Zscaler and Orca Security partner through an existing integration with Zscaler Unified Vulnerability Management (UVM), enabling customers to bring Orca’s cloud-native vulnerability insights into UVM’s consolidated exposure view. This helps organizations maintain consistent risk scoring and streamline remediation across their cloud environments
In today’s cloud-native era, organizations are facing a dual challenge: securing sprawling cloud workloads and managing remote or private application access that bypasses traditional network perimeters. As access infrastructure and cloud assets both rapidly evolve, threat detection and prioritization must evolve together.
To address this, Orca Security and Zscaler are deepening their strategic technology partnership by bringing together Zscaler Private Access™ (ZPA™) context and Orca’s cloud-risk intelligence. The result? Smarter alerting, stronger prioritization, and fewer false positives — delivering real impact to security operations.
What is Zscaler Private Access?
Zscaler Private Access (ZPA) is a cloud-delivered zero trust network access (ZTNA) solution that provides secure, seamless, and direct connections between users and private applications without ever placing users on the network. Instead of relying on traditional VPNs, ZPA uses identity, device posture, and contextual policies to verify every request and manage connections through the Zscaler Zero Trust Exchange™ platform. This approach eliminates lateral movement, reduces attack surface, and simplifies access for distributed and hybrid workforces.
ZPA dynamically connects authorized users to internal applications running in data centers or public clouds such as AWS, Azure, or Google Cloud. The service is fully managed and globally distributed, ensuring low latency and high availability. With granular policy controls and continuous posture assessment, ZPA enables organizations to modernize access, replace legacy VPN infrastructure, and embrace a zero trust model.
Why This Matters
Cloud environments continue to expand: containers, serverless functions, VMs, managed services. At the same time, the way users connect and access applications has shifted dramatically. Private apps, egress IPs, managed connectors aren’t outlying concerns anymore. They’re a core part of your attack surface.
With this growth comes noise: thousands of alerts, thousands of endpoints, access patterns, trust boundaries. Security teams often struggle with the question: Which of these alerts matter? Which can I safely ignore? Which one is telling me the right next step?
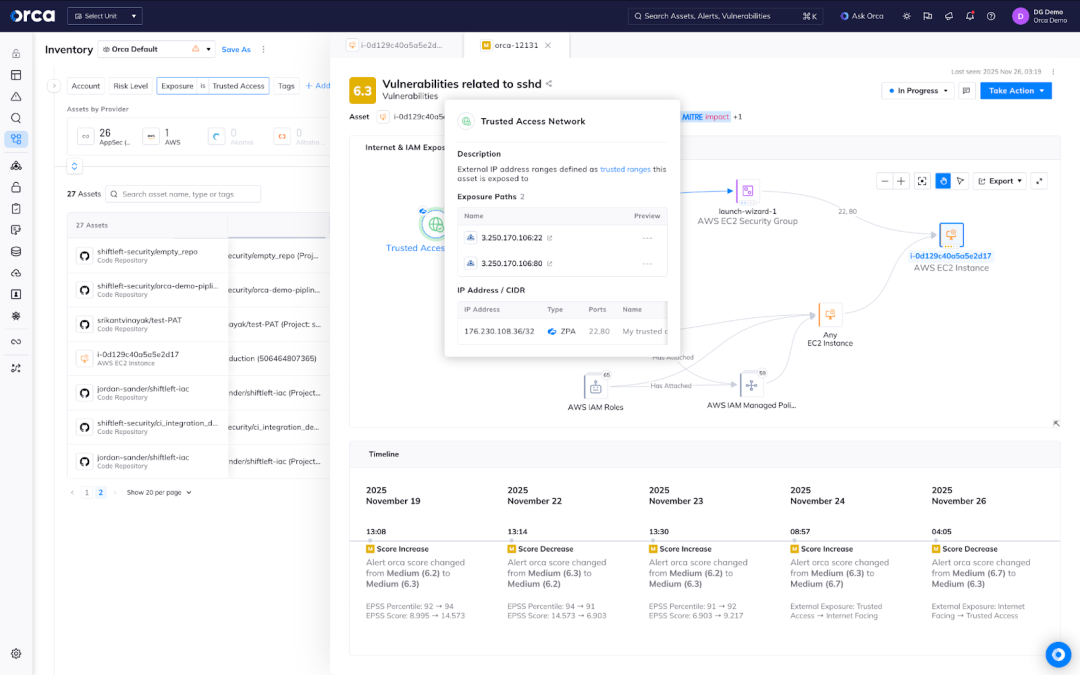
That’s where the Orca + Zscaler integration comes in. By combining access context from ZPA with asset & exposure context from Orca, we can understand more about the alert allowing us to better identify and prioritize work.
What’s New in the Integration
Here’s how the enhanced partnership unlocks value:
- Ingest ZPA access & egress metadata – Zscaler’s managed/egress IPs, private-app endpoints, connector metadata and access footprints now feed into Orca in near real time.
- Automatically correlate alerts – When Orca flags a “malicious or suspicious IP” alert, it now checks whether that IP belongs to a ZPA managed/egress pool or is tied to a private-app connector. If it is — that access flow may already be trusted.
- Tighten risk scoring & reduce noise – If the destination is verified by ZPA context, Orca can dynamically lower severity or suppress alerts, freeing security teams to focus on the truly unknown or untrusted risks.
- Unified visibility across access + cloud assets – This integration bridges what users/apps are doing (via ZPA) and what the cloud workloads are exposed to or doing (via Orca). That’s a powerful combination for prevention, detection and response.
Real-World Impact: What Customers Experience
With the Orca-Zscaler integration, that trust-infrastructure question becomes clearer. If the suspicious IP is part of a ZPA connector that you manage and trust, the alert can be deprioritized. If not, it’s flagged — and you get insight into why.
Benefits of the integration include:
- Less alert fatigue & fewer false positives – By eliminating alerts tied to trusted access flows, the signal-to-noise ratio improves.
- Faster investigation time – By correlating access metadata and risk scoring in one place, SecOps teams spend less time stitching together logs and more time acting.
- Stronger Zero-Trust posture – Access and workloads are no longer siloed; you get end-to-end risk insight across private apps, egress IPs and cloud exposures.
Why Partnering Matters
This partnership is about more than data sharing or connector knock-ins. It’s about bringing together two domains that too often operate in isolation:
- Access infrastructure (who/what/app) – handled by Zscaler’s Zero Trust Exchange.
- Cloud workload exposure & asset risk (where/what) – handled by Orca’s cloud-native application protection platform.
By integrating, we’re enabling a new paradigm: trust isn’t just “you’re on the network”, it’s “you’re accessing that app from that connector and the workload behind it has this exposure”. That level of context unlocks smarter prioritization, faster detection and better posture.
About Orca Security
Orca Security provides agentless, cloud-native application protection across multi-cloud workloads. We deliver full visibility into risk, exposure and threat across the cloud environment — enabling teams to move fast while staying secure. Interested in discovering the benefits of the Orca Platform? Schedule a personalized 1:1 demo.
About Zscaler
Zscaler enables secure access to applications, users and devices – no matter where they are. Its Zero Trust Exchange architecture delivers fast, policy-driven connectivity and protection in the modern perimeterless world.





