Today, we’re excited to release the 2025 State of Cloud Security Report, which reveals deep insights uncovered by the Orca Cloud Security Platform across actual production environments and development pipelines. This year’s report reveals the most prevalent—and notable—cloud risks organizations face today, based on data, not theory.
Compiled by the Orca Research Pod, the report publishes analysis of billions of cloud assets on AWS, Azure, Google Cloud, Oracle Cloud, and Alibaba Cloud and hundreds of thousands of code repositories scanned by the Orca Cloud Security Platform. In this blog, we provide an overview of key findings, explore notable trends, and share expert recommendations for securing the cloud in the year ahead.
Key report findings
The Orca’s Report report presents key findings, including:
- More cloud innovation brings greater cloud risk.
As cloud adoption and cloud-native technologies expand, so too does the volume and severity of cloud risks. Nearly a third of cloud assets are neglected today, and each asset contains on average 115 vulnerabilities. Both are two data points among many others illustrating this troubling trend. - Attack surfaces are expanding—and risks are increasingly interconnected.
76% of organizations have at least one public-facing asset that enables lateral movement, turning a single risk into an opportunity for broader compromise. Security teams not only need to defend a growing attack surface, but increasingly interconnected risks. To illustrate, 36% of organizations have at least one cloud risk supporting more than 100 attack paths—giving attackers a direct route to endanger high-value assets. - Risks span the entire application pipeline.
Cloud security risks aren’t confined to runtime environments—they often originate earlier in the application development lifecycle. 85% of organizations have plaintext secrets embedded in their source code repositories. If a repository is exposed, attackers can extract the secrets to access systems, exfiltrate data, and more. Oversights such as these can compound risk across the cloud ecosystem. - Innovation is expanding attack surfaces—and the scale of cloud risks.
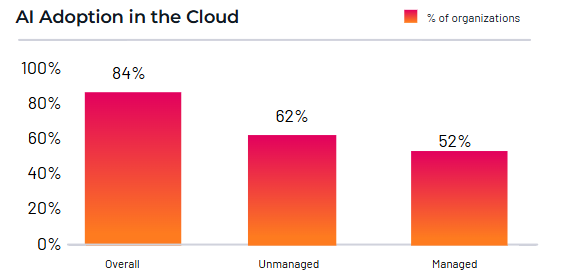
84% of organizations are now using AI in the cloud, introducing new risks, including AI-related CVEs that enable remote code execution. Kubernetes adoption adds further complexity—93% of organizations have at least one privileged service account, increasing the potential of a breach. Combined with growing multi-cloud adoption, these trends are reshaping the nature and scale of cloud security challenges.
The 2025 State of Cloud Security Report shows how the increased software development productivity that comes with using cloud services creates challenges of scale for security teams. Traditional exposures, like neglected cloud assets and exposed sensitive data, continue to grow. At the same time, new challenges are emerging—from the rapid rise of non-human identities to a growing number of AI-related vulnerabilities. The report sheds light on how security teams need to address the expanding attack surfaces for effective cloud security.”
Melinda Marks, Practice Director at Enterprise Strategy Group
AI continues to reshape the cloud security equation
AI adoption is increasing—84% of organizations now use AI in the cloud. But this innovation comes with new risks: 62% of organizations have at least one vulnerable AI package, and some of the most prevalent AI-related CVEs enable remote code execution. These trends demand a new approach to securing the cloud—one that accounts for innovation without compromising security.
Non-human identities are quietly (and quickly) expanding the attack surface
Non-human identities (NHIs)—digital identities assigned to machines, services, and automated processes—play a critical role in cloud and Kubernetes environments. But when overprovisioned or left unmanaged, they can significantly increase risk. According to our analysis, NHIs now outnumber human identities by an average of 50 to 1. Even more concerning, 78% of organizations have at least one IAM role that hasn’t been used in more than 90 days. These unused NHIs can serve as low-profile entry points for attackers, especially when tied to excessive permissions.
Traditional risks aren’t going away—they’re intensifying
Results from the report point to a surge in cloud risks across many well-established types. Consider sensitive data exposure: 38% of organizations with sensitive data in their databases also have those databases exposed to the public. That’s a significant increase from last year, and one that follows a trend of organizations storing more data, including sensitive data, in the cloud.
Data exposure expands an organization’s attack surface and makes it more attractive to attackers. Yet the problem doesn’t stop with data. Other cloud risks also continue to rise, including vulnerabilities, neglected assets, overpermissioned identities, and much more.
Industry insights: Risks by sector
Cloud risks are not a one-size-fits-all dilemma. Their prevalence and severity vary significantly by industry. To provide an accurate reflection of the state of cloud security, this year we broke down key findings by sector to show their relative impact.
Here are key industry findings from the report:
- Sensitive data exposure: Healthcare ranks as one of the industries most prone to sensitive data exposure. More than half (51%) of organizations with sensitive data in their databases also have them exposed to the public. Meanwhile, Media ranks #1 in terms of the percentage of organizations with publicly exposed storage buckets that have sensitive data in them (43%).
- Public-facing neglected assets: The Consumer and Manufacturing industry has the highest share of public-facing neglected assets, with 97% of organizations having at least one asset that fits this description. That industry is followed closely by Technology (94%) and Public Sector (92%).
Key recommendations: Embracing security by and for AI, unifying security, and protecting high-value assets
The report reveals eight recommendations for securing your cloud in 2025 and beyond. Below are three featured in the report:
Embrace security by and for AI
Organizations need cloud security capabilities that leverage and secure AI. The former provides teams with the automation and expertise they need to boost their productivity, capacity, and know-how. The latter enables organizations to secure their managed and unmanaged AI models, packages, and data—each a prime target for attackers.
Unify pre-deployment and runtime security
Security can’t stop at the CI/CD pipeline—or start at production. Organizations should look to adopt capabilities and visibility that span the entire lifecycle of an application, combining pre-deployment and runtime security into one cohesive and connected view.
Focus on protecting high-value assets
High-value assets such as storage buckets containing sensitive data or privileged identities must serve as a key focus of your security strategy. Use Attack Path Analysis to break risk chains before attackers can exploit them, and deploy real-time runtime security to protect against sophisticated attacks, such as in-memory attacks.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Cloud Security Platform? Schedule a personalized 1:1 demo.







