Non-human identities (NHI) play an essential role in cloud computing, helping to deliver many of its core benefits—from scalability to accessibility and beyond. Many software components rely on NHIs, such as cloud services, automation tools, CI/CD pipelines, and APIs. Unlike human users, these identities operate automatically and often use credentials that don’t expire or rotate regularly.
Despite their importance, NHIs also raise concern for security teams. A recent study by Gartner found that compromised non-human identities (NHIs) account for 85% of identity-related security breaches, an increasingly common incident for organizations.
The Orca Platform offers several key capabilities that help organizations secure their NHIs and manage the risks they present. In this blog, we examine them in detail, why they matter, and how they work.
What is a NHI?
An NHI is the digital identity used by machines, applications, and services to access resources and perform tasks in cloud environments—all without direct human involvement. These digital identities include service accounts, API keys, OAuth tokens, and secrets. They power machine-to-machine communication, enable automation, and help applications operate at scale.
Like other cloud resources, NHIs spin up continually and on demand, making them highly dynamic and distributed. This helps explain why they continue to multiply at a staggering pace and far outnumber their human counterparts. In fact, a recent analysis by the Orca Research Pod found that the ratio of NHIs to users is now 50 to 1.
Why does Orca secure NHIs?
As automation scales, so does the number of service roles, machine identities, and access tokens created to support it. These NHIs form a large portion of the cloud attack surface and are often overlooked by organizations.
By securing NHIs, organizations can enforce the principle of least privilege (PoLP), reduce unnecessary exposures, and secure interactions between services.
How does the Orca Platform secure NHIs?
The Orca Platform helps organizations detect, prioritize, and remediate their NHI-related risks through several important capabilities, which include new enhancements.
#1. NHI discovery and investigation
The challenge: NHIs are multiplying faster than teams can manage, creating an ever-expanding attack surface. Security teams need to keep pace—not just with discovery, but with triage and investigation.
The solution: Orca identifies non-human identities by scanning the control plane and analyzing cloud-native configurations. To detect NHIs, Orca reviews:
- IAM roles, service principals, and machine users in your cloud accounts
- Trust relationships and policy definitions
- Usage patterns, such as long-lived tokens used in automation
- Activity metadata that distinguishes between human and automated behavior
- Secrets such as API keys found in code repositories, buckets, databases, and virtual machines
These inputs help Orca identify NHIs and surface findings that provide you with insights to investigate their behavior, access patterns, and risk levels across your environment.
Orca offers multiple out-of-the-box queries to streamline the discovery and investigation of NHIs and their associated status. Available through the Orca Query Catalog, these predefined queries enable you to identify workload identities, API keys, private keys, managed or unmanaged SSL certificates, and more—with just a few clicks.
For example, you can run a predefined query to automatically see a complete inventory of all managed cloud provider API keys in your environment. After running the search, you can drill down further into each result to see its associated details, risks, and compliance information.
Our predefined NHI queries give you complete and immediate visibility into the NHIs you want to find across a variety of common use cases.
#2. Expanded visibility into third-party vendor NHIs
The challenge: According to the Orca Research Pod, organizations on average use four third-party APIs. These NHIs carry out important functions, ranging from provisioning access to automating operations. Yet they can provide attackers with a soft target if they go overlooked and neglected by security teams.
The solution: Using the Orca Platform, you can easily see, track, and monitor every third-party NHI in your cloud estate—all in one place. This includes any missing service accounts from popular applications, applications with basic service accounts, and more.
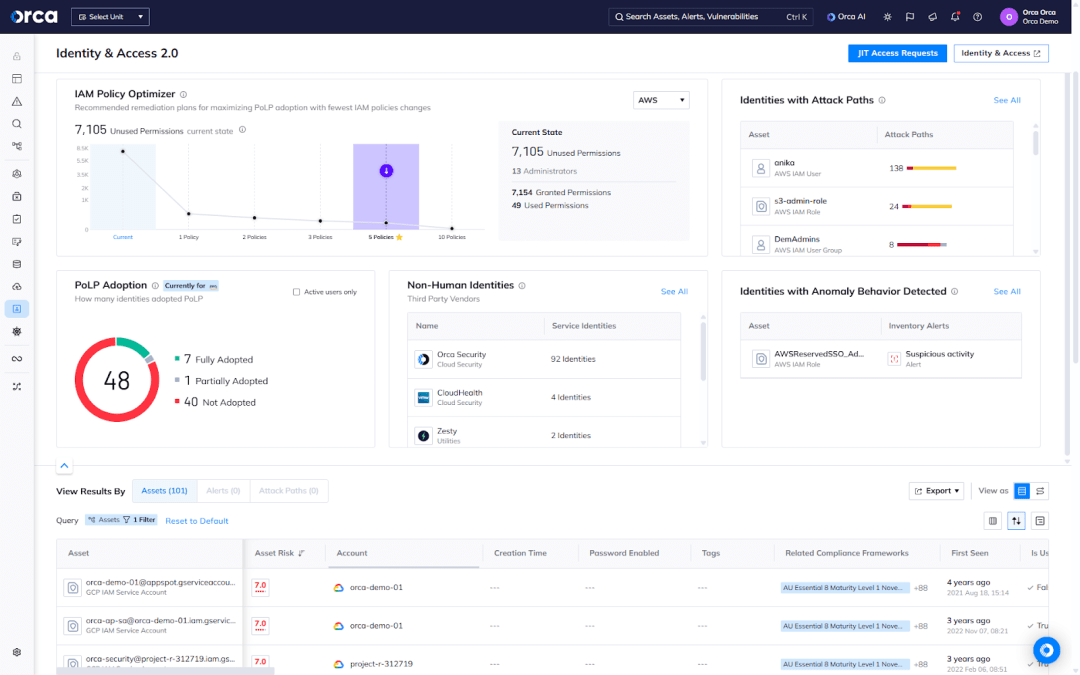
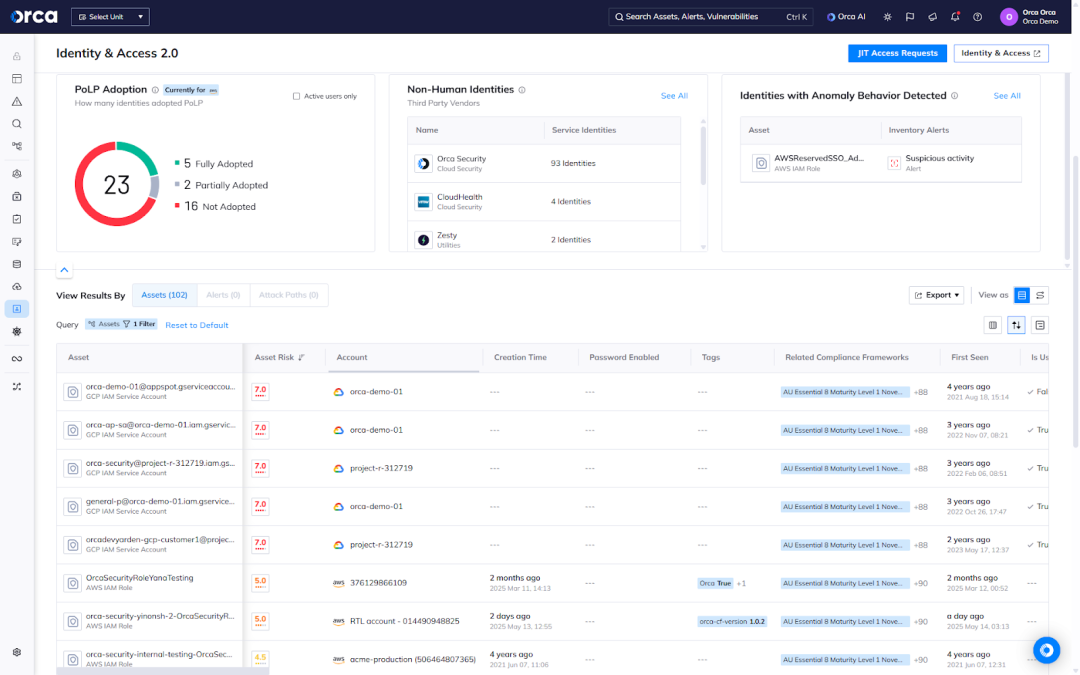
From Orca’s Identity and Access dashboard, you can view the third-party NHI vendors with the most service identities in your environment and the number associated with each.
You can also easily filter and view a complete inventory of third-party NHIs, all prioritized by the criticality of their associated risks. Both features provide security teams insight into their supply-chain identities.
#3. Comprehensive risk detections for NHIs
The challenge: NHIs can present a variety of risks that security teams must protect against, including risks related to Identity and Access Management (IAM), APIs, lateral movement, and much more. Without the ability to identify, prioritize, and remediate the different types of NHI risks, organizations face increased risk of security breaches or other severe incidents.
The solution: Orca detects a comprehensive range of NHI risks, including improper identity offboarding, secret leakage, insecure authentication, human use of NHI, broad permissions, and much more.
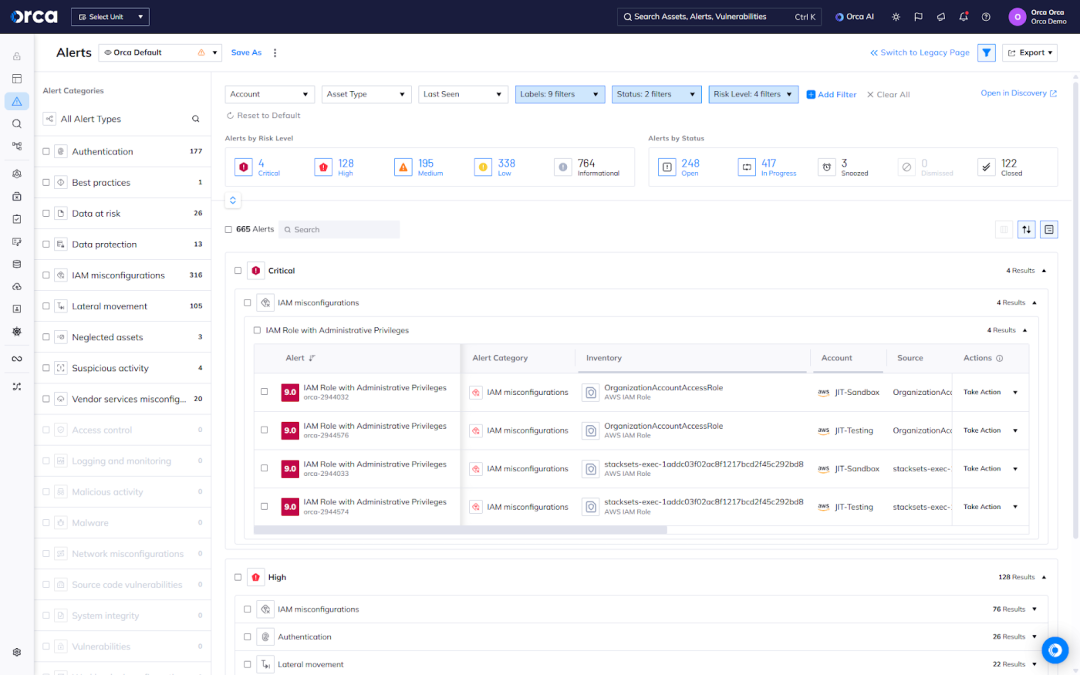
Along with all other types of risks, you can view a prioritized list of NHI-related risks via the Orca Alerts view, which offers a convenient filter to scoping alerts to see only the most common and critical types, as defined by the OWASP Non-Human Identities Top 10 project. This makes it easy and fast for you to focus on the NHIs risks that pose the greatest risk to your cloud.
Like all other risks detected by the Orca Platform, you can also remediate NHI risks quickly and easily using AI-driven or assisted options.
#4. NHI continuous monitoring and compliance
The challenge: While security teams struggle to gain visibility into their NHIs, they also face challenges sustaining it. As the volume of NHIs continues to increase, organizations must contend with new and existing exposures.
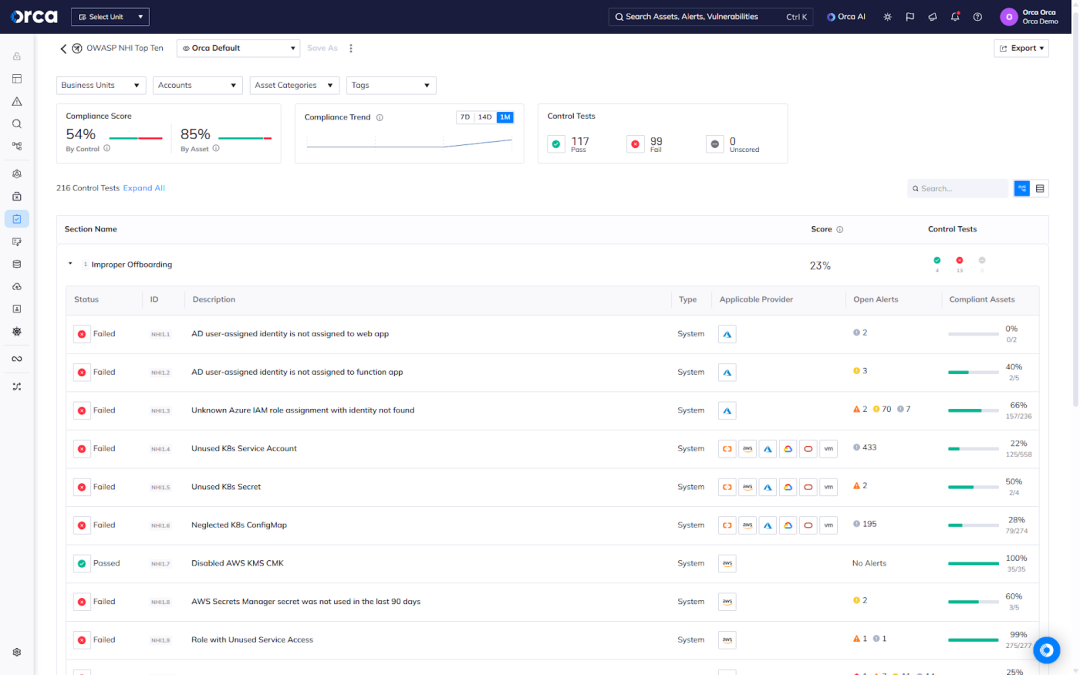
The solution: The Orca Platform provides you with a sustainable way to protect against the most common and critical NHI-related risks. Orca now offers a built-in framework for the OWASP Top 10 for Non-Human Identities project, helping you track and monitor the most critical NHI risks.
Orca automatically detects all of the OWASP Top 10 risks and maps them to the framework, giving you up-to-date and continuous visibility in one unified location.
Like any of 200+ built-in compliance frameworks that the Orca Platform offers, you can export the framework on demand in CSV or JSON formats, as well as schedule an exported report to send automatically on a recurring or one-time basis to an email, storage bucket, or Slack channel.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ Technology to provide complete coverage and comprehensive risk detection.
Learn More
Interested in discovering the benefits of the Orca Platform and its capabilities for securing NHIs? Schedule a personalized 1:1 demo.