Picture this: You’re a security professional staring at yet another dashboard, trying to make sense of your organization’s sprawling digital footprint. Domains, subdomains, IP addresses—they multiply faster than you can catalog them and expose your web and API endpoints. Meanwhile, somewhere out there, an attacker is methodically scanning these same assets, looking for the gaps you haven’t seen yet.
It should be no surprise that modern organizations struggle with this outside-in visibility challenge. As we’ve digitally transformed our businesses, we’ve inadvertently created a complex web of internet-facing assets that can be incredibly difficult to secure comprehensively. The fundamental question isn’t whether these assets exist. It’s whether we understand how they appear to the outside world before an adversary does.
The Reality of External Exposure
While traditional security approaches focus heavily on internal monitoring and compliance frameworks, they often miss a critical perspective: how your infrastructure looks from the public internet. This blind spot creates a dangerous disconnect between what security teams think they’re protecting and what attackers can actually observe and exploit.
Every exposed service, misconfigured certificate, missing security header, or leaked credential represents a potential entry point that threat actors can discover using the same scanning techniques available to anyone with internet access. The challenge most organizations face is understanding their security posture from an attacker’s viewpoint and prioritizing remediation based on actual exposure risk.
Introducing the new Web & API Exposure Posture Framework
Orca’s new Web & API Exposure Posture Framework addresses this visibility gap by evaluating your internet-facing application endpoints exactly as attackers and third-party security rating services do. Rather than relying solely on internal asset inventories, this framework provides a comprehensive outside-in assessment that reveals how your organization’s digital footprint appears on the public internet.
The framework evaluates seven critical areas that directly impact your external security posture:
Ownership and takeover risks help identify domains and subdomains that could be hijacked or impersonated for malicious activities.
TLS and certificate hygiene ensures your encryption standards meet modern security requirements and won’t trigger browser warnings that erode user trust.
Exposed services reveal which applications and APIs are publicly accessible, helping you understand your true attack surface beyond what you intended to expose.
Insecure configurations highlight settings that could be exploited by attackers, from weak authentication mechanisms to overly permissive access controls.
Data and secret leaks identify exposed sensitive information that could facilitate targeted attacks against your organization.
Missing security headers show gaps that could enable client-side attacks.
Threat-reputation signals provide intelligence about whether your assets are already being targeted or have been compromised.
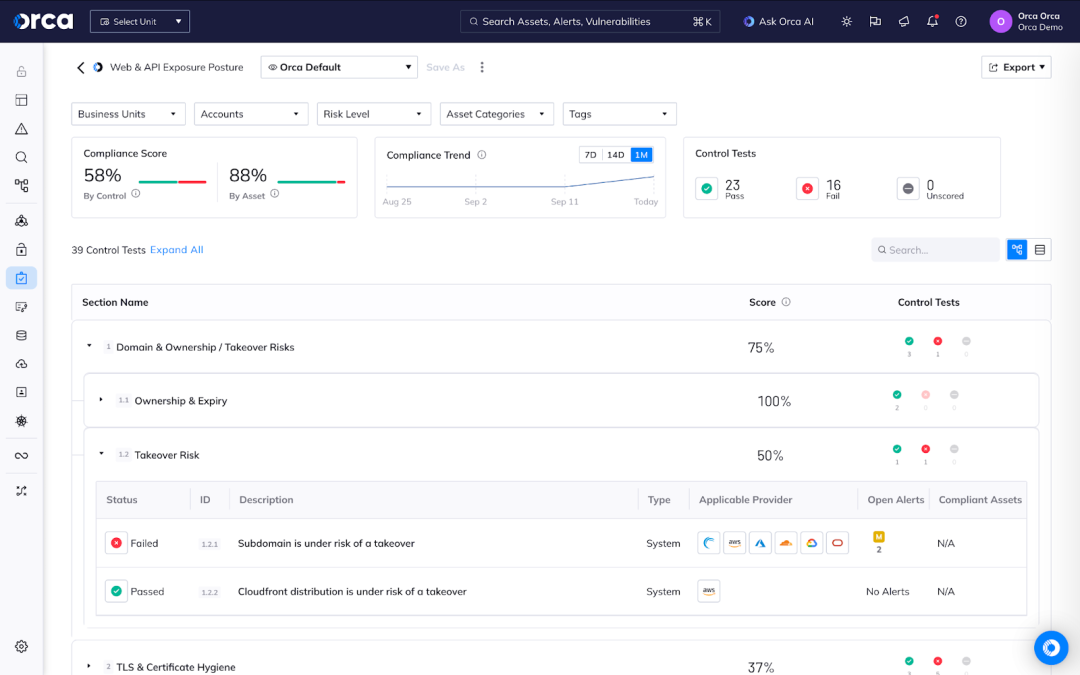
Context-Driven Security Decision Making
What makes this framework particularly powerful is its focus on providing actionable context, not just compliance checkboxes. Each failed control is connected to alerts that include severity scoring and detailed evidence, enabling security teams to prioritize remediation based on actual risk rather than generic policy violations.
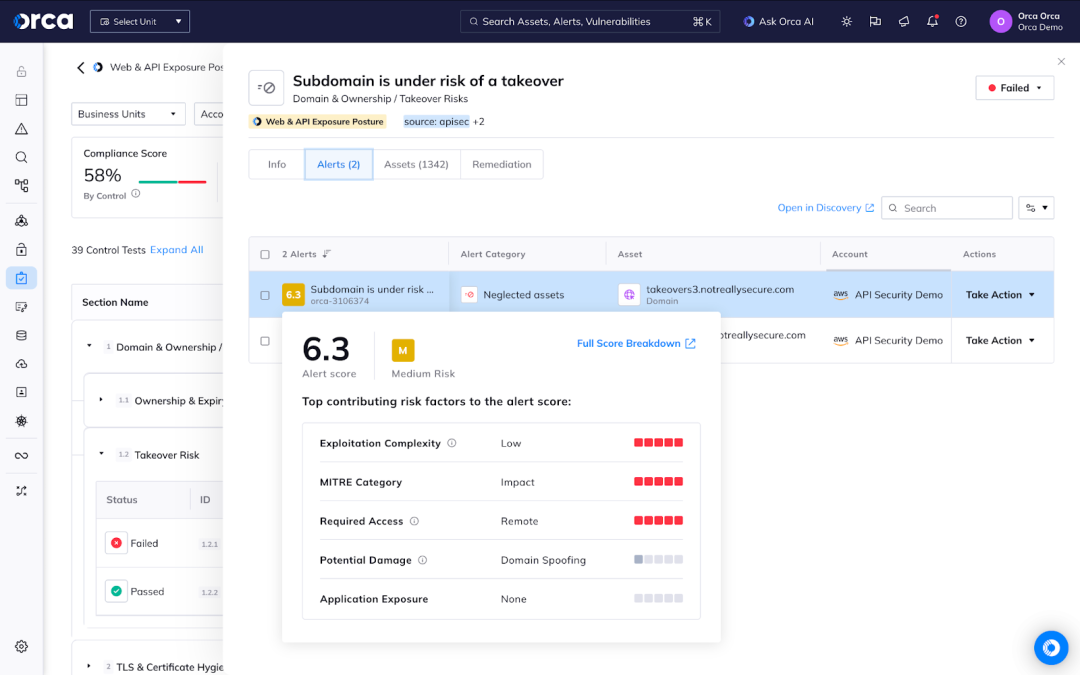
Behind the scenes, Orca runs an external scanner to automatically discover web and API assets in your cloud environment, then systematically assess their external exposure from the public internet by sending HTTP GET requests and analyzing the responses. The Orca Platform enriches this data with third-party sources like Whois and VirusTotal to gather context about domain ownership to uncover risk represented in the new Web & API Exposure framework.
The framework reflects reality: how your application endpoints appear on the public internet to anyone who cares to look. This outside-in perspective helps bridge the gap between theoretical security policies and practical threat exposure, ensuring your security investments address the risks that matter most.
Taking Action on External Exposure
Security doesn’t have to be a game of whack-a-mole with endless findings lists. By understanding your external exposure posture through the same lens that attackers use, you can make informed decisions about where to focus your limited security resources for maximum impact.
The Web & API Exposure Posture Framework empowers security teams to move from reactive fire-fighting to proactive risk management. Instead of discovering vulnerabilities after they’ve been exploited, you can identify and address exposure gaps before they become attack vectors. The Orca Platform also provides remediation recommendations, powered by Orca AI, to help teams determine mitigation steps more quickly.

Ready to see your infrastructure through an attacker’s eyes? Your external security posture is only as strong as your ability to understand and address how it appears to those who wish you harm.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Want to explore how this new compliance framework can unlock efficiency for your organization? Schedule a personalized 1:1 demo, and we’ll demonstrate how the Orca Cloud Security Platform drives cross-functional efficiency for every team that touches cloud security.





