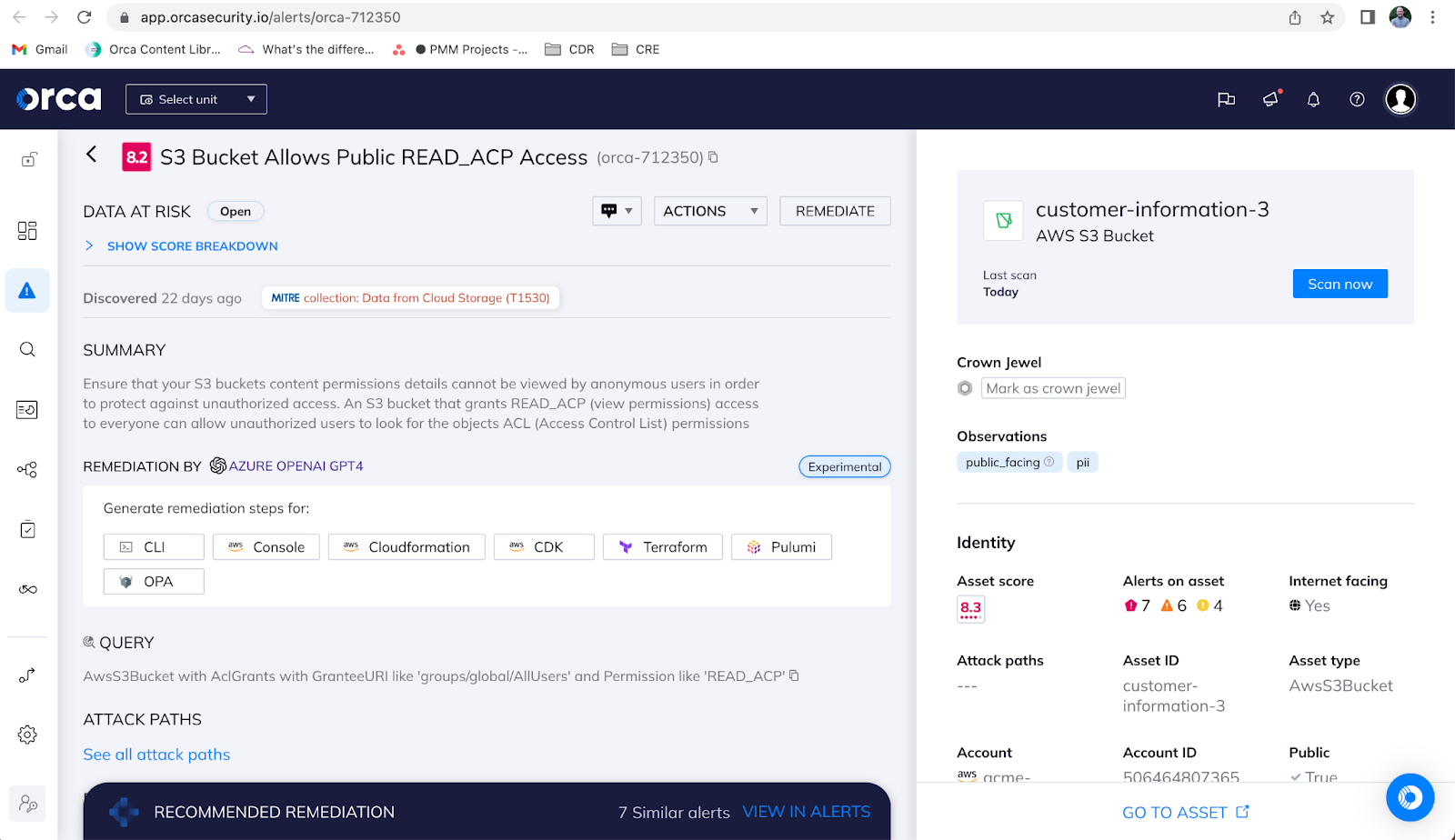
The fourth best practice is to encrypt cardholder data and implement strong encryption mechanisms such as Advanced Encryption Standard (AES) with a key length of 256 bits. Encryption is essential for protecting cardholder data from unauthorized access and theft. Organizations must ensure that all cardholder data is encrypted in the cloud both in transit and at rest. This includes data that is transmitted between the customer and the CSP and data that is stored in the cloud environment.
Additionally, organizations must ensure that encryption keys are managed securely and that they are rotated regularly to prevent unauthorized access.
5. Maintain compliance through regular audits and assessments
Finally, to maintain PCI DSS compliance in the cloud, it is essential to conduct regular audits and risk assessments, including vulnerability scanning. These assessments will help you identify any weaknesses in your system that could be exploited by attackers and enable you to take steps to correct them. By conducting regular assessments, you can ensure that your cloud infrastructure remains secure and compliant with PCI DSS.
A Proactive Approach to PCI DSS Compliance
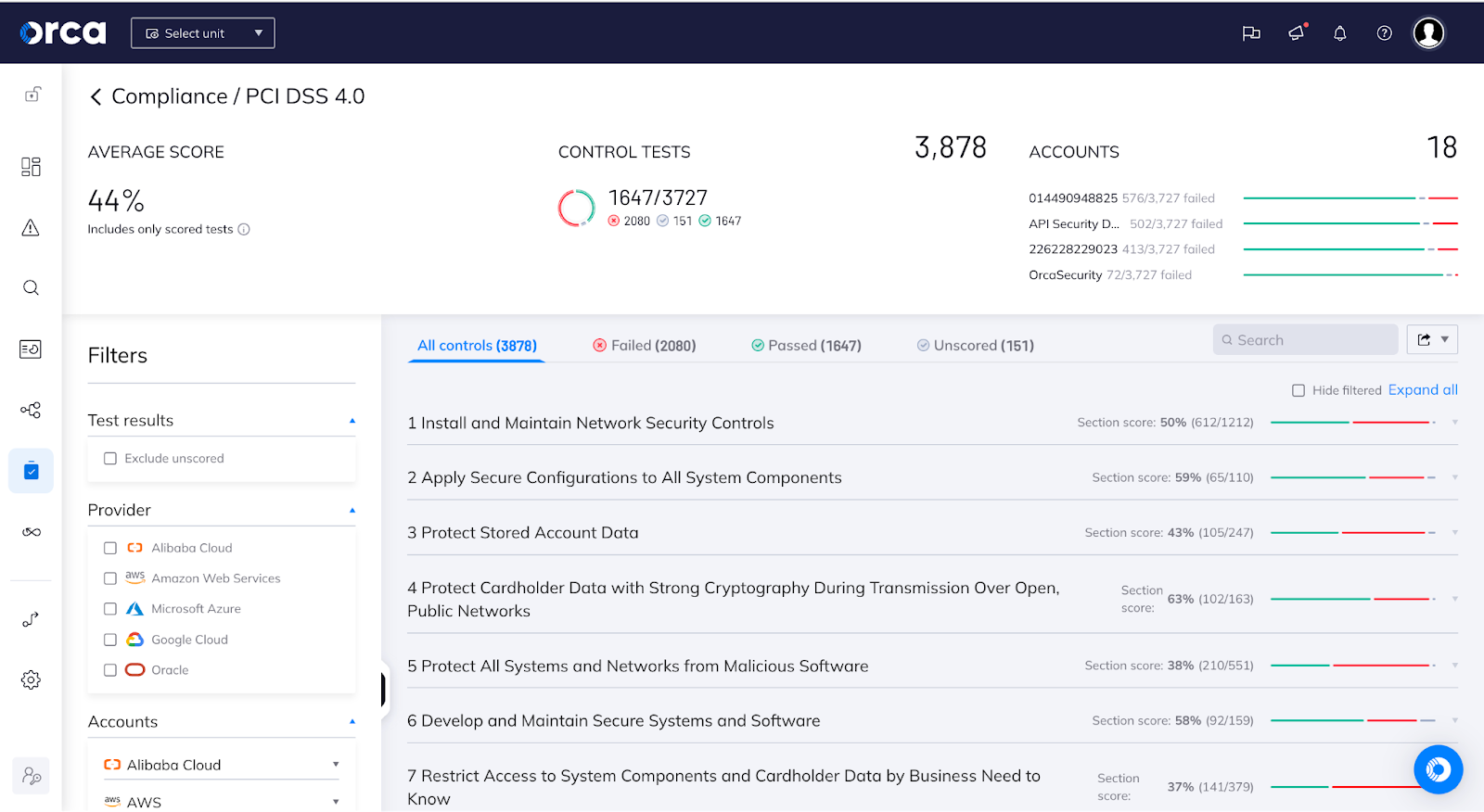
Achieving PCI DSS compliance can be a complex and time-consuming task. However, a central cloud security and compliance platform can relieve much of this pain. GRSee Consulting, an independent security and risk management consulting firm and approved Qualified Security Assessor (QSA), recently completed a report detailing how the Orca Cloud Security Platform enables organizations to meet PCI DSS compliance requirements in the cloud.
The report provides verification that Orca ensures compliance with the following PCI DSS controls in the cloud:
- Build and Maintain a Secure Network
- Install and Maintain Network Security Controls
- Apply Secure Configurations to All System Components
- Protect Cardholder Data
- Protect Stored Account Data
- Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
- Maintain a Vulnerability Management Program
- Protect All Systems and Networks from Malicious Software
- Develop and Maintain Secure Systems and Software
- Strong Access Control Measures
- Restrict Access to Cardholder data by Business Need-to-Know
- Identify Users and Authenticate Access to System Components
- Regularly Monitor and Test Networks
- Log and Monitor All Access to System Components and Cardholder Data
- Test the Security of Systems and Networks Regularly
Connecting Security and Compliance to Minimize Cloud Risk
Orca not only streamlines the PCI DSS compliance process, but also provides the following numerous benefits:
- Centralized Multi-Cloud Compliance: Rather than relying on separate tools from different cloud service providers, Orca’s multi-cloud compliance platform offers a unified view of PCI DSS compliance across the entire cloud estate.
- Enhanced Asset Visibility: Unlike traditional approaches that require agents to be installed on every cloud workload, Orca provides complete visibility into cloud assets without such limitations. It covers a wide range of cloud resources, including virtual machines, containers, storage buckets, databases, serverless functions, cloud infrastructure, identities, web and API endpoints, and sensitive data.
- Comprehensive Risk Identification: Using that wide visibility, Orca helps organizations address a broad range of cloud risk categories by alerting teams to misconfigurations, vulnerabilities, sensitive data at risk, identity and access management, lateral movement, exposed APIs, suspicious activity, and more.
- Ability to Customize PCI DSS Controls: Orca offers the flexibility to customize controls according to an organization’s unique requirements and incorporate additional best practices. While the PCI DSS guidelines offer general guidance, they may not address the specific nuances of each cloud environment. By leveraging this flexibility, organizations can enhance their overall compliance efforts and address unique cloud-related risks.
To learn more about how Orca simplifies compliance efforts and helps maintain a strong cloud security posture, read our blog Taking the Pain Out of Cloud Compliance. To read about each PCI DSS control that Orca helps organizations meet, download the GRESee Consulting assessment Meet PCI DSS Requirements with the Orca Cloud Security Platform.






