This week, three new high-severity vulnerabilities were revealed in runC, the fundamental runtime technology used by most container platforms. This impacts major systems such as Docker, containerd, Kubernetes, and virtually all managed Kubernetes services offered by major cloud providers.
These vulnerabilities combined allow for a container escape, where a malicious factor can break out of the container’s bound and affect the host system directly.
What is runC?
runC is a lightweight, low-level container runtime that directly interfaces with Linux kernel features like namespaces and cgroups to create and run containers. It’s the reference implementation of the Open Container Initiative (OCI) specification, used by higher-level tools like Docker and containerd to actually start containers. Because it operates so close to the kernel, vulnerabilities in runC can lead to serious security risks such as container escapes or host compromise.
How do these vulnerabilities work?
CVE-2025-31133 — runC relies on bind-mounting /dev/null to “mask” sensitive host files. A vulnerability exists where an attacker can exploit the container initialization process by replacing /dev/null with a symlink. This manipulation can cause runC to bind-mount an attacker-controlled target read-write into the container, allowing writes to /proc and potentially leading to a container escape.
CVE-2025-52565 — A vulnerability exists where the /dev/console bind mount can be exploited through races/symlinks. This manipulation allows runc to mount an unexpected target inside the container before security protections are fully in place. Consequently, this can grant write access to critical procfs entries, potentially leading to container breakouts.
CVE-2025-52881 — runC is vulnerable to a flaw that allows an attacker to redirect writes intended for /proc to arbitrary, attacker-controlled locations. This vulnerability can be exploited to achieve arbitrary writes to sensitive files, such as /proc/sysrq-trigger, bypassing LSM relabel protections in certain configurations.
Exploitability
In order to exploit these vulnerabilities the attacker must be at a starting point of having the ability to start containers with custom mount configurations, which can be achieved through malicious container images or Dockerfiles.
From here, by combining these 3 vulnerabilities, the attacker can trick runC to write to the host’s /proc filesystem instead of the container’s view of it. This means the attacker can get execution rights on the host, cause a full cluster outage and maintain persistence beyond the container lifecycle.
So am I vulnerable?
The versions of runC that are vulnerable:
- CVE-2025-31133, CVE-2025-52881—all runC versions are vulnerable
- CVE-2025-52565—versions 1.0.0-rc3 and later
Fixes are available in runC versions 1.2.8, 1.3.3, 1.4.0-rc.3, and later.
Mitigation
In order to mitigate this vulnerability there is a need to update runC to the patched version ASAP. But, this vulnerability highlights an issue container users tend to ignore. If you use a container running a code you didn’t write yourself, assume it can be broken through.
There are several precautions that can be taken in order to reduce the risks of using “untrusted” containers:
- Avoid from running unsigned/untrusted container images
- Refrain from giving unnecessary permissions to clusters
- Monitor behavior of risky containers
- Isolate possibly problematic environment
How Orca can help
The Orca Cloud Security Platform enables organizations to identify, prioritize, and remediate cloud security risks across multi-cloud environments spanning AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. This includes detecting vulnerabilities in foundational container runtime technologies such as runC, which powers Docker, containerd, and most managed Kubernetes services. The Orca Platform offers comprehensive features to help you protect your containerized workloads and prevent potential container escapes.
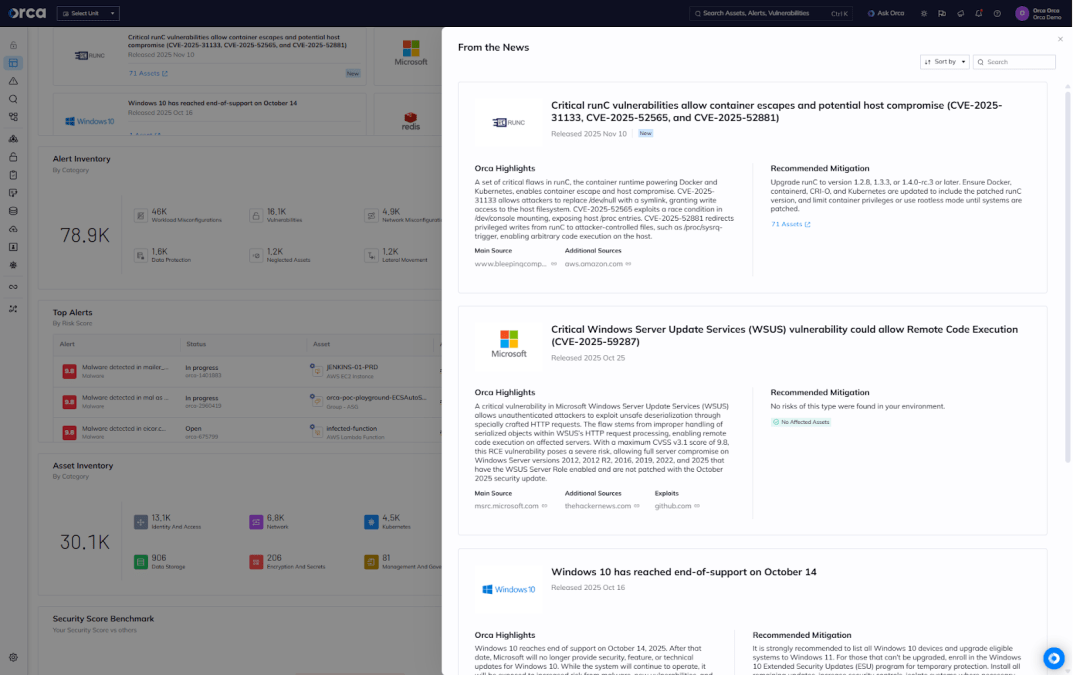
The Orca Platform displays trending vulnerabilities in the “From the News” widget on the Orca dashboard. Users can immediately see if their environment is exposed to any of the runC CVEs and receive clear guidance on remediation steps.
Command your cloud with Orca
The Orca Cloud Security Platform is an open platform that identifies, prioritizes, and remediates security risks and compliance gaps across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Platform leverages our patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn more
To see how the Orca Platform can work for your organization, schedule a personalized 1:1 demo.