There are two key benefits for federal departments that choose a multi-cloud strategy. First, using multiple cloud providers can improve resilience by distributing workloads and de-risking downtime. Second, different agencies within the department can align their use cases to specific cloud provider strengths, like using Azure to integrate with the rest of the Microsoft suite.
However, employing a multi-cloud strategy comes with its own set of challenges. In this blog, we explore the three most common challenges and Orca’s approach to securing multi-cloud environments. The Orca Platform is FedRAMP® Moderate and GovRAMP authorized.
Challenge #1: Siloed accounts, tools, and data
Each cloud service provider has their own services to manage configurations, log events and activity, check for vulnerabilities and threats, enforce roles and entitlements, and monitor security across the workloads and cloud resources used in each account and project. As more agencies create cloud-native apps, more accounts and services get turned on, creating sprawl and inconsistent enforcement of controls across each cloud provider.
Siloed accounts create blind spots to risk, like neglected assets that were turned on and forgotten, inflating cloud costs. This sprawl of data across accounts and cloud providers also makes it difficult to discover the toxic combinations of risk that make the environment susceptible to compromise.
The Orca Approach: One place to see all risks across every layer of the cloud stack
Orca takes an agentless-first approach to deliver a comprehensive view of risks across multi-cloud environments, with the opportunity to organize each agency and team into their own business unit views. Security teams gain a clear line of sight into what is deployed in production, including cloud configurations, host OSes, AI models, container images, Kubernetes clusters, open-source components, and more.
The Orca Platform supports Zero Trust mandates by continuously monitoring for overly permissive cloud entitlements and uses machine learning to recommend optimized policy updates that efficiently address multiple risks. Agencies can integrate security across the full software development lifecycle by using the Orca Platform to scan code repositories (i.e. GitHub, GitLab, BitBucket, Azure DevOps), connect cloud risks to code origins, and monitor the security posture of their source code management tools.
Challenge #2: Too many alerts with no clarity around what to focus on first
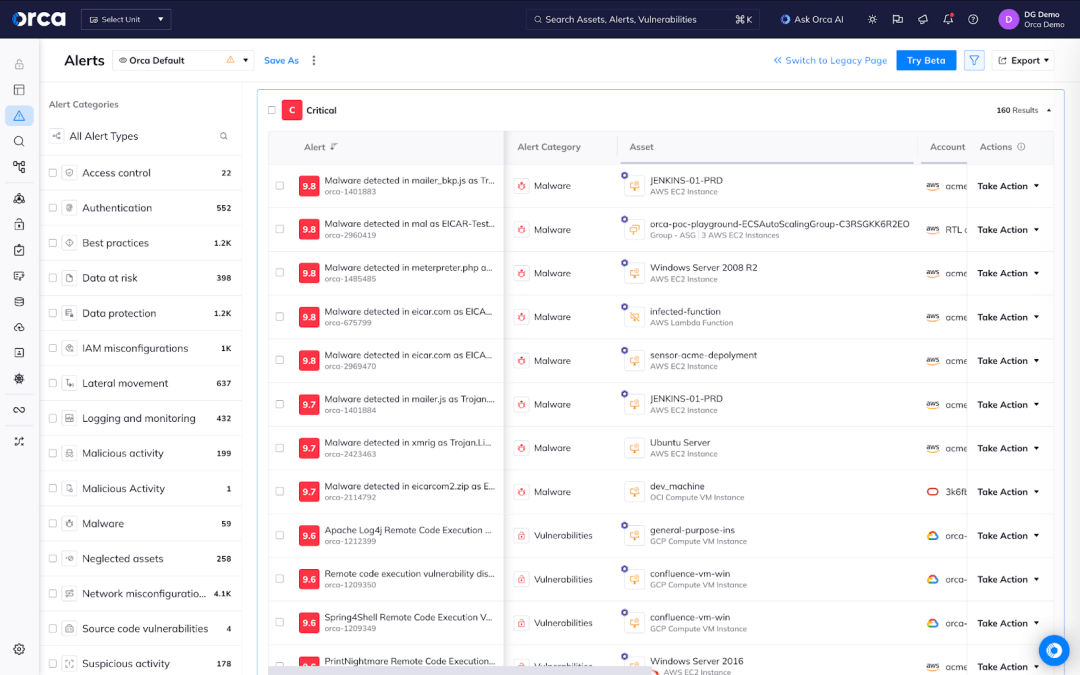
Security risks in multi-cloud environments span across misconfigurations, vulnerabilities, malware, overly permissive identities, secrets leaked in code, and more. There are many ways threat actors could take advantage of weak points in the multi-cloud environment, leading to an overwhelming number of alerts. Do security teams simply start with the vulnerabilities with high CVSS scores and known exploits? What about the risks that don’t have a CVE tied to it? Manually investigating risks takes time to model the threat and understand possible vectors threat actors could take. Agencies with limited time, resources, and knowledge of the cloud require better prioritization of risk to ensure sensitive data and systems are properly protected from nation-state actors.
The Orca Approach: Dynamic risk prioritization based on asset context and attack path analysis
Because Orca aggregates information across your multi-cloud environment into one Unified Data Model, the Orca Platform can provide an opinionated view of risk. Orca dynamically prioritizes risk in two key ways—attack path analysis and numerical risk scores. In the Orca Platform, users can manually mark what assets they consider to be their crown jewels. However, Orca also performs its own analysis of assets that could be considered crown jewels based on factors like PII or secrets detected. Orca then analyzes possible attack paths by combining different risks and scores these paths based on probability and business impact. Security teams can focus remediation efforts by looking at the most critical attack paths and plan mitigation steps around interrupting the attack chain.
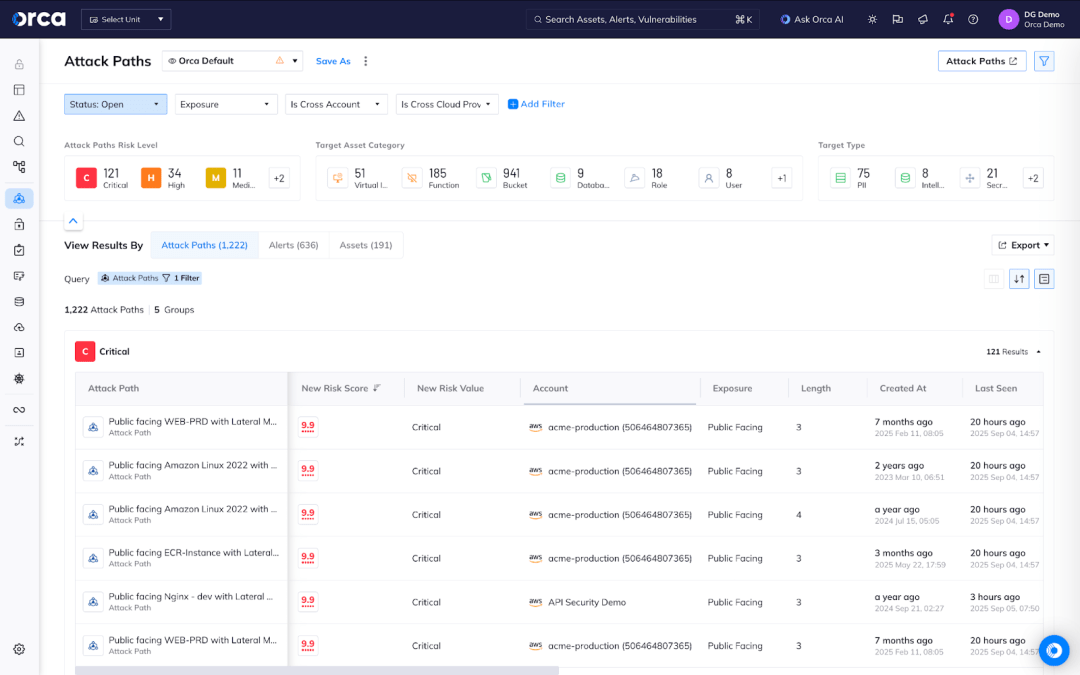
Security teams can also focus remediation efforts by sorting alerts according to their numerical risk scores. These scores are dynamically updated according to a number of factors, including:
- how many attack paths are associated with the alert,
- the asset context (e.g. is the asset running or marked for deletion),
- exposure information (e.g. is it publicly accessible),
- what sensitive data is at risk, and
- standard CVSS and EPSS scores
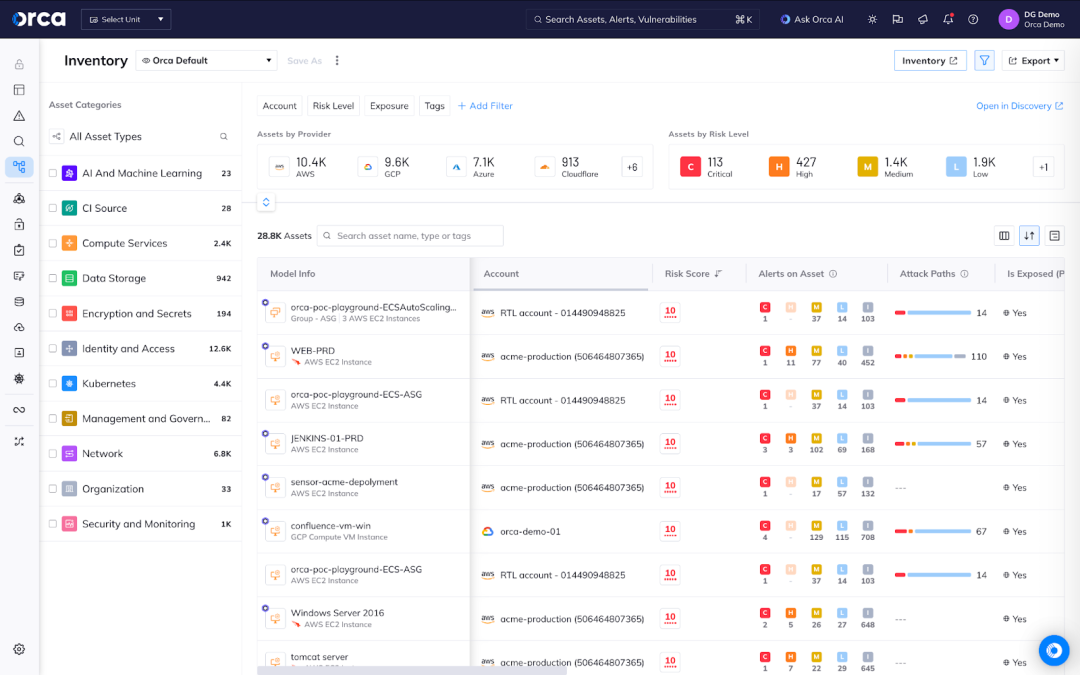
If security teams want to focus remediation with an asset-based view, all assets in the inventory are also assigned a risk score. These scores are calculated according to the number of alerts on the asset and their severity levels.
Challenge #3: Manual overhead to collect and share risk context with the right people
When federal departments employ a multi-cloud strategy, security is a shared responsibility between the cloud provider and the federal department. It is also a shared responsibility between the security team and the end users of the cloud resources within the federal department (i.e. developers, DevOps, data scientists, etc).
Security teams are held accountable to mitigate risk, but the steps to implement risk remediation are often carried out by the end users. Additionally, depending on internal agreements between functional groups, there may be some division of responsibility between what assets the security team is accountable for and what assets are fully managed by the end users. This business logic doesn’t always transfer to system-level clarity of ownership, so security teams spend an inordinate amount of time hunting down the root cause of risks, finding the right team members to fix the issue, and managing the alert lifecycle, ultimately delaying the desired outcome—remediated risk.
The Orca Approach: Streamlined workflows with robust integrations and automation
The Orca Platform is committed to building an open ecosystem so that intelligence from Orca can be delivered directly to the people who need the context to make informed decisions. The Orca Platform has robust bi-directional integrations with ticketing systems like Jira and ServiceNow where admins have the flexibility to create templates of what data flows into tickets for different projects and teams. Admins then set up automation for a group of Orca alerts to create tickets with those templates and automatically close out tickets when alerts are properly resolved and verified.
The Orca Platform also has integrations to share data with SIEMs like Splunk, as well as SOAR platforms like Tines. The Orca Platform can also pull in data from sources like Chainguard, Snyk, Cloudflare, and more to augment the intelligence that Orca delivers with its opinionated view of risk. Take a look at our integration directory to see how Orca can plug into workflows you’ve already created to address risk in your cloud environment.
Command Your Cloud with Orca
The Orca Platform is FedRAMP® Moderate and GovRAMP authorized. Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Cloud Security Platform? Contact Orca Security’s government team today to learn how we can help you thrive securely in the cloud at fedrampsales@orca.security.





