The security industry has lived through several iterations of answering the question, “What security issue is most important to resolve?” Over the last 25 years, the focus has shifted from discovering what could hypothetically go wrong to what is most likely to be exploited by an attacker. Reachability analysis is the newest wave of security techniques to get clear on what security problems are most likely to be exploited.
Orca Security is the industry’s first cloud security platform to deliver Agentless Reachability Analysis with a distinct focus on what is at risk in production workloads.
The Orca Platform offers two types of reachability analysis for production workloads, combining exposure details with a clear view of what vulnerable software components are used in production with defined paths to exploit.
- Agentless Reachability Analysis for production workloads: Powered by patent-pending technology, detect what vulnerable packages are potentially executable in running workloads.
- Runtime Dynamic Reachability Analysis: Using Orca Sensor, detect which vulnerable packages are actually executed at runtime.
What is Reachability Analysis?
In the simplest terms, it’s a way of understanding if a vulnerable software component is being used when the application runs. It helps with more precise prioritization of risk and remediation because if a vulnerable package is running in production, then it’s actually “reachable” for an attacker to exploit.
To understand why reachability analysis is a major development that security teams should pay attention to, we need to look at how we’ve been tackling security risks over the past 25 years.
First came the CVE Program, created “to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities” with the Common Vulnerability Scoring System (CVSS) arriving soon after to numerically score the severity of vulnerabilities. This paired a constructive and standardized way to document what could go wrong with a numerical method to rate how terrible the impact could be.
Then the cloud radically shifted how applications got built. Open-source software rose in popularity, driving a completely new approach to building, and therefore securing, applications. The “Shift Left” movement took off with the ultimate goal to find and fix issues earlier in the build cycle of an application, widening the group of stakeholders who had a hand in resolving security problems.
Soon after, data security took the spotlight as security teams could finally speak about the impact of a compromise in terms their business partners could understand—customer data, customer trust, and revenue lost due to compromise. Eventually the Exploit Prediction Scoring System (EPSS) entered the stage to capture the likelihood of an exploit.
Advances in the last decade of application security have given us greater organizational and technical capabilities to catch security issues in pre-production, driven by a prevention mindset.
Cloud security advances have delivered broad and deep telemetry to what is live in production, with agentless approaches radically changing what could be seen in production environments and agents observing details on the runtime activity of an application.
While these advances help security teams identify more security risks and compliance gaps, we are still left with more alerts and issues overwhelming teams instead of clear paths to prioritization and remediation.
The Cyentia Institute shared research showing teams only have the capacity to remediate 1 in 10 vulnerabilities in their environment in a given month. The 2025 Open Source Security and Risk Analysis (OSSRA) report found that 97% of all applications evaluated for the report contained open source software.
Developers and security teams need a more defensible way to determine what gets fixed first. Reachability analysis aims to solve this problem.
Current Approaches to Reachability Analysis
There are two main types of reachability analysis in the market today:
- Pre-production static reachability
- Agent-driven dynamic reachability at runtime
Pre-production static reachability analysis
Most supply chain analysis and code scanning only provide a dependency tree, with direct and transitive dependencies, then point out which packages have vulnerabilities associated with them. This produces an overwhelming number of vulnerabilities to investigate and make a plan to remediate. It’s untenable.
Some Software Composition Analysis (SCA) vendors have extended their capabilities to see if the code actually calls vulnerable packages to be executed. Some vendors also determine if the specific function related to a CVE is being used.
Vulnerable packages that are coded to potentially be executed are considered more urgent to remediate because there seems to be a clear path to exploiting the vulnerable package. However, this type of reachability analysis merely hints at what could be high priority because it doesn’t operate from the full picture of what is live in production. It doesn’t actually answer the question of “What is truly exploitable?” This leads us to the second category of reachability analysis—dynamic at runtime.
Agent-driven dynamic reachability analysis at runtime
The logical way of answering the question, “What is truly exploitable?” is to observe what happens at runtime. Traditional agents have long been used to observe runtime activity, spot any anomalous behavior with vulnerable components, and address the threat as soon as possible. However, agents are usually expensive, time intensive to install and maintain, and can only see what’s happening on the resource they’re observing. The agent approach only shows a partial view of dynamic reachability at runtime across production workloads.
Many XDR or EDR vendors can extend their capabilities to this type of analysis, while emerging ADR vendors deliver this today.
These approaches still leave this critical question unanswered, “How do we figure out what vulnerable components are reachable in production workloads—at scale?”
Meet Orca’s Patent-Pending Agentless Reachability Analysis
Orca Security is the pioneer of agentless cloud security with our patented SideScanning™ technology delivering comprehensive visibility across your cloud estate. Now, Orca has patent-pending technology to deliver Agentless Reachability Analysis for production workloads. Security teams can zero in on what vulnerable components in production are potentially reachable, without the overhead of agents or any extra point solutions.
To complete Agentless Reachability Analysis, Orca’s SideScanning™ technology first takes snapshots and enumerates containers, among other cloud assets. We analyze the container entry script to generate a control flow graph and understand what packages are actively referenced and potentially executed. Then, Orca simulates code execution and analyzes configuration files to distinguish between reachable and unused packages.
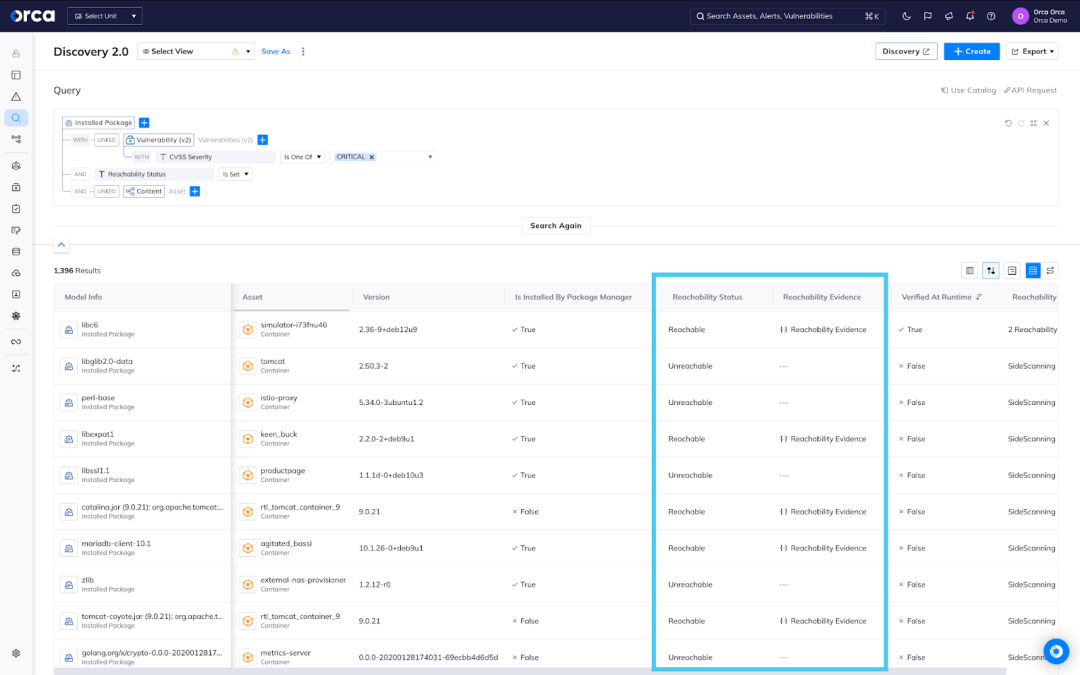
Orca will run a reachability check for every installed package found on containers in the SideScanning™ process, regardless if there is a vulnerability in the package. Orca shows the reachability status and evidence to demonstrate the path by which an attacker could reach the package. To filter down to the 10% of packages vulnerabilities that are potentially reachable, simply filter on the vulnerability model by criticality and the “Reachability Status” field.
Dynamic Runtime Reachability Analysis via Orca Sensor
Now what’s better than knowing what could potentially be executed in real-time? Knowing what is actually called and executed at runtime.
Since we already have a broad picture of static reachability for production workloads, we can focus runtime protection resources on your crown jewels. Orca Sensor, our lightweight, eBPF-based solution, will know what packages are actually being used at runtime and augment vulnerability findings with dynamic reachability details.
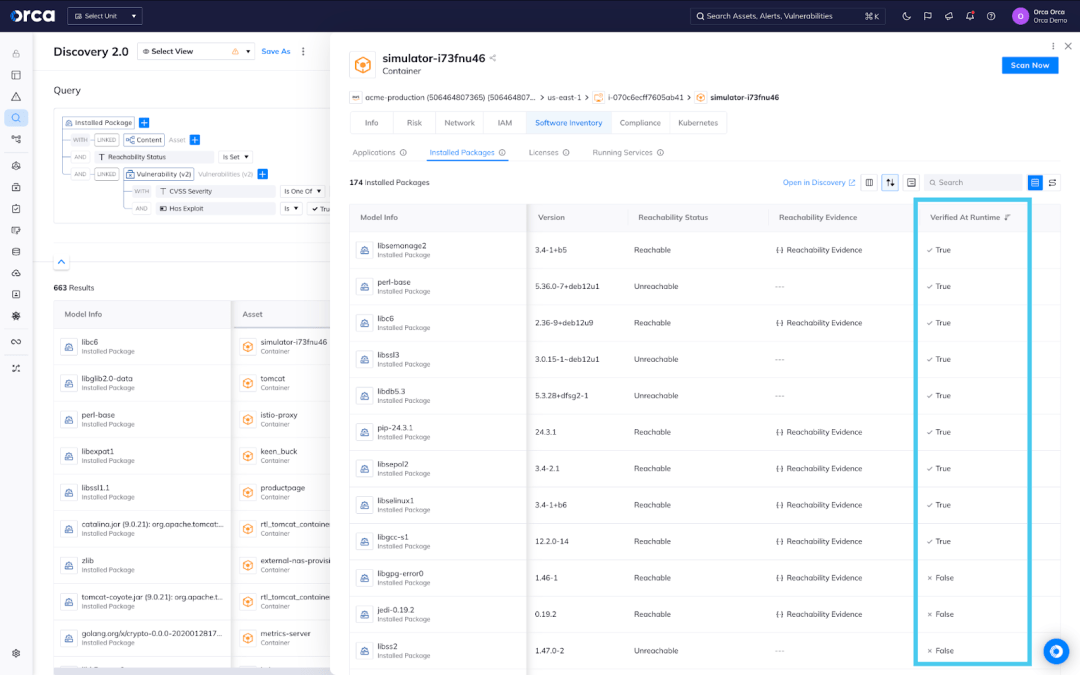
Orca Sensor enriches findings from Agentless Reachability Analysis by analyzing what is found in memory at runtime. Whether users take a comprehensive installed package inventory view or an asset-specific view, the fields for “Reachability Status”, “Reachability Evidence”, and “Verified at Runtime” are available to confirm what is “Reachable.”
Unified Reachability Analysis to Reduce Risk At Scale
With a distinct focus on what is reachable in production, the Orca Platform delivers the most scalable way to prioritize patching based on reachability of vulnerable packages. Out-of-the-box, Agentless Reachability Analysis helps your team understand which installed packages are potentially reachable by attackers, effectively reducing the amount of vulnerabilities to address by 90%. Orca Sensor enriches this data by verifying what is running in real time with Dynamic Reachability Analysis..
Command Your Cloud with Orca
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in seeing how the Orca Platform can help you command your cloud? Schedule a personalized 1:1 demo.






