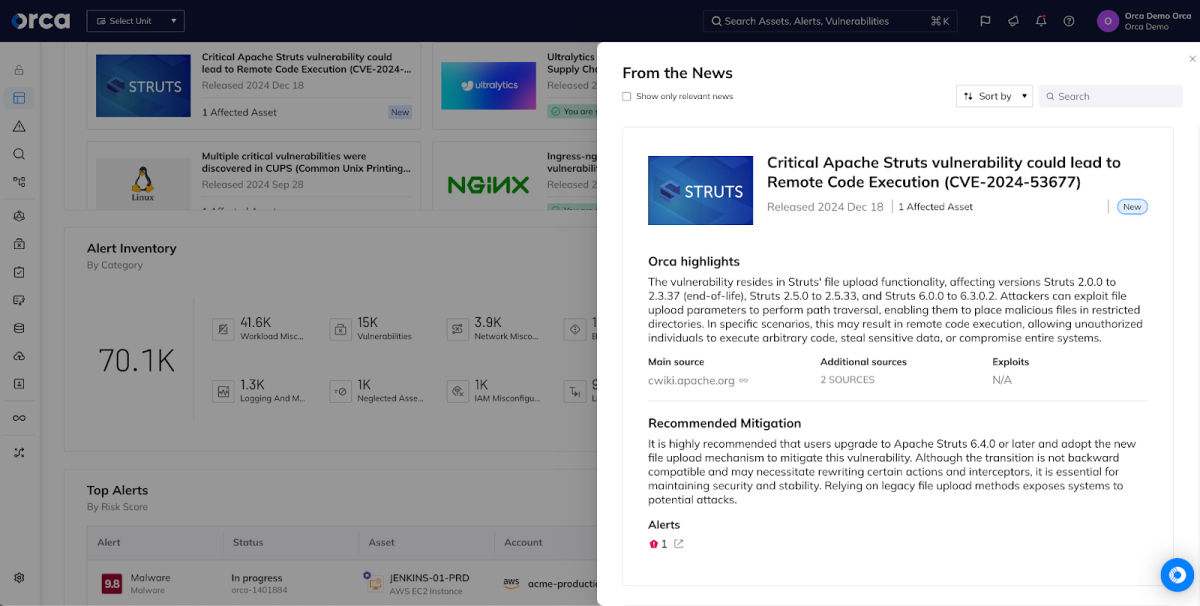
A critical vulnerability, CVE-2024-53677, has been identified in the Apache Struts 2 framework, a popular platform for developing Java-based web applications. The vulnerability, with a CVSS score of 9.5/10, allows attackers to exploit a flaw in the file upload mechanism to cause arbitrary file overwrite or execute arbitrary code remotely. Security experts have confirmed active exploitation of this flaw, prompting urgent action to mitigate potential risks to organizations worldwide.
Based on Orca’s analysis, nearly 1 in 5 organizations (18%) operating in the cloud have vulnerable applications currently deployed.
Key Points
- Critical Severity: With a CVSS score of 9.5/10, CVE-2024-53677 poses a significant risk, enabling remote code execution and potential full system compromise.
- Proof-of-Concept Available: A publicly available PoC exploit heightens the urgency for organizations to act quickly to mitigate the vulnerability.
- High-Profile Targets: Due to its widespread use by enterprises and government agencies, Apache Struts is a prime target for attackers, further amplifying the potential impact of this flaw.
What is Apache Struts?
Apache Struts is an open-source framework for Java web applications. It is widely used in Java-based web applications and, given both its ubiquity and that web applications are normally exposed to the Internet, previous critical vulnerabilities in Struts have been widely exploited.
About CVE-2024-53677
CVE-2024-53677 exploits Apache Struts’ file upload logic, allowing attackers to perform path traversal and arbitrary file overwriting by manipulating the top.uploadFileName parameter in multipart requests. Using a crafted boundary string, the attacker bypasses security mechanisms to upload files to unauthorized locations, enabling remote code execution (RCE). The flaw exists due to improper validation of multiple parameters in the request.
Apache Struts versions 2.0.0–2.3.37, 2.5.0–2.5.33, and 6.0.0–6.3.0.2 are vulnerable. Users must upgrade to version 6.4.0 or later, which resolves the issue. This update requires adopting the new, secure file upload mechanism, as older methods are incompatible.
CVE-2024-53677 shows the importance of timely patching and strong security practices. Organizations using affected Apache Struts versions are encouraged to review their systems and consider upgrading to mitigate potential risks. Taking timely action can help safeguard critical systems and reduce exposure to this security flaw.
Recommendations
We recommend acting quickly to:
- Identify assets that are potentially vulnerable to CVE-2024-53677
- Prioritize remediation for vulnerable assets that are exposed directly to the Internet, part of an attack path, or otherwise high-risk/high-value
- Investigate exposed, vulnerable systems to determine if they have been already compromised
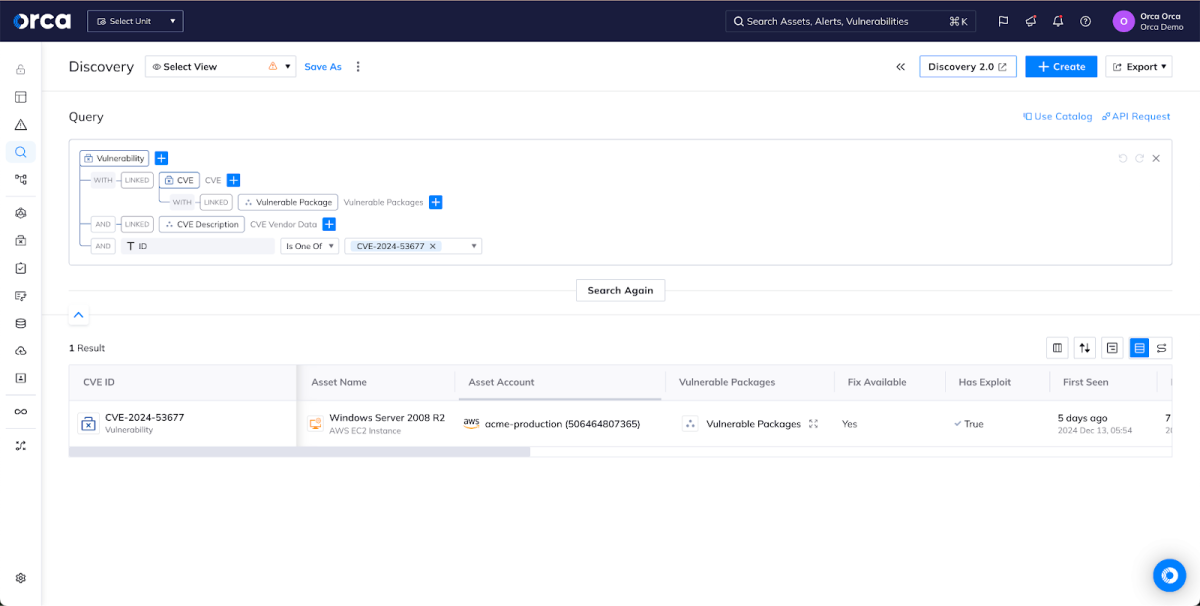
Orca Security can help
To see how Orca can help you discover any affected resources in your cloud environments on AWS, Azure, Google Cloud, Oracle Cloud, and Alibaba Cloud, as well as mitigate and investigate any vulnerabilities, schedule a 1:1 demo with one of our experts.