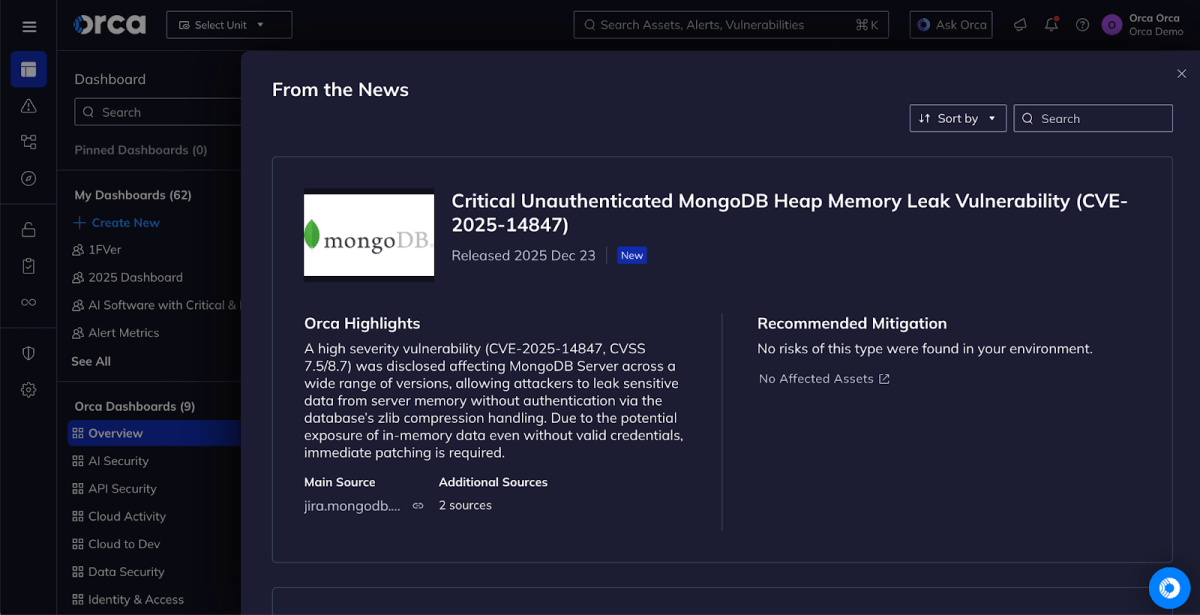
A high severity vulnerability (CVE-2025-14847, CVSS 7.5/8.7) was disclosed affecting MongoDB Server across a wide range of versions, allowing attackers to leak sensitive data from server memory without authentication via the database’s zlib compression handling. Due to the potential exposure of in-memory data even without valid credentials, immediate patching is required.
The issue originates from how MongoDB’s server implements zlib compressed protocol headers, where mismatched length fields lead to uninitialized heap memory being returned in responses. By sending specially crafted requests over the network to a reachable MongoDB instance, attackers can trick the server into responding with memory contents that may include previously handled query data or other cached information, potentially exposing sensitive information with no authentication required and low complexity to exploit.
The following components are affected: MongoDB Server versions 8.2.0 through 8.2.3, 8.0.0 through 8.0.16, 7.0.0 through 7.0.26, 6.0.0 through 6.0.26, 5.0.0 through 5.0.31, 4.4.0 through 4.4.29, and all 4.2, 4.0, and 3.6 series builds. These server releases are widely deployed across on-premise and cloud environments and are particularly impactful when internet-facing or reachable from untrusted networks.
Users should upgrade to the fixed versions addressing the flaw, including 8.2.3, 8.0.17, 7.0.28, 6.0.27, 5.0.32 and 4.4.30, which close the vulnerability. If immediate upgrades are not feasible, temporarily disabling zlib compression is possible but not a substitute for patching.
At the time of writing, public proof-of-concepts are circulating and no widespread exploitation has yet been reported, but the severity and unauthenticated nature make this high risk for exposed databases. Successful exploitation could allow attackers to harvest sensitive fragments of memory, which attackers could leverage for subsequent reconnaissance or credential harvesting, leading to broader compromise or data leakage.
How can Orca help?
The Orca Cloud Security Platform enables customers to quickly identify assets running vulnerable MongoDB versions, understand their exposure in context – including internet accessibility, runtime reachability, and asset criticality – and prioritize remediation based on real risk rather than CVSS alone. Orca’s platform highlights affected assets directly in the newItem view, helping security teams focus on the most critical remediation paths first.
Learn more
If you’re interested in learning more about the Orca Platform and how it can help you protect against vulnerabilities, schedule a personalized 1:1 demo.