Stolen credentials remain one of the leading causes of data breaches and one of the costliest. According to IBM’s 2025 Cost of a Data Breach Report, breaches caused by compromised credentials result in average losses of $4.67 million USD per incident.
Among the many risks facing today’s cloud environments, leaked passwords stand out as both highly dangerous and often overlooked. A single exposed credential can provide attackers with direct access to critical cloud assets, bypassing perimeter defenses and security tools.
In this post, we’ll explore what leaked passwords are, why detecting them is so critical, and the steps organizations can take to defend themselves. We’ll also show how the Orca Cloud Security Platform helps teams identify, address, and prevent leaked passwords across their environments.
What are leaked passwords?
A leaked password is any password—often associated with an operating system user account—that has been exposed through a major data breach or otherwise published online. These leaked credentials frequently appear in dark web marketplaces, paste sites, or aggregated password dumps.
Because attackers can easily access these databases, leaked passwords pose a real risk to organizations that reuse or fail to rotate them. Even a single compromised account can serve as an attacker’s foothold into a cloud environment.
The Orca Platform helps detect these risks by scanning block storage and checking discovered credentials against databases of known leaked or commonly used passwords. Orca also performs offline brute force testing, fuzzy username searches, and password hash comparisons to confirm when a password is truly compromised, then generates an alert so teams can act quickly.
Why detecting leaked credentials is critical
Unlike traditional on-premises networks, cloud environments are inherently exposed. Services and accounts can often be accessed from anywhere in the world, meaning a compromised password provides attackers with immediate entry.
Once inside, adversaries rarely stop at the first system they compromise. They frequently:
- Escalate privileges to gain admin-level access
- Move laterally through cloud accounts and regions
- Steal or encrypt sensitive data
- Manipulate source code and deployments
For example, if an administrator’s password for a cloud management console is leaked, attackers could provision new resources, disable security controls, or exfiltrate sensitive customer data. Beyond the direct financial impact, organizations must often deal with reputational and regulatory consequences.
How to protect against leaked passwords
When it comes to leaked credentials, the real question isn’t if, it’s when. To reduce exposure, organizations must combine proactive detection, rapid remediation, and preventive controls.
1. Adopt multi-layered detection
A single method of detection isn’t enough. That’s why the Orca Platform employs multiple techniques to surface leaked credentials:
- Password matching: Comparing discovered credentials against databases of commonly used and known leaked passwords.
- Offline brute force testing: Evaluating how easily weak passwords can be cracked.
- Fuzzy username searches: Testing variations like alternate domains or misspellings (for example, johndoe@acme.com → john.doe@acme.net).
- Hash comparison: Matching discovered passwords against stored hashes to confirm compromises.
When Orca detects a leaked password, it generates a prioritized alert enriched with full context. This layered approach gives organizations the best chance of finding leaked credentials before attackers do.
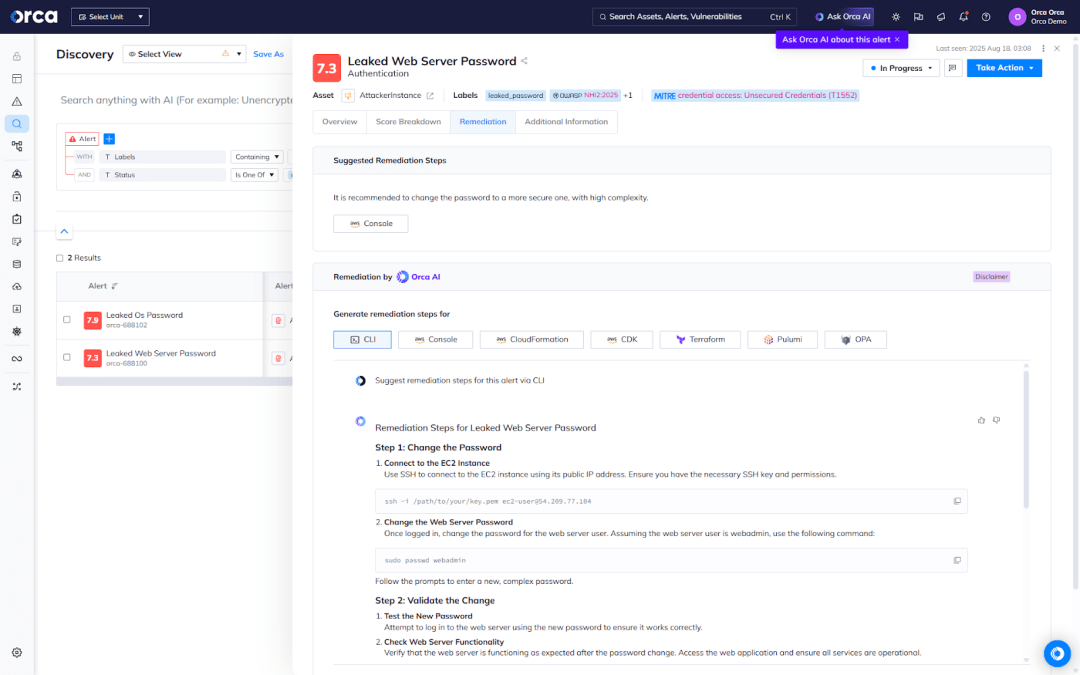
2. Enable rapid remediation
Detection is only the first step in addressing leaked credentials. When a leaked password is identified, security teams need the ability to:
- Force password resets.
- Rotate passwords.
- Investigate access logs for suspicious activity.
With Orca, teams can remediate alerts using multiple tailored and targeted options, including those powered by Orca’s AI-Driven Remediation feature or created and vetted by our security experts. The former enables users to produce high-quality remediation instructions and code in one-click, ensuring fast and easy fixes.
3. Prevent password leaks in the first place
Beyond detection, prevention is key. Orca provides Application Security (AppSec) capabilities such as Secrets Detection, which prevents credentials from ever reaching production environments.
- Deep integrations with development platforms: Orca natively integrates with source code management (SCM) platforms like GitHub, GitLab, Azure DevOps, and Bitbucket, providing comprehensive and continuous coverage of all your code repositories, including any new ones your developers create.
- Code scanning: Orca automatically scans for secrets whenever developers push something new or create a pull request, as well as your entire Git history.
- Customizable policies: Teams can block builds containing secrets or simply notify developers without disrupting workflows.
- Git hooks: Orca offers pre-commit and pre-receive hooks to catch secrets on workstations or SCM platforms before they spread across the organization.
This matters because attackers act fast. The Orca Research Pod found it takes just two minutes for exposed secrets on GitHub to be discovered and exploited.
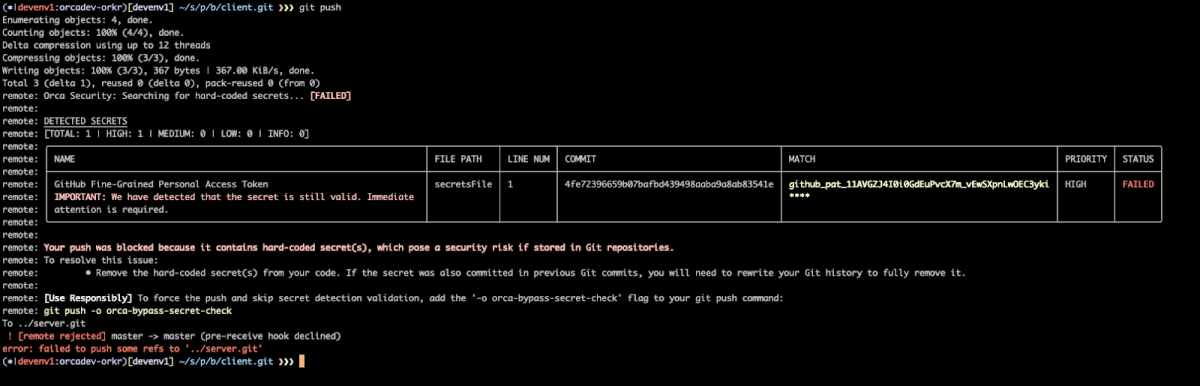
4. Build a comprehensive defense
Leaked password detection should be one layer of a broader security strategy. Organizations should also adopt zero-trust principles, fortify Identity and Access Management (IAM), and more.
Orca offers built-in Cloud Infrastructure Entitlement Management (CIEM) capabilities that help organizations enforce the principle of least privilege (PoLP). Using Orca, security teams can gain deep visibility into cloud entitlements, right-size permissions to align with least-privilege principles, and reduce the risk of credential misuse.
Most recently, Orca extended its CIEM capabilities with Just-in-Time (JIT) Access. This feature allows administrators to grant temporary, time-bound access to internal or external users, minimizing the dangers of standing privileges. If a password is leaked, JIT ensures there are fewer always-on accounts that attackers can exploit, reducing the potential blast radius of a compromise.
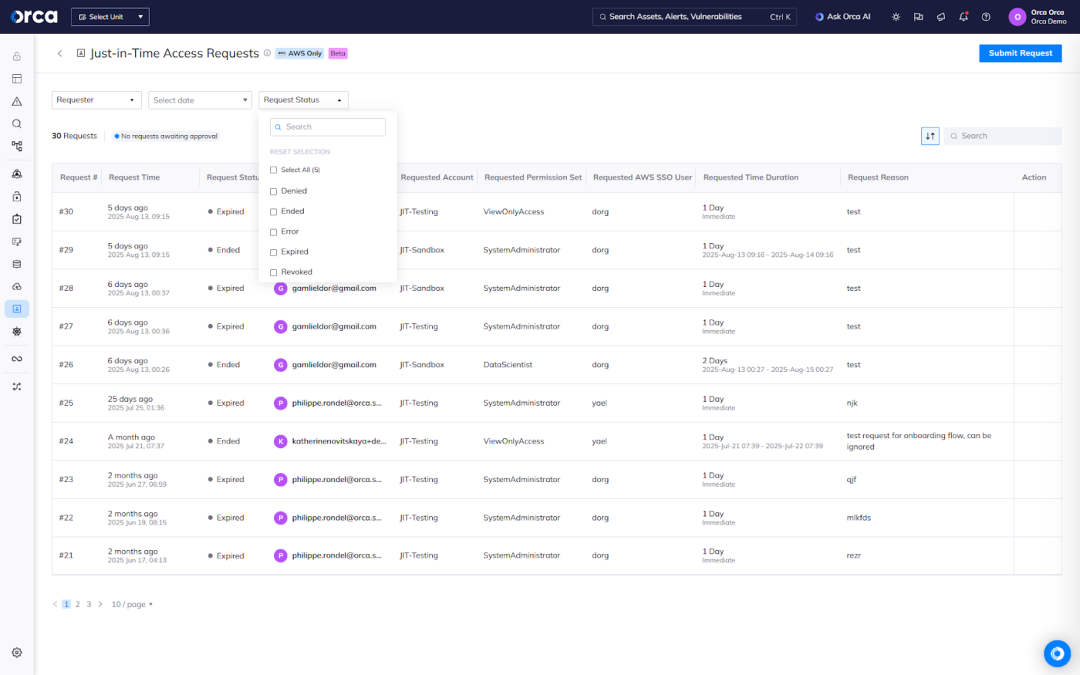
The bottom line
The cost of implementing strong password detection and prevention is small compared to the impact of a successful breach. Proactive credential monitoring isn’t just a best practice, it’s a business necessity.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn more
Interested in discovering the benefits of the Orca Platform, including how it secures your cloud? Schedule a personalized 1:1 demo, and we’ll demonstrate how Orca can protect against leaked secrets and other cloud security risks.






