In Azure environments, guest users are the go-to option when giving access to a user from a different tenant. Often, little effort is invested in keeping guest users safe. However, this could prove to be a costly mistake.
It’s actually very important to monitor the third-party applications and identities that have access to your environment, since guest users often possess powerful permissions and can expose your organization to many risks if compromised. Through analysis of hundreds of cloud environments scanned by the Orca Platform, we found that over 37% of Azure accounts have at least one overly permissive guest user.
In this blog post, we present a case study in which a compromised Azure Active Directory Guest user leads to sensitive data leakage. We dive deep into the different stages of the attack and demonstrate how the Orca Cloud Security Platform can help you establish best practices to prevent these attacks from occurring, as well as detect actual attacks in real-time using Cloud Detection and Response (CDR).
What is an Azure Guest User?
An Azure Guest User refers to an individual who has been granted limited access to a Microsoft Azure environment but is not a member of the organization’s tenant. This access is typically provided to external partners or vendors who need to interact with resources within the organization’s Azure environment. Guest users are often invited to join the Azure Active Directory of the host organization, which allows them to sign in with their own credentials.
The Sample Environment
In our case study, we take the common scenario of an organization hiring the services of a third-party company that requires access to the cloud environment. In this case, we are hiring an IT Service Provider, called Atlantica IT Services, to provide IT support and maintenance in our cloud environment.
To provide the IT Service Provider with the necessary access, we created a tenant named ‘Atlantica IT Services’. In this tenant, we created a user – “Mike Atlantica”- and added him to the Orca Research tenant as a guest user.
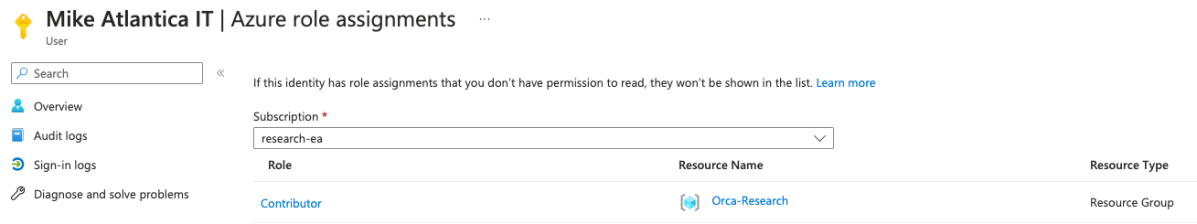
The ‘Mike Atlantica’ Azure guest user is given strong permissions
As we often see in the wild, we granted strong permissions to this user: We made them a contributor in the Orca-Research resource group. A Contributor in Azure IAM is an administrator role with access to almost every service in Azure.
Our sample cloud environment contains a Virtual Machine (VM) called prod-pg-server – an unmanaged PostGres DB with multiple credit card records.
Abusing the Guest User to Access Sensitive Data
If Atlantica IT Services suffers a security breach, and an attacker were to gain access to the user “Mike Atlantica”, they could use their permissions to access our Orca-Research resource group. The attacker can then search for VMs that host databases and have a public IP address in the resource group. Browsing the virtual machines, they will then find our prod-pg-server:
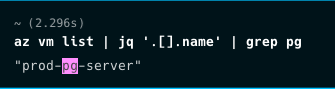
To gain access to this resource, they can try to use their permissions to reset the server password:
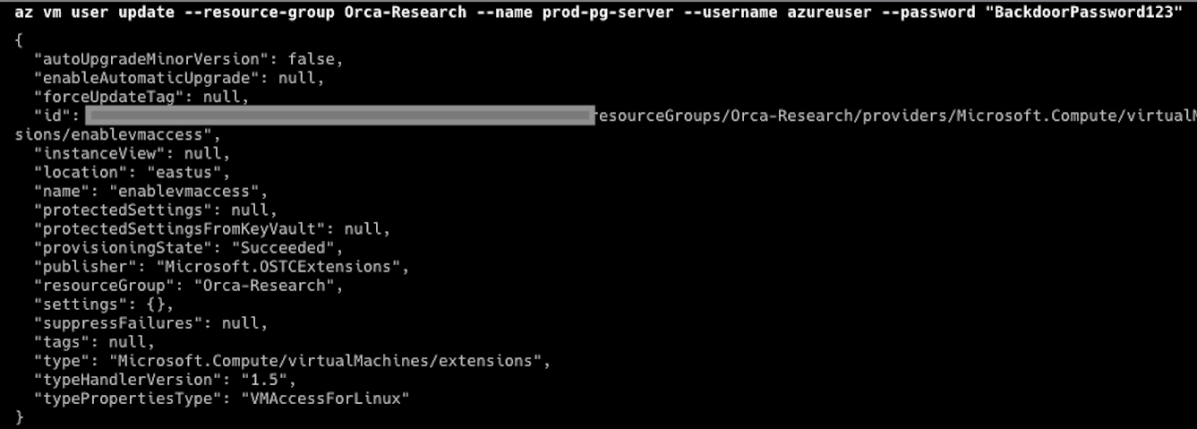
And voila! Now the attacker can connect to our prod-pg-server and access the sensitive credit card data. As you can see, it was super easy to access the sensitive data from the compromised external user account.
How to Defend against Guest User Abuse
Unfortunately, we don’t always know if third parties are properly managing their defenses. Even if they do, there are still no guarantees that they won’t be breached. So the potential danger with Azure guest users is clear, but what can we do about it?
We can’t simply not use Azure guest user accounts, since many organizations will still need them to provide access to third-party vendors or partners.
However, there are ways in which the risk of such exploits can be significantly reduced:
- Implement the principle of least privilege: Only provide the guest user with the permissions that are strictly needed to perform their duties. Providing them with Administrator access is not a good idea, unless strictly necessary.
- Perform regular auditing and monitoring: This ensures that any accounts that are no longer being used are deactivated timely, and if roles change, permissions are updated accordingly.
- Enable MFA on the guest user account: In this way, even if the account is compromised, there is an additional authorization measure in place.
- Apply Role-Based Access Control (RBAC): By using access control based on roles, it’s easier to manage least privilege permissions.
- Utilize Cloud Detection and Response (CDR): Even if an attacker is able to gain access to the environment, a CDR solution can quickly detect cloud attacks by continuously collecting and analyzing intelligence from cloud feeds, workloads, and configurations, allowing security teams to immediately respond to such an attack.
Leveraging the Orca Platform to Reduce Exposure
The Orca Cloud Security Platform can help prevent these types of attacks by continuously scanning cloud environments and alerting to overly permissive identities and other configurations that don’t align with cloud security best practices.
In the screenshot below, we can see that the Orca Platform generated the following two alerts for the user “Mike Atlantica”:
- “Azure Guest user with permissive role”
- “Privilege user MFA is disabled”
By remediating these alerts, an organization can prevent the attack scenario or limit potential damage before anything actually happens.
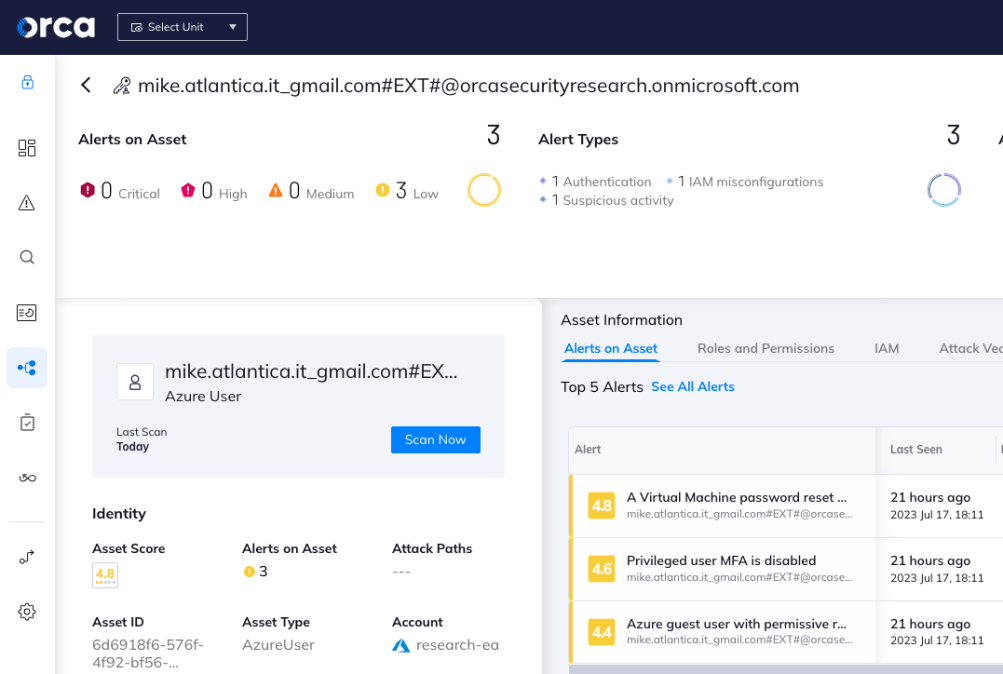
The Orca platform has detected security risks for the Azure guest user Mike Atlantica
Since in our example the attacker was able to penetrate the environment and reset the virtual machine password, Orca CDR detected this event. Since the action was also linked to a Guest user, this raised a red flag, and Orca alerted on this suspicious activity, enabling the security team to respond quickly.
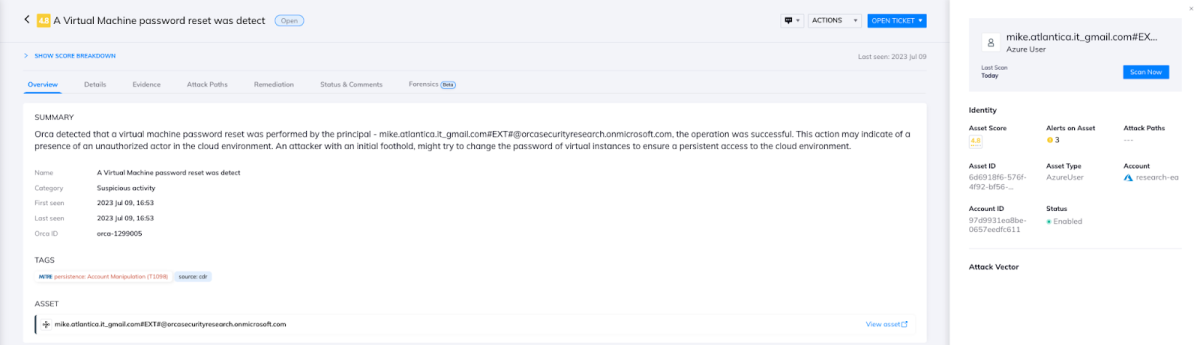
Using Orca Data Security Posture Management (DSPM) capabilities, we can search the affected asset and determine that it contains sensitive credit card information.
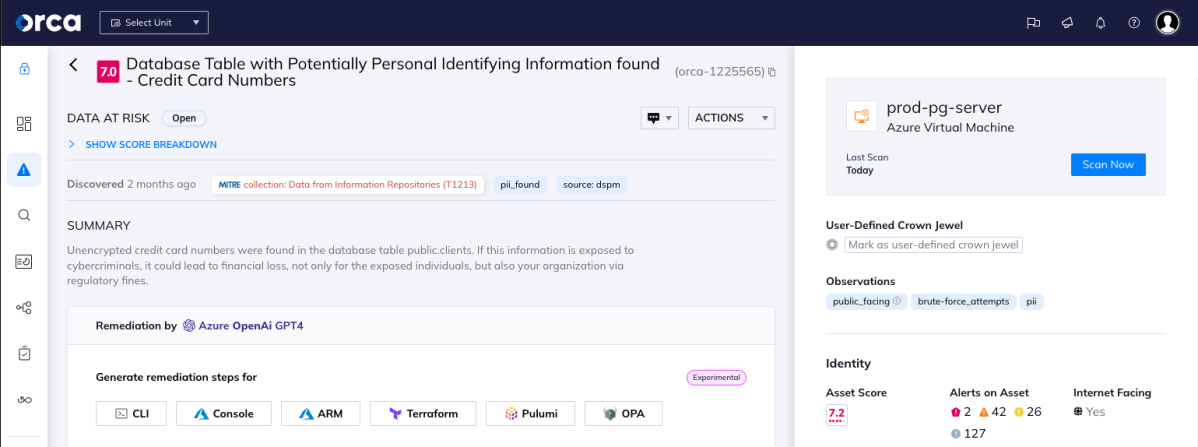
The SOC team can now respond with immediate remediation action, including disabling the guest user account and resetting the VM password, to prevent the attacker from connecting to the database server and leaking sensitive information, thus allowing the organization to contain the attack.
About the Orca Cloud Security Platform
The Orca Platform identifies, prioritizes, and remediates risks and compliance issues across cloud estates spanning AWS, Azure, Google Cloud, Oracle Cloud, Alibaba Cloud, and Kubernetes. Leveraging its patented SideScanning technology, Orca offers comprehensive cloud security coverage detecting vulnerabilities, misconfigurations, lateral movement, API risks, sensitive data at risk, anomalous events and behaviors, and overly permissive identities. Instead of layering multiple siloed tools together or deploying cumbersome agents, Orca delivers complete cloud security in a single platform.
Learn More
Would you like to learn more about the Orca Platform? Schedule a 1:1 demo, or download the Orca Platform Overview.






