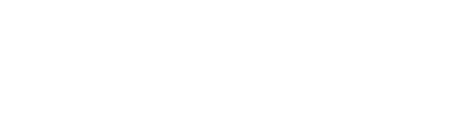The Challenge
Traditional CSPM Isn’t Enough
Traditional CSPM solutions help organizations stay compliant and address cloud risks such as misconfigurations and overly permissive identities. However, a CSPM only covers one part of the attack surface, leaving cloud workloads, event monitoring, and sensitive data discovery out of the picture.
Traditional CSPMs lack insight into cloud workloads, which means they cannot detect vulnerabilities, malware, data at risk, or exposed secrets.
Security teams must supplement traditional CSPMs with multiple siloed tools, which results in constantly having to switch consoles, duplicating efforts, and hindering consistency.
Siloed or ‘integrated’ tools lack shared context, resulting in contradictory alerts and ineffective alert prioritization.
Our Approach
Orca Defines the Future of CSPM
Orca consolidates cloud workload, configuration, identity & entitlement security, container security, sensitive data discovery, and detection & response all in one platform across the entire SDLC. This unified approach allows Orca to understand the full context of risks and recognize when seemingly unrelated issues can create dangerous attack paths. Leveraging these insights, Orca is able to prioritize risks effectively, reducing alert fatigue and ensuring that security teams stay focused on what matters most.
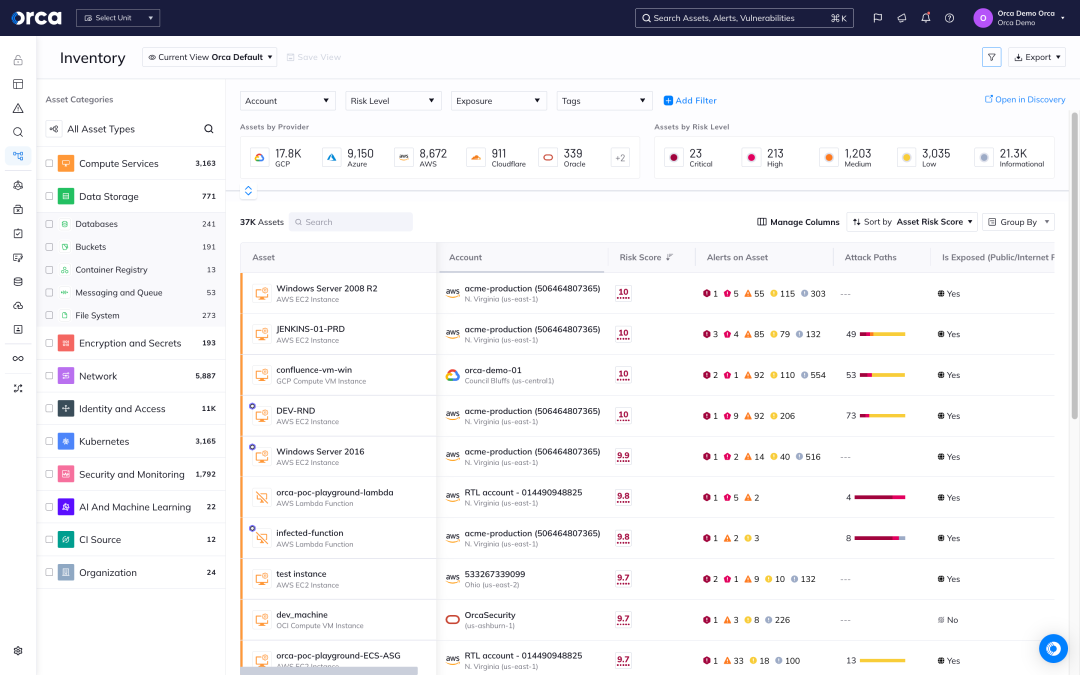
Receive alerts when security policy violations occur, such as misconfigured S3 buckets, Google storage buckets, KMS keys, Elasticsearch and RDS databases, and much more.
Leverage 2,500+ configuration controls across 10+ categories, including authentication, data protection, logging and monitoring, network configurations, Kubernetes configurations, and system integrity.
Instead of getting inundated with alerts, security teams can rely on Orca to prioritize the risks that endanger the company’s most critical assets so they can be addressed first.
Additionally, Orca continuously checks for misconfigurations across multi-cloud estates to ensure controls are set securely and comply with best practices and industry and regulatory standards.
Understand risks across your entire tech stack
Unlike other CSPMs, Orca also scans cloud workloads and identities to surface full insights into the risks across your entire tech stack. This enables Orca to understand which risk combinations pose the greatest danger, so your teams can address those first.
- By scoring and prioritizing attack paths, security teams can focus on a much smaller number of dangerous attack paths versus sifting through hundreds of siloed alerts.
- Orca presents potential attack paths in a visual graph showing the end target as well as detailed information on each step.
- For each attack path, Orca shows which risks need to be remediated to break the attack path, further prioritizing issues for remediation if they break multiple paths.
Ensure multi-cloud compliance
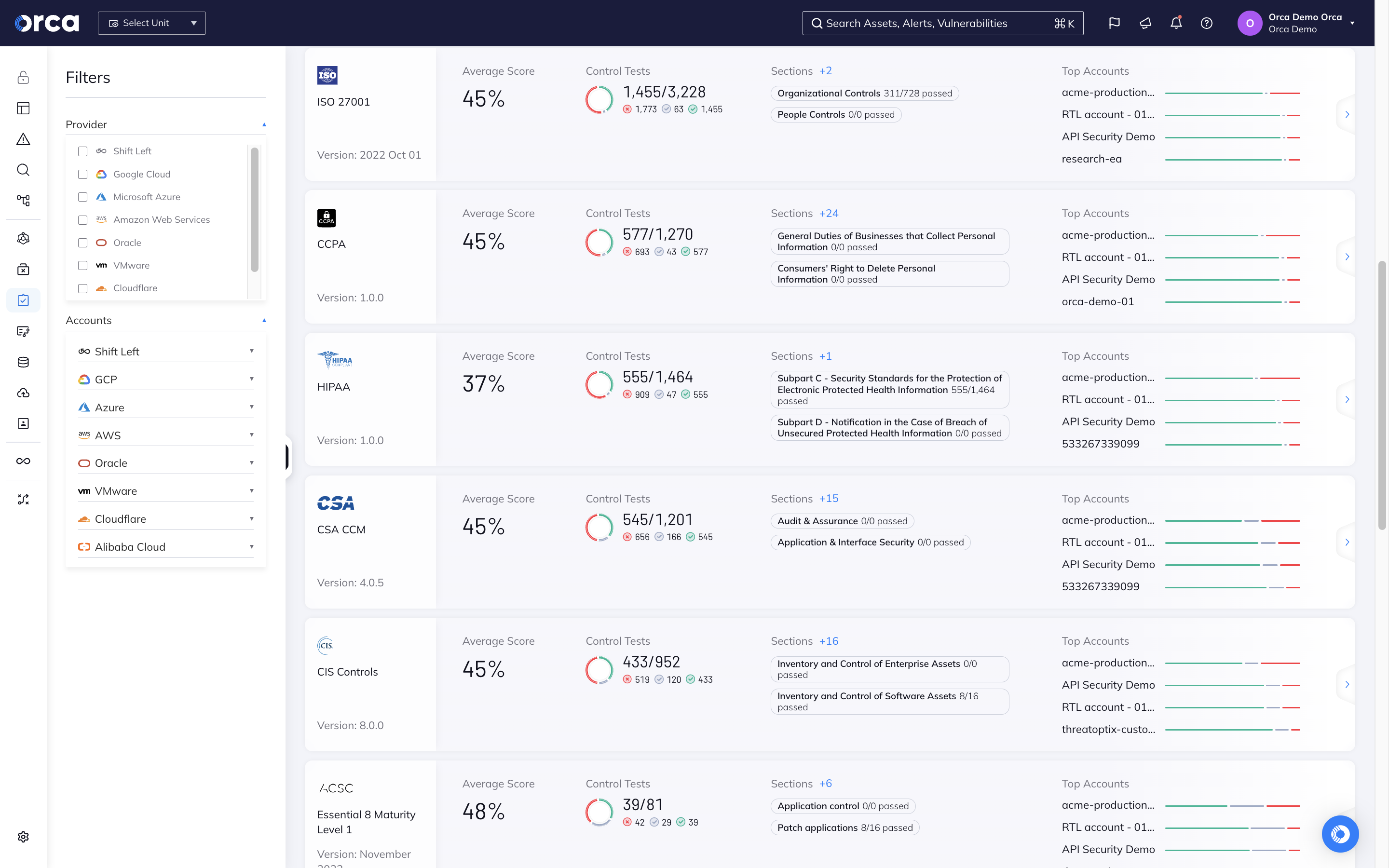
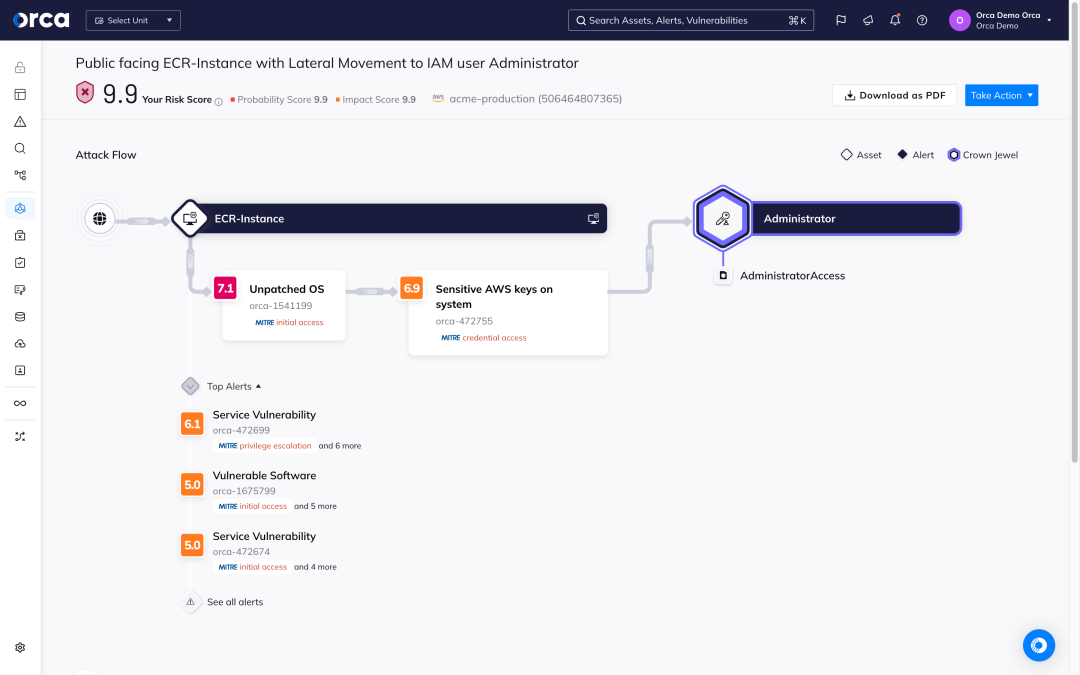
Another important CSPM function that Orca provides is ensuring that cloud resources comply with regulatory frameworks and industry benchmarks, including data privacy requirements. Orca unifies compliance for cloud infrastructure workloads, containers, identities, data and more – all in a single dashboard.
- Orca checks cloud configurations and policies against more than 150 industry and regulatory frameworks, including Orca Best Practices and a wide range of CIS control benchmarks.
- Unlike other CSPMs, Orca also discovers sensitive data in your cloud environment and notifies you when data, such as PII, is vulnerable through potential exploitation paths.
- With this insight, Orca helps organizations prioritize data security and demonstrate their compliance with mandates such as PCI-DSS, GDPR, HIPAA, and CCPA.
Remediate risks at the speed of the cloud
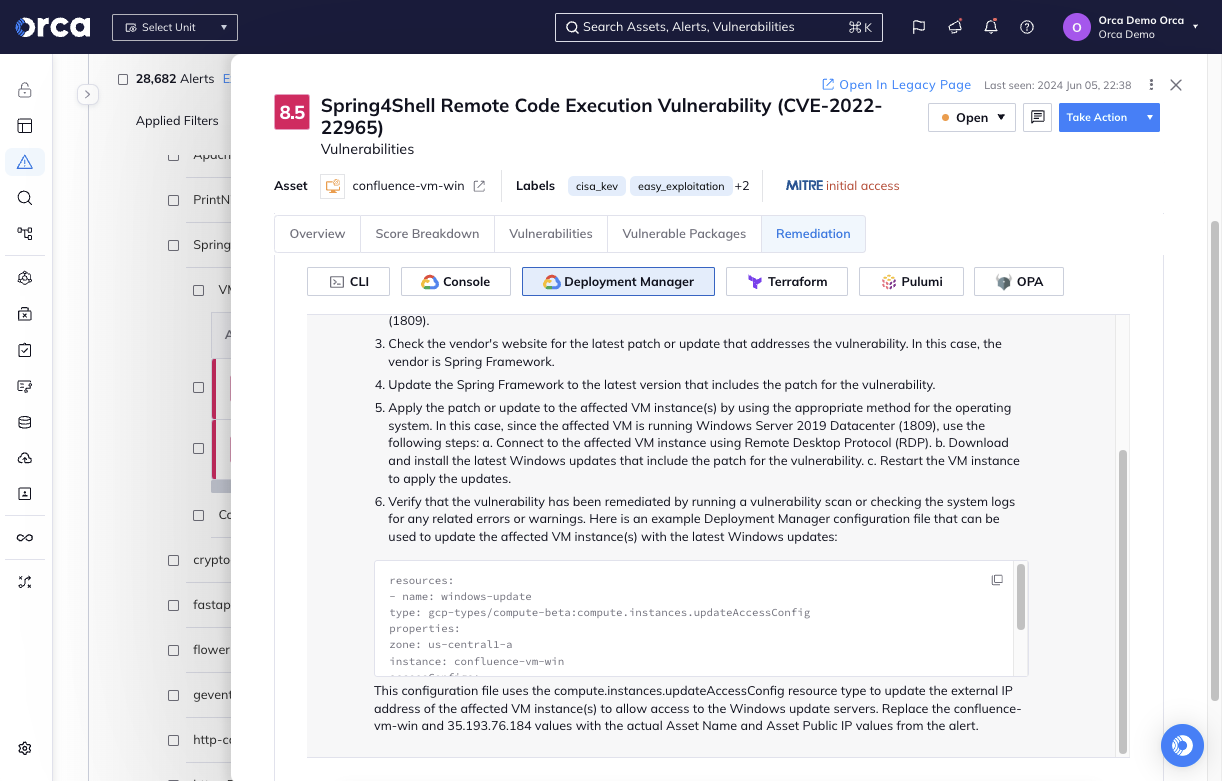
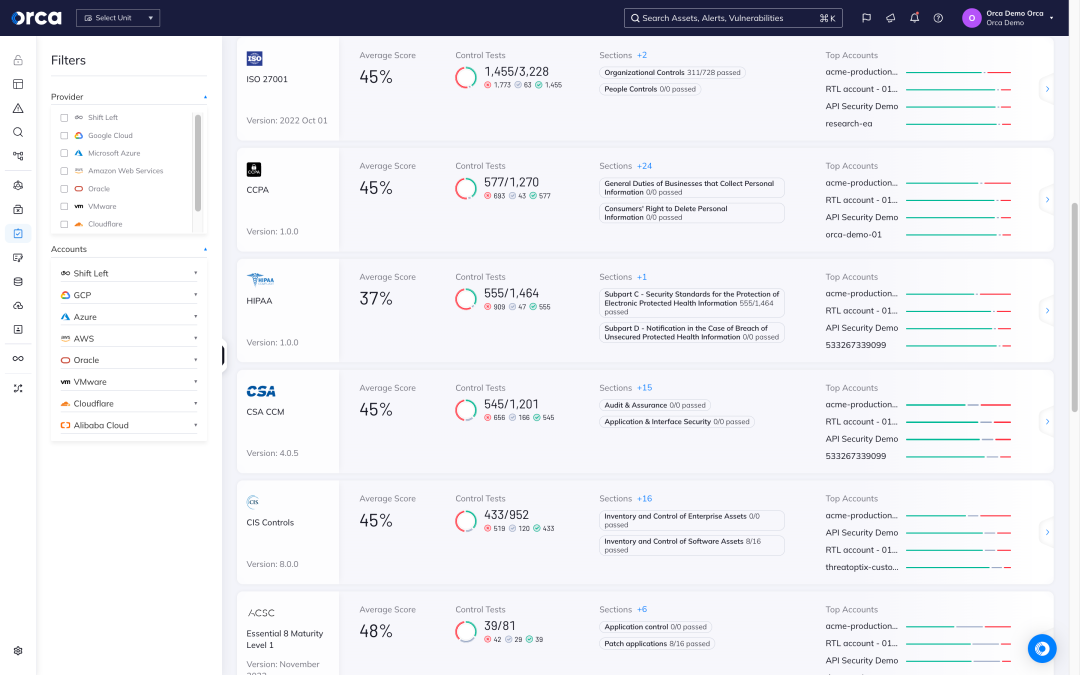
Orca offers auto remediation and guided remediation options, helping you to quickly address any detected risks – reducing your Mean Time to Remediation (MTTR) and improving your cloud security posture.
- Configure automation rules that remediate alerts as soon as they are detected without requiring any manual intervention.
- Generate high-quality remediation instructions for each alert leveraging generative AI built into the Orca platform.
- Copy and paste remediation code into a command line interface or Infrastructure as Code (IaC) provisioning tools, or follow steps in the console.
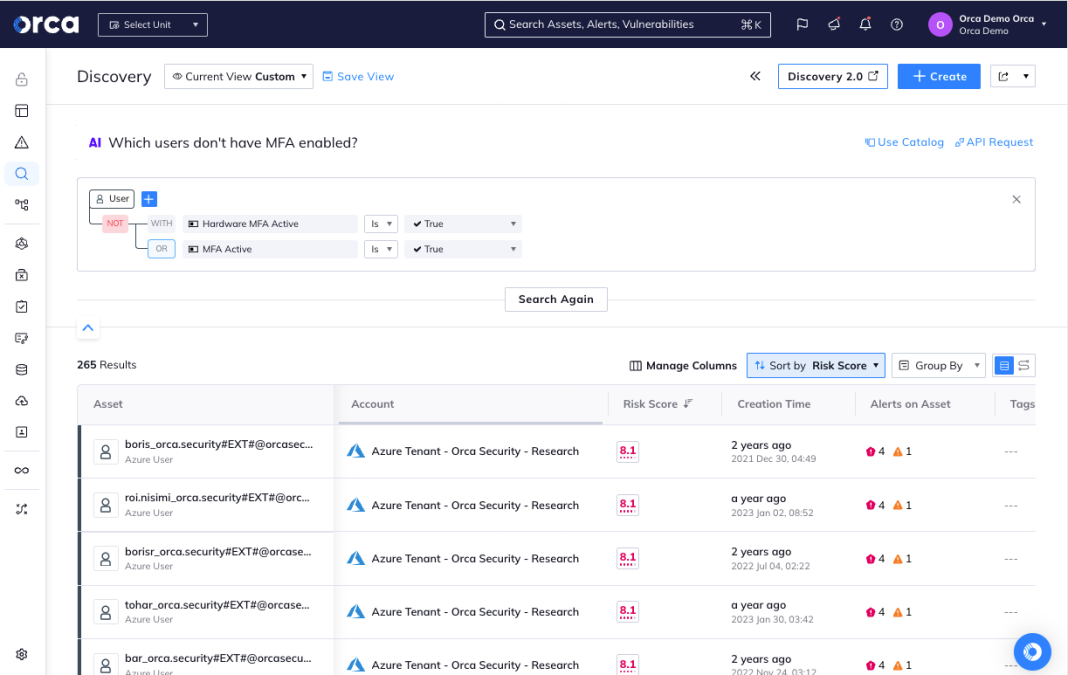
Easily search your cloud environment
Leveraging AI, Orca greatly simplifies searches by enabling users to ask natural language questions – significantly reducing time-to-discovery and improving compliance.
- Ask plain language questions such as ‘Do I have any vulnerabilities that are public facing?’ or “Do I have any unencrypted databases with sensitive data exposed to the Internet?”
- Regardless of skill level, Orca allows users across the organization to easily understand exactly what’s in their cloud environment.
- Advanced users can craft complex and granular queries much faster than when having to code in a proprietary query language.
Orca Has You Covered
Frequently Asked Questions
Cloud Security Posture Management (CSPM) is a cloud security solution that enables organizations to identify and remediate risks and any misconfigurations in their cloud infrastructure so they can reduce their attack surface.
Gartner first named CSPMs as a cloud security category in 2014. CSPMs emerged as a necessary solution to help organizations maintain the proper configurations of cloud services as they migrated to popular public cloud environments such as AWS, Azure, and Google Cloud.
CSPMs remain a popular cloud security solution. According to Gartner, the CSPM market is expected to grow in the coming years, with annual revenues predicted to reach $3.32 billion by 2027. Still, a subsequent Gartner analysis estimates that 75% of new CSPM purchases will come from cloud native application protection platforms (CNAPPs) by 2025.
Cloud misconfigurations are a top cloud security concern. Several factors increase their likelihood, including insufficient monitoring, unrestricted access controls, mismanaged secrets, unreviewed default values, and more. According to a Gartner survey, misconfigurations cause 80% of all data security breaches, and predictions are that until 2025, 99% of cloud environment failures will be attributed to human errors.
As a segment of cloud security tools, CSPMs play an important role in continuously monitoring cloud infrastructure for gaps in security policy enforcement. They automatically identify misconfigurations across cloud infrastructures, and in some cases remediate them too. As a result, CSPMs can help organizations save money, identify security risks, and educate teams.
A CSPM helps security teams remediate misconfigurations and maintain compliance by monitoring the cloud control plane and ensuring that it aligns with defined security policies. More specifically, a CSPM:
- Maintains a cloud asset inventory: Creates and maintains an organized inventory of all cloud infrastructure.
- Ensures cloud compliance: On an ongoing basis, tracks cloud assets for compliance against relevant regulatory frameworks and industry benchmarks.
- Defines and enforces policies: Identifies and enforces policies for accessing data and compliance reporting.
- Detects cloud threats: Identifies risks in your cloud infrastructure and creates alerts for remediation.
- Facilitates incident response: Assists incident response by presenting relevant information and guidance needed to remediate risks or compliance issues.
CSPMs are essential for cloud security, however traditional CSPM solutions present important limitations, including:
- Only cover control plane: CSPMs provide visibility into cloud configurations (control plane) but not cloud workloads (data plane). As a result, they have no insight into vulnerabilities, malware, or exposed secrets.
- Alert fatigue: Without visibility into workloads, CSPM solutions lack the unified insight to fully contextualize risks and prioritize alerts based on the full context.
- No identity and permissions management: CSPM tools also don’t manage access controls, permissions, or entitlements. To support and enforce the principle of least privilege (PoLP), organizations need a cloud infrastructure entitlement management (CIEM) solution.
For this reason, CNAPPs (Cloud-Native Application Protection Platforms) have emerged to address the challenges of using siloed traditional cloud security solutions. A CNAPP is a cloud security solution that detects risks across the full technology stack (control plane and data plane), including cloud misconfigurations, mismanaged identity access, vulnerabilities, malware and data at risk.
Traditional CSPM tools pull metadata via the cloud provider’s APIs to obtain visibility into the cloud infrastructure, but only identify simple control plane misconfigurations and have limited insight into overall workload risk posture. CSPM tools can only detect risks such as malware and vulnerabilities at the cloud infrastructure layer, leaving a significant portion (OS, application, and data) of the cloud estate exposed. In addition, because they have a limited perspective on data risk, CSPM tools lack insight as to where sensitive data might be stored and the potential for its exposure.
In contrast, as a CNAPP, Orca combines CSPM, CWPP, CIEM and more in a single platform, and provides full-stack visibility of your cloud estate—that is, visibility that spans the cloud infrastructure, OS, application, and data layers—ensuring you have complete security and compliance coverage.