We are pleased to announce the launch of our new Attack Path Analysis capabilities, as part of our ongoing efforts to continually innovate and enhance the Orca Cloud Security Platform. The new features incorporate the detection of cross-account and cross-cloud provider attack paths, a type of attack path that we are increasingly seeing in the cloud environments we scan. Other enhancements include attack path timelines, risk blast radius, and choke point detection, further enabling security teams to address risks strategically and reduce the damage that a potential attacker can cause in the environment.
What is Orca Attack Path Analysis?
Instead of only looking at siloed risks, Orca uses attack path analysis to identify the different weaknesses that a potential attacker could exploit to move laterally in the cloud environment to reach business critical assets. By understanding how risks can be combined to create dangerous attack paths, security teams can focus on the risks that pose the greatest danger, and spend less time on insignificant ones. Orca scores each attack path based on its exploitability and potential business impact so teams can quickly prioritize issues.
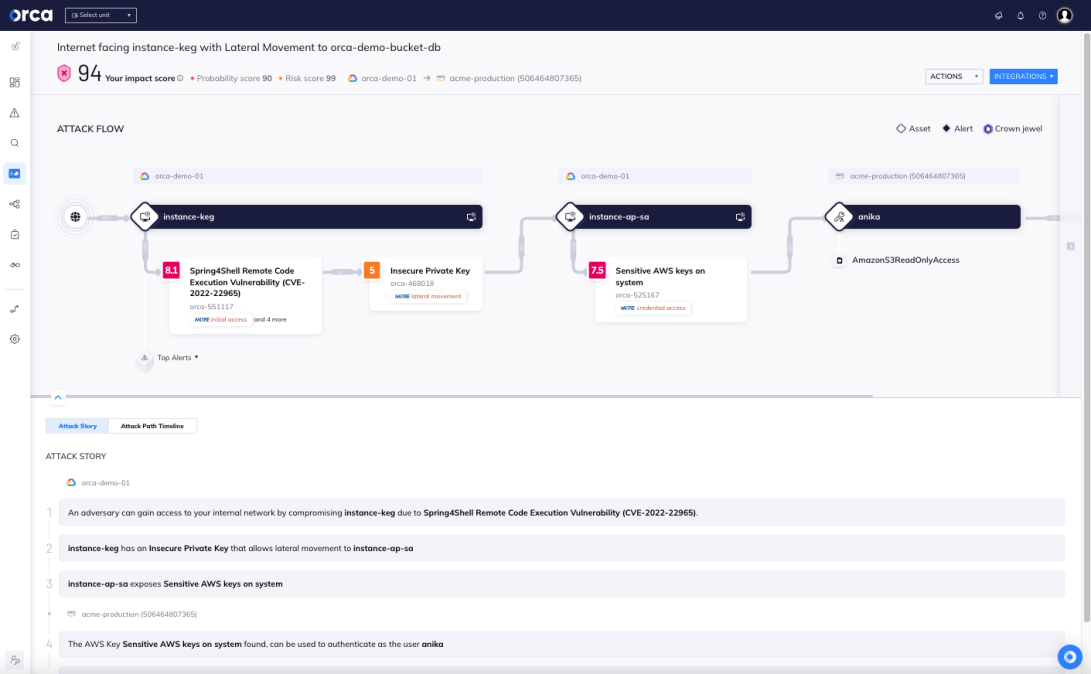
How Does Attack Path Analysis Enable Strategic Remediation?
Instead of flooding security professionals with hundreds of siloed alerts each day, attack path analysis enables teams to see the bigger picture and in doing so, understand which risks are the most critical.
For instance, if we take the analogy of trying to secure a house against a burglary, we may not mind so much that the lock on the garden shed is weak if we don’t store any valuables in the shed and it’s not connected to the house. However, if we keep a key to the house in the shed, this would constitute a critical attack path. To resolve this, it would be of high importance to remove the key in the shed. Fixing the lock on the shed door would however be of much lower priority.
With attack path analysis, defenders can quickly understand which weaknesses need to be fixed to avoid the most dangerous risks, without wasting time on attack vectors that don’t lead anywhere. With the enormous amounts of alerts that security practitioners receive every day (our Cloud Security Alert Fatigue Survey found that the majority receive more than 500 alerts every day), teams can simply not be expected to fix *all* weaknesses and instead need to remediate strategically to remain effective and not become completely overwhelmed.
What’s New in Orca’s Attack Path Analysis?
Below we list the five new Attack Path Analysis features on the Orca platform, designed to empower teams to see the bigger, multi-cloud picture and instantly understand which risks need to be fixed to obtain the highest yielding security improvements.
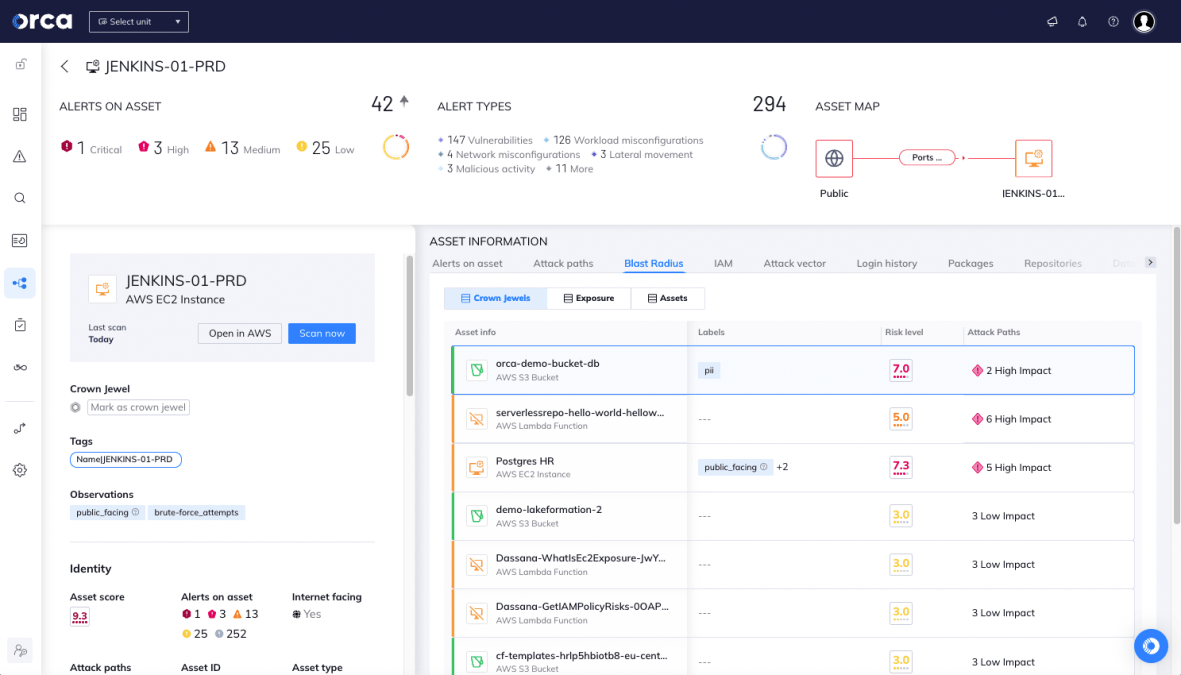
1. Risk Blast Radius
Orca now shows the blast radius of each risk, in other words how many assets the detected risk could affect and which ones are crown jewels. In addition, it shows all the different access paths that lead to the risk (exposure). Risks that endanger crown jewels should be prioritized, followed by risks that expose the most assets and are the most exposed.
2. Attack Path Timeline
Each attack path now also includes a timeline, helping teams understand how events and actions either increase or decrease risk severity and attack path score. For instance, when a vulnerability is fixed, the timeline will show how many attack paths have been resolved and/or whether the attack path risk score was reduced. Alternatively, if a user stores sensitive data in an S3 Bucket that is exposed by several existing attack paths, the attack path risk scores will be increased since Orca will detect the sensitive data as a crown jewel and raise the attack path score to critical.
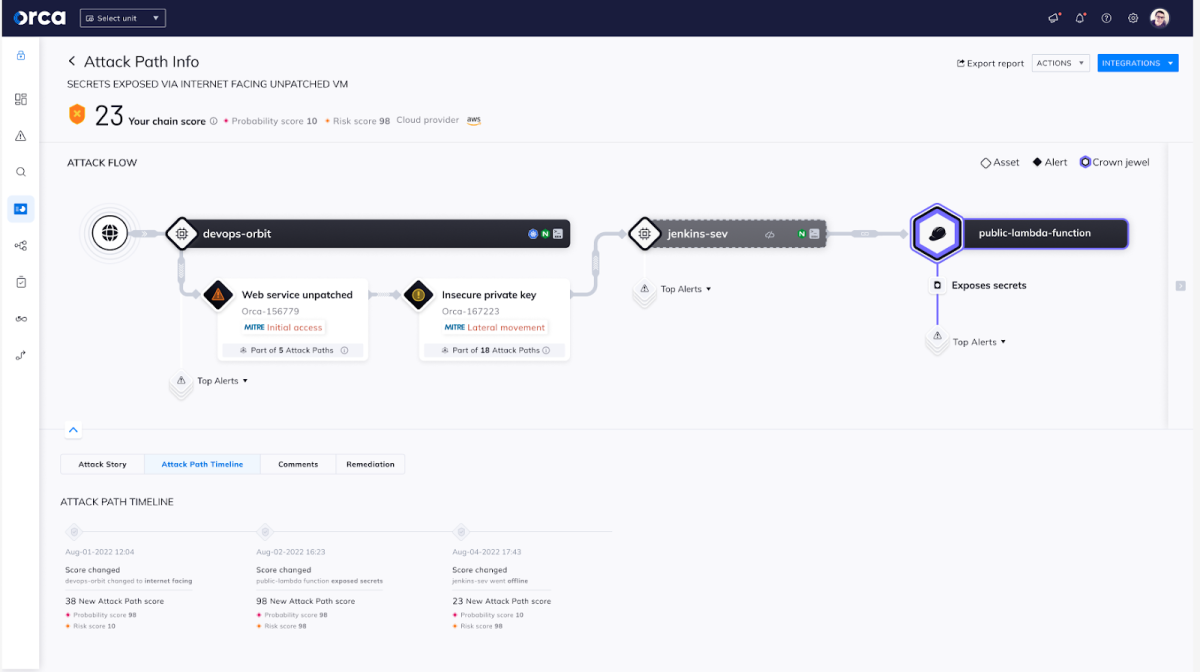
3. Cross-account Attack Paths
Another enhancement is Orca’s ability to detect attack paths that ‘hop’ from one account to another account within the same cloud provider platform. For organizations with multi-account environments, identifying cross-account risks is crucial to securing their cloud resources and data.
For instance, it is possible that the environment of one cloud account is very secure, but that there is a key allowing access to the account on an entirely different cloud account. This is like having a very secure lock on your front door, and all your windows dead bolted, but leaving the side door open. With Orca Attack Path Analysis, security teams will be alerted to these types of cross-account risks.
4. Cross-provider Attack Paths
What many organizations may not realize is that if they are utilizing multiple cloud provider platforms, there can also be attack paths that ‘hop’ from one cloud provider to another. If an organization is using single cloud platform security tools, they will be blindsided to these risks, which could turn out to be critical.
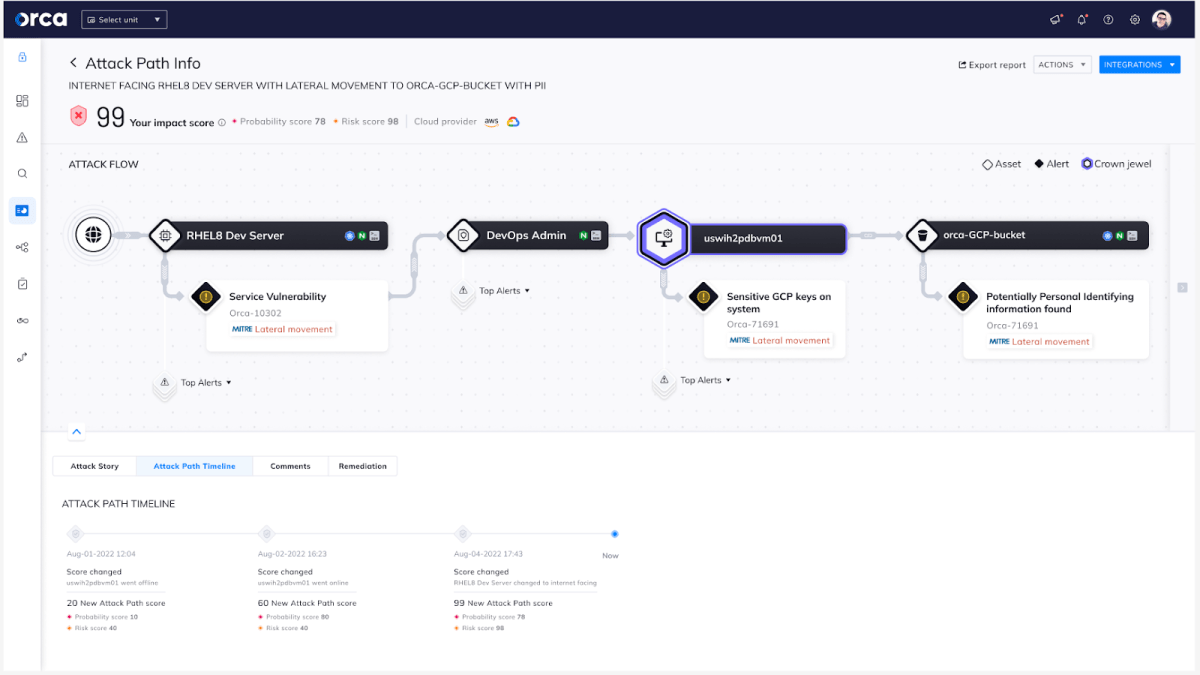
Since Orca supports multiple cloud providers and combines all the data in a single platform, it can detect possible cross-provider attack paths that would allow an attacker to move from one cloud provider to another. For example, a forgotten AWS key on a developer Azure machine could lead to a full account takeover of the AWS environment. If separate security tools are used for the Azure and AWS environments, this attack path could not be identified.
5. Choke Point Alerts
In addition to showing teams which attack paths lead to business critical assets and need to be fixed with priority, Orca also shows teams how they can be most effective in their mitigation efforts. Let’s say the security team has been able to diffuse all the critical attack paths. They now have the luxury of attending to perhaps less critical but still important risks that need to be remediated.
To help teams understand how they can be the most effective with their time, for each alert, Orca shows the number of attack paths it is part of, their average score, and total potential impact. The alerts that are part of the most attack paths with the highest severity are referred to as ‘choke points’. By prioritizing the remediation of these choke points, security teams can improve their effectiveness, overcome resource restraints, and significantly improve cloud security posture with less effort.
Work Smarter, Not Harder
In summary, Orca’s attack path analysis enables teams to make informed decisions about how to allocate their remediation efforts, based on a thorough understanding of what their most critical risks are. By taking this strategic approach to remediation, organizations can reduce their exposure to damaging breaches and improve their overall cloud security posture. In addition, by reducing the flood of alerts to a much smaller number of critical attack paths, choke points, and risks with the largest blast radius, alert fatigue and team burnout can be significantly reduced.
Want to learn more about cross-account and cross-cloud provider attack paths and how Orca can help your security team stay one step ahead of attackers? Join our webinar ‘Defending Against Multi-Cloud Attack Paths’ on April 13th, at 11 am PST.
Let Orca Find and Prioritize Your Attack Paths
Want to get more hands-on and find out which attack paths in your cloud environment are the most critical and how to tackle them with the greatest effectiveness? Sign up for Orca’s free, no obligation 30-day risk assessment. Since the Orca platform covers 100% of your assets without requiring agents, after only a simple 30-minute setup, Orca will start scanning your entire environment, surfacing all your most critical risks and attack paths.