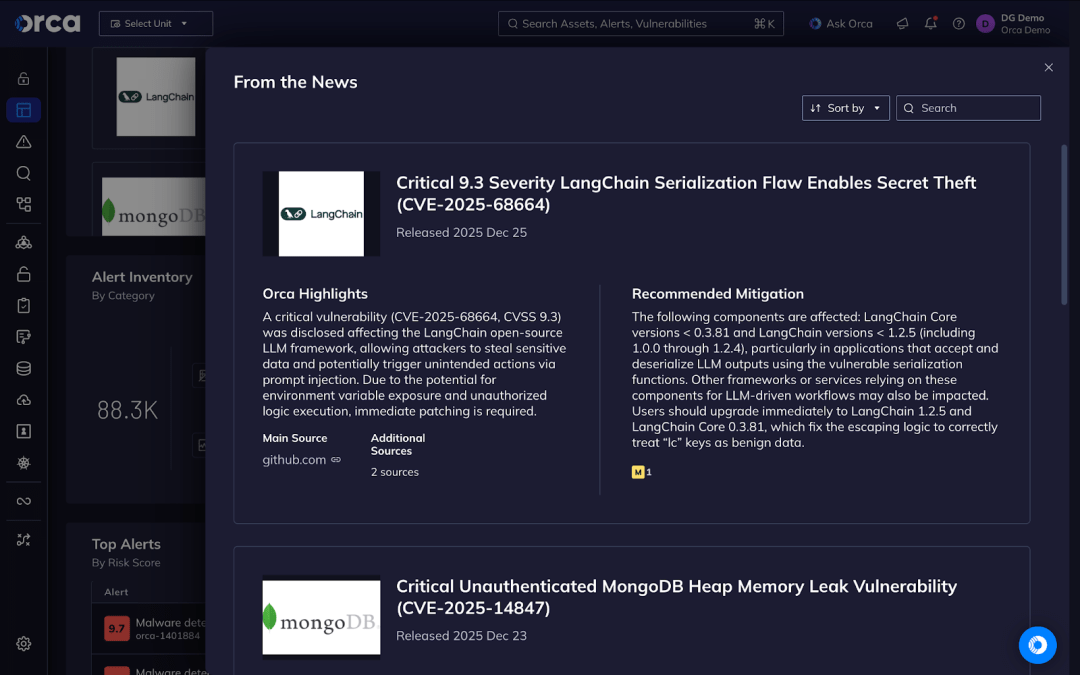
A critical vulnerability (CVE-2025-68664, CVSS 9.3) was disclosed affecting the LangChain open-source LLM framework, allowing attackers to steal sensitive data and potentially trigger unintended actions via prompt injection. Due to the potential for environment variable exposure and unauthorized logic execution, immediate patching is required.
The issue originates from LangChain’s (and LangChain Core’s) data serialization logic, where improper handling of special dictionary keys leads to a failure to escape user-controlled input during deserialization. By sending a specially crafted dictionary containing the reserved “lc” key via LLM output fields (such as response metadata that can be manipulated through prompt injection), attackers can trick the deserializer into treating attacker-controlled data as trusted objects, extract secret environment variables, and potentially instantiate arbitrary internal classes that perform side-effects like network calls or file operations.
No authentication is required to exploit this issue if an attacker can influence prompt output data. The following components are affected: LangChain Core versions < 0.3.81 and LangChain versions < 1.2.5 (including 1.0.0 through 1.2.4), particularly in applications that accept and deserialize LLM outputs using the vulnerable serialization functions. Other frameworks or services relying on these components for LLM-driven workflows may also be impacted.
Users should upgrade immediately to LangChain 1.2.5 and LangChain Core 0.3.81, which fix the escaping logic to correctly treat “lc” keys as benign data.
At the time of writing, public proof-of-concept details have been disclosed and there are no widely reported in-the-wild exploit campaigns, but the high severity and ease of exploitation make this vulnerability high risk, especially in internet-facing or data-critical deployments. Successful exploitation could allow attackers to extract API keys and environment secrets, execute unexpected internal logic, and potentially pivot to further compromise application components or backend systems.
How can Orca help?
The Orca Cloud Security Platform enables customers to quickly identify assets running vulnerable versions, understand their exposure in context – including internet accessibility, runtime reachability, and asset criticality – and prioritize remediation based on real risk rather than CVSS alone. Orca’s platform highlights affected assets directly in the “From the News” item view, helping security teams focus on the most critical remediation paths first.
Learn more
If you’re interested in learning more about the Orca Platform and how it can help you protect against vulnerabilities, schedule a personalized 1:1 demo.