On March 21, 2025, a major security incident was reported by CloudSEK involving Oracle Cloud’s authentication systems. A threat actor, “rose87168,” claimed to have stolen 6 million records, impacting over 140,000 tenants. The stolen data allegedly includes JKS files, encrypted SSO and LDAP passwords, and JPS keys. The attacker is demanding payments from affected organizations to prevent further exposure. Affected organizations should take immediate action to assess their security posture and implement necessary safeguards.
In this post, we examine the details of the incident, what steps you should take to protect your organization, and how the Orca Cloud Security Platform can help.
Detailed overview
The breach was detected when “rose87168” advertised the stolen records on a dark web forum. The attacker claimed to have exploited a vulnerability (CVE-2021-35587) in Oracle Cloud’s login infrastructure, specifically targeting the endpoint login.(region-name).oraclecloud.com. The compromised data reportedly includes:
- Java Key Store (JKS) files: Stores cryptographic keys and certificates for Java applications.
- Encrypted SSO passwords: Used for Single Sign-On; compromise may allow unauthorized access.
- Encrypted LDAP passwords: Used for directory authentication; compromise may allow unauthorized access.
- Enterprise Manager JPS keys: Manage access and encryption in Oracle Enterprise Manager.
The attacker is demanding organizations pay for data removal. Despite these claims, Oracle maintains that their systems remain secure and no customer data has been leaked. It’s also important to note that both the SSO and LDAP credentials are reported to be encrypted, which means they wouldn’t be of value to attackers until they can be decrypted. The attackers have reportedly offered a bounty for anyone that can decrypt them.
Recommended mitigation and response
Organizations using Oracle Cloud should take the following actions:
- Reset credentials: Immediately reset passwords, especially for privileged accounts, and enforce strong password policies with multi-factor authentication (MFA).
- Monitor for suspicious activity: Deploy security monitoring tools to detect unauthorized access or unusual behavior.
You can view additional recommendations in the original report.
This incident highlights the persistent threats facing cloud environments and the high stakes for organizations relying on cloud infrastructure. Adopting strong security practices, including regular assessments, access controls, and proactive threat monitoring, remains essential in mitigating risks.
Securing Oracle Cloud with the Orca Platform
The Orca Cloud Security Platform provides full visibility in your Oracle Cloud Infrastructure (OCI) accounts and continuously checks for misconfigurations to ensure controls are set securely and comply with best practices and industry and regulatory standards. Using the Orca Platform, you can receive prioritized alerts to identify all of your OCI accounts, along with AI-driven and assisted remediation capabilities to address issues and accelerate your mean time to resolution (MTTR).
The Orca Platform also displays trending vulnerabilities in the “From the News” widget of the Orca dashboard. Here, you can see if their environment is affected by the security breach and get recommended mitigation instructions.
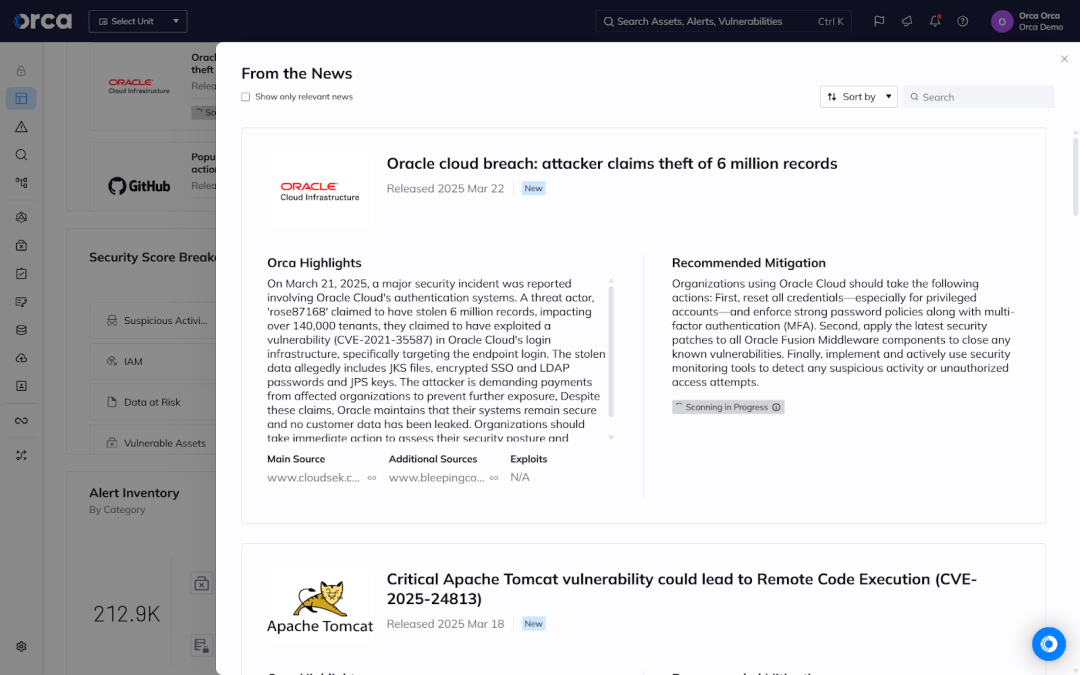
To find out if you are affected by the security breach in your environment, click the news item. This displays your OCI accounts and enables you to see details on each.
About Orca Security
We’re on a mission to provide the industry’s most comprehensive cloud security platform while adhering to what we believe in: frictionless security and contextual insights, so you can prioritize your most critical risks and operate in the cloud with confidence.
Unlike other solutions, Orca is agentless-first and fully deploys in minutes with 100% coverage, providing wide and deep visibility into risks across every layer of your cloud estate. This includes cloud configurations, workloads, and identities. Orca combines all this information in a Unified Data Model to effectively prioritize risks and recognize when seemingly unrelated issues can be combined to create dangerous attack paths.
To learn more, see the Orca Platform in action.




