A critical vulnerability (CVE-2025-68613, CVSS 9.9/10.0) was disclosed affecting the n8n workflow automation platform, allowing attackers to execute arbitrary code on the underlying server via expression injection in workflow definitions. Due to the potential for full instance takeover, data exposure, and lateral movement, immediate patching is required.
The issue originates from n8n’s workflow expression evaluation mechanism, where insufficient sandbox isolation allows user-supplied expressions to escape the intended execution context. By submitting specially crafted workflow expressions, an attacker can execute OS-level commands with the privileges of the n8n process, effectively gaining remote code execution on the host. Exploitation requires authentication, but no elevated privileges beyond workflow creation or editing.
The vulnerability affects the n8n core workflow engine in versions starting from 0.211.0 up to but not including the fixed releases 1.120.4, 1.121.1, and 1.122.0. These components are widely used in self-hosted n8n deployments and embedded automation environments, particularly where interactive workflow editing is enabled. Other services or platforms that rely on vulnerable n8n versions may also be impacted. Users should upgrade immediately to n8n versions 1.120.4, 1.121.1, or 1.122.0, which properly harden expression evaluation and prevent sandbox escapes. Environments that previously applied partial mitigations should still upgrade, as earlier fixes did not fully address the underlying issue.
At the time of writing, there are no widely reported public proof-of-concept exploits or confirmed in-the-wild exploitation. However, the severity of the vulnerability and the relative ease of exploitation make it high risk, especially for internet-facing or multi-tenant n8n deployments. Successful exploitation could allow attackers to execute arbitrary commands, access or exfiltrate sensitive data processed by workflows, manipulate or destroy automation logic, and potentially pivot further into the surrounding infrastructure, leading to service disruption or full environment compromise.
How can Orca help?
The Orca Cloud Security Platform enables customers to quickly identify assets running vulnerable n8n versions and understand their exposure in context, including internet accessibility, runtime reachability, and asset criticality. Orca helps prioritize remediation based on real risk rather than CVSS alone, highlighting affected assets directly in the newItem view so security teams can focus on the most critical remediation paths first.
The Orca Platform displays trending vulnerabilities in the “From the News” widget of the Orca dashboard. Users can see if their environment is vulnerable to the vulnerabilities and how to remediate them.
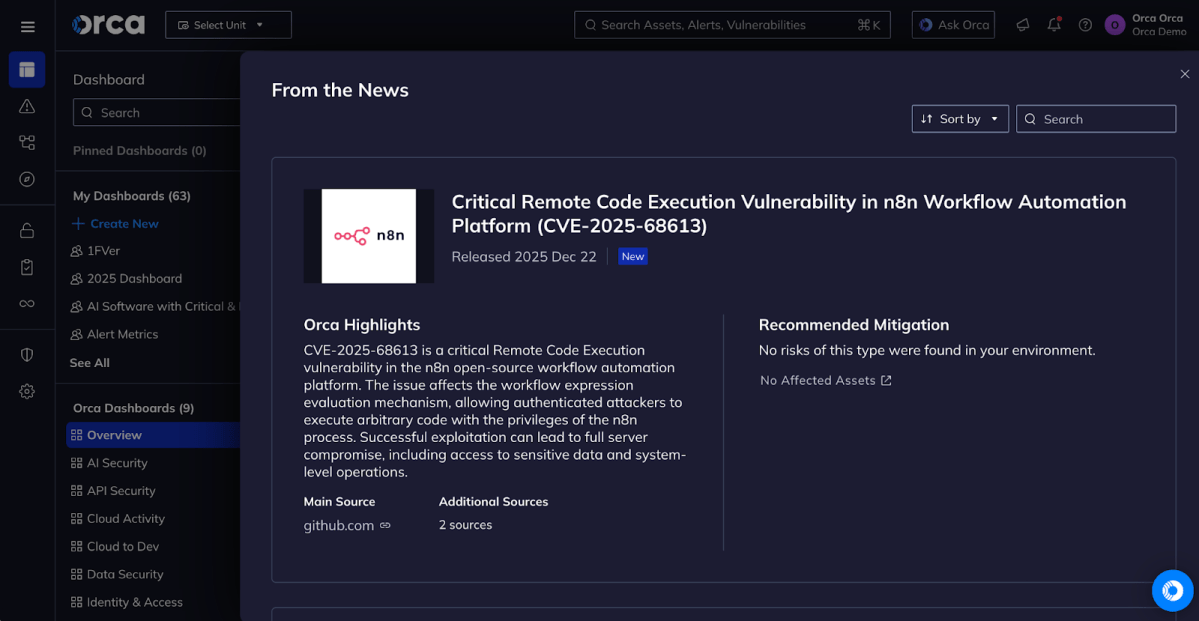
Learn more
If you’re interested in learning more about the Orca Platform and how it can help you protect against vulnerabilities, schedule a personalized 1:1 demo.




