According to PwC’s 2024 Global Digital Insights report, nearly half of executives rate cloud security as their top cyber concern–that bookmarks an important finding for the vast majority of third-party organizations that depend on the cloud to deliver their services, such as SaaS platforms, Fintech companies, and business analytics services. As these providers search for new business, they face the growing challenge of having to earn the trust of risk-averse prospects.
Fortunately, SOC 2 offers an effective pathway toward establishing credibility. SOC 2 is a voluntary compliance framework designed for service organizations to demonstrate their ability to safeguard client data from unauthorized access and disclosure. Yet achieving SOC 2 can prove challenging, especially as organizations become more dependent on cloud environments that are constantly changing and demand skills that are in short supply.
In this post, we dive deep into the world of SOC 2 compliance, examining the standards it requires companies to meet, the challenges it presents, and the best practices you can implement to achieve compliance more easily and sustainably. In addition, we explain how the Orca Cloud Security Platform can automatically run all SOC 2 controls in your multi-cloud environment so your teams can quickly address any identified issues and maintain continuous compliance.
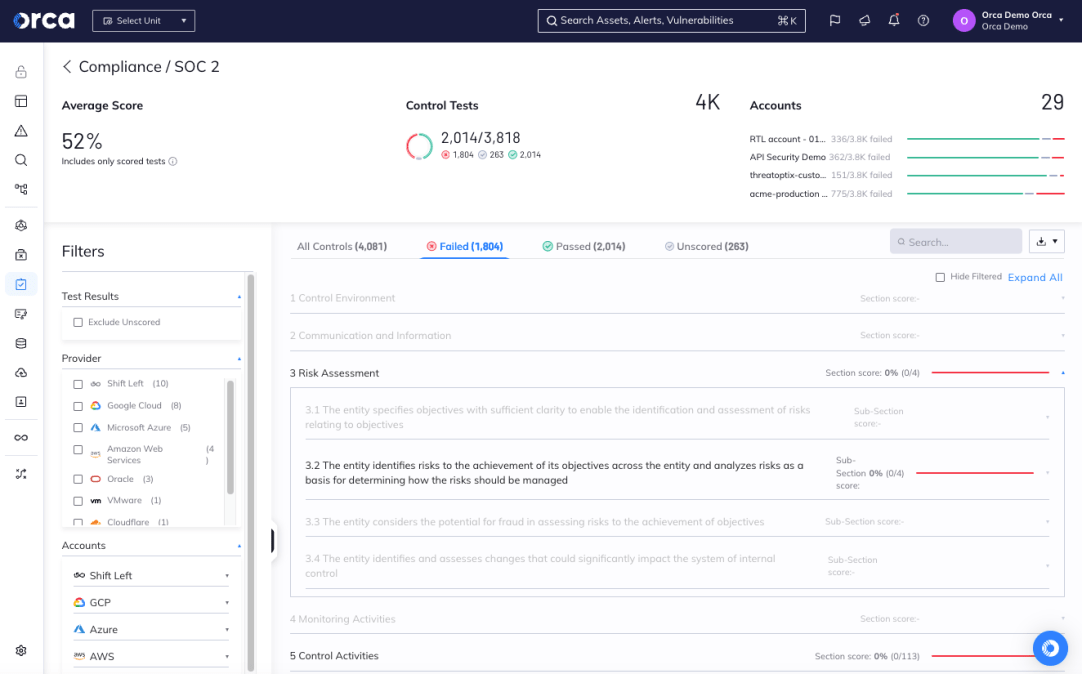
What is SOC 2?
Developed and published by the American Institute of Certified Public Accountants (AICPA), SOC 2 is a compliance framework used by service organizations to demonstrate their commitment to safeguarding customer data. The framework evaluates internal controls across five key areas, referred to as trust services criteria (TSC):
- Security: Protect stored data from unauthorized access and disclosure.
- Availability: Ensure systems remain operable and available for use.
- Confidentiality: Protect confidential information.
- Privacy: Ensure that personal information is collected, stored, disclosed, and removed according to established policies.
- Processing Integrity: Ensure system processing remains complete, valid, accurate, timely, and authorized, and customer data stays accurate and unchanged during the processing lifecycle.
To comply with SOC 2, service providers must identify the internal controls that warrant validation and meet the trust service criteria. Once identified, a licensed CPA firm audits the controls and prepares a formal report, which customers, prospects, business partners, and other stakeholders may request for review.
SOC 2 is one of three types of SOC reports:
- SOC 1: Analyzes controls related to financial reporting.
- SOC 2: Assesses controls related to one or more trust services criteria: Security, Availability, Privacy, Confidentiality, and Process Integrity. The audience for the report includes existing customers, prospects, business partners, and other stakeholders.
- SOC 3: Analyzes the same controls as SOC 2 but reports findings at a high-level in an abbreviated format for the same audience as SOC 2.
Additionally, two kinds of reports are available for SOC 2, which determine the scope of the analysis:
- Type I – Evaluates internal controls against one or more trust services criteria at a specific point in time.
- Type II – Evaluates internal controls against one or more trust services criteria for three to 12 months.
What are the challenges of achieving SOC 2 compliance in the cloud?
To be clear, the SOC 2 compliance framework applies broadly to a specific set of controls implemented by an organization, meaning it doesn’t focus exclusively on what happens in the cloud. Still, the cloud presents special challenges for compliance with the voluntary framework.
Below are some of the most common that service providers face:
- Coverage of cloud assets – To comply with SOC 2, organizations need complete and continuous visibility into their entire cloud estate. Agent-based compliance solutions cover only about 50% of cloud assets, creating blind spots in your cloud environments. This results in data security concerns and compliance gaps. For example, agent-based technology cannot discover all personally identifiable information (PII) at risk since it simply doesn’t cover all your resources and could easily miss shadow data.
- Multi-cloud policy management – With most organizations using more than one cloud, multi-cloud policy management is a must. Cloud service providers offer native security features that can assist with policy management, but these tools remain platform-specific and disparate. However, using a multi-cloud security platform avoids the need to manually manage and align policies for each cloud environment, which creates duplicative work for teams and increases the potential for discrepancies.
- Risk prioritization – While compliance solutions can effectively identify issues to resolve, they often fail to prioritize alerts so security, DevOps, and development teams know which issues are most critical. This often leads to alert fatigue, frustration, and inefficiencies, not to mention delays in addressing the most time-sensitive issues. It also distracts teams from other responsibilities and higher-value priorities. Nearly 60% of security teams report receiving 500 cloud security alerts per day, according to Orca’s Cloud Security Alert Fatigue Report.
- Customization – Organizations face different compliance needs and requirements that are unique to their business. Unfortunately, many dedicated compliance solutions offer standard compliance frameworks that prevent customization and tailoring compliance frameworks to specific use cases. This prevents organizations from streamlining their compliance reporting to account for their unique processes, policies, and security infrastructure.
- Remediation – Dedicated compliance solutions may identify gaps and issues in compliance, yet they fail to provide guidance or instructions for remediating problems. This presents significant challenges and delays, especially as organizations face talent and skills shortages.
- Unified context – Compliance is affected by every inch of the cloud estate. Because few compliance solutions can synthesize everything happening across multi-cloud environments, organizations lack unified context about their compliance risks and issues. This makes compliance more difficult to achieve and sustain, as well as time-consuming and costly.
Best practices for achieving SOC 2 compliance in the cloud
When it comes to your cloud environments, you can achieve SOC 2 compliance by adopting five best practices, which we review below:
1. Choose a SOC 2 compliant cloud service provider (CSP)
The first step toward compliance is to choose a cloud service provider (CSP) that can certify that their products meet SOC 2 compliance standards. Today’s most popular CSPs make third-party audit reports publicly available on their website, including:
- AWS compliance
- Azure compliance
- Google Cloud compliance
- Alibaba cloud compliance
- Oracle Cloud compliance
Choosing a SOC 2 compliant CSP is essential for your compliance efforts. That’s because CSPs operate according to a shared responsibility model. This means that CSPs are accountable for meeting compliance standards in the infrastructure they provide. However, organizations are still accountable for securing the assets and applications that they run in the cloud. This last part comes as no surprise considering that Gartner predicts that 99% of cloud security failures will be caused by customers, not CSPs, by 2025.
2. Adopt the right CNAPP
Compliance demands complete protection, visibility, and coverage of your entire cloud estate. That calls for adopting the right kind of cloud security solution that secures not only your cloud infrastructure, but your workloads too. While this historically meant relying on multiple point solutions, cloud-native application protection platforms (CNAPPs) have emerged as the optimal solution for unified and comprehensive cloud security.
True CNAPPs combine the capabilities of multiple cloud security solutions into one integrated solution, all of which are necessary for compliance. These include:
- Cloud workload protection platforms (CWPPs)
- Cloud security posture management (CSPM)
- Cloud infrastructure entitlement management (CIEM)
- Data security posture management (DSPM)
- Cloud detection & response (CDR)
- Vulnerability management
- API security
- Shift Left security
- Container and Kubernetes security
Yet the emphasis here is on “true CNAPPs.” They aren’t created equal, and some can add to the burden of SOC 2 compliance. Here are important qualities to look for when shopping for a CNAPP. Note that this isn’t an exhaustive list, but a good place to start.
- Agentless-first: As referenced earlier, agent-based solutions provide limited visibility and coverage of your cloud assets, which prevents compliance. They also involve complex configurations, slow deployments, and time-consuming maintenance. Agentless-first solutions alleviate these constraints by allowing you to see and protect both your control plane and data plane from a single platform. They also save you the burden of installing and maintaining agents, allowing you to deploy your CNAPP in minutes and get the full protection of cloud security on day one.
- Unified and comprehensive: Unified and comprehensive CNAPPs natively combine all the cloud security point solutions referenced earlier. As a result, they centralize your data, streamline compliance tasks, and effectively prioritize your alerts. Also, they detect all types of cloud risks, including misconfigurations, vulnerabilities, malware, lateral movement, API risks, data risks, active breaches, and more.
- Compliance-friendly: Compliance-friendly CNAPPs empower organizations to streamline compliance for their unique needs. They offer out-of-the-box, fully customizable compliance templates for an extensive library of regulatory frameworks, including SOC 2, ISO 27001, PCI-DSS, GDPR, HIPAA, NIST 800-53, and MITRE ATT&CK. They also allow you to mix and match frameworks to reflect your unique regulatory needs. All templates are consistently updated to reflect the latest standards and best practices.
- Contextualized and prioritized alerts: True CNAPPs allow you to focus on the 1% of critical alerts that truly matter. They do this by prioritizing alerts and linking cloud risks to associated compliance frameworks with clear remediation instructions.
- AI driven: CNAPPs should also leverage the power of AI to automate and accelerate critical tasks for your teams. This includes enhancing search and remediation capabilities with GenAI.
3. Establish your tailored compliance framework
With the right CNAPP in place, you can begin to optimize your cloud compliance efforts. To start, you need to set up your compliance framework or frameworks within your CNAPP. This ensures that it can continuously monitor your cloud environment, detect compliance risks, and automate activities.
Best practice is to start building your framework via a standard template, rather than starting from scratch. If you use more than one framework, it makes sense to choose and combine multiple templates at this time.
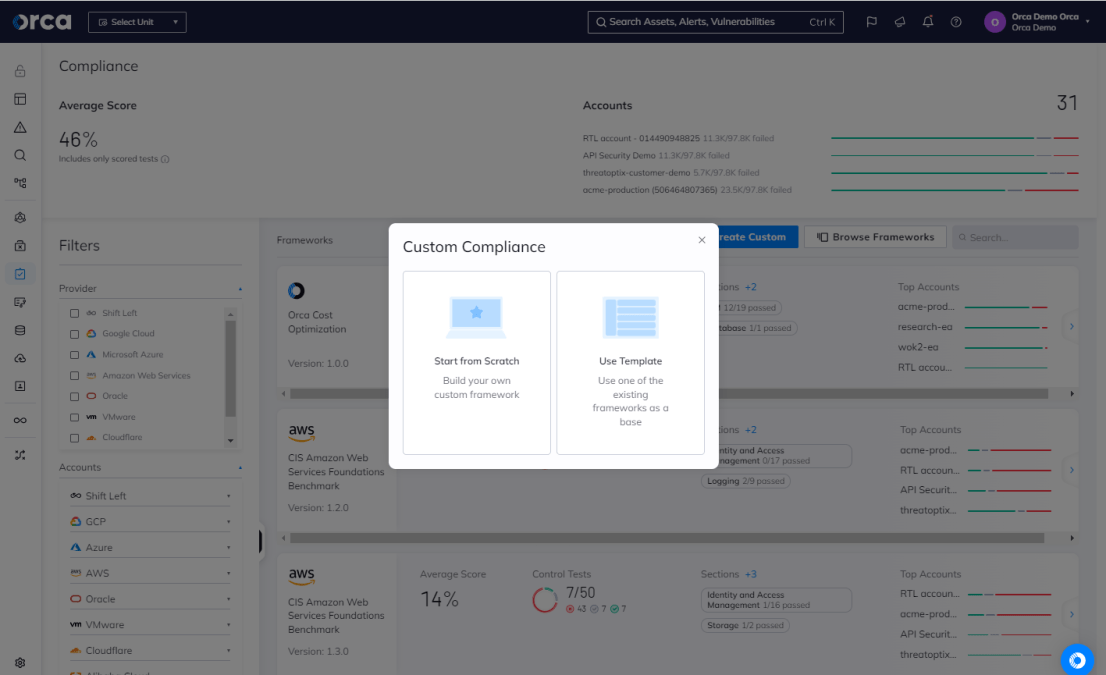
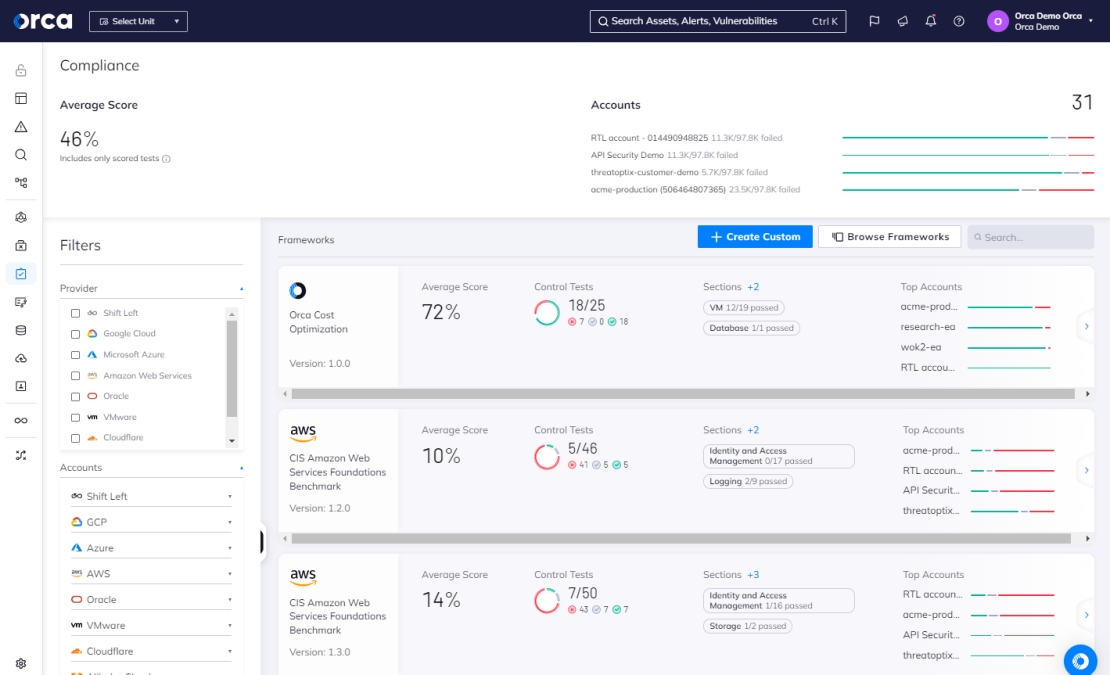
Solutions like the Orca Cloud Security Platform enable you to mix and match more than 125 compliance frameworks to fully reflect your needs. Orca also allows you to tailor your customized framework by removing any unnecessary standards that you don’t need.
4. Leverage AI
According to Gartner, 72% of companies are leveraging AI in their business, with nearly half using it across at least two business functions. The business value of GenAI is real, and there’s no reason to ignore it when it comes to your cloud compliance. That’s why you should leverage the different AI capabilities of your CNAPP solution whenever appropriate. As with anything, however, you should also ensure you review and verify the output of any GenAI prompt or command.
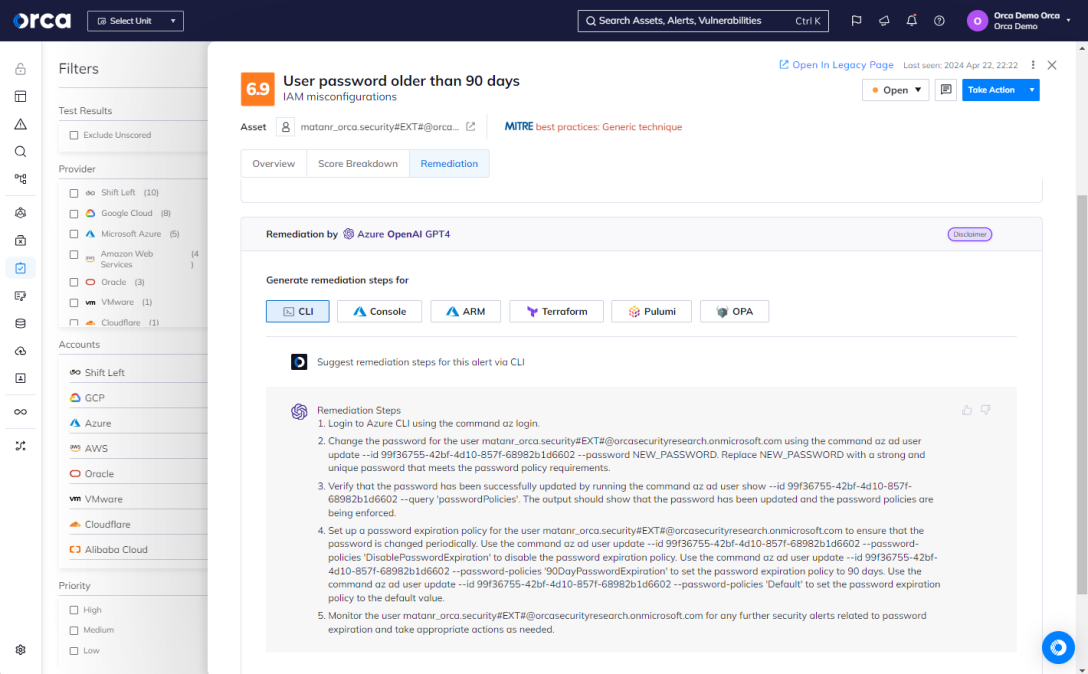
Orca enables you to streamline your search and remediation activities using generative AI. Our AI search functionality enables natural language queries, while our AI remediation generates real-time instructions to use with your preferred remediation tool. This enables you to empower your security, DevOps, and development teams to automate and accelerate their critical tasks.
5. Focus on cloud security, not just compliance
While important, compliance is just one aspect of cloud security, not the sole or primary focus of it. After all, compliance depends on prioritizing vulnerability management, shift left practices, and all the capabilities that a true CNAPP enables. Without this holistic approach, true compliance isn’t possible.
Case Study
How Orca helped Hunters with SOC 2 compliance
Achieve SOC 2 compliance with Orca Security
Securing and sustaining SOC 2 compliance remains a complex and challenging effort for service organizations. Adopting a unified cloud security and compliance platform can simplify this responsibility by making it easier, more manageable, and more efficient to achieve and sustain compliance.
Recently, GRSee Consulting, an independent security and risk management consulting firm and Qualified Security Assessor (QSA), completed an in-depth analysis and report on how the Orca Cloud Security Platform enables organizations to meet SOC 2 compliance requirements in the cloud. The scope of the analysis focused on aspects of the SOC 2 compliance framework that apply to cloud security and fall within Orca’s direct control (listed below).
The report certifies that Orca meets, supports, or validates the efforts of validating SOC 2 compliance in these areas:
- Risk Assessment
- Control Activities
- Logical and Physical Access Controls
- System Operations
- Change Management
- Availability
- Confidentiality
- Processing Integrity
- Privacy
Learn more about how Orca eases compliance efforts
With more than 125 frameworks and CIS® benchmarks, Orca helps organizations achieve multi-cloud compliance and fortify their cloud security posture.
The Orca Cloud Security Platform is certified by the Center of Internet Security® (CIS®) Benchmarks across 24 cloud frameworks. This certification validates that the platform accurately identifies any configurations that deviate from recommended best practices in over 60 CIS® Benchmarks.
Would you like to see Orca in action? Reach out to us to schedule a demo.





