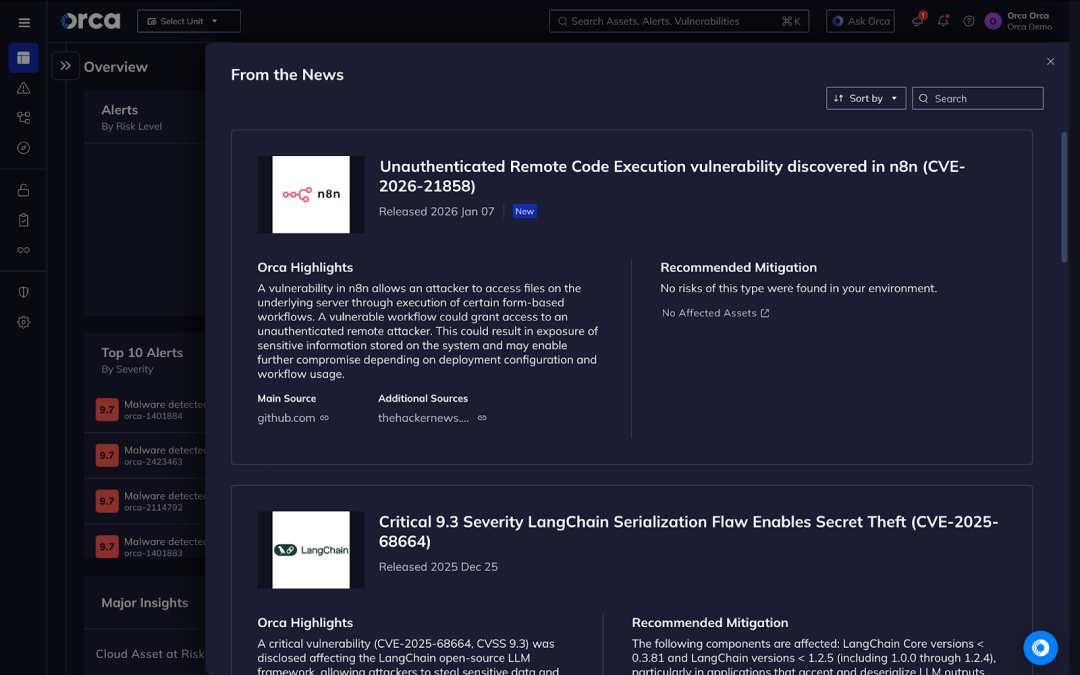
A critical vulnerability (CVE-2026-21858, CVSS score 10.0) was disclosed affecting the n8n workflow automation platform, allowing attackers to remotely execute code and fully take over vulnerable instances without any authentication. Due to the potential for complete compromise of automation infrastructure, data exposure, and downstream access to integrated systems, immediate patching is required.
The issue originates from a Content-Type confusion flaw in n8n’s webhook and file-handling logic, where incorrect handling of the Content-Type header leads to overriding internal request parsing state and enables arbitrary file access and execution paths. By sending specially crafted HTTP requests with manipulated content types and body structures to webhook endpoints, attackers can override internal state, access sensitive files including authentication secrets, forge admin sessions, and ultimately achieve arbitrary code execution on the host. These impacts include server takeover, credential and secret theft, and lateral movement into connected services. No authentication is required to exploit this issue.
The following components are affected: n8n webhook handlers and file upload parsers in versions prior to 1.121.0. These components are used by self-hosted n8n deployments and automation infrastructures that integrate internal systems, APIs, and cloud services.
Users should upgrade to n8n version 1.121.0 or later, which addresses the underlying issue, as no effective official workarounds are available. At the time of writing, proof-of-concept details are public in the Cyera-published research, and internet-facing instances are widely exposed, making this vulnerability high risk. Regardless, the severity and ease of exploitation make this vulnerability high risk, especially in internet-facing deployments. Successful exploitation could allow attackers to take full control of the instance, extract sensitive data and credentials, and pivot deeper into connected infrastructure, leading to service disruption, data exposure, or full infrastructure compromise.
How can Orca help?
Orca enables customers to quickly identify assets running vulnerable n8n versions, understand their exposure in context – including internet accessibility, runtime reachability, and asset criticality – and prioritize remediation based on real risk rather than CVSS alone. Orca’s platform highlights affected assets directly in the “From the News” item view, helping security teams focus on the most critical remediation paths first.
Learn more
If you’re interested in learning more about the Orca Platform and how it can help you protect against vulnerabilities, schedule a personalized 1:1 demo.




