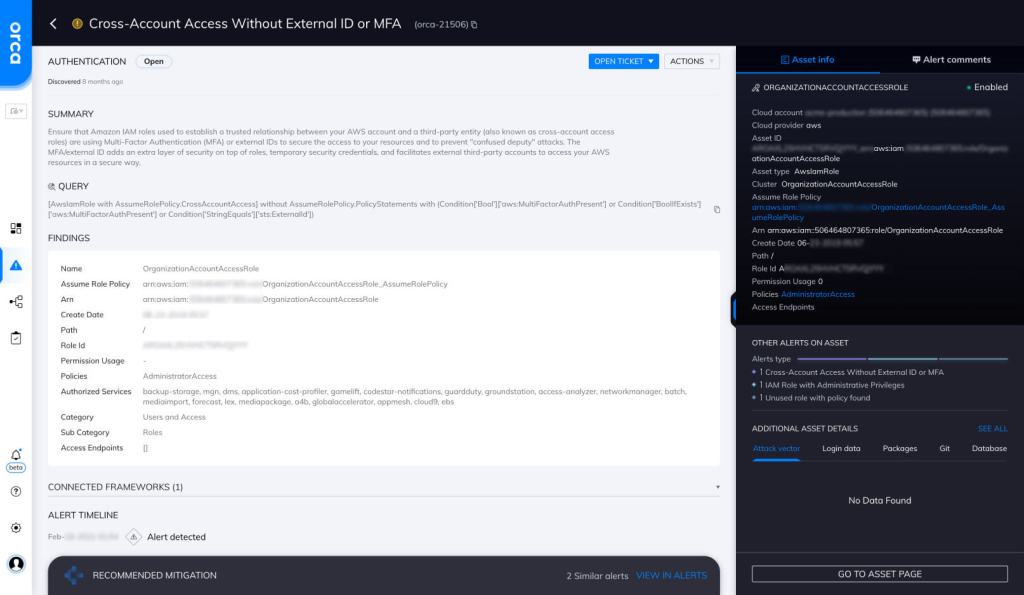
Cross-Account Access Without External ID or MFA
Hazardous (3)
APRA, MAS, NIST 800-53 (Rev. 4)
About Cross-Account Access
Many AWS architectures have separate accounts for development and production environments. AWS launched cross-account access to simplify multi-role access for engineers, allowing them to seamlessly switch between accounts, without having to (repeatedly) sign in and out.
Using cross-account access, administrators can define a role that grants access to resources in a different AWS account. This means that you don’t have to create a new IAM user for every account. Let’s look at an example.
In your AWS infrastructure, you have three different accounts: development, staging, and production. Developers spend most of their time in the development and staging environments. Sometimes, they have to venture into the production environment to solve critical bugs.
One way to provide access is to create separate IAM users for your developers across all three accounts. This approach requires developers to sign in and out each time they move between accounts. Another, more efficient solution, is to create a role in the production account and give certain development account users the ability to assume it. This way, a user logged into the developer account can switch roles from within the management console and access, say, an S3 bucket in the production account. Convenient and seamless? Yes. Secure? That depends.
When configured without external IDs or multi-factor authentication (MFA), cross-account access is prone to the confused deputy problem. This is when someone other than the intended entity assumes the cross-account role by providing the correct Amazon Resource Name (ARN).
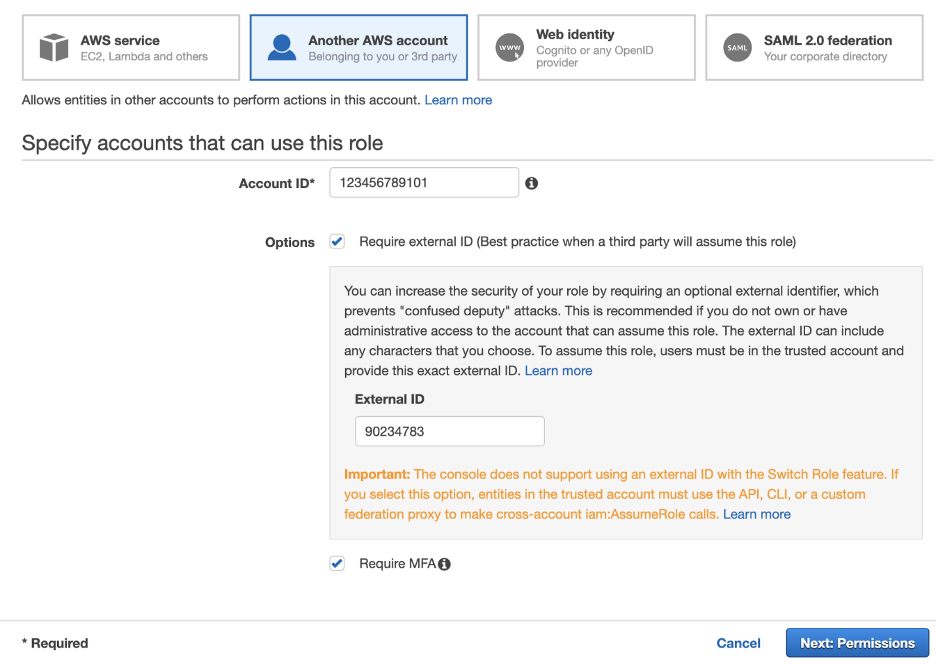
External IDs, required to be included in the requests to assume a cross-account role, ensure that the right person is accessing the right resource under the right circumstances. MFA requires the user to provide the unique code generated by the MFA device.
Cloud Risk Description
While creating a cross-account role on the AWS console, it’s optional to require MFA or external IDs. This means that any number of internal or third-party roles can be configured without the recommended authentication factors.
Malicious users can exploit the confused deputy problem to gain unauthorized access to resources, potentially causing irreparable damage to your infrastructure and reputation.
How Does Orca Help?
AWS allows you to audit your environment for insecure cross-account access, but Orca saves you the hassle. Orca can alert you if you have a role that allows cross-account access without MFA or an external ID.
Useful Links
- AWS cross-account access tutorial: https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-account-with-roles.html
- Creating a role to delegate permissions: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-user.html
- Cross-account access to S3 objects: https://aws.amazon.com/premiumsupport/knowledge-center/cross-account-access-s3/
- Cross-account access for Amazon EMR: https://docs.aws.amazon.com/emr/latest/ManagementGuide/emr-lf-cross-account-access.html
- Confused deputy problem: https://docs.aws.amazon.com/IAM/latest/UserGuide/confused-deputy.html
- External ID for third parties: https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_create_for-user_externalid.html
Orca Security, the cloud security innovation leader, provides cloud-wide, workload-deep security and compliance for AWS, Azure, and GCP - without the gaps in coverage, alert fatigue, and operational costs of agents.
