Table of contents
- What is DSPM?
- Core Components of DSPM
- The impact of DSPM on cloud data security
- DSPM implementation and best practices
- Addressing the security execution gap with DSPM
- Case studies and real-world DSPM applications
- DSPM is only one part of comprehensive cloud security
- Conclusion
- About Orca Security
- Data Security Posture Management FAQs
Do you know that feeling of accomplishment after migrating your data to the cloud? Freedom, flexibility – the possibilities seem endless. But then, a niggling worry creeps in. Where exactly is all that sensitive information stored? Who has access? How can I control such scattered data across the cloud? One wrong configuration and – boom! – a data breach disaster. This is because you are trying to duct tape together point solutions for each part of data security posture management (DSPM), leaving dangerous gaps attackers happily scurry through.
What you need is a solid DSPM strategy to rein in the data chaos. DSPM gives you continuous visibility into your data stores, what they contain, who can access them, and which data is most at risk across your clouds. Then it helps you take action to reduce your attack surface before you become another data breach statistic. However, not all DSPM solutions are created equal. The right one equips you with essential capabilities like automated data discovery, unified data intelligence, and seamless integration without requiring extra tools.
Ready to take control of your cloud data security? Let’s break down everything about DSPM, why it’s vital for securing your cloud data in 2024, and how to pick the best solution for defending your dynamic data estate.
What is DSPM?
Data security posture management (DSPM) is a cybersecurity approach to managing risks related to sensitive data in the cloud. As more organizations migrate data and workloads to the cloud, traditional security measures are no longer sufficient. While the cloud offers scalability and agility, it also introduces complexity. Sensitive data may be spread across infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) in public, private, and hybrid clouds. DSPM helps address the security execution gap by providing centralized visibility and control over data in these diverse, dynamic environments.
DSPM solutions empower security teams to implement or adjust security controls like firewalls, access controls, and IPS configurations. This ensures data protection across cloud environments. These solutions leverage intelligent automation for regular testing and auditing. This automation streamlines the process of identifying potential vulnerabilities and helps organizations maximize their overall cloud data security posture.
The benefits of DSPM are extensive. It helps reduce the risk of data breaches by giving security teams full visibility into their sensitive data, access control, and cloud risks. DSPM also enhances regulatory compliance by enabling organizations to locate, classify, and monitor sensitive data subject to privacy laws.
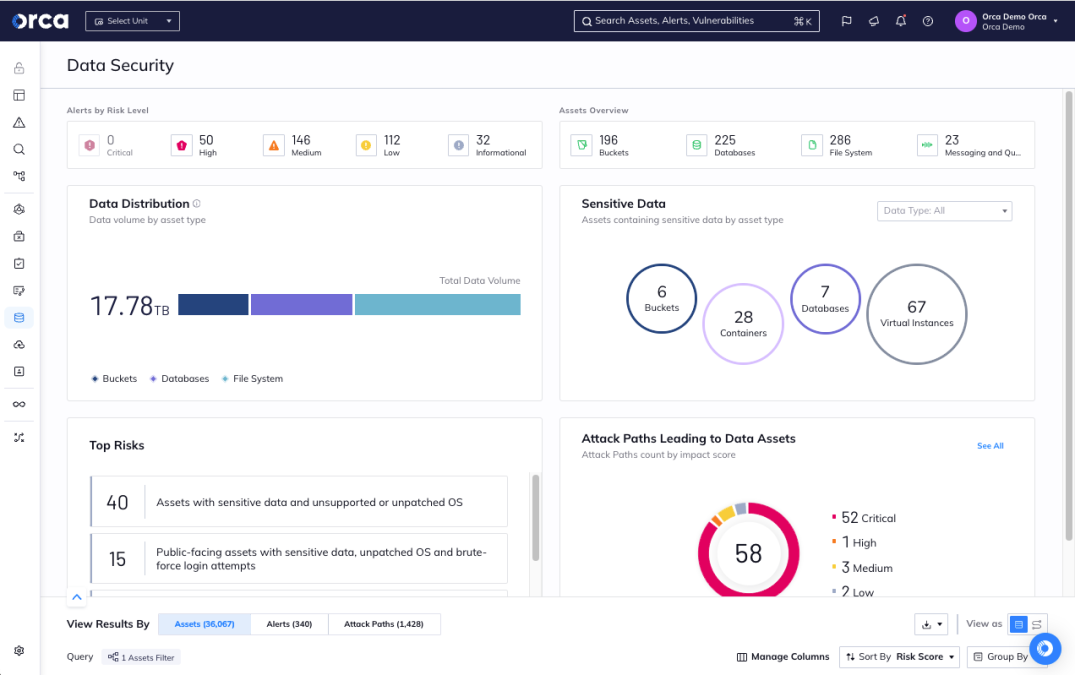
DSPM goes beyond traditional data security tools like data loss prevention (DLP) or cloud security posture management (CSPM). While DLP focuses on data in motion and CSPM analyzes cloud configuration risks, DSPM provides a holistic view of data security across infrastructure and access vectors. Some of the core capabilities of DSPM solutions include:
- Data discovery: Identifying where sensitive data resides across cloud environments. This includes classifying data by level of sensitivity and risk.
- Access control: Managing access to sensitive data and enforcing least privilege permissions.
- Continuous monitoring: Real-time monitoring of data risks and compliance violations. DSPM solutions generate actionable risk telemetry for efficient remediation.
- Risk assessment: Evaluating data security risks and prioritizing remediation efforts. This helps organizations address the highest risks first based on data sensitivity and exposure.
Implementing DSPM requires significant effort and resources. However, the payoff can be huge in reducing data breach risks, ensuring compliance, and enabling data-driven business innovation. With the right strategy and tools in place, organizations can make big strides in securing their most valuable data assets across increasingly complex cloud environments. While DSPM is not a silver bullet, it is a critical capability for cloud-first organizations who are serious about data protection.
Core Components of DSPM
To effectively manage your data security posture, you’ll need visibility into all your sensitive data and how it’s accessed. DSPM solutions provide this through several key components.
1. Data discovery
Continuous data discovery allows DSPM to locate where your sensitive data resides across all your cloud environments. Without discovery, you have no chance of securing data you don’t even know exists! DSPM uses machine learning and behavioral analysis to automatically find sensitive data wherever it lives.
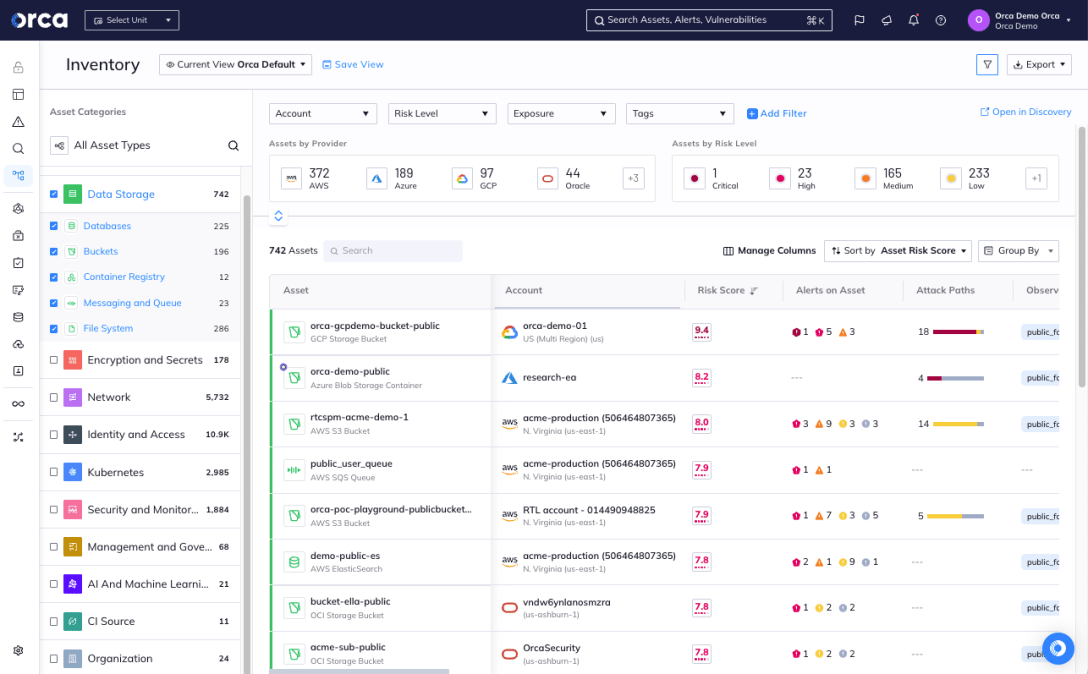
2. Data classification
Once data is discovered, DSPM classifies it based on sensitivity level, such as public, internal, confidential, or restricted. Classification helps determine appropriate security controls and access restrictions for your data.
3. Access control
DSPM manages least-privilege access control, ensuring that only the required users can access the data. It also monitors for suspicious access patterns that could indicate compromised credentials or insider threats.
4. Continuous monitoring and risk assessment
DSPM doesn’t just get you visibility into your data security posture at a single point in time. It continuously monitors your data environments to detect vulnerabilities, policy violations, and misconfigurations that could put sensitive data at risk. DSPM platforms use machine learning and behavioral analytics to evaluate risks in real-time so you can take action quickly.
5. Remediation
The final component of DSPM is remediating any issues detected during monitoring and risk assessment. This could include revoking unnecessary user access, encrypting sensitive data, or fixing vulnerable systems. Automated remediation can even fix some simple issues without any human intervention.
The impact of DSPM on cloud data security
DSPM is essential for securing sensitive data in today’s multi-cloud world. By reducing risks, strengthening compliance, and enabling governance, DSPM helps organizations protect their data, finances, and reputations from threats in increasingly complex IT environments. Below is a breakdown of the impact of DSPM on cloud data security.
1. Reducing risks from data breaches
Data breaches expose sensitive data, damaging trust and costing millions. DSPM discovers data and access risks, allowing teams to remediate them before breaches occur. Continuous monitoring also detects breaches early, minimizing damage. According to an IBM report in 2023, the global average cost of a data breach is $4.45 million. DSPM reduces breach risks and associated costs.
2. Strengthening compliance
Regulations like GDPR, HIPAA, and PCI DSS require managing access controls and monitoring sensitive data. However, compliance is challenging in dynamic cloud environments. DSPM provides visibility and control over sensitive data to meet compliance mandates. It allows classifying data, enforcing access policies, and monitoring risks to stay compliant even as cloud resources change.
3. Enhancing data governance
Effective data governance relies on understanding what data you have and who can access it. DSPM catalogs sensitive data across clouds, classifies it by sensitivity, and shows who has access. This helps establish data ownership, set security policies, and ensure compliance with privacy regulations. Data governance is critical as organizations adopt cloud services, and DSPM provides the visibility to govern data properly.
DSPM implementation and best practices
With the right strategy and tooling in place, DSPM can help secure your data in the cloud and close the security gap for good. Here are some of the best practices you can employ to implement DSPM, stay ahead of threats, and help you achieve data protection at scale.
Start with discovery
The first step to implementing DSPM is gaining full visibility into your data landscape. You need to uncover where all your sensitive data resides across cloud services, databases, and data stores. Look for a solution that uses innovative scanning techniques to provide complete cloud coverage and full data inventory – without requiring agents or APIs.
Assess your risks
Once you have a data map, you can determine your level of risk. Look at factors like data classification, access control, and security misconfigurations across environments. A good DSPM tool will automatically analyze risks and provide actionable insights to prioritize remediation.
Remediate high-risk issues
With risks identified, you can get to work fixing problems. Start with your highest risks like open databases, overly permissive access controls, or unencrypted sensitive data. Look for a DSPM solution that not only finds risks but also provides automated remediation and guided remediation leveraging generative AI.
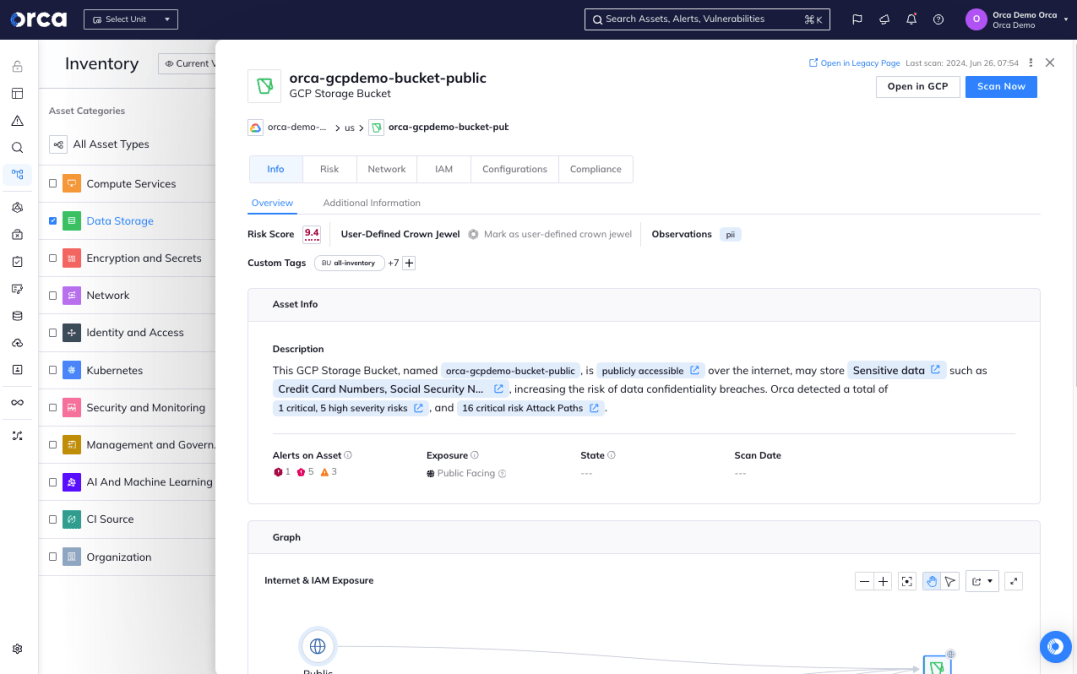
Continuously monitor
Even after initial remediation, new data stores, access changes, and vulnerabilities emerge constantly. Effective DSPM requires ongoing monitoring to detect deviations from your security policies in real time. Look for a solution that provides continuous discovery and risk assessment to give you 24/7 visibility and protection of your cloud data.
Define key capabilities
As you evaluate DSPM solutions, look for key capabilities like:
- Automated data discovery across all cloud data stores
- Risk-based data classification and sensitivity labeling
- Access control monitoring and anomaly detection
- Automated remediation of common misconfigurations
- Integration with cloud security tools like CSPM, CWPP, and CIEM
- Compliance reporting for regulations like GDPR, HIPAA, PCI DSS
Addressing the security execution gap with DSPM
Cloud environments are dynamic, diverse, and complex—presenting many challenges for data security. The security execution gap refers to the difference between an organization’s data security intentions or policies and their ability to actually execute and implement those policies. DSPM helps bridge this gap by providing continuous visibility and control over sensitive data in the cloud.
With DSPM, you gain insight into where your data resides across clouds, how it’s accessed, and who has privileges. This helps you understand your data risk exposure and prioritize remediation efforts. Say your organization has a policy restricting access to financial data, but without DSPM, you have limited visibility into whether that policy is truly being enforced. DSPM tools automatically discover your data, monitor for policy violations, and alert you to take action.
Continuous monitoring
DSPM doesn’t stop at initial data discovery. It continuously monitors your environment for changes that could impact your security posture. If a new data store is provisioned or a user’s access is modified, DSPM detects these changes in real time. This constant vigilance is essential for data security in the cloud where resources are ephemeral.
Risk-based prioritization
Not all data is equally sensitive, and not all policy violations pose the same level of risk. DSPM evaluates risks based on factors like data classification, user access, and environment. It identifies your high-risk data so you can focus remediation efforts where they matter most.
Automated remediation
The security execution gap often comes down to limited resources and too many manual processes. DSPM incorporates automation to help streamline data protection at scale. It can automatically remediate certain issues like removing unauthorized user access or encrypting unprotected data stores. This frees up your security team to focus on higher-level initiatives rather than repetitive tasks.
Case studies and real-world DSPM applications
PII data breach prevention
One successful DSPM implementation was by a healthcare organization with sensitive patient data in the cloud. They used automated data discovery to identify over 15,000 unsecured patient records across cloud storage services. By applying access controls and encryption, they reduced their risk of a HIPAA violation and data breach.
Compliance risk remediation
A multinational bank needed to meet data privacy regulations across regions. Their DSPM solution provided visibility into sensitive data locations, ownership, and access. This allowed them to restrict unauthorized access, delete unused data, and apply region-specific controls. Within months, they achieved and maintained compliance with GDPR, CCPA, and other laws.
Reducing cloud data risk
A tech company wanted to move petabytes of data to the cloud while maintaining security. With a CNAPP platform including DSPM, they gained visibility into data risks from misconfigurations, weak access controls, and vulnerabilities. Continuous monitoring and guided remediation allowed them to find and fix issues quickly. They migrated data with confidence, knowing their sensitive data was secured according to policy.
Consolidating cloud security tools
Rather than manage separate DSPM, CWPP, and CIEM tools, a CNAPP offers integrated data security in one platform. One company used a CNAPP to replace their existing data discovery, access management, and vulnerability scanning point solutions. With a single pane of glass, they gained end-to-end visibility and control over data risks. And by eliminating tool sprawl, they optimized resources and reduced costs.
DSPM is only one part of comprehensive cloud security
If you’re securing data across multiple clouds, DSPM tools are essential but not enough on their own. As cloud environments grow increasingly complex, the trend is consolidating key cloud security capabilities into a single platform known as CNAPP (Cloud-Native Application Protection Platform). Here are some of the capabilities that CNAPP solutions offer:
A CNAPP platform integrates must-have cloud security tools
Rather than juggling a bunch of separate point solutions, a CNAPP brings together tools like cloud security posture management (CSPM), data security posture management (DSPM), threat detection, and more. This integrated approach gives you a comprehensive view of risks across your cloud infrastructure and workloads.
A CNAPP boosts visibility and control
With a CNAPP, you gain real-time visibility into the security of your cloud resources, sensitive data, configurations, and access controls. Armed with this visibility, you can take quick action to remediate risks, enforce policies, and tighten security controls. A true CNAPP should also offer “single pane of glass” management, allowing you to centrally monitor and manage security across all your cloud environments and understand how different risks can be combined into dangerous attack paths.
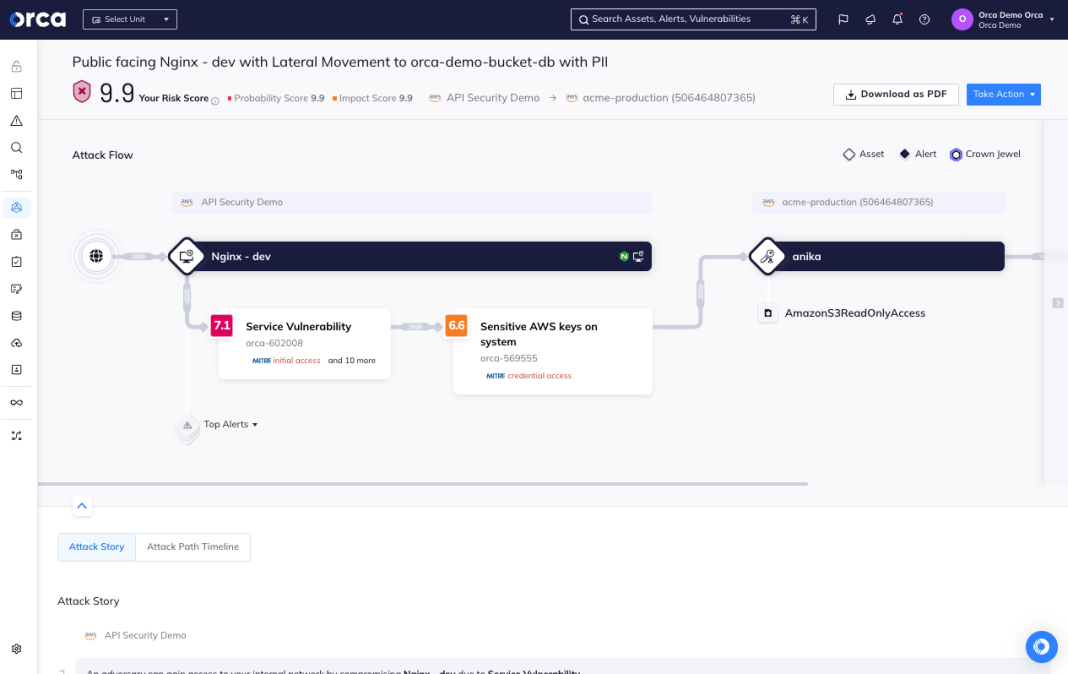
Cost and time savings
Managing fewer tools means lower costs for licensing, maintenance, and resources to deploy and operate them. It also minimizes the time spent integrating tools and reconciling conflicting insights or controls. With a CNAPP, you can focus on using security data to improve your cloud risk posture rather than wrangling a bunch of tools.
Conclusion
As organizations adopt multi-cloud and cloud-native architectures, data is scattered across environments, creating major security challenges. Data Security Posture Management (DSPM) tools help gain continuous visibility into sensitive data, access, and risks across clouds.
However, many existing DSPM solutions lack key capabilities like automated data discovery, risk prioritization, and integration with other cloud security tools.
Orca Security offers a Cloud Native Application Protection Platform (CNAPP) that provides DSPM and additional cloud security capabilities in a single solution. The Orca platform discovers and protects data across environments using machine learning without requiring agents. It identifies sensitive data and access risks, prioritizes issues based on severity, and provides remediation guidance to reduce exposure.
About Orca Security
Orca Security’s CNAPP platform consolidates key cloud security tools – DSPM, CSPM, CWPP, and CWP – providing a comprehensive yet simplified approach to data protection and compliance. The Orca CNAPP platform offers:
- Agentless data security posture management: Continuously discover, classify, and monitor sensitive data across clouds. Gain actionable insights into access risks and data exposure.
- Cloud security posture management: Identify misconfigurations and compliance risks across environments. Receive prioritized remediation guidance based on severity.
- Cloud workload protection: Detect vulnerabilities, malware, and anomalies in cloud workloads and containers in real-time. Respond quickly to threats targeting cloud-native applications.
- Container security: Monitor containers and Kubernetes environments for risks related to configurations, images, network policies, and more. Enforce policies to reduce the attack surface.
By consolidating multiple tools into a single platform, Orca Security provides an efficient solution to manage data security, compliance, and cloud risks. The Orca CNAPP platform helps organizations strengthen data protection, reduce exposure, and gain continuous compliance across dynamic cloud environments. Schedule a 1:1 demo to see how Orca can take your cloud security to the next level.
Data Security Posture Management FAQs
Data security leaders often have questions about Data Security Posture Management (DSPM) and how to implement it. Here are some of the most frequently asked questions and answers:
What differentiates CNAPP from DSPM?
CNAPP stands for Cloud-Native Application Protection Platform. While DSPM focuses specifically on securing data across environments, CNAPP takes a broader approach to cloud security. In addition to DSPM capabilities like data discovery and classification, CNAPP also provides workload protection, container security, API security, AI security posture management, and more. Some CNAPP solutions, like Orca Security, also fully integrate DSPM functionality.
What is the difference between DLP and DSPM?
Data Loss Prevention (DLP) tools are designed to detect and prevent potential data breaches and exfiltration. DSPM has a wider scope, continuously monitoring data security risks and posture across environments. DSPM leverages DLP data discovery capabilities but also assesses access control, data classification, and risk. DSPM can incorporate DLP tools as part of its broader data protection strategy.
How does DSPM enhance multi-cloud security?
DSPM gives organizations visibility into sensitive data distributed across multiple public clouds, private data centers, and SaaS apps. By discovering, monitoring, and remediating risks in diverse environments, DSPM helps close security gaps that would otherwise remain invisible. DSPM also simplifies compliance in multi-cloud environments by providing a single pane of glass into data governance controls.
What are the steps in deploying a DSPM strategy?
The steps in implementing DSPM are:
- Discover and catalog where sensitive data resides across your environments.
- Classify data by importance and sensitivity.
- Evaluate access controls and ensure the least privileged access to sensitive data.
- Continuously monitor environments for data security risks and changes.
- Remediate any identified issues to reduce risk.
- Define key data security metrics and KPIs to measure your security posture over time.
How do you measure data security posture?
Key metrics for evaluating data security posture include:
- Percentage of sensitive data discovered and classified
- Number of data stores with excessive access or weak authentication
- Time to discover and remediate critical data security risks
- Compliance with data protection regulations and policies
- Trends in data risk assessments over time
Continuous monitoring and improvement of these metrics help strengthen your overall data security posture. DSPM solutions can provide reports and dashboards to track these KPIs across your organization.
Table of contents
- What is DSPM?
- Core Components of DSPM
- The impact of DSPM on cloud data security
- DSPM implementation and best practices
- Addressing the security execution gap with DSPM
- Case studies and real-world DSPM applications
- DSPM is only one part of comprehensive cloud security
- Conclusion
- About Orca Security
- Data Security Posture Management FAQs




