After leading several cloud security transformations across large and fast-moving organizations, I have found that one truth has always held: you can’t protect what you can’t see.
That’s why the first decision every CISO faces, where to begin your cloud security journey, matters more than any single tool or technology. Should you start with posture management? Workload protection? Application Security? Runtime threat detection?
The truth is, there’s no single correct answer, because cloud security has become inherently cyclical. Each step feeds the next, and no matter where you begin, you’ll eventually circle back to improve earlier stages. That’s why the most successful programs follow a logical maturity path, layering visibility, protection, and detection in the right order, while staying adaptable.
STEP 1: Start with CSPM and CIEM—the foundation for everything else
When I first stepped into my last CISO role, the hardest part wasn’t remediating threats, it was figuring out what even existed.
Cloud Security Posture Management (CSPM) solves that problem. It gives you the complete inventory and posture baseline needed to manage risk across clouds, accounts, and business units.
CSPM should answer questions like:
- What assets do we actually have and where are they?
- Which configurations introduce exposure?
- Where are we violating compliance baselines (e.g. CIS benchmarks)?
- Which resources are publicly exposed or overprivileged?
CSPM gives you the map before you start defending the territory.
Where CIEM fits in
Early on, you’ll discover that identities, not servers, are your biggest attack surface.
That’s where Cloud Infrastructure Entitlement Management (CIEM) comes in. It complements CSPM by highlighting:
- Unused or excessive permissions
- Privilege escalation risks
- Shadow identities and rogue service accounts
Together, CSPM and CIEM establish your foundation of visibility and access control, setting the tone for everything that follows.
STEP 2: Deepen protection with CWPP and Data Security
Once you can see your environment clearly, it’s time to strengthen what’s inside it.
A Cloud Workload Protection Platform (CWPP) expands your defenses to cover the workloads powering your business, from EC2 instances to containers, Kubernetes clusters, and serverless functions.
In past transformations, CWPP became the key to understanding what was actually running inside the workloads, from vulnerable packages to misconfigured containers or outdated libraries.
At this stage, you’re moving from “what do I have” to “what could be exploited.”
Where Data Security fits in
No cloud security program is complete without understanding where sensitive data lives and how it’s being accessed.
Data Security Posture Management (DSPM) helps identify:
- Sensitive data stores across clouds
- Overexposed or unencrypted data
- Data access paths tied to identity risk
When DSPM insights are correlated with posture (CSPM) and access (CIEM) data, you can finally measure risk in business context, not just in technical terms.
STEP 3: Mature into Runtime Detection & Response (CDR) and AI Security
Once posture and workload hygiene are under control, it’s time to focus on what’s happening right now.
That’s where Cloud Detection and Response (CDR) comes into play. It correlates runtime activity (API calls, IAM behavior, network flows, process executions) to detect active threats early and with precision.
In my experience, runtime data is only valuable when paired with strong posture and identity context. Without it, your SOC will drown in false positives.
Where AI Security enters the picture
As more organizations embed AI models and pipelines into production systems, AI Security becomes a new dimension of cloud defense.
It builds on everything that came before:
- CSPM defines where models and datasets live
- CIEM governs who and what can access them
- DSPM identifies sensitive training data
- CWPP and CDR monitor runtime behavior for model drift, poisoning, or data exfiltration
Think of AI Security as your next-generation runtime layer; one that protects the intelligence driving your business.
STEP 4: Introduce Application Security (if you are ready)
In many organizations I’ve led, Application Security (AppSec) didn’t become meaningful until much later, despite the industry’s push to “shift left.”
And that’s not a failure. It’s a sign of maturity.
AppSec only becomes powerful once you have a strong grasp of:
- What your cloud workloads look like
- How they behave at runtime
- How identities interact with them
- Where sensitive data lives
- How pipelines deploy changes into production
At this stage, AppSec becomes the bridge between development and cloud operations. It allows you to trace a vulnerability from source code into the running workload, understand how it behaves at runtime, and feed findings back into engineering for faster remediation.
You’re no longer scanning code in isolation. You’re connecting code → infrastructure → identity → data → runtime in a continuous loop.
And while AppSec often enters late in the journey, it remains flexible.
Organizations with strong DevOps cultures may introduce it earlier; others may wait until their cloud environment is stable and predictable. Both paths make sense, depending on where you are in your Cloud journey.
STEP 5: Leverage the synergy of CNAPP
Over the years, I’ve watched cloud security evolve from point tools into integrated platforms.
That’s what CNAPP (Cloud-Native Application Protection Platform) represents: the convergence of posture, identity, workload, data, and runtime protection into a single, correlated view.
| Layer | Provides | Enables |
|---|---|---|
| CSPM | Asset visibility & posture | CIEM, CWPP, DSPM, CDR |
| CIEM | Identity context | DSPM, CDR, AI Security |
| CWPP | Workload & vulnerability data | CDR, AI Security |
| DSPM | Data sensitivity & exposure | Runtime correlation, AI Security |
| AI Security | Model & data protection | Full CNAPP maturity |
| CDR | Threat detection & response | Automated, context-aware defense |
| AppSec | Code-to-cloud lineage & application insight | Stronger shift-left practices, remediation prioritization |
When combined, these layers finally deliver what we’ve all been chasing: risk-based security that aligns with how the cloud actually works.
Build from the ground up, not the other way around
Every cloud security transformation I’ve led has reinforced the same lesson:
“You can’t automate, detect, or defend what you haven’t first mapped and understood.”
There is a logical maturity curve in cloud security, but organizations rarely begin at the same point. Some start with posture, some with workload hardening, some with runtime monitoring, and others with code-level controls.
The key is understanding how the layers build on one another, no matter where you enter the cycle.
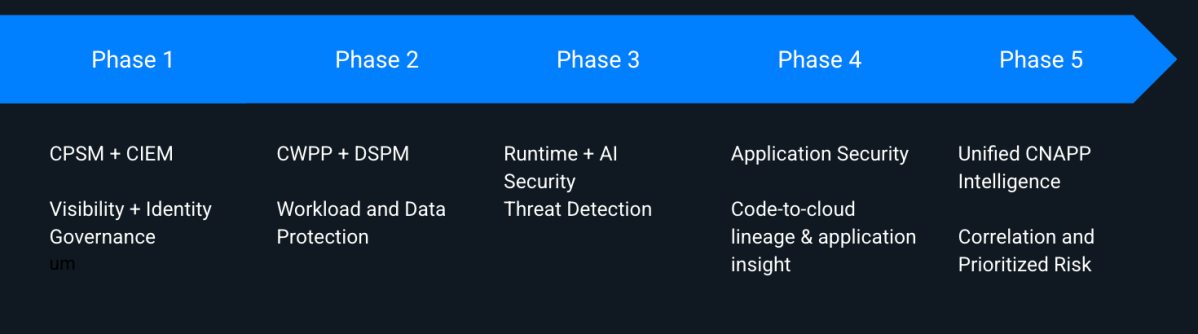
A practical, real-world maturity order looks like this:
- CSPM + CIEM – establish visibility and control
- CWPP + DSPM – secure workloads and data
- Runtime + AI Security – detect and respond to live threats
- AppSec (option) — introduced when the organization is ready, tying code → cloud → runtime
- Unified CNAPP – correlate it all for prioritized, risk-driven action
At Orca Security, this layered philosophy is built into our CNAPP platform.
By correlating posture, workload, identity, data, and runtime signals automatically, Orca helps organizations accelerate cloud maturity – no matter where they begin – and reduce risk without adding complexity or noise.
Because in the end, the best security programs don’t just find issues faster, they make the cloud safer, more resilient, and more predictable by design.
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. The Orca Cloud Security Platform leverages Orca’s patented SideScanning™ technology to provide complete coverage and comprehensive risk detection.
Learn more
Interested in seeing the Orca Platform in action? Schedule a personalized 1:1 demo.
Table of contents
- STEP 1: Start with CSPM and CIEM—the foundation for everything else
- STEP 2: Deepen protection with CWPP and Data Security
- STEP 3: Mature into Runtime Detection & Response (CDR) and AI Security
- STEP 4: Introduce Application Security (if you are ready)
- STEP 5: Leverage the synergy of CNAPP
- Build from the ground up, not the other way around
- About the Orca Cloud Security Platform
- Learn more
Table of contents
- STEP 1: Start with CSPM and CIEM—the foundation for everything else
- STEP 2: Deepen protection with CWPP and Data Security
- STEP 3: Mature into Runtime Detection & Response (CDR) and AI Security
- STEP 4: Introduce Application Security (if you are ready)
- STEP 5: Leverage the synergy of CNAPP
- Build from the ground up, not the other way around
- About the Orca Cloud Security Platform
- Learn more





