An ever-increasing number of vulnerabilities, coupled with the widespread use of third-party and open-source software components, makes the work of defenders increasingly difficult. Research suggests security teams can only address 10 percent of the vulnerabilities they encounter each month. Meanwhile, the cost of data breaches has reached an all-time high, with public cloud environments accounting for the highest total of any target.
The current and future state of cloud security demands an important shift in security teams’ favor. Orca’s Hybrid Reachability Analysis, combining both Agentless and Dynamic Runtime Analysis answers this need, providing defenders a new level of visibility and capability for enhanced risk prioritization, remediation, and much more.
In this blog, we examine Orca’s Dynamic Reachability Analysis capabilities in a technical deep-dive, exploring what it entails, why it matters, and how it can give your security teams a substantive advantage over adversaries.
What is dynamic reachability analysis?
Reachability analysis is a software security capability that determines whether a vulnerable software component is reachable and therefore exploitable by attackers. The question of reachability comes down to whether the vulnerable package is installed, loaded, and executed in runtime—or left unused, as often occurs with third-party and open-source components.
Reachability analysis answers this question in two ways: statically and dynamically. Static reachability analysis detects the vulnerable packages that could be executed in runtime and often occurs before applications reach production. Dynamic reachability, on the other hand, occurs in runtime and identifies the vulnerable packages that are actually executed in production.
While both technologies can help improve detection and risk prioritization, they can present key limitations based on the technologies and approaches used. Most static reachability analysis occurs in pre-production only, while many dynamic approaches rely on heavyweight agents that provide only partial visibility and demand significant resources.
Fortunately, Orca offers a revolutionary new approach that uniquely combines Agentless Reachability Analysis with fully integrated and lightweight Dynamic Reachability Analysis.
Why is Orca offering Dynamic Reachability Analysis?
Dynamic reachability analysis enables organizations to detect the vulnerable packages actually executed in runtime, enabling them to prioritize remediation efforts. It also enables them to detect some risks and threats that only surface in production, including malware and other exploits executed in memory.
While ADR, XDR, and EDR solutions all attempt to fill this need in various ways, they present important limitations. They all require a heavyweight agent installed on each production workload to monitor and protect it. They also call for time-intensive deployments, configurations, and maintenance, not to mention performance hits.
Orca’s Dynamic Reachability Analysis provides a lightweight, eBPF-based, and superior alternative to the agent-driven solutions on the market. Importantly, the feature offers advanced runtime telemetry and capabilities that deeply integrate with and extend the full coverage of Orca’s patent-pending Agentless Reachability Analysis feature. For a technical deep-dive on the latter, see our previous post.
Introducing Orca’s Dynamic Reachability Analysis
Orca’s Dynamic Reachability Analysis capabilities are powered by Orca Sensor, a lightweight eBPF-based runtime sensor. Sensor provides visibility into active, loaded, and potentially exploitable software components, enriching insights from Orca’s patent-pending Agentless Reachability Analysis with runtime context.
Orca’s Dynamic Reachability Analysis feature gives organizations immediate verification of agentless findings, greater visibility, and enhanced prioritization. The feature includes key capabilities, which we examine in detail below.
#1: Real-time verification and enrichment of agentless findings
Challenge: While agent-driven solutions can provide runtime verification of vulnerable packages in use, they present blindspots for every workload where an agent isn’t installed and call for significant resource overhead.
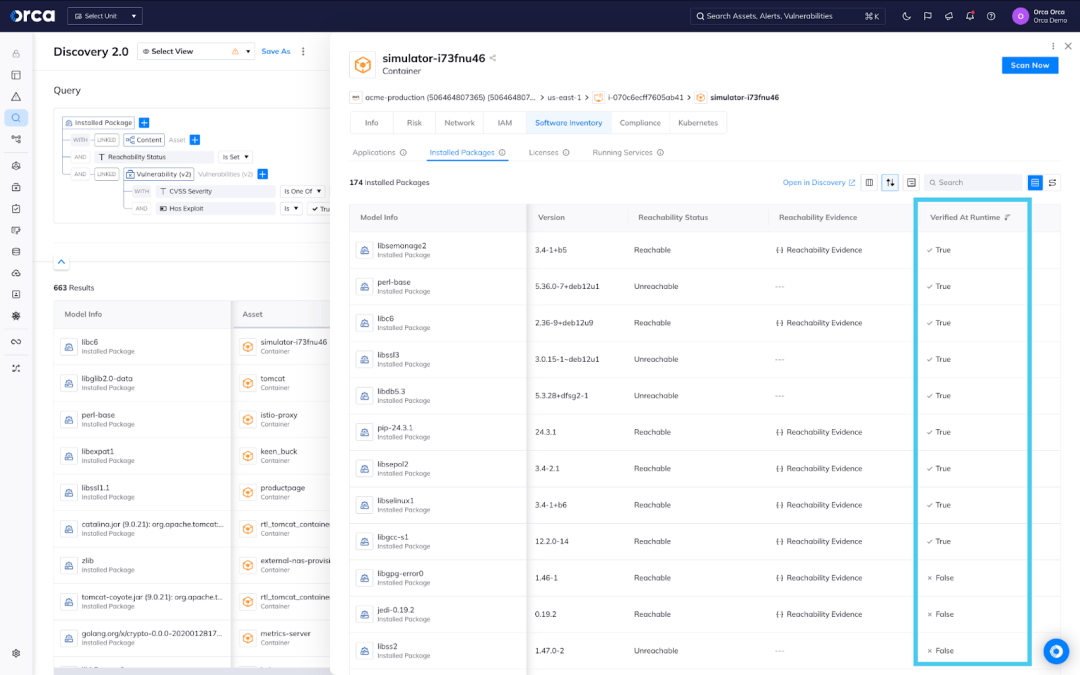
Solution: Orca’s Dynamic Reachability Analysis provides real-time verification and enrichment of Orca’s Agentless Reachability findings. Using the former, security teams can view real-time insights about the vulnerable packages detected through Orca’s patented SideScanning™ technology. This includes whether a vulnerable package is installed, loaded, and/or executed, the application or service using the vulnerable package, and its loaded file path. This enables teams to verify whether a vulnerable software component is reachable and potentially exploitable in runtime, increasing its priority while helping to reduce false positives.
#2: Unified view of agentless and real-time vulnerabilities
Challenge: To perform reachability analysis, security teams often rely on agent-driven tools that provide limited visibility into their cloud estate, or require the use of multiple point solutions (such as different tools for static and dynamic analysis). Both approaches present barriers in terms of visibility, as well as obstacles to fast and effective remediation and response.
Solution: The Orca Platform provides a single, unified view for all its capabilities, including Dynamic Reachability Analysis. Using Orca, defenders can view a full inventory of their vulnerable packages and easily filter them to view those detected agentlessly or dynamically, verified or not verified in runtime, and more.
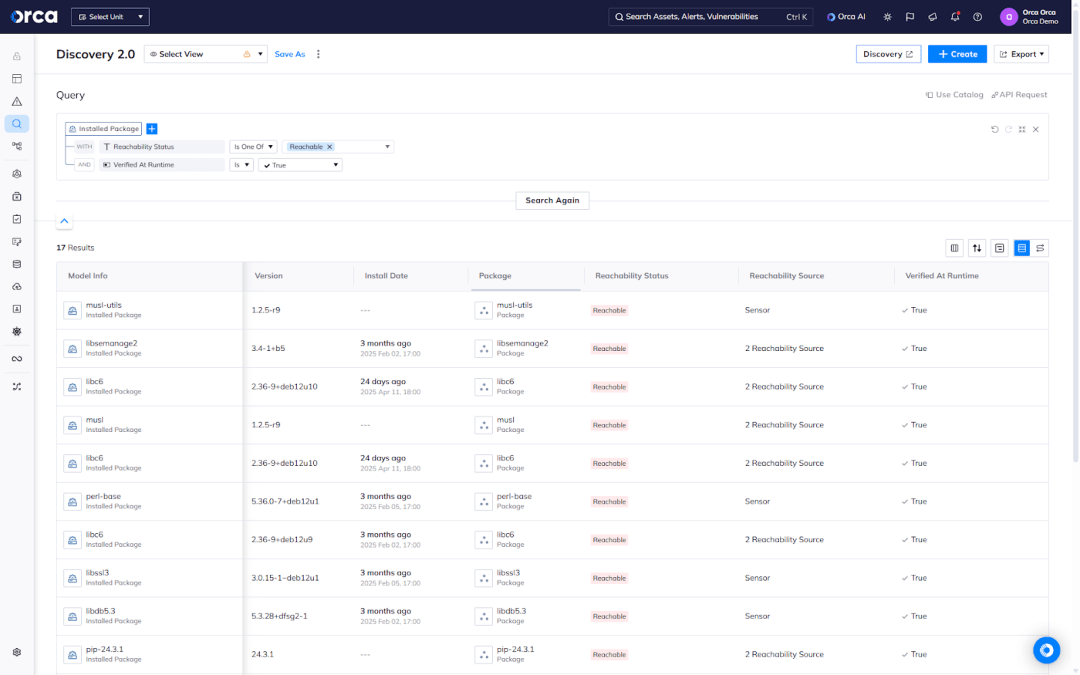
Additionally, Orca now enriches vulnerability-specific views with key reachability insights. When viewing a specific CVE page, for example, security teams can now see the runtime verification status of vulnerable packages associated with the CVE along with other Sensor metadata. This extends the advantages of Orca’s Reachability Analysis capabilities to additional views and workflows—and in a unified way.
About Orca
The Orca Cloud Security Platform is an open platform that identifies, prioritizes, and remediates security risks and compliance gaps across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Platform leverages our patented SideScanning™ technology to provide complete coverage and comprehensive risk detection. To see how this platform can work for your organization, schedule a personalized 1:1 demo.






