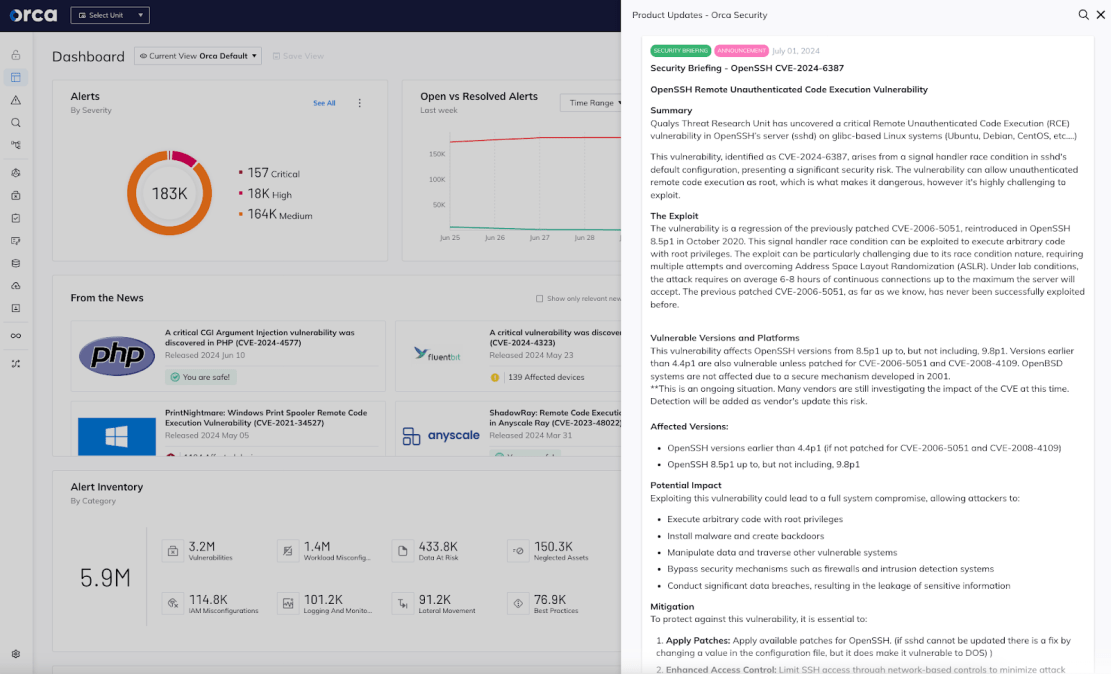
A critical Remote Unauthenticated Code Execution (RCE) vulnerability has been discovered in OpenSSH server (sshd) on glibc-based Linux systems (Ubuntu, Debian, CentOS, etc.). The vulnerability, identified as CVE-2024-6387, arises from a signal handler race condition in sshd’s default configuration, presenting a significant security risk.
If exploited, CVE-2024-6387 can allow unauthenticated remote code execution as root, making it extremely dangerous. However the vulnerability is highly challenging to exploit, so the likelihood of a successful exploitation is not that large. This is why the vulnerability was assigned the severity of High rather than Critical, with a score of 8.1.
Through analysis of the cloud environments scanned by the Orca Platform, the Orca Research Pod found that nearly half (48%) of organizations are using a vulnerable OpenSSH package. In total, 69% of organizations are using OpenSSH (through a dependency or directly), and of those organizations 70% are using a vulnerable OpenSSH version.
Even though this is a serious and widespread vulnerability, there are certainly mitigating actions that are available to greatly reduce the attack surface and the chance that an attacker will be able to exploit it.
What is OpenSSH?
OpenSSH (Open Secure Shell) is a suite of secure networking utilities based on the Secure Shell (SSH) protocol, developed to provide encrypted communication sessions over a computer network. OpenSSH encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks. It includes several components, such as ssh (for secure remote login), scp and sftp (for secure file transfers), and sshd (the SSH server daemon). CVE-2024-6387 was discovered in sshd on glibc-based Linux systems.
About CVE-2024-6387
The vulnerability is a regression of the previously patched CVE-2006-5051, reintroduced in OpenSSH 8.5p1 in October 2020. This signal handler race condition can be exploited to execute arbitrary code with root privileges. The exploit can be particularly challenging due to its race condition nature, requiring multiple attempts and overcoming Address Space Layout Randomization (ASLR). Under lab conditions, the attack requires on average 6-8 hours of continuous connections up to the maximum the server will accept. Advancements in deep learning may significantly increase the exploitation rate, potentially providing attackers with a substantial advantage in leveraging such security flaws,
The affected service is sshd in its default configuration.
The previously patched CVE-2006-5051, as far as we know, has never been successfully exploited before.
Who is vulnerable to CVE-2024-6387?
This vulnerability affects the following OpenSSH versions:
- OpenSSH versions earlier than 4.4p1 (if not patched for CVE-2006-5051 and CVE-2008-4109)
- OpenSSH 8.5p1 up to, but not including, 9.8p1
Note that OpenBSD systems are not affected due to a secure mechanism developed in 2001.
Potential impact
Exploiting this vulnerability could lead to a full system compromise, allowing attackers to:
- Execute arbitrary code with root privileges
- Install malware and create backdoors
- Manipulate data and traverse other vulnerable systems
- Bypass security mechanisms such as firewalls and intrusion detection systems
- Conduct significant data breaches, resulting in the leakage of sensitive information
Recommended mitigations
To protect against this vulnerability, organizations should:
- Apply all OpenSSH patches: Apply available patches for OpenSSH (if sshd cannot be updated there is a fix by changing a value in the configuration file, but it does make it vulnerable to DOS).
- Lock down access control: Limit SSH access via tcp/22 through network-based controls to minimize attack risks.
- Apply segmentation: Divide networks to restrict unauthorized access to the OpenSSH server.
- Watch for suspicious activity: Deploy systems to monitor and alert on unusual activities.
How Orca can help
Orca provides capabilities to identify and manage this critical vulnerability:
- Detect all assets that are vulnerable to CVE-2024-6387: For instance, in the Orca Platform > Discovery, you can enter the question ‘Which assets are vulnerable to CVE-2024-6387?’ Orca will show you all your assets that are running a vulnerable version of OpenSHH and are vulnerable to the CVE.
- Understand which of those assets need to be prioritized: For each of the vulnerable assets, Orca will show you the Orca Risk Score, so it’s immediately clear which assets are the most at risk. For instance this could be because they are Internet-facing and/or if breached, might provide access to sensitive information. It is recommended to start by mitigating the risks on the assets with the highest score.
- Monitor for unusual activity: Orca’s Cloud Detection and Response capabilities monitor events 24/7 and will alert when unusual and possibly malicious activity is occurring in the cloud environment.
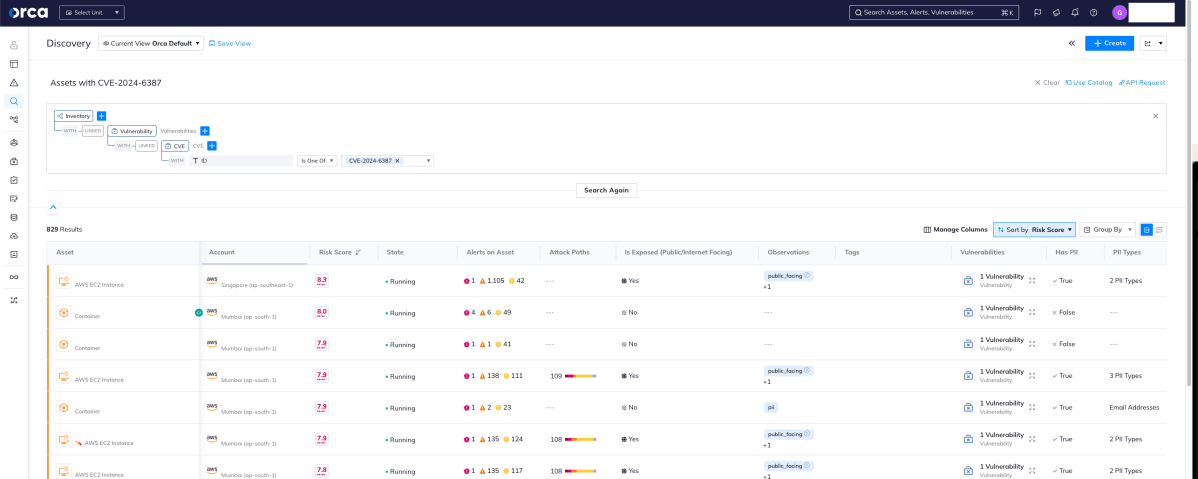
Orca shows you which assets have CVE-2024-6387 and which ones have the highest risk score and need to be mitigated first
About the Orca Cloud Security Platform
Orca offers a unified and comprehensive cloud security platform that identifies, prioritizes, and remediates security risks and compliance issues across AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. Using its patented SideScanning™ technology, Orca detects vulnerabilities, misconfigurations, malware, lateral movement, data risks, API risks, overly permissive identities, and much more.
Speak to an Orca expert
To learn more about how the Orca Platform can help to detect and mitigate CVE-2024-6387 and other CVEs, schedule a 1:1 demo with one of our Orca experts.